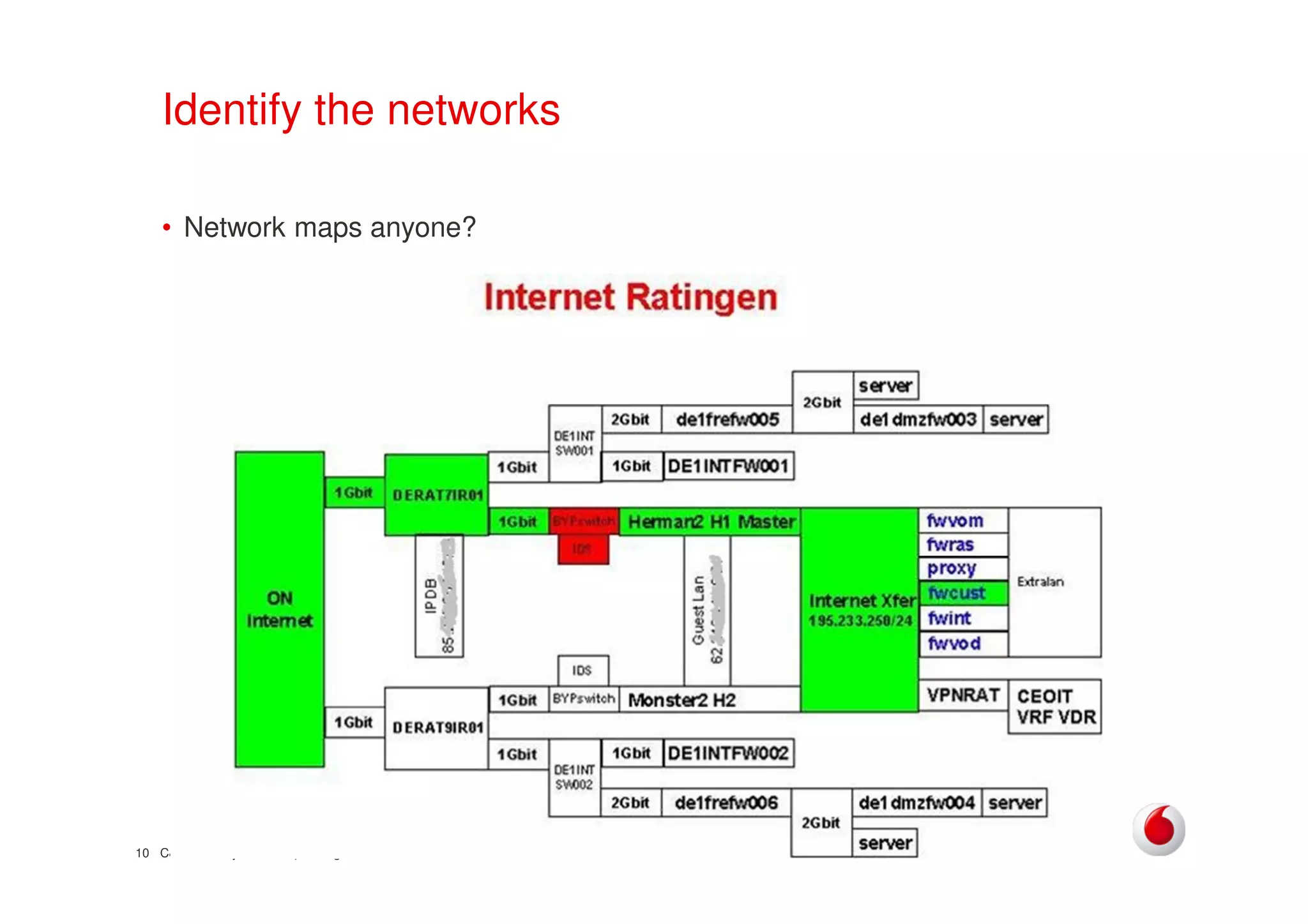
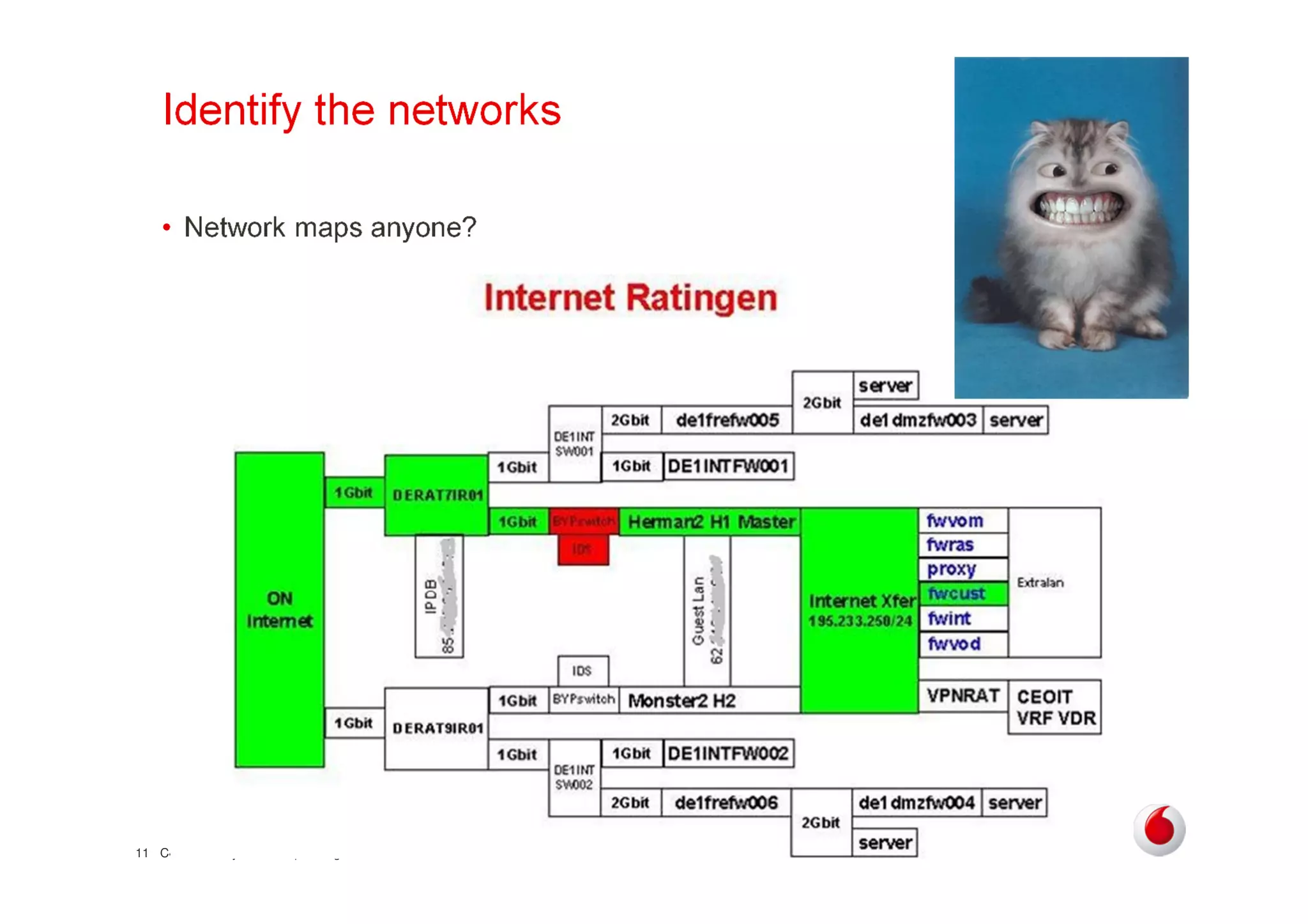
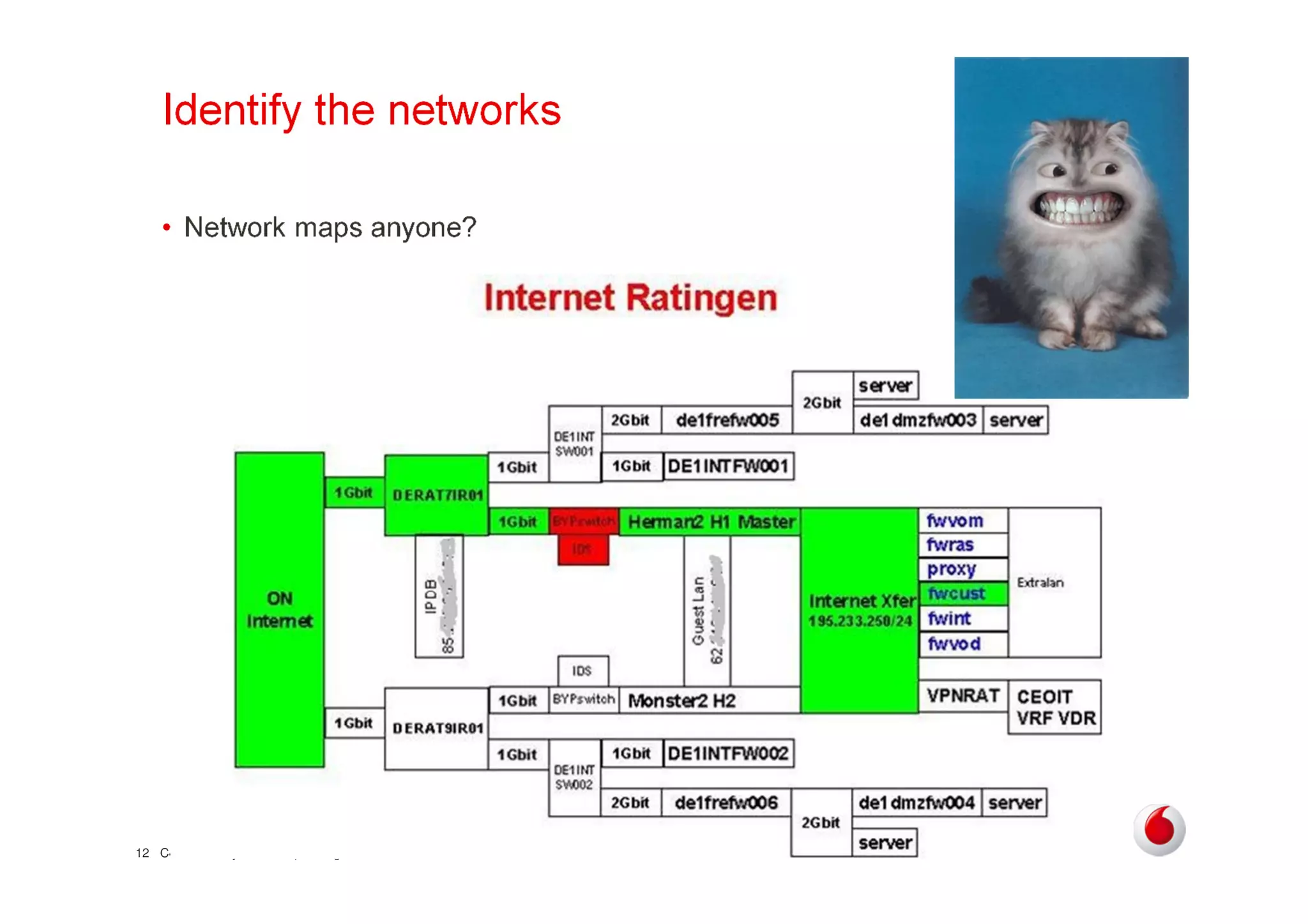
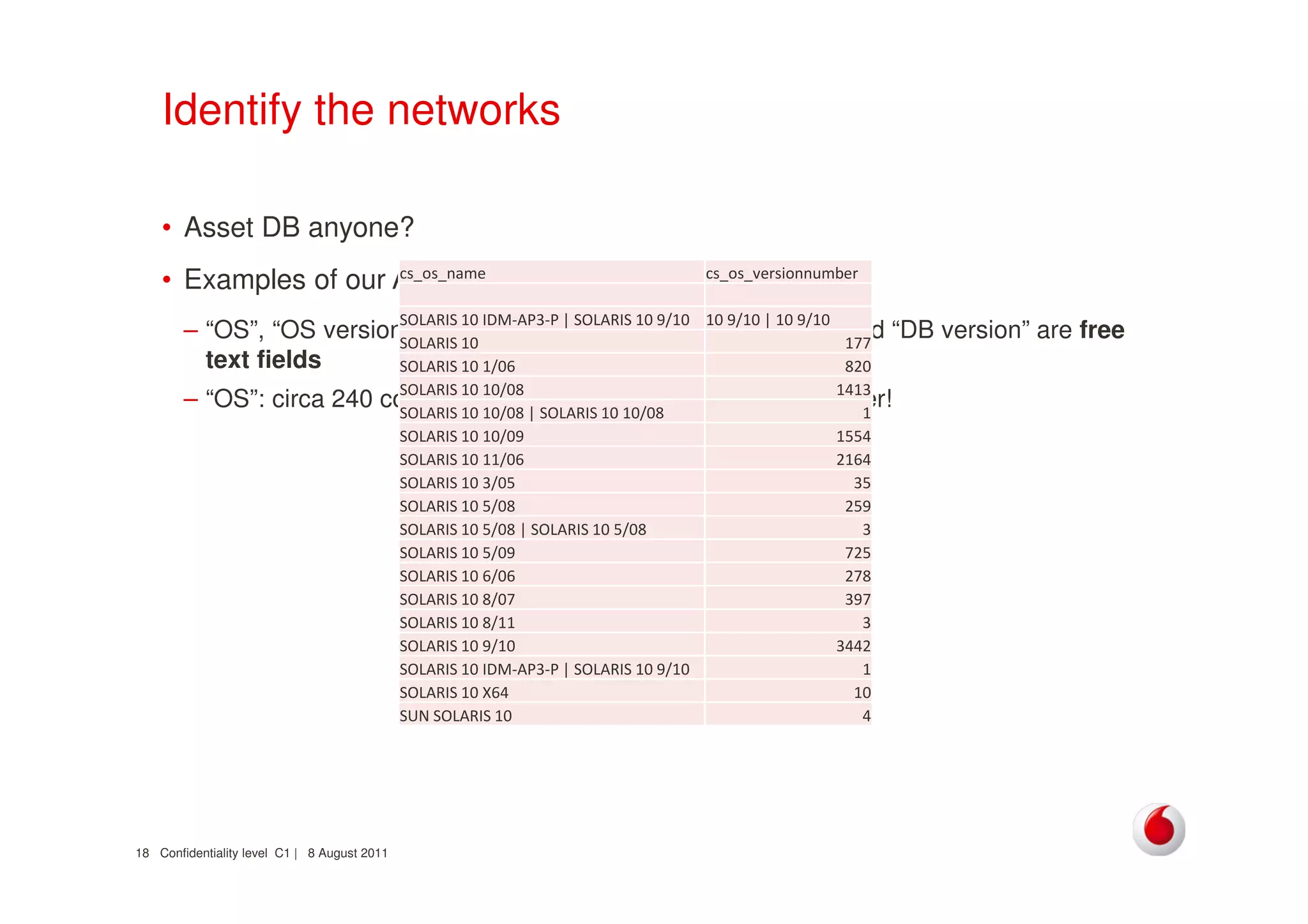
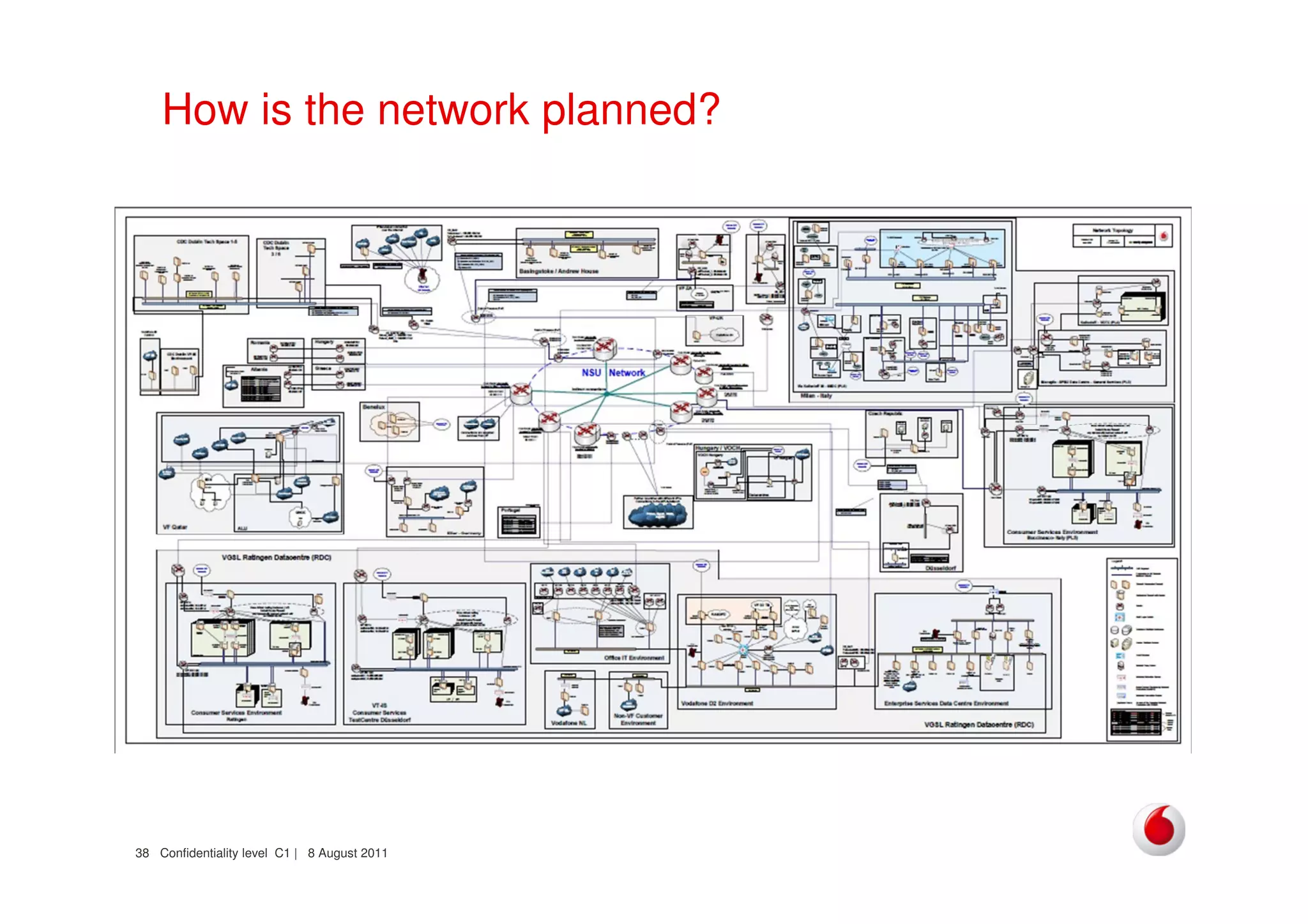
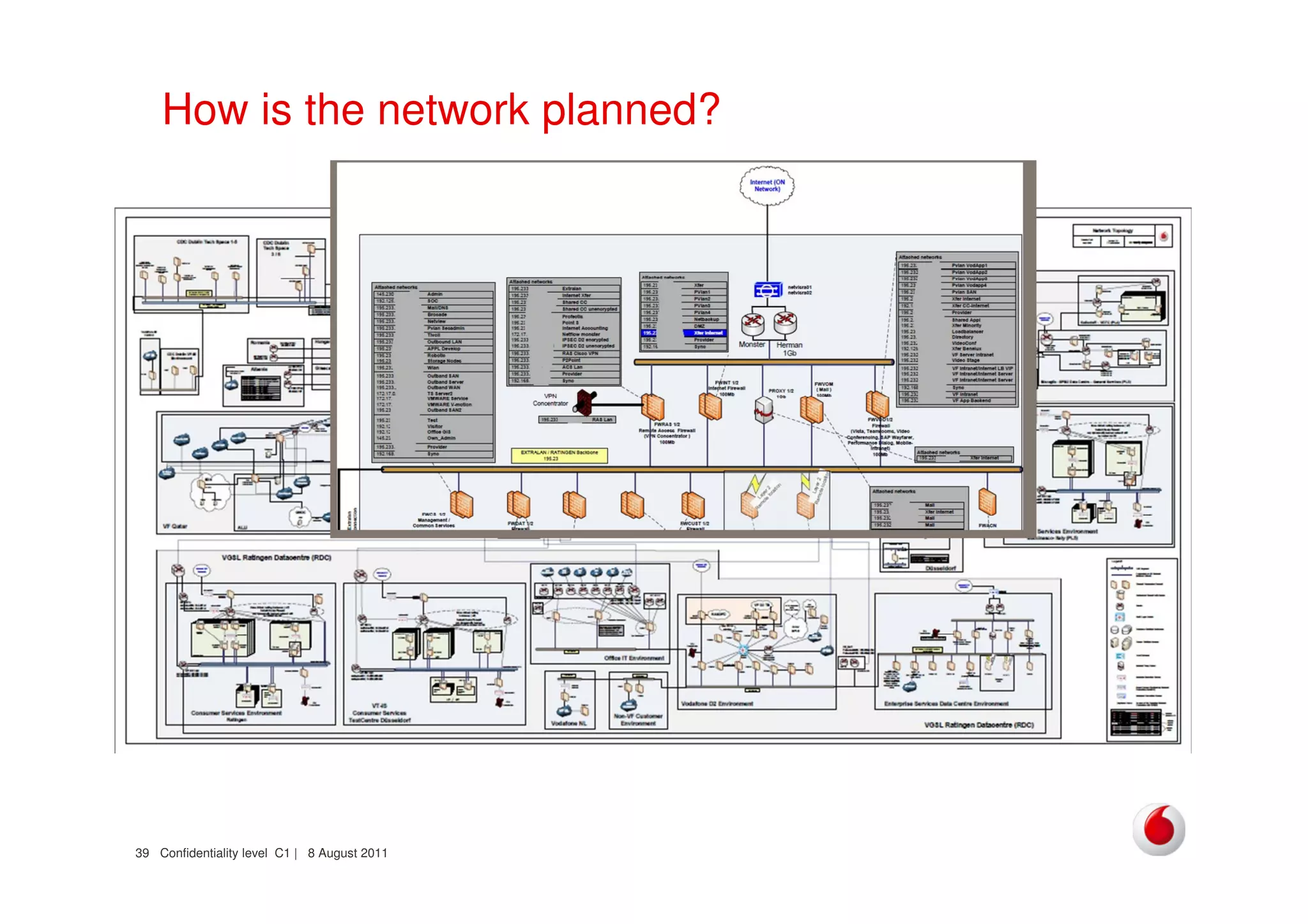
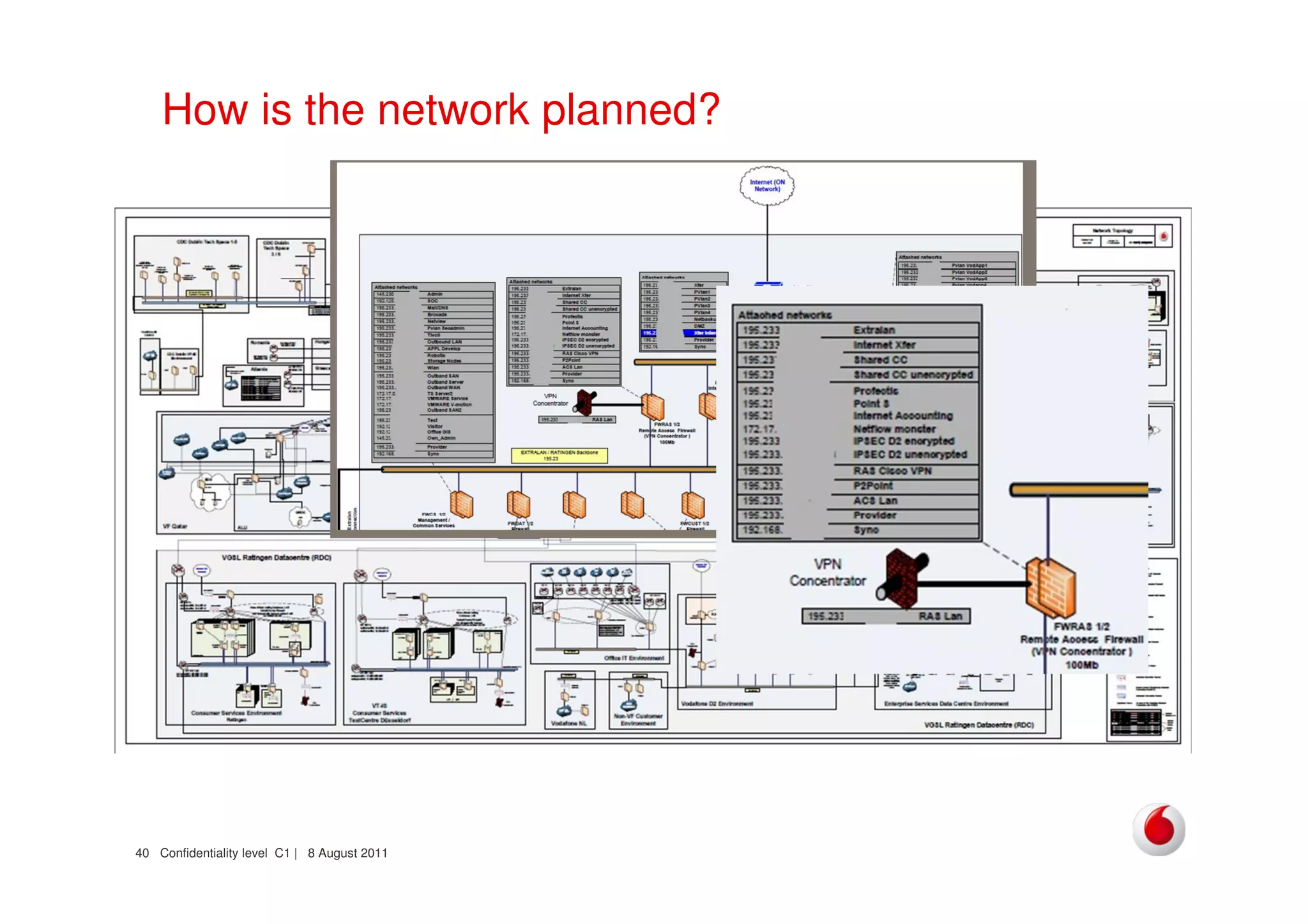
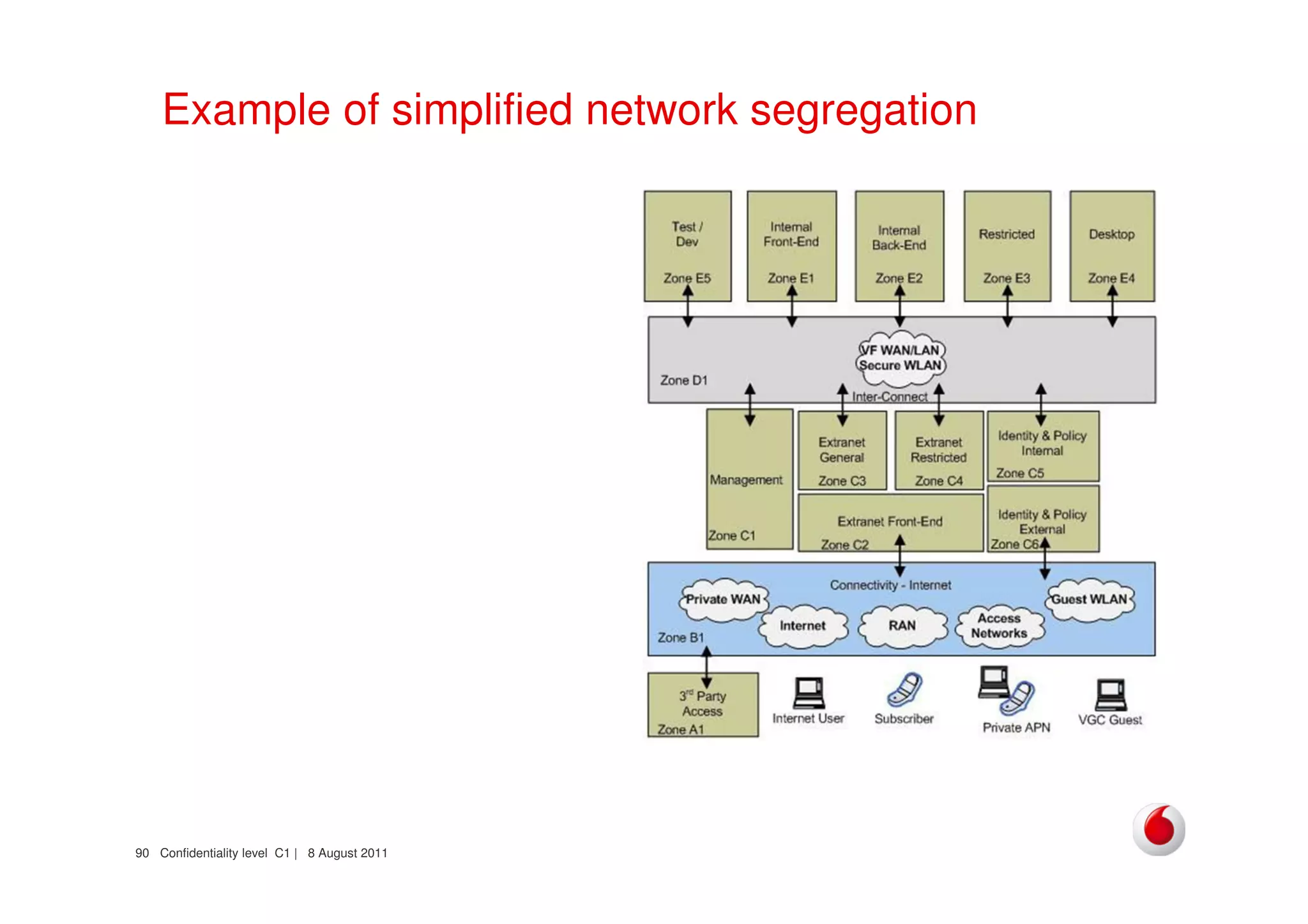
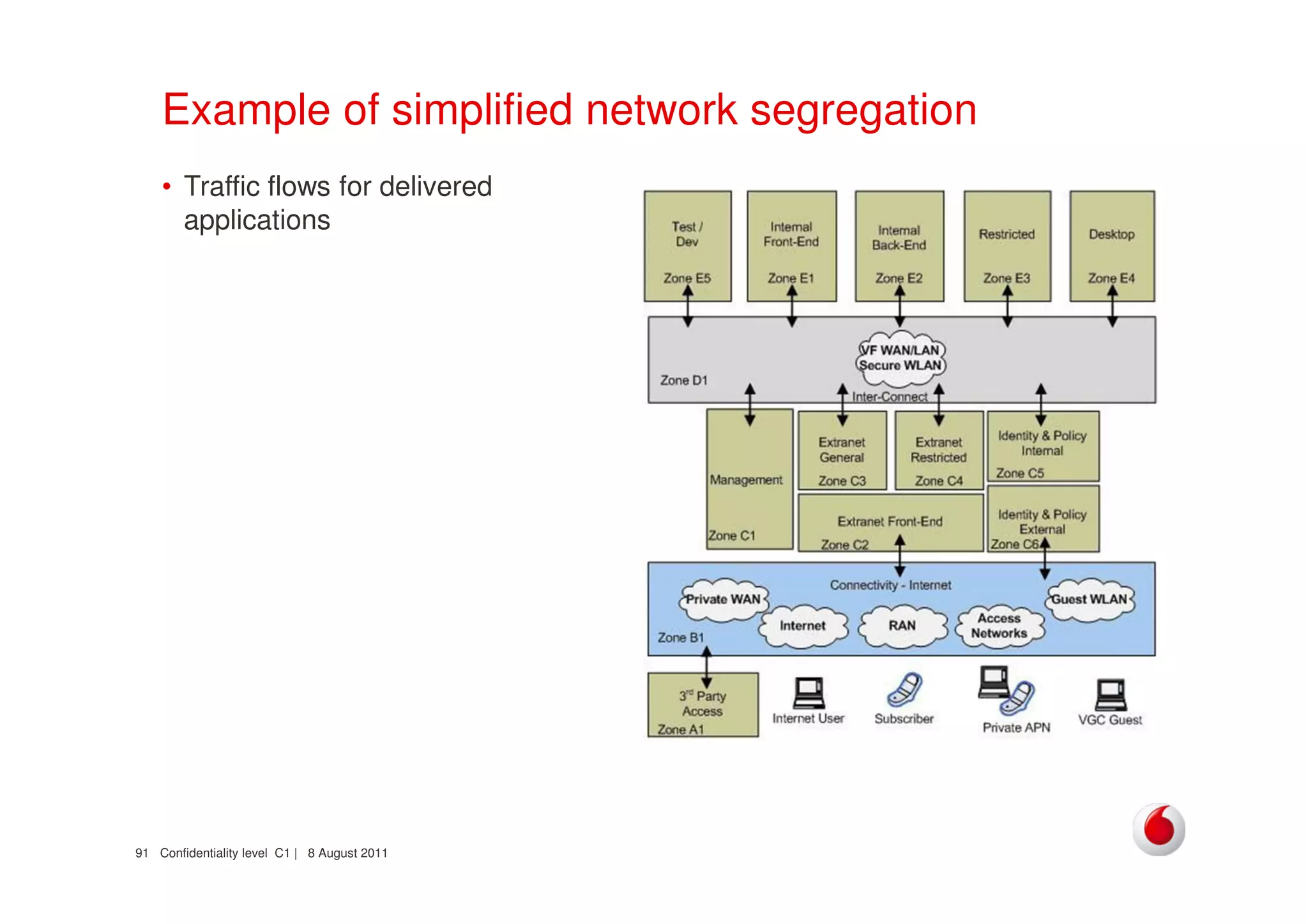
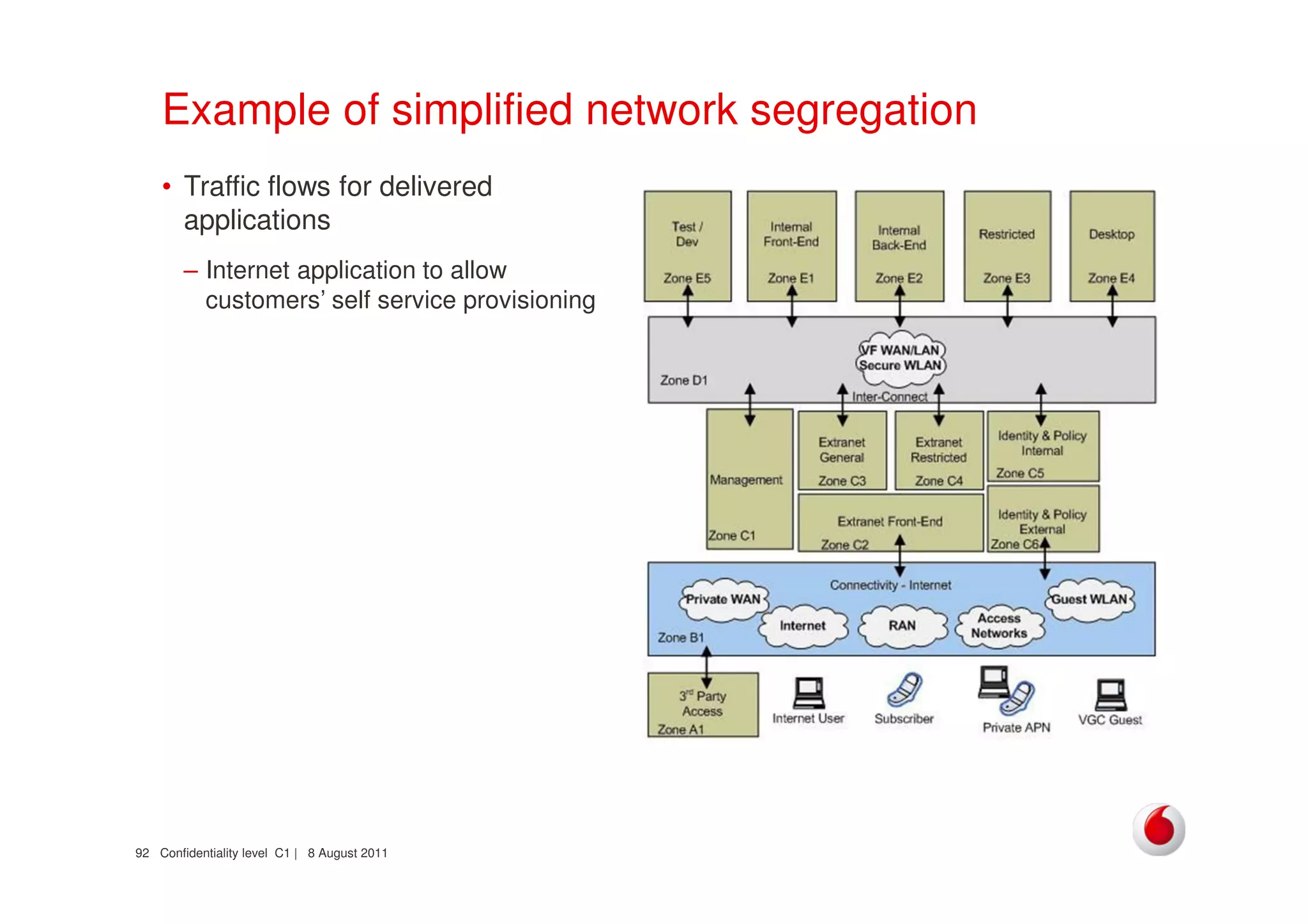
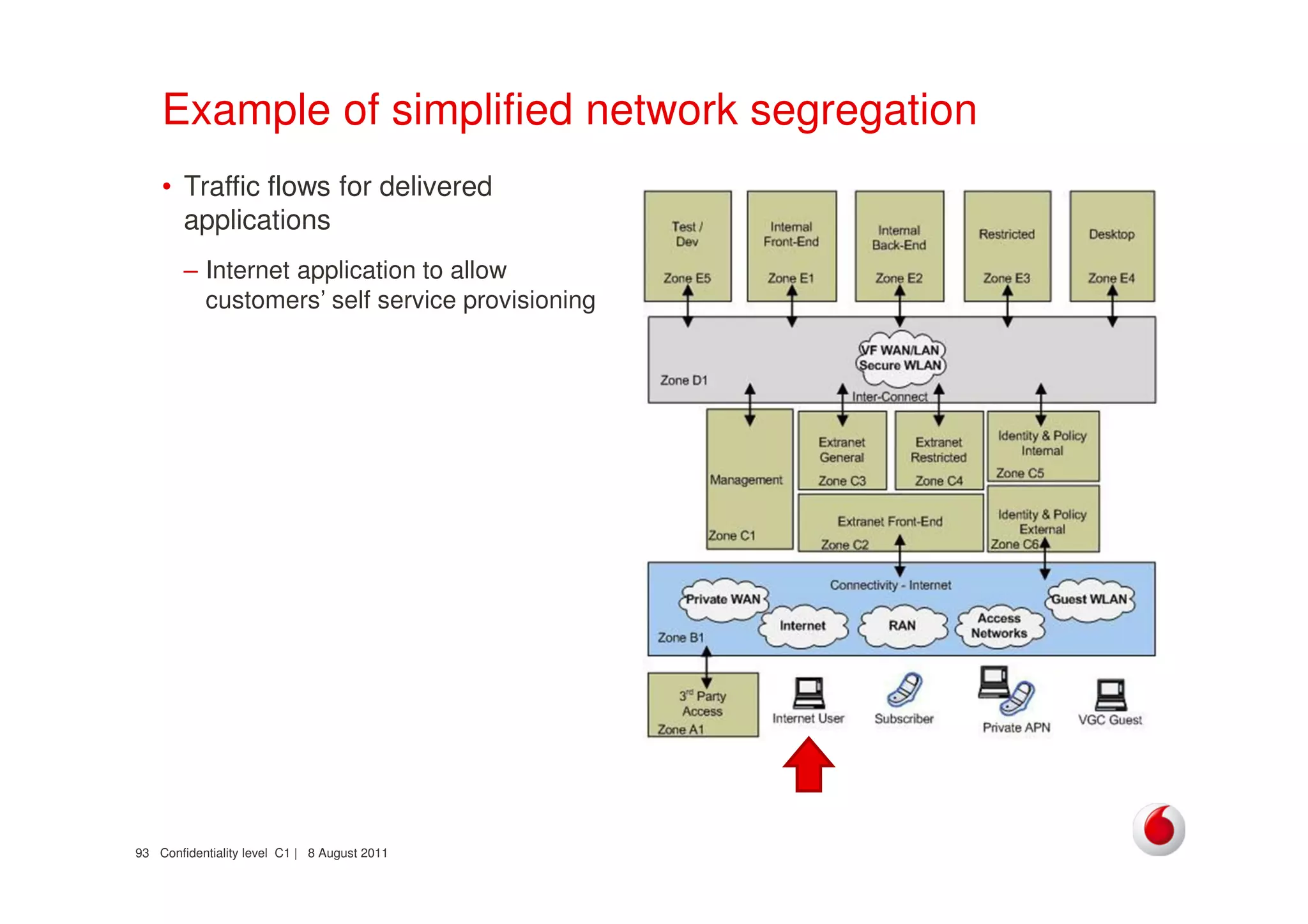
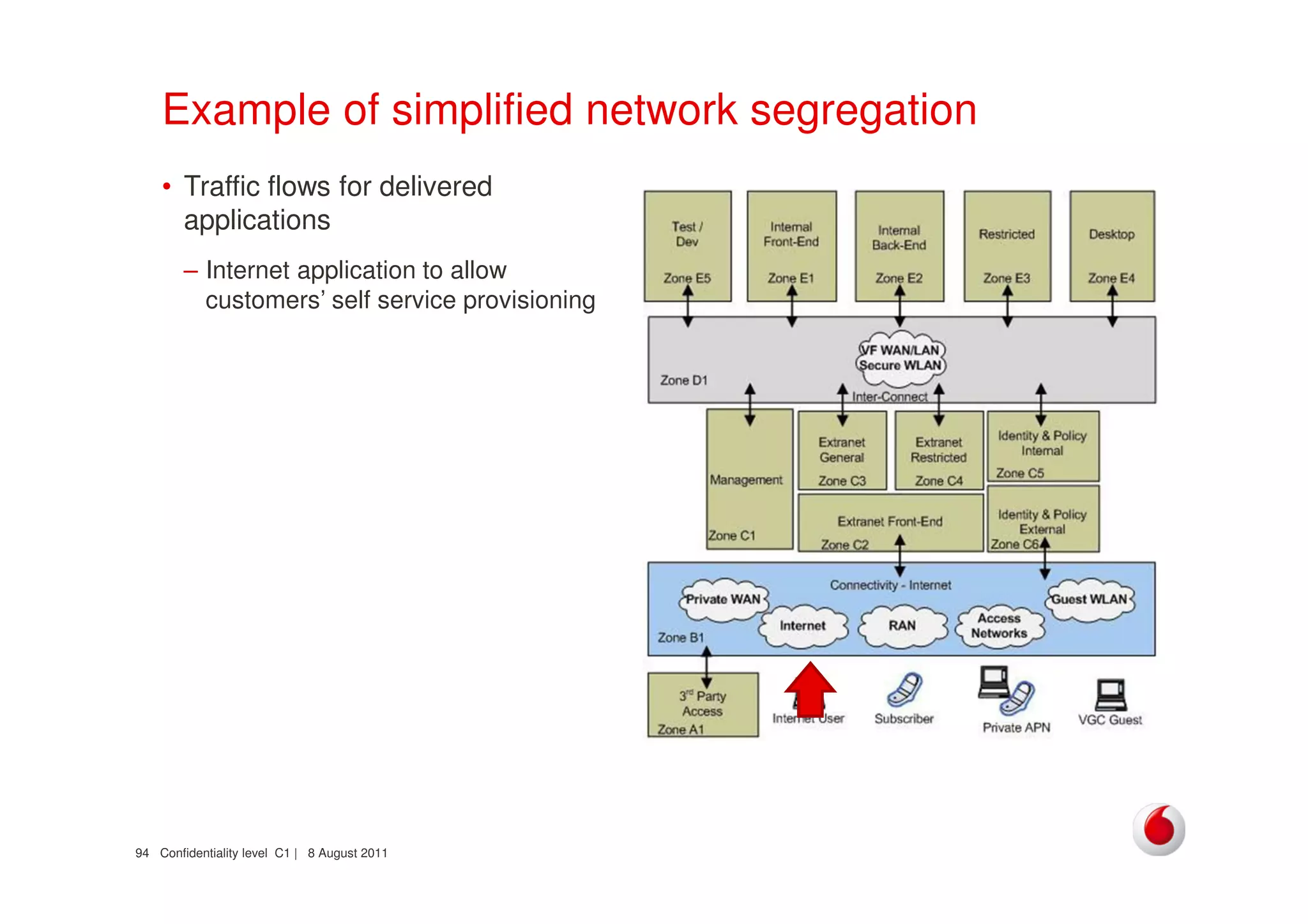
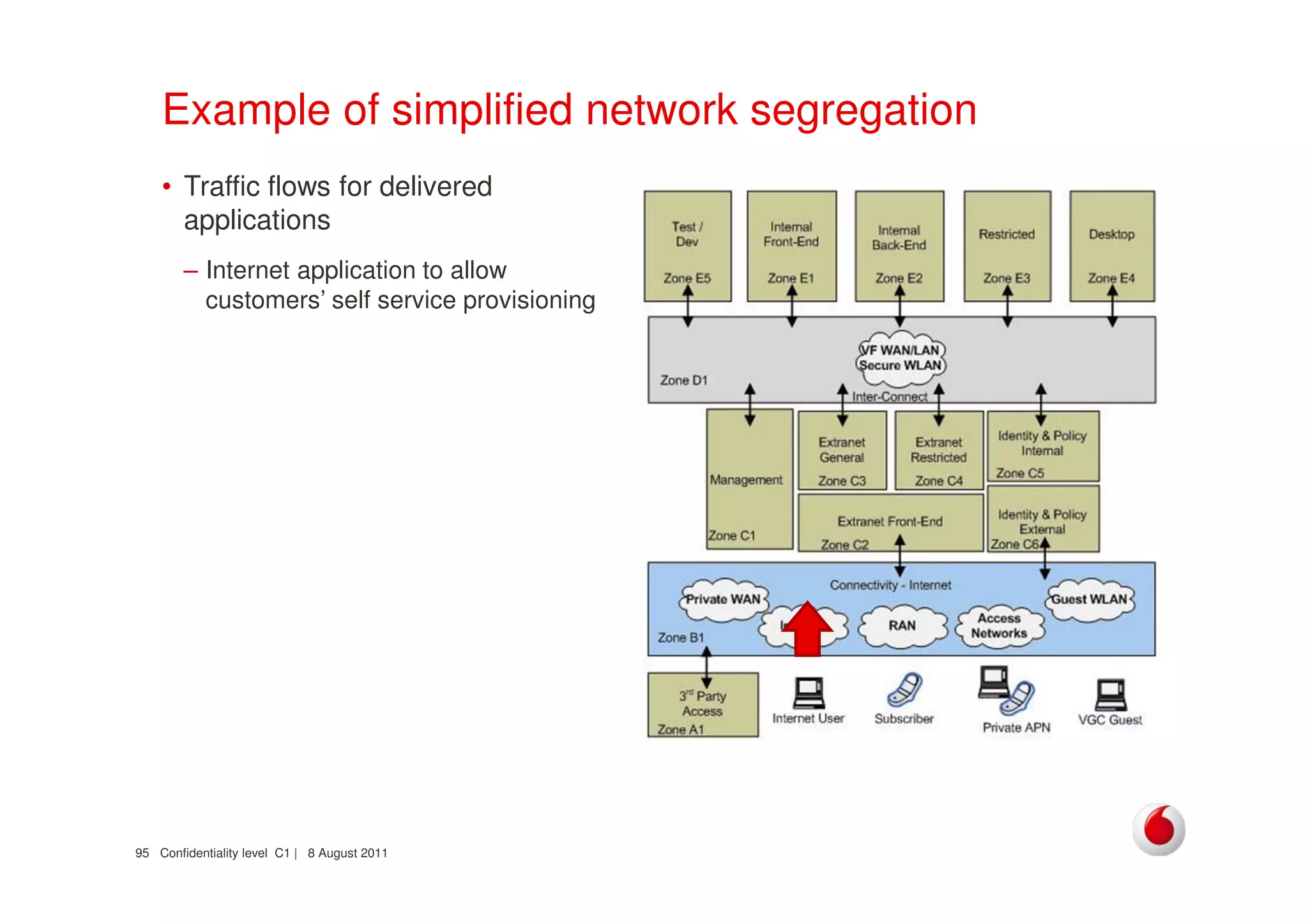
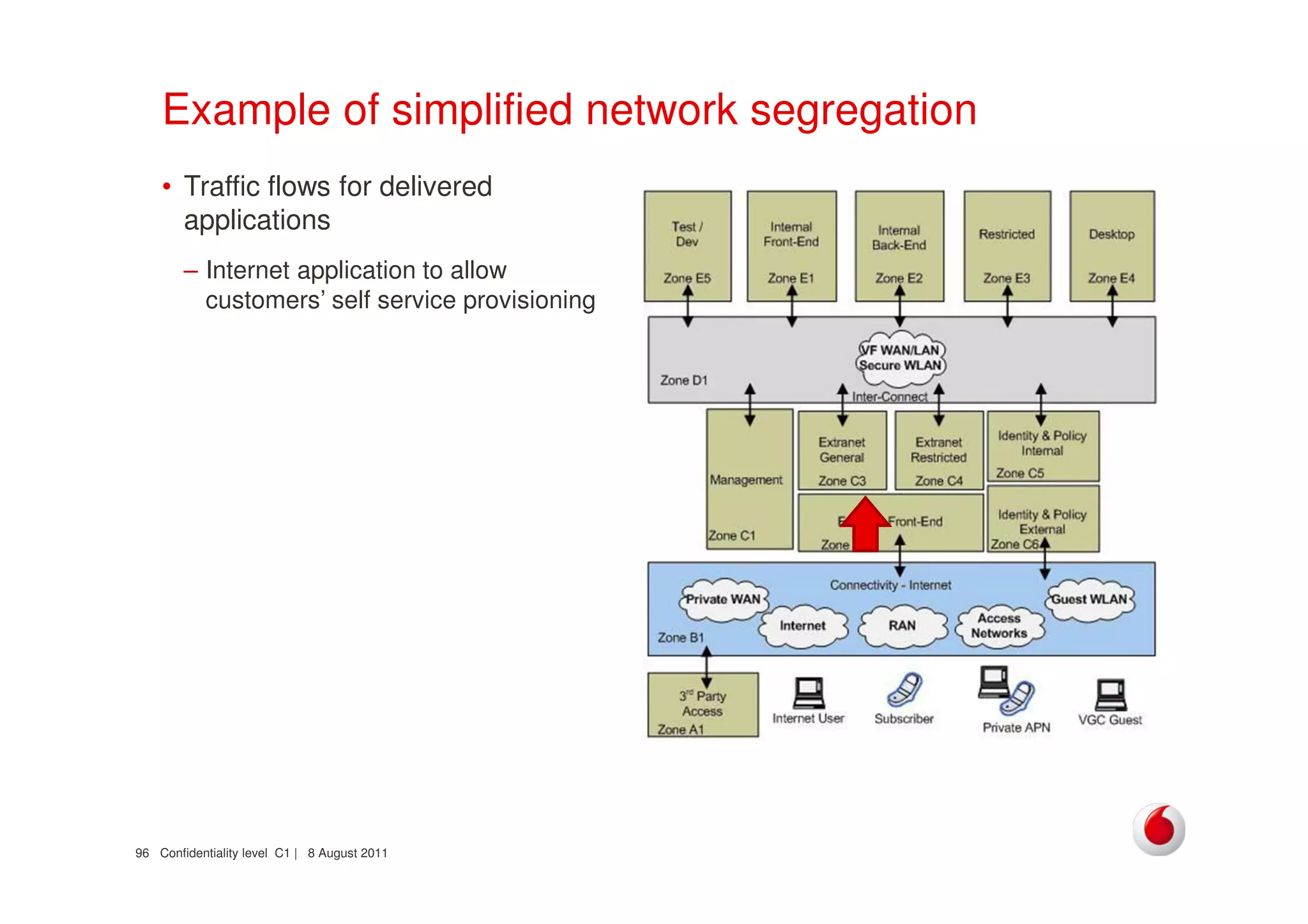
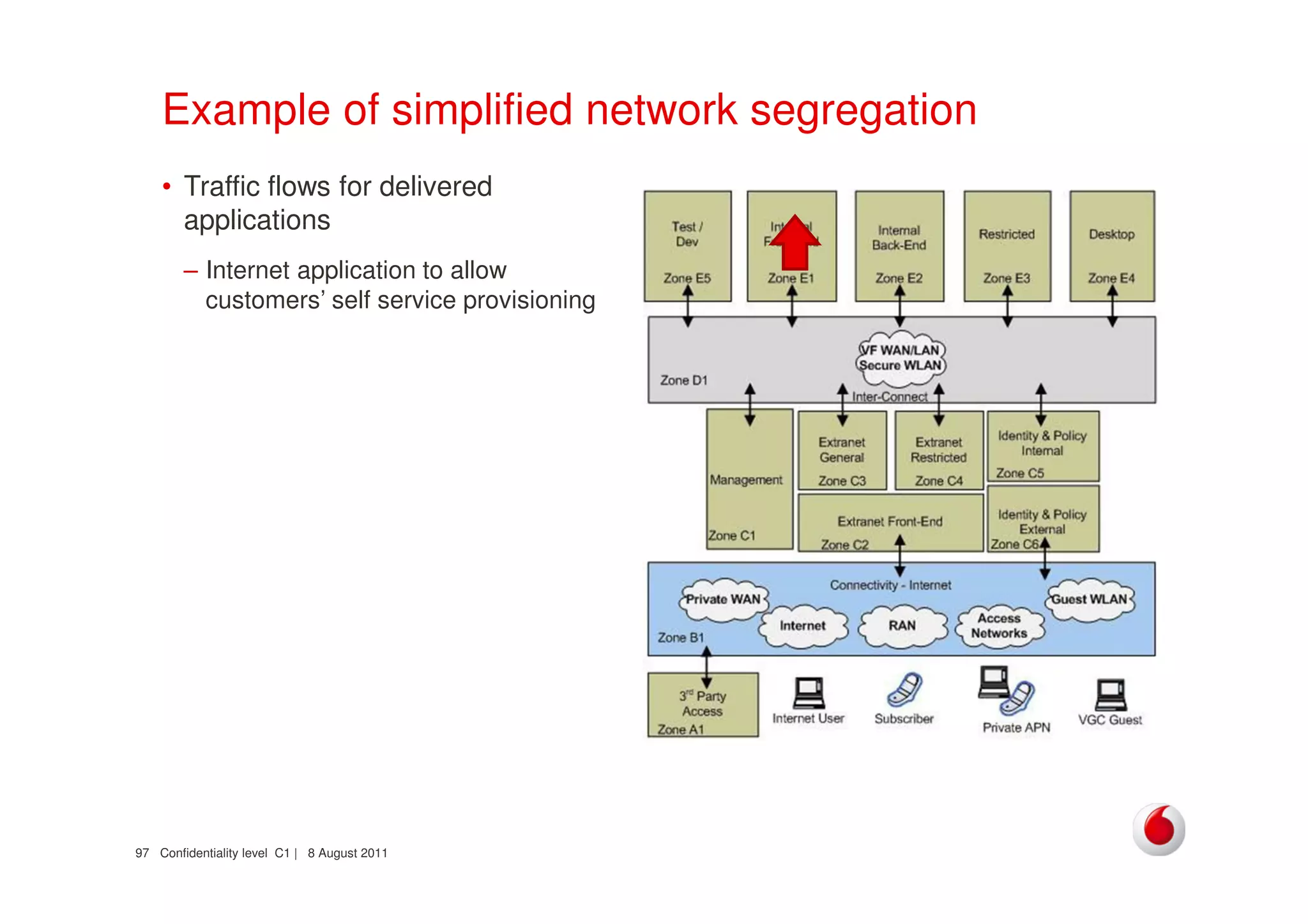
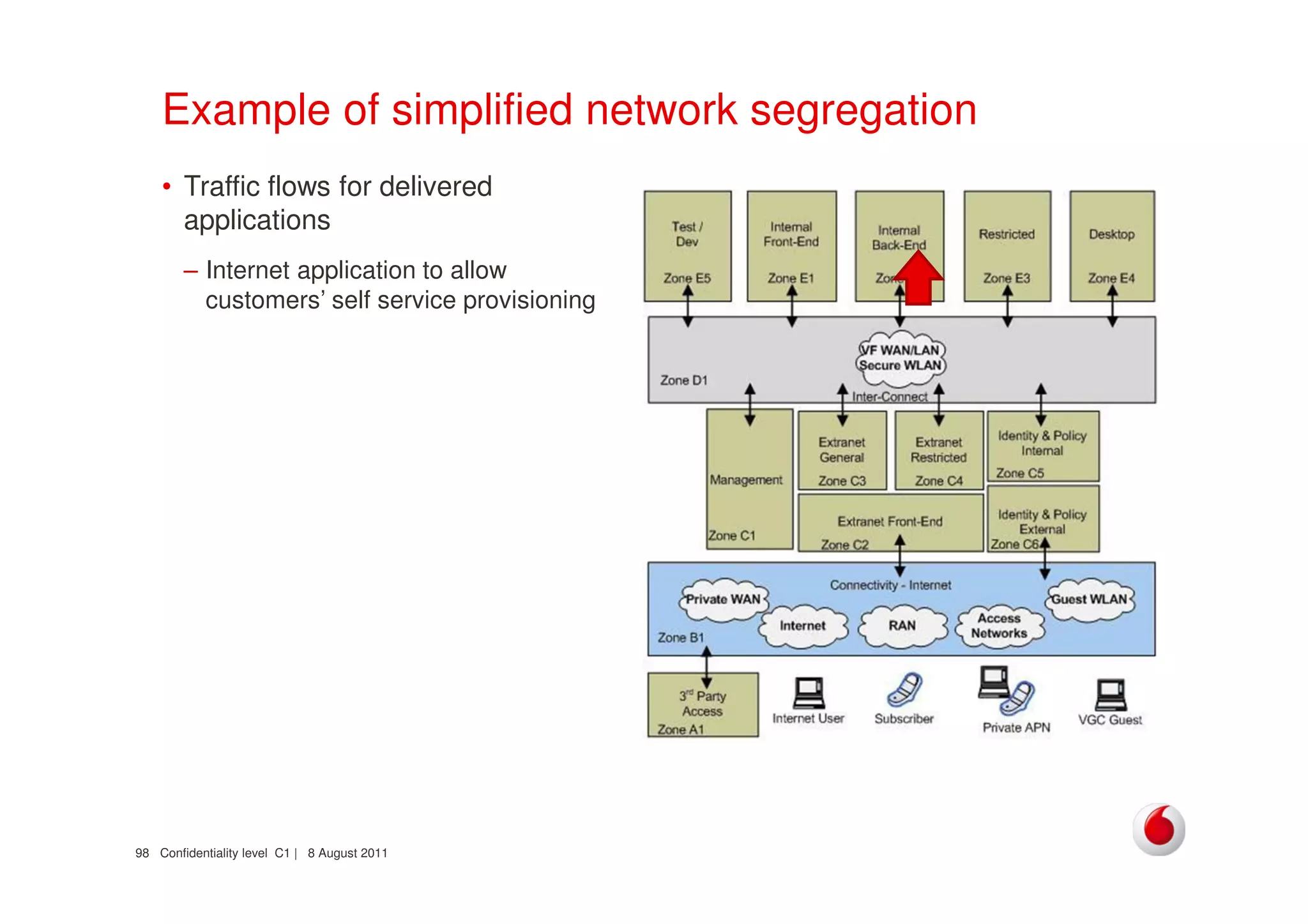
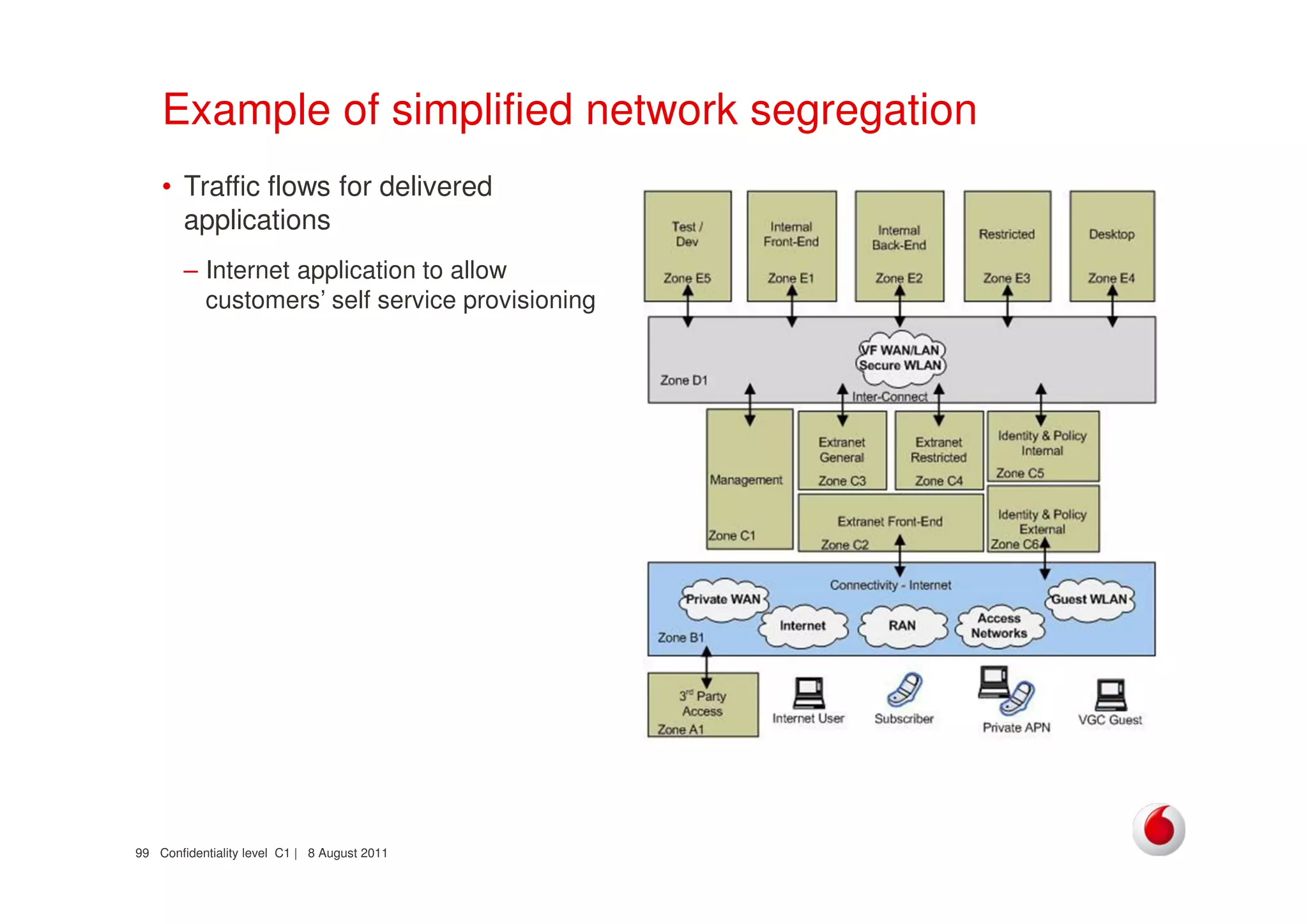
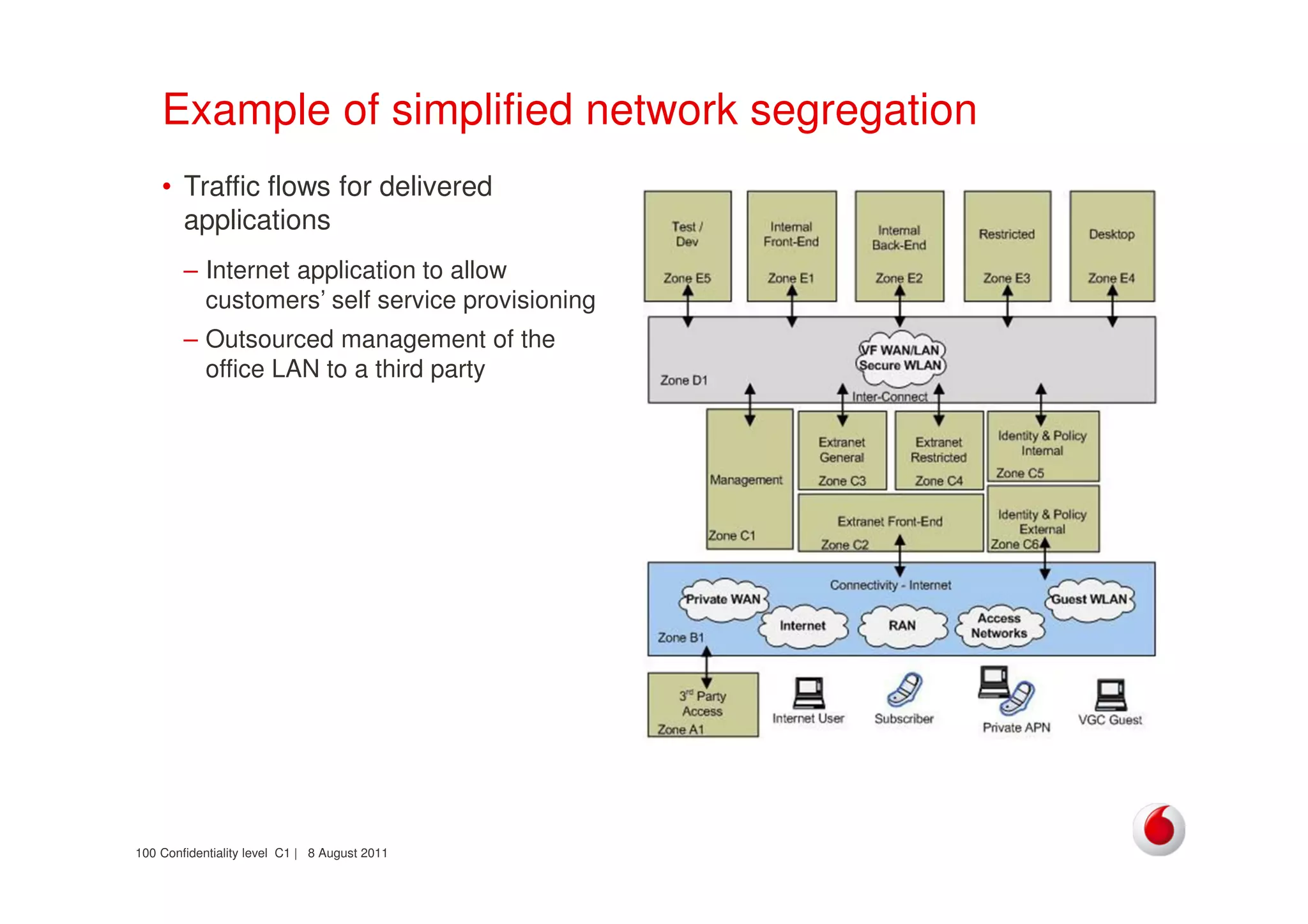
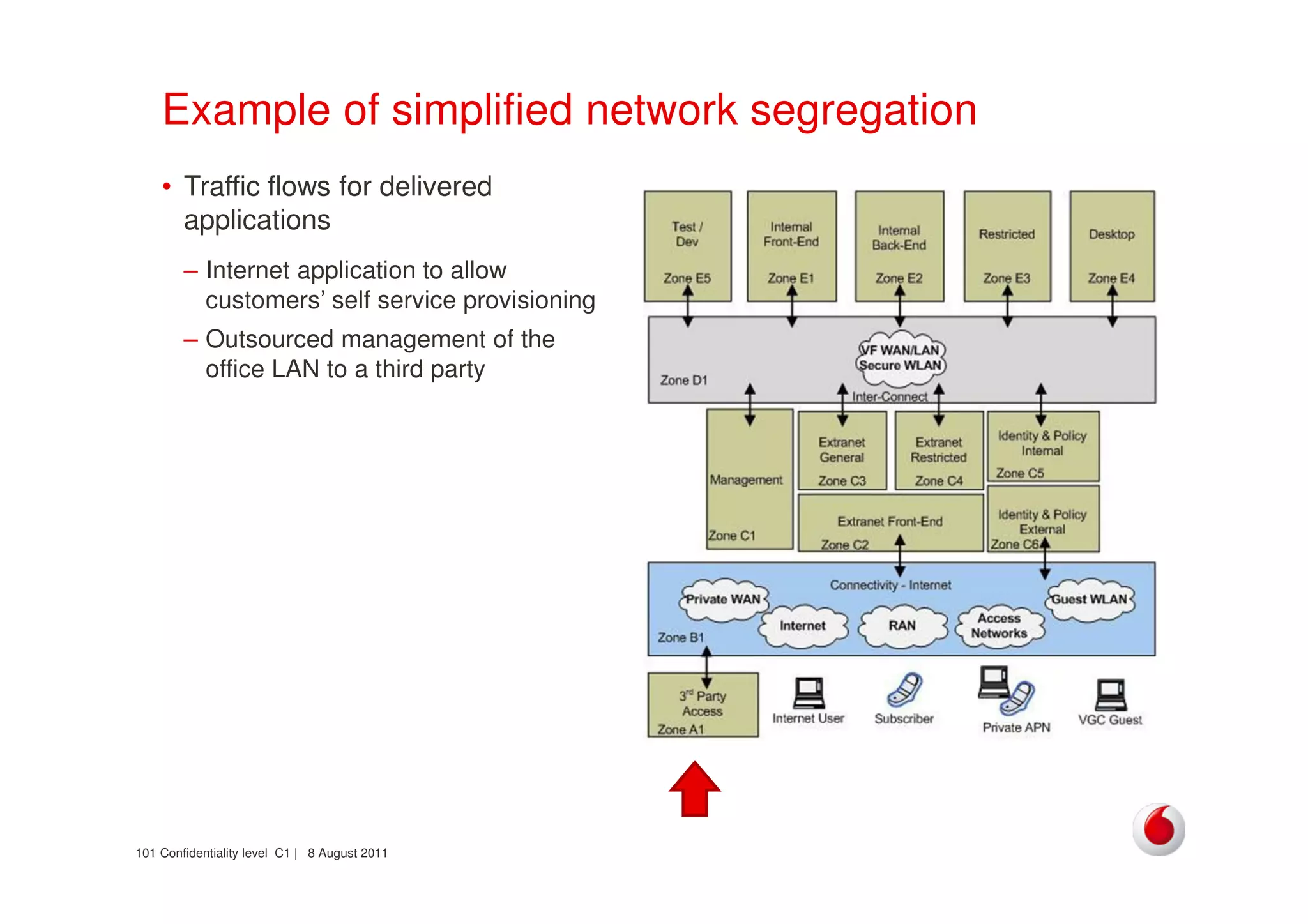
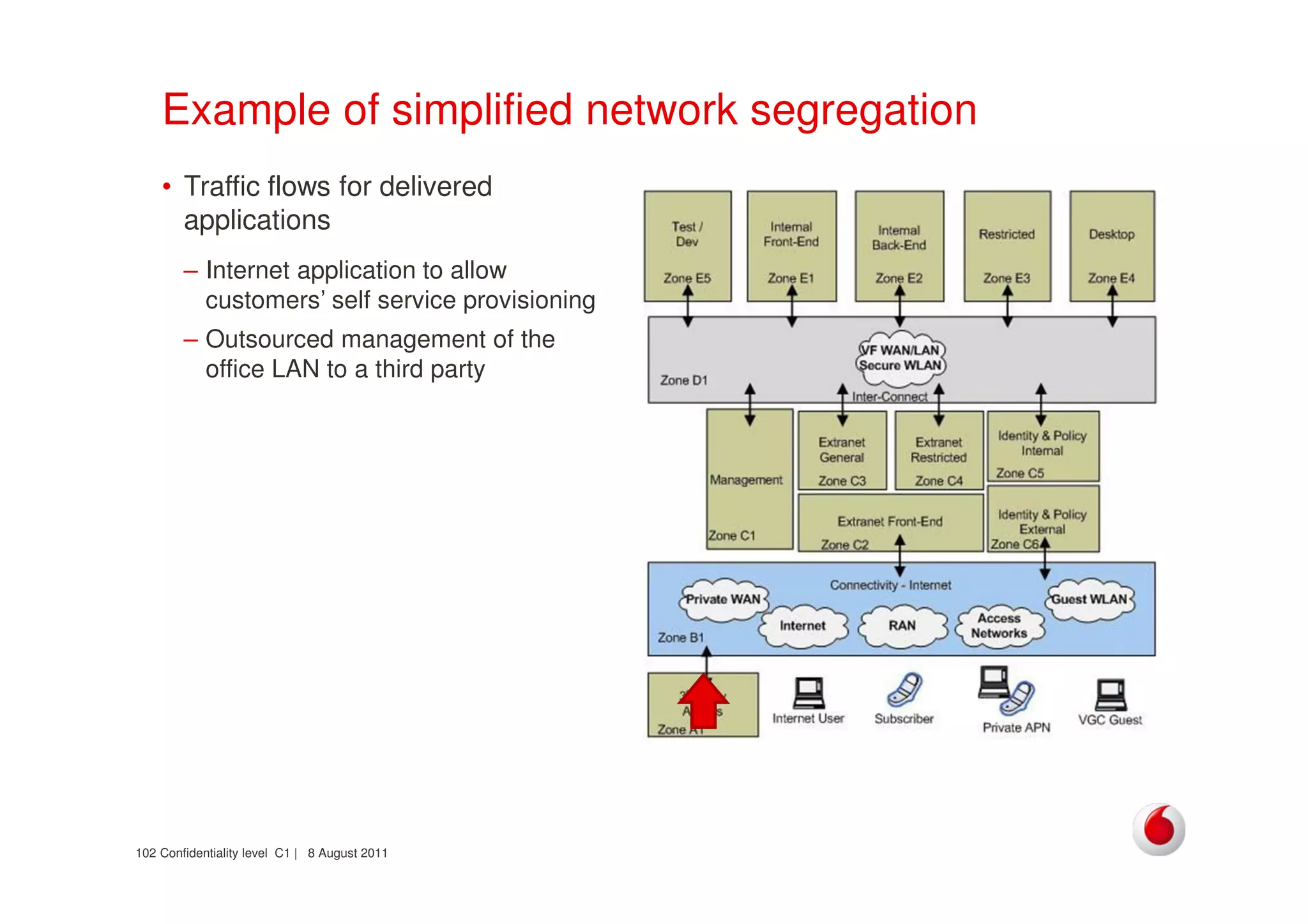
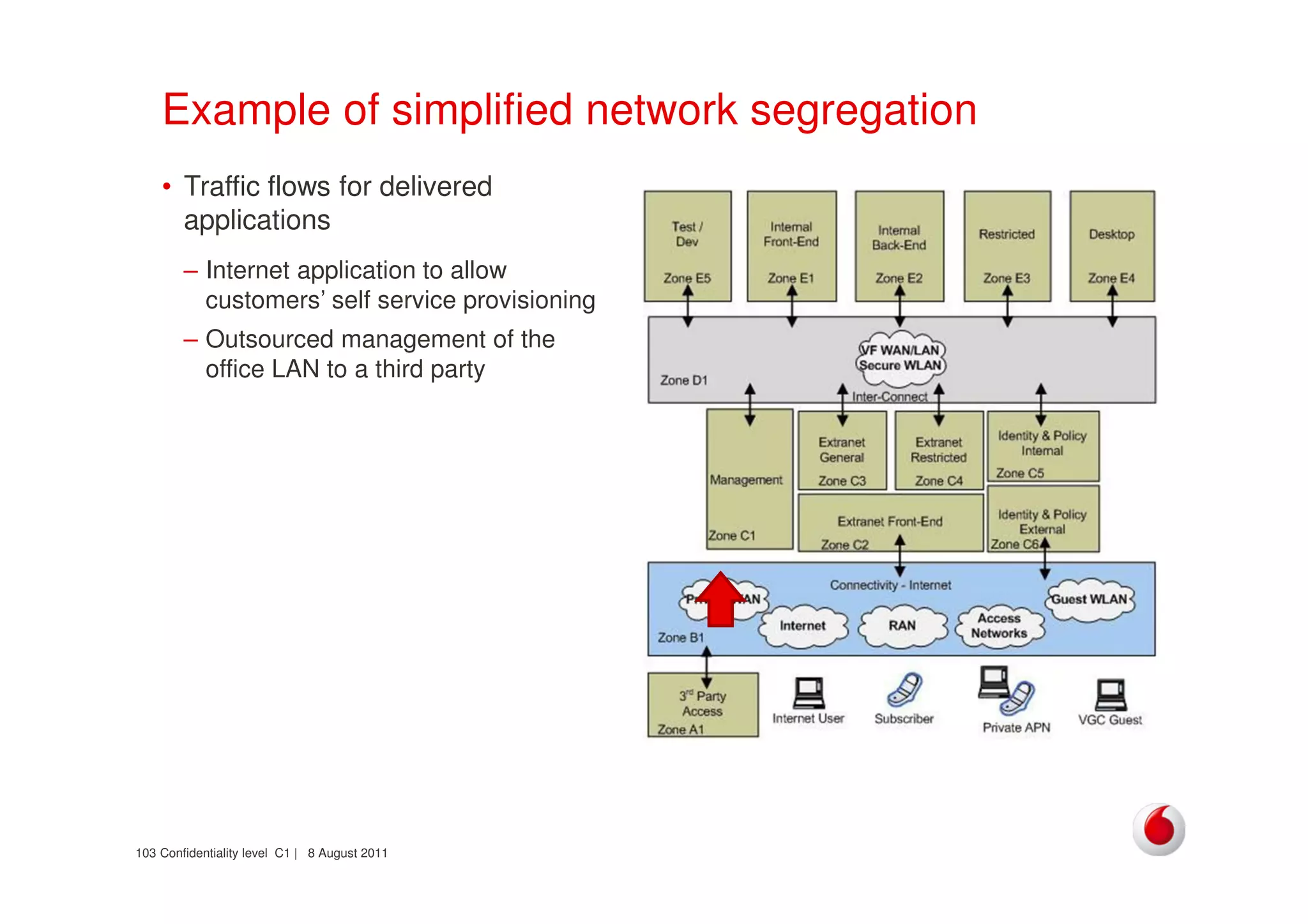
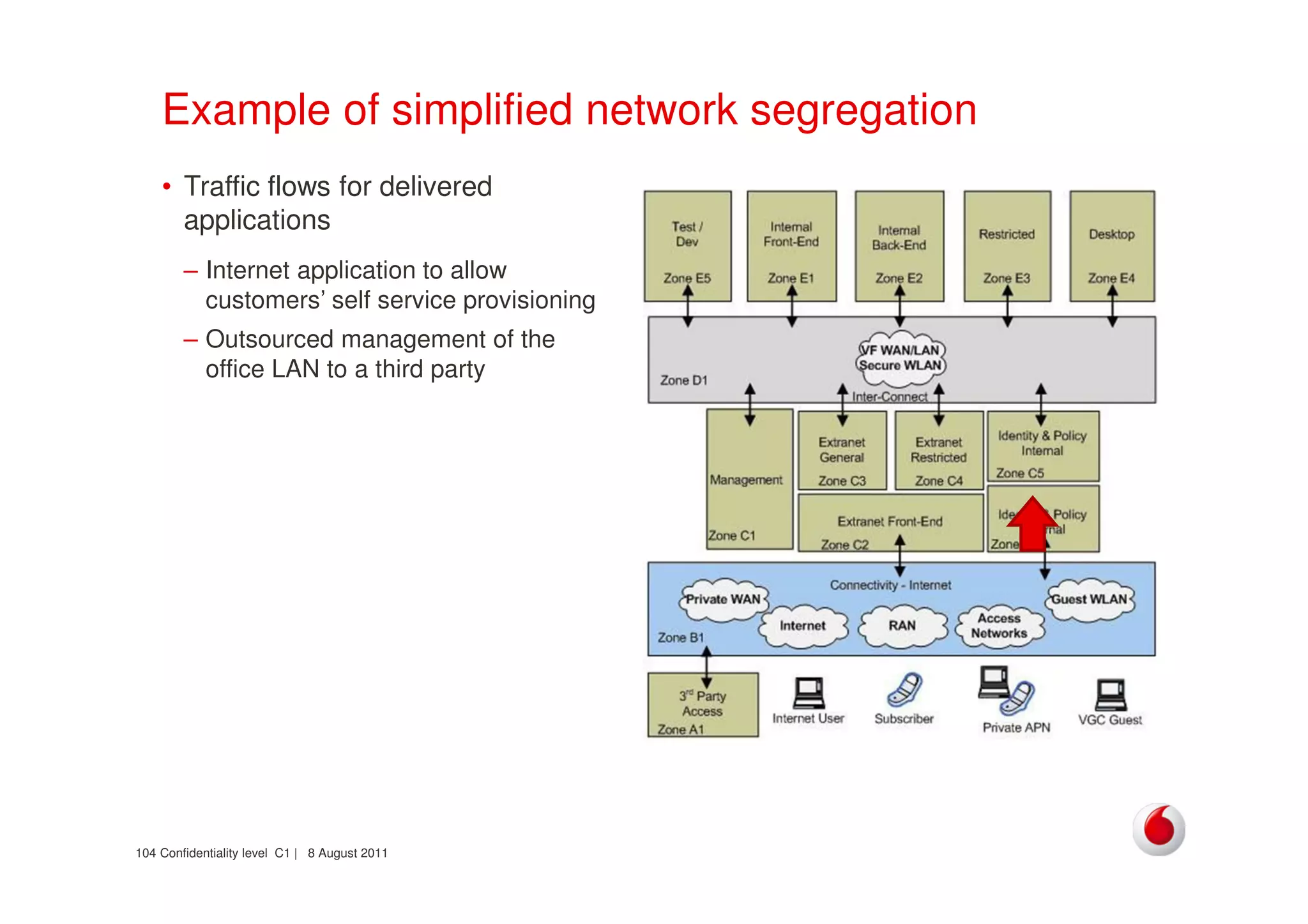
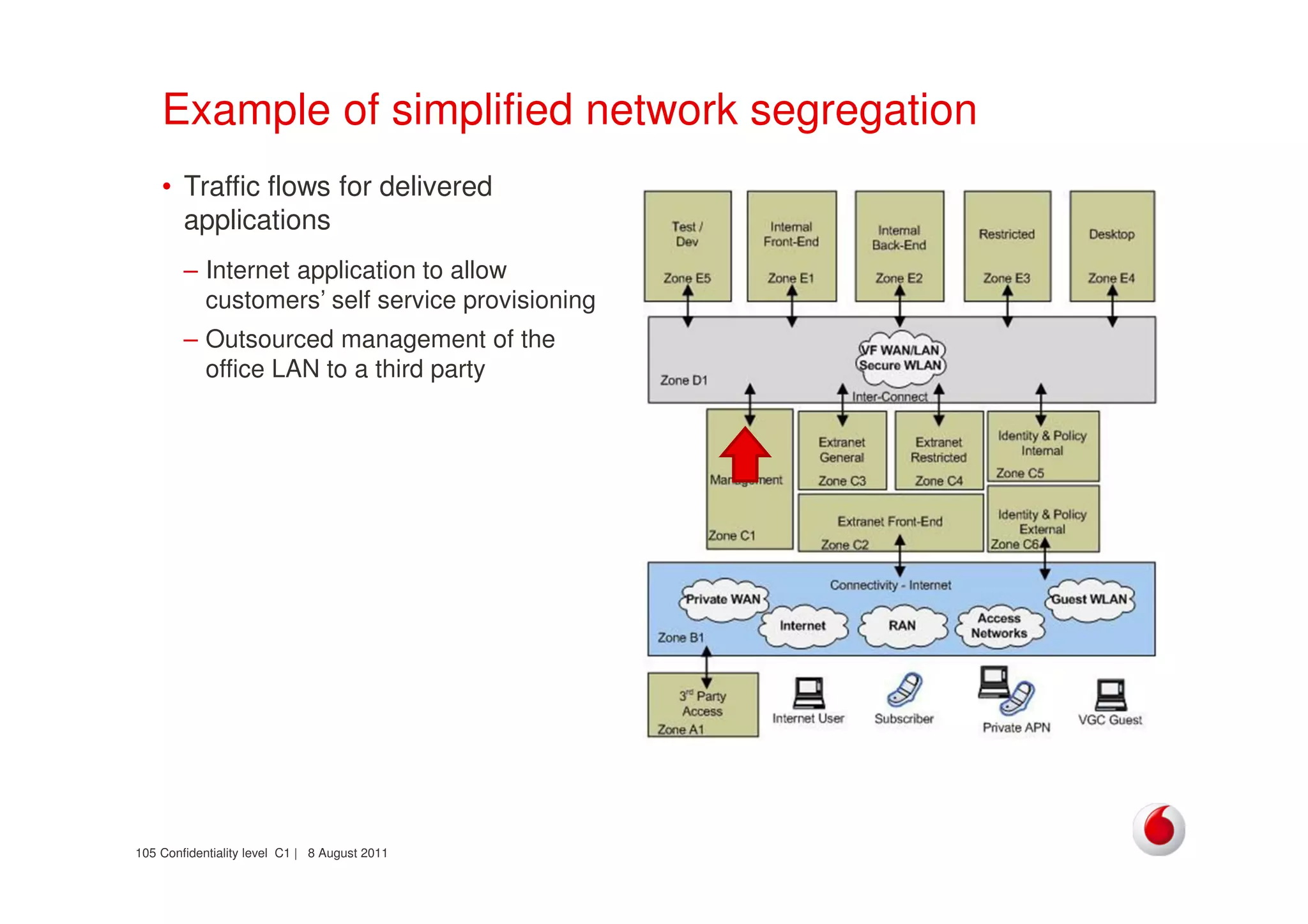
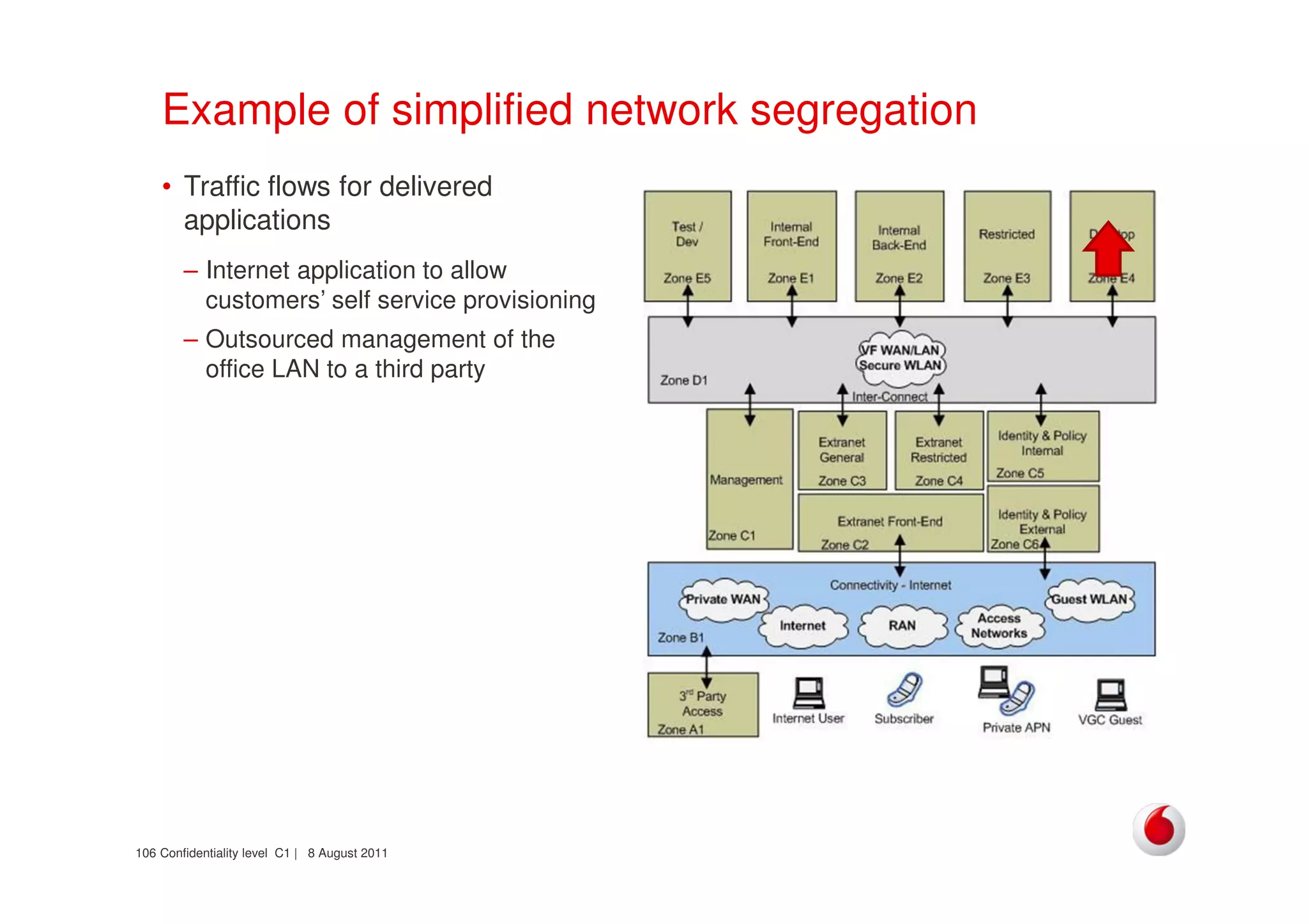
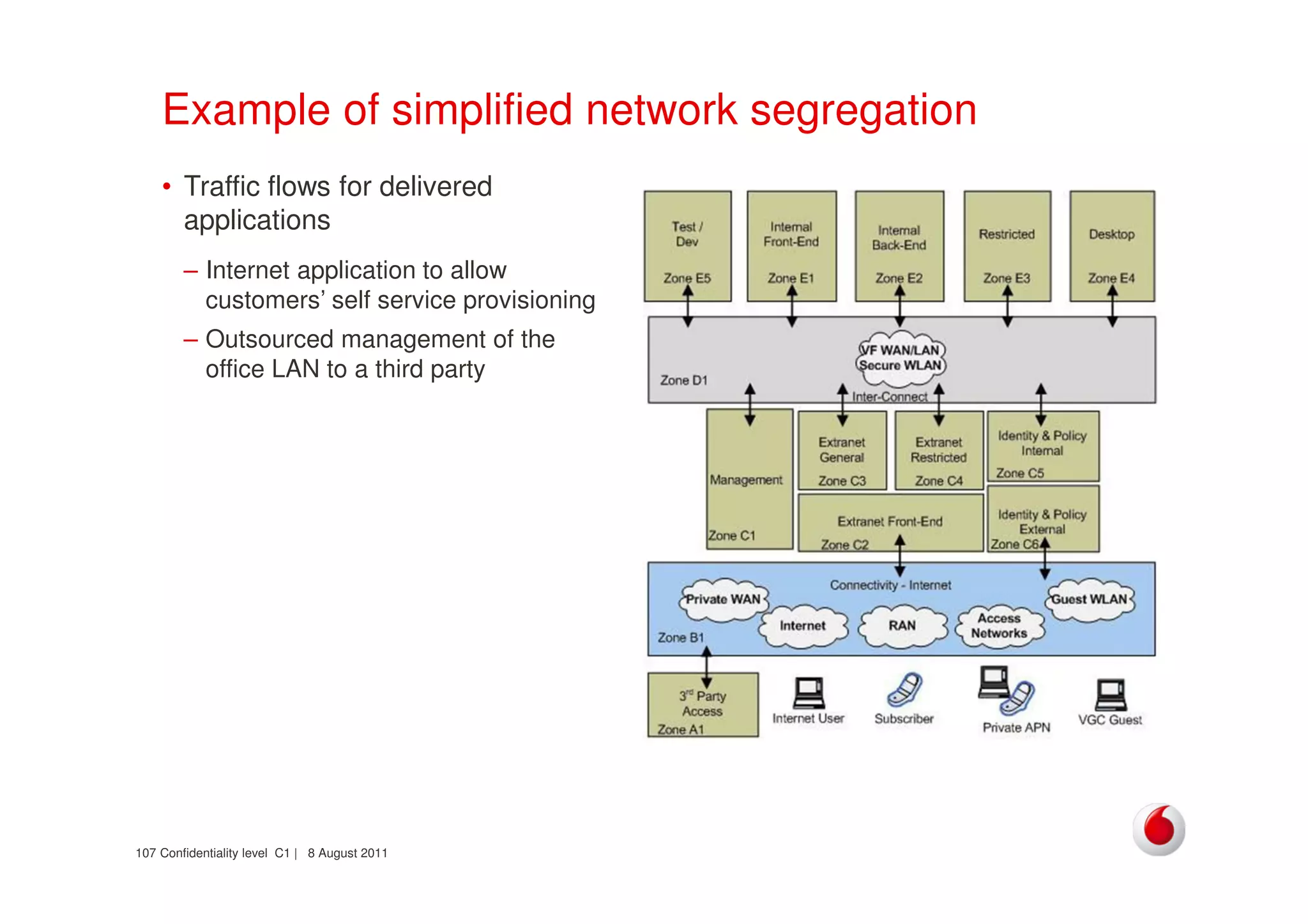
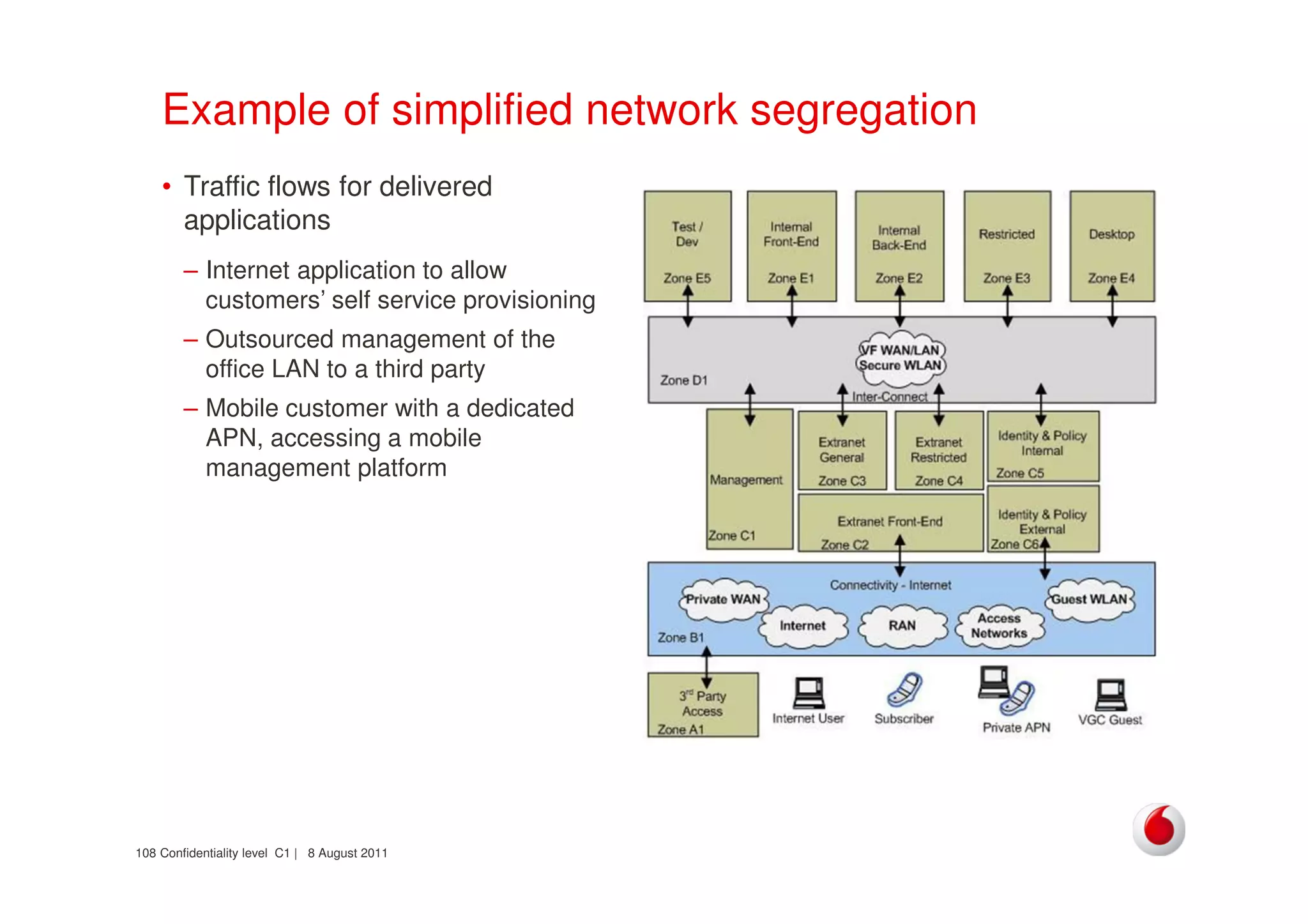
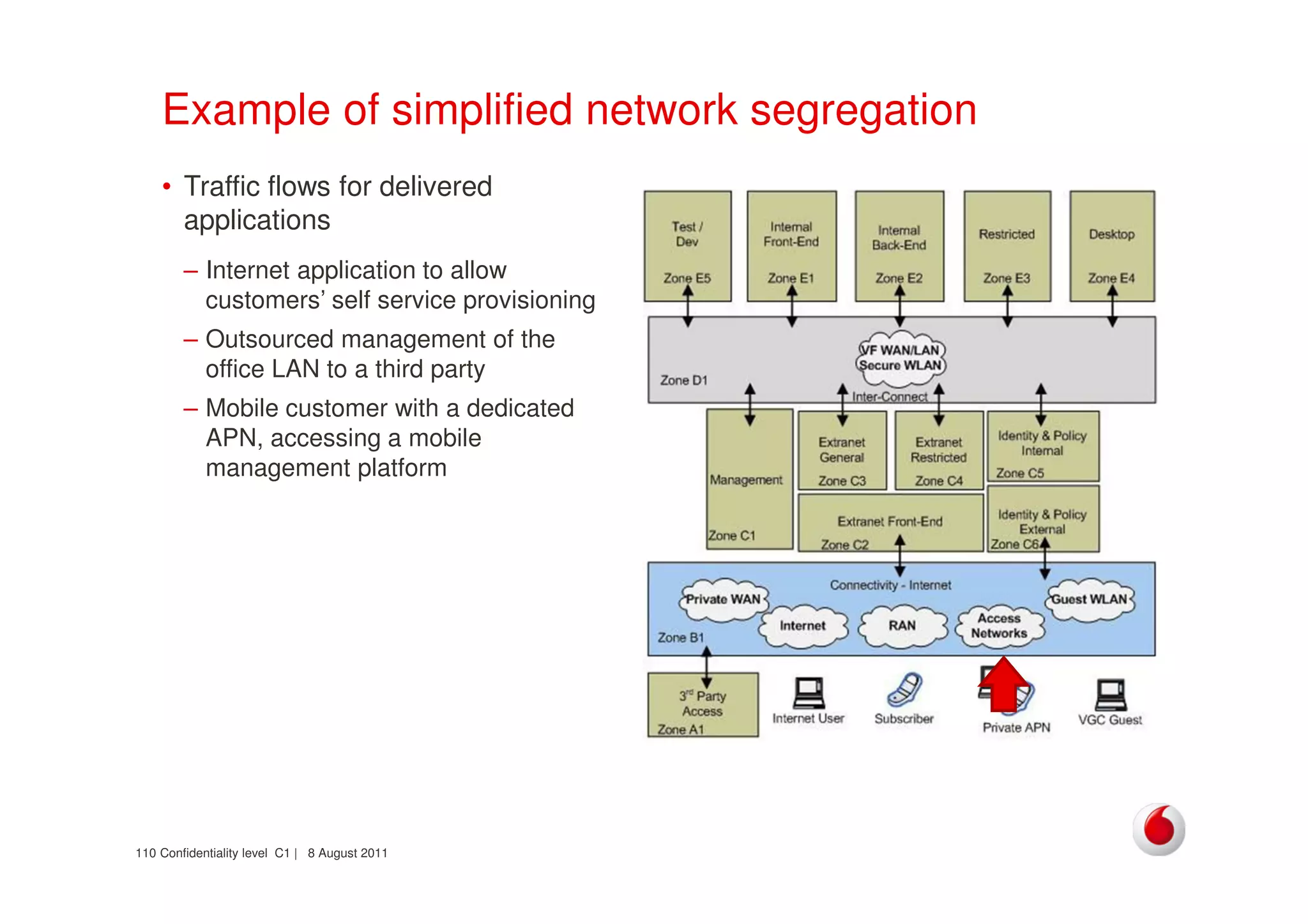
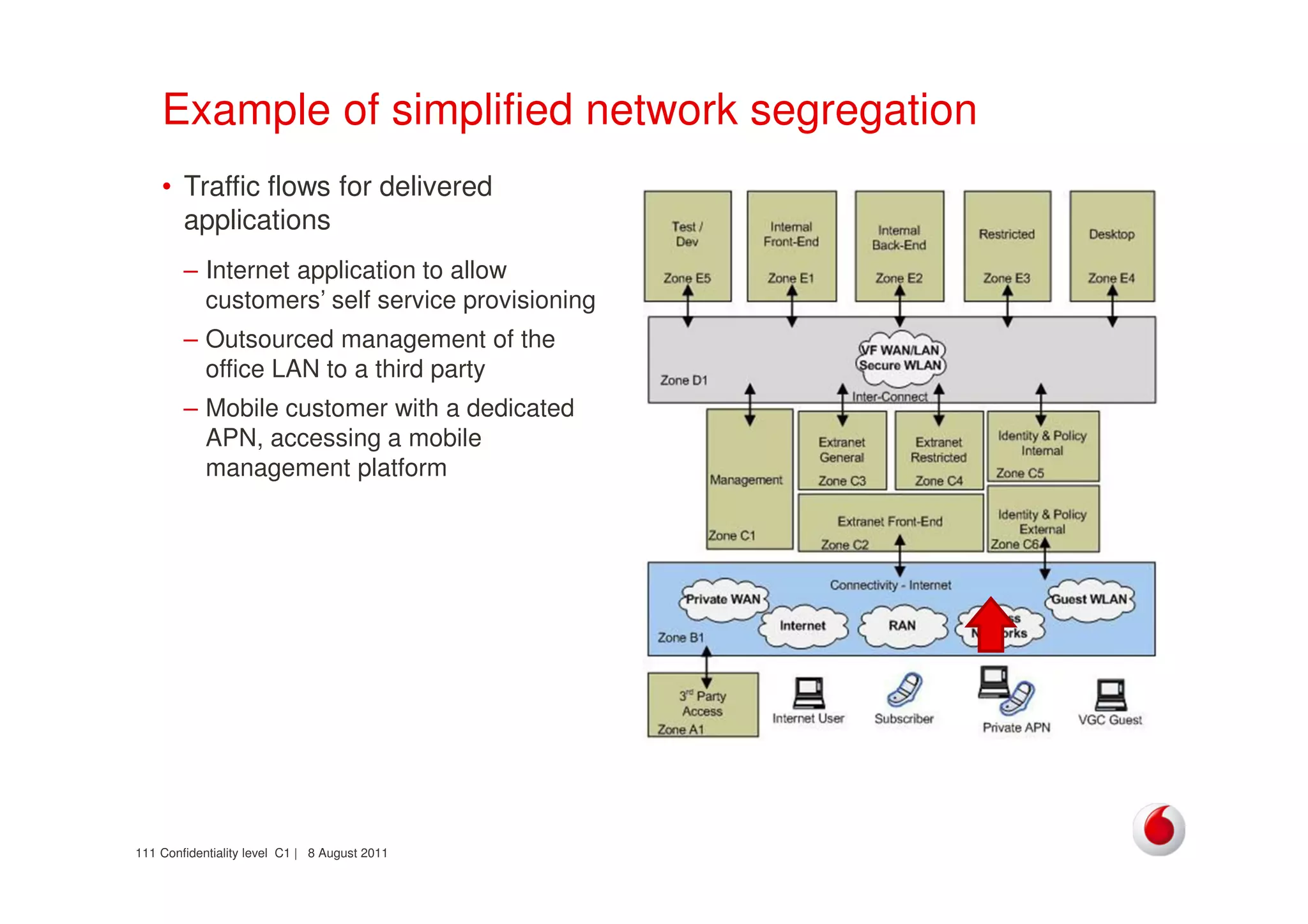
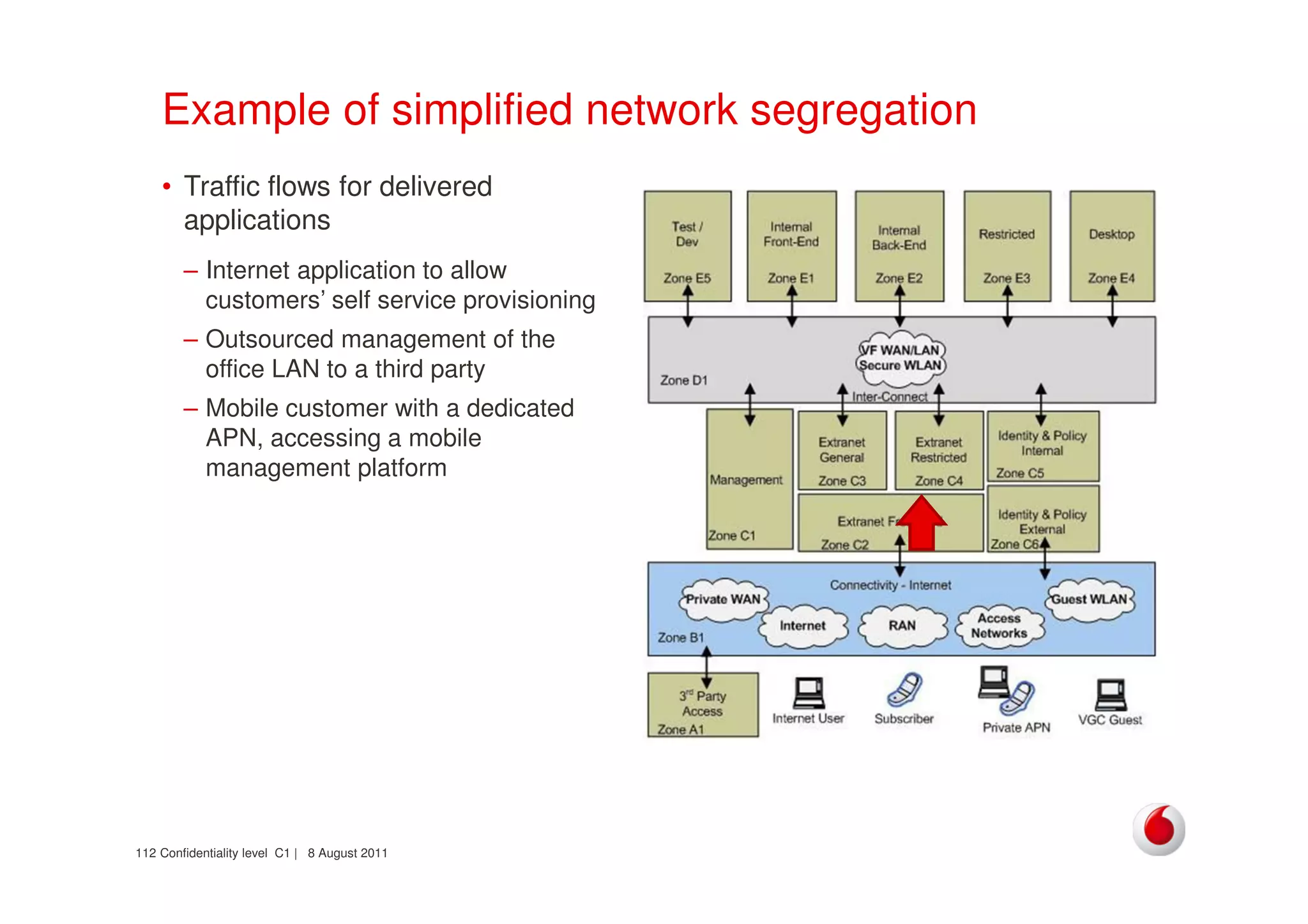
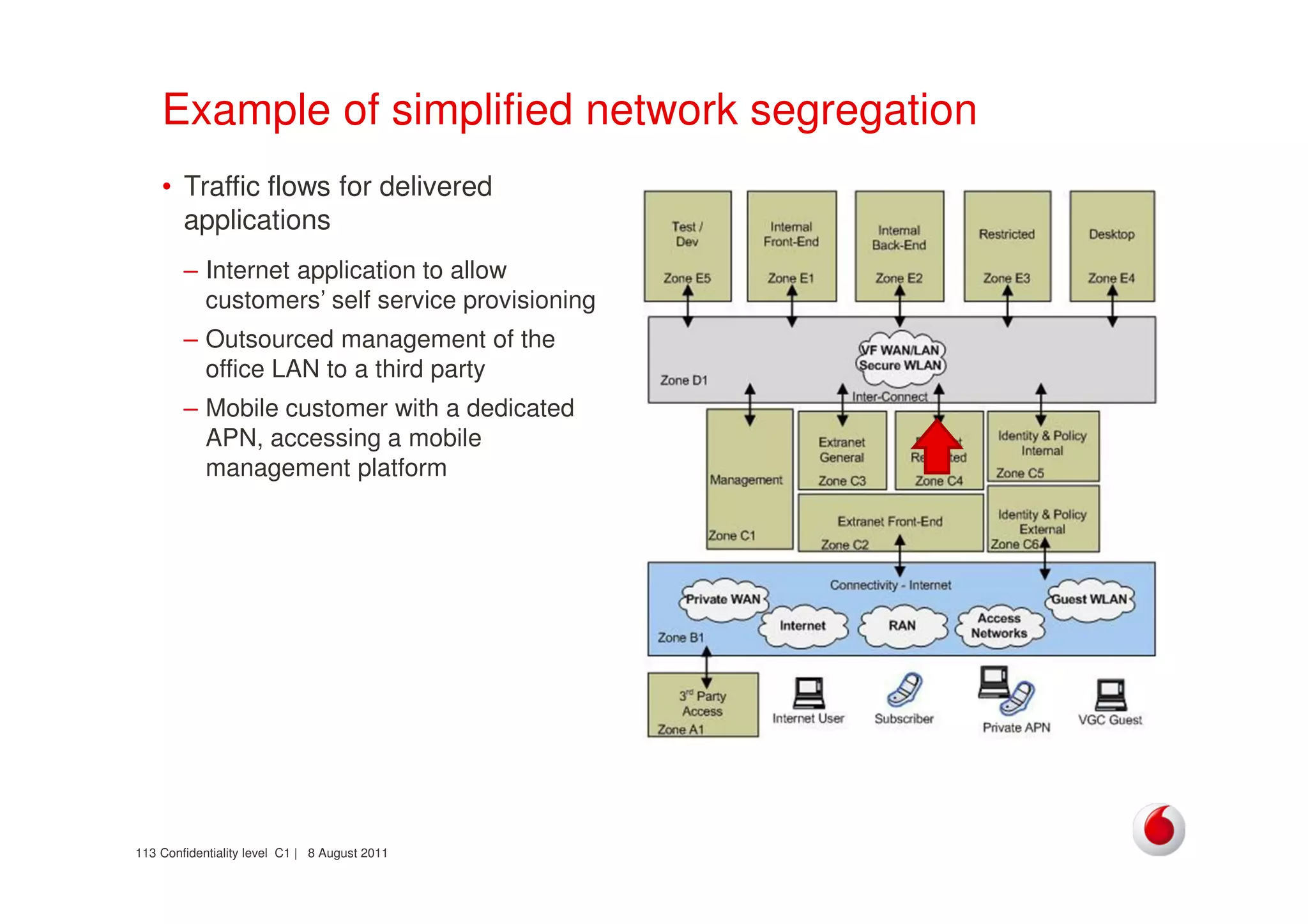
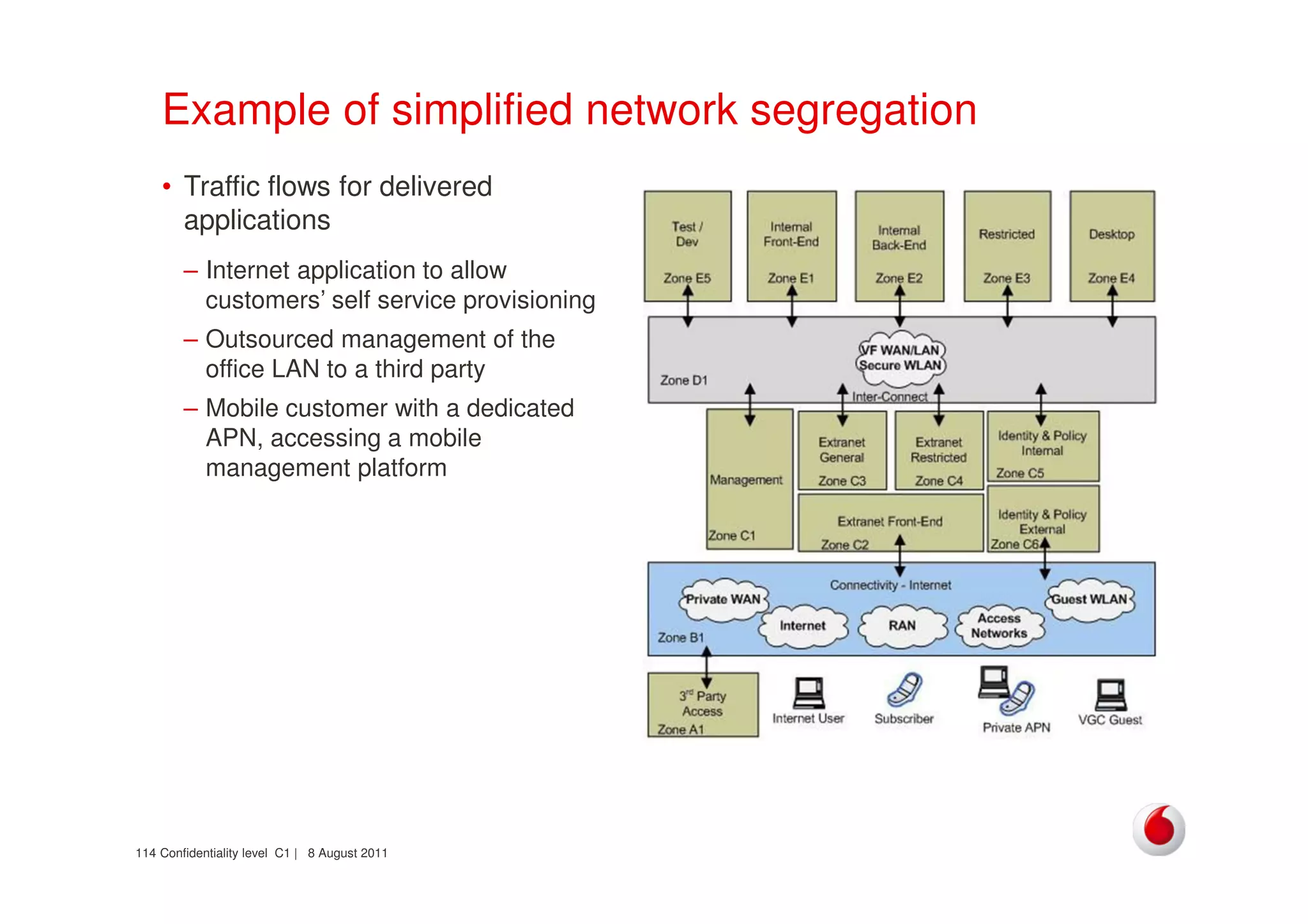
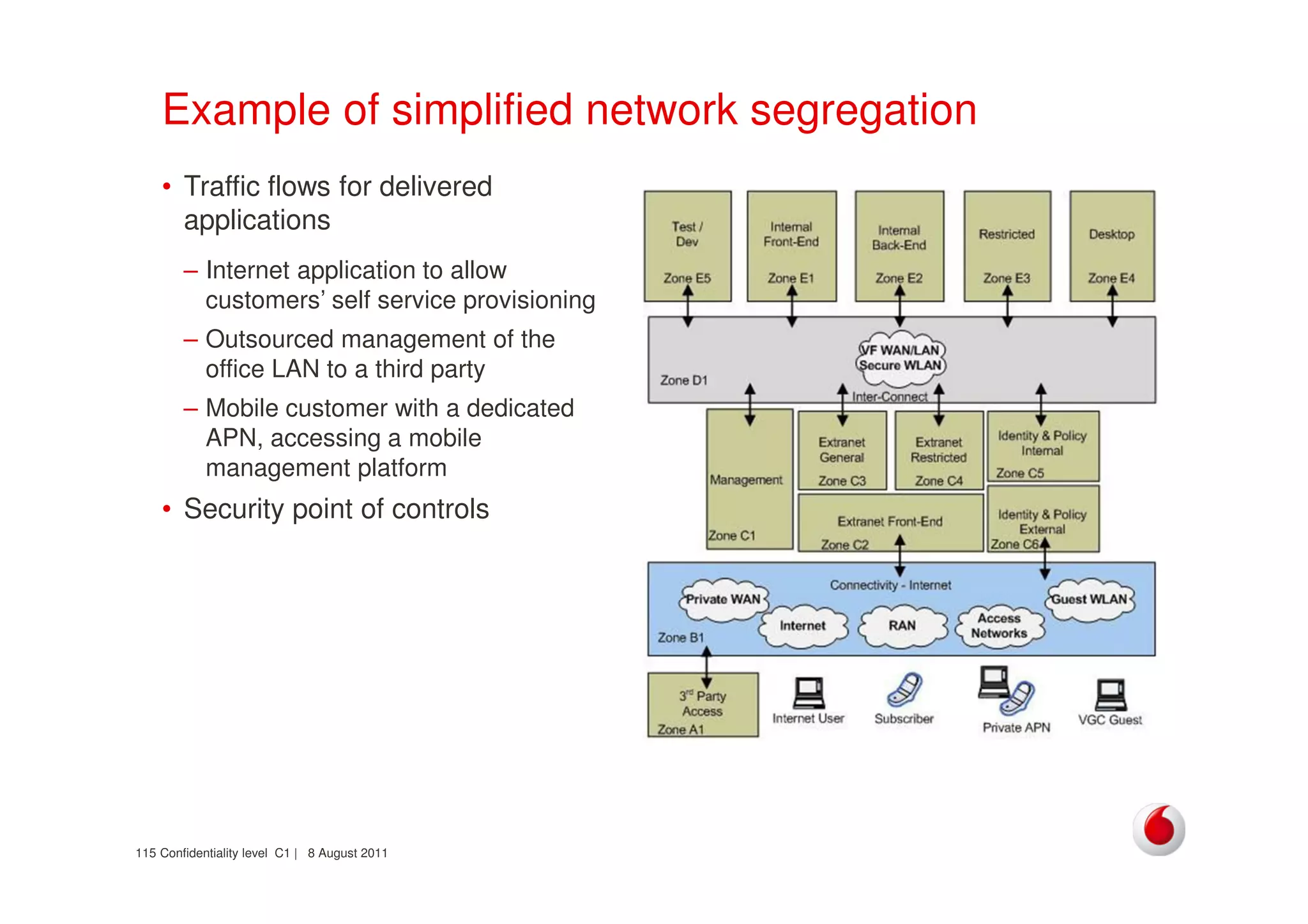
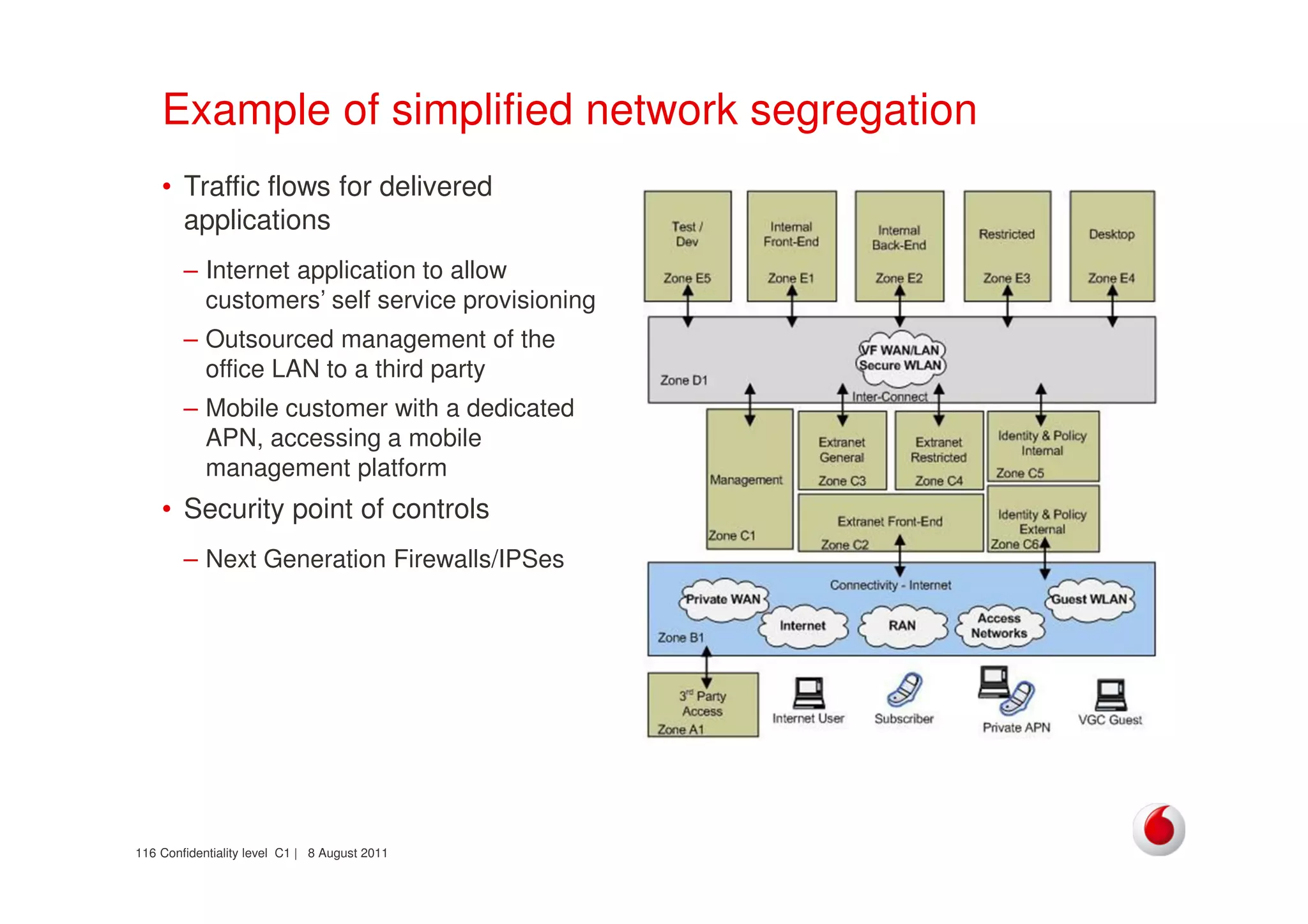
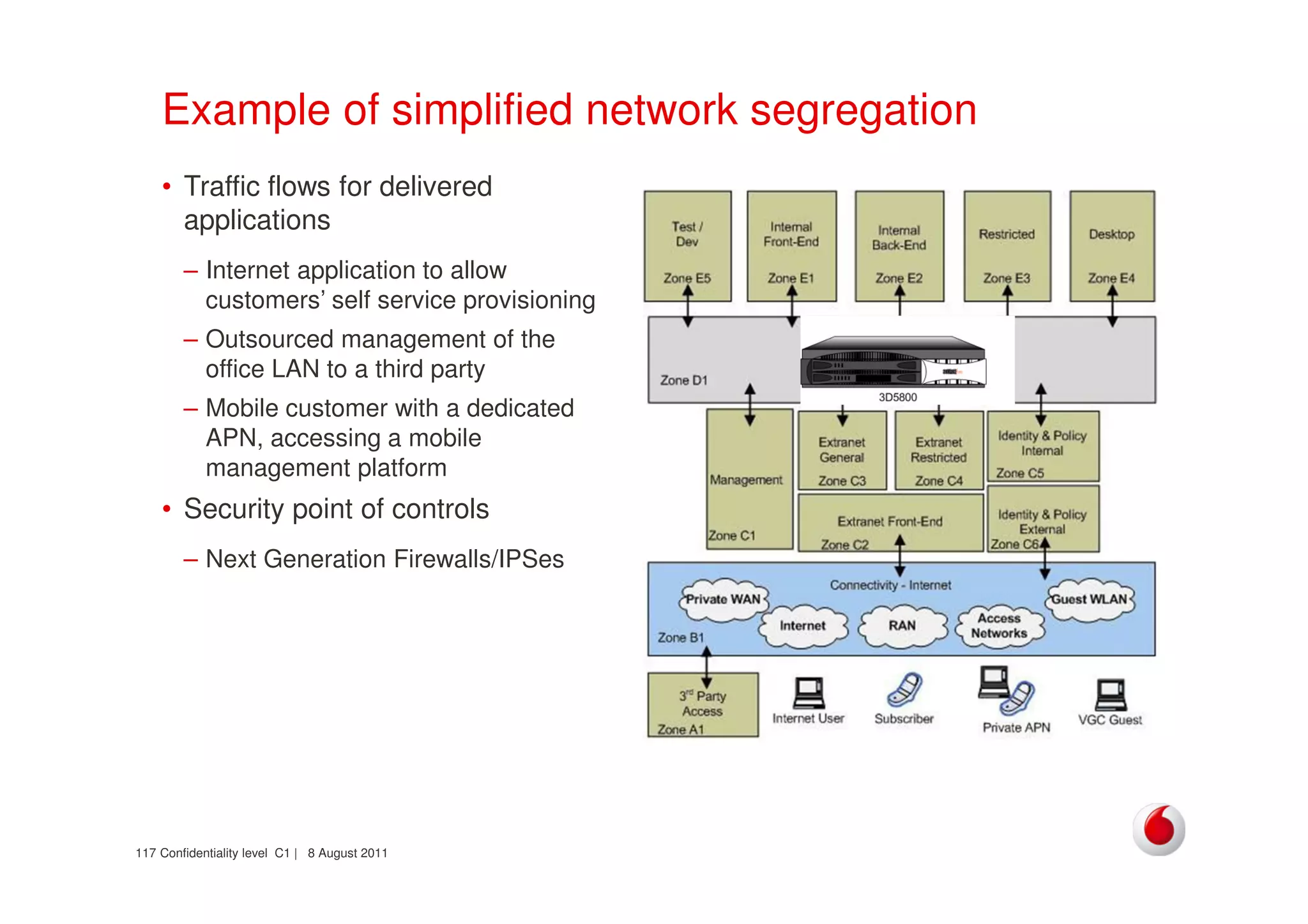
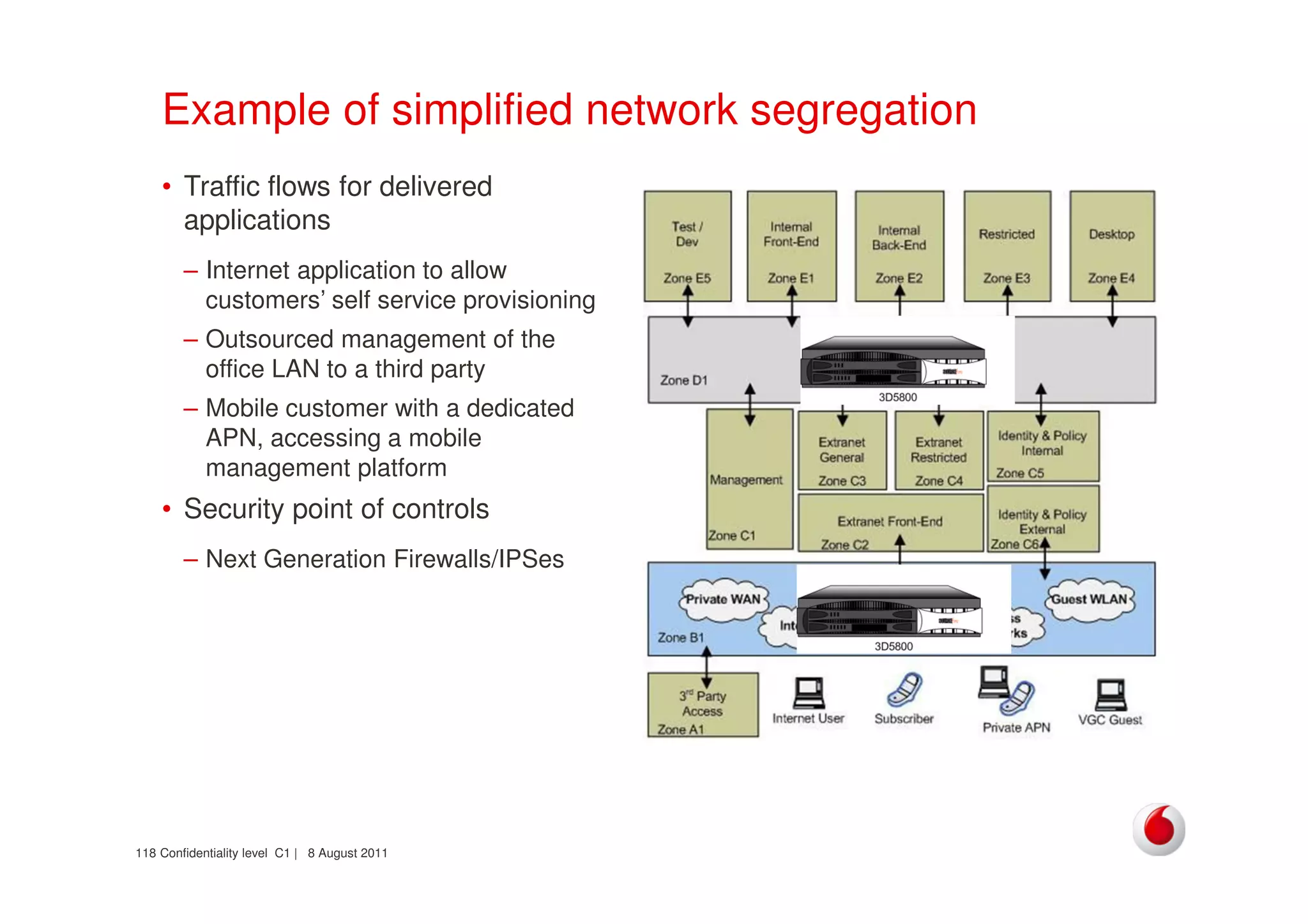
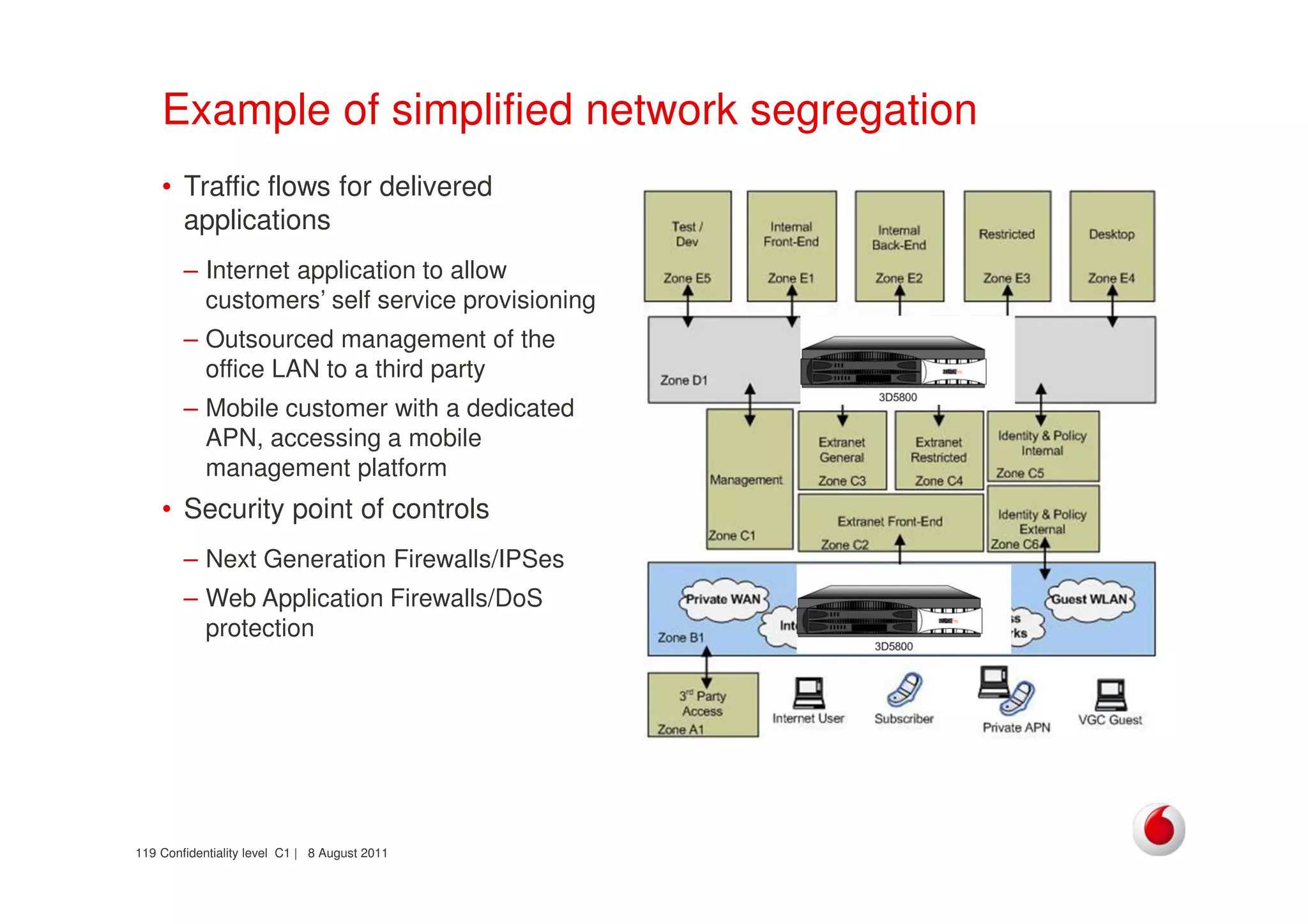
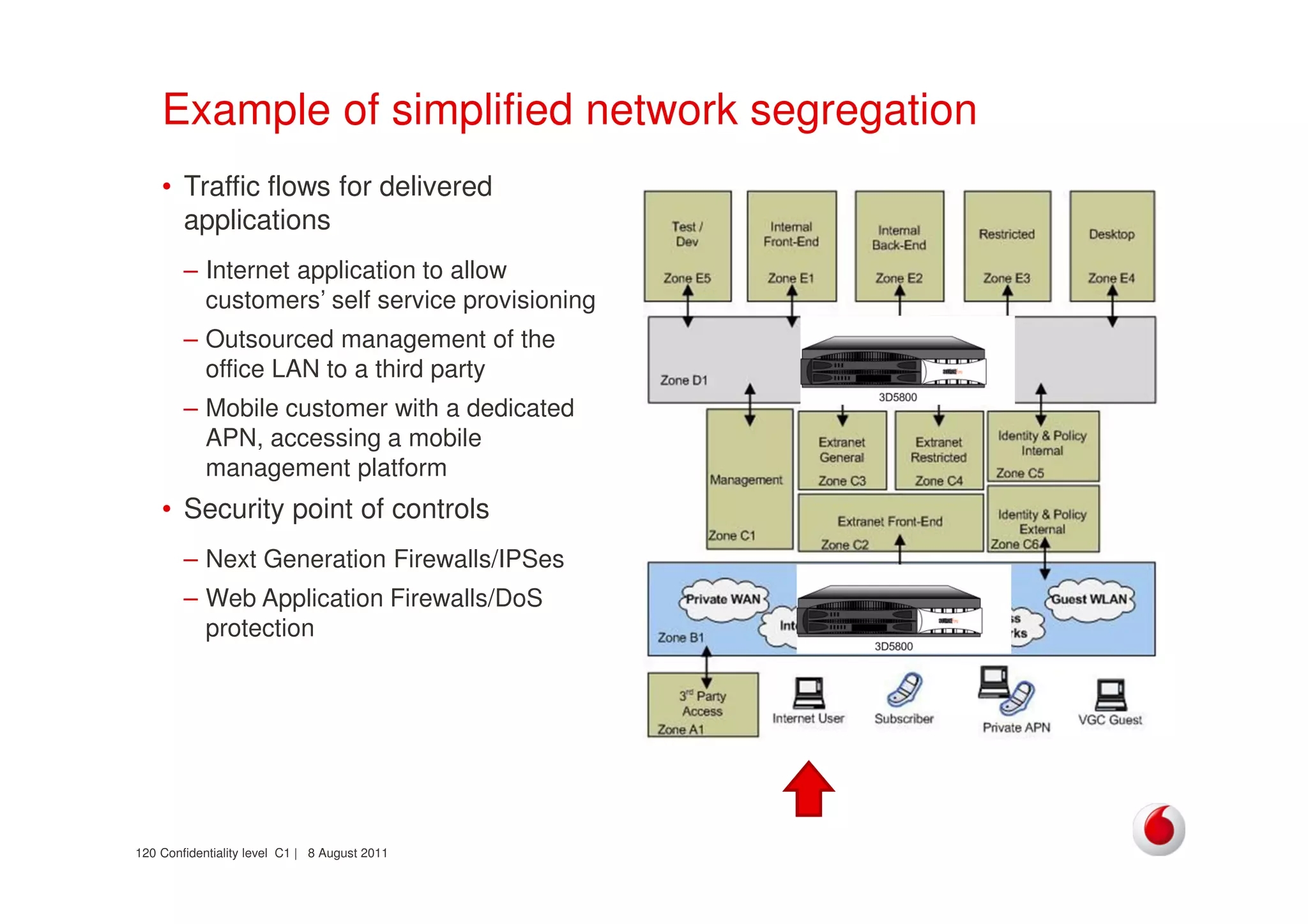
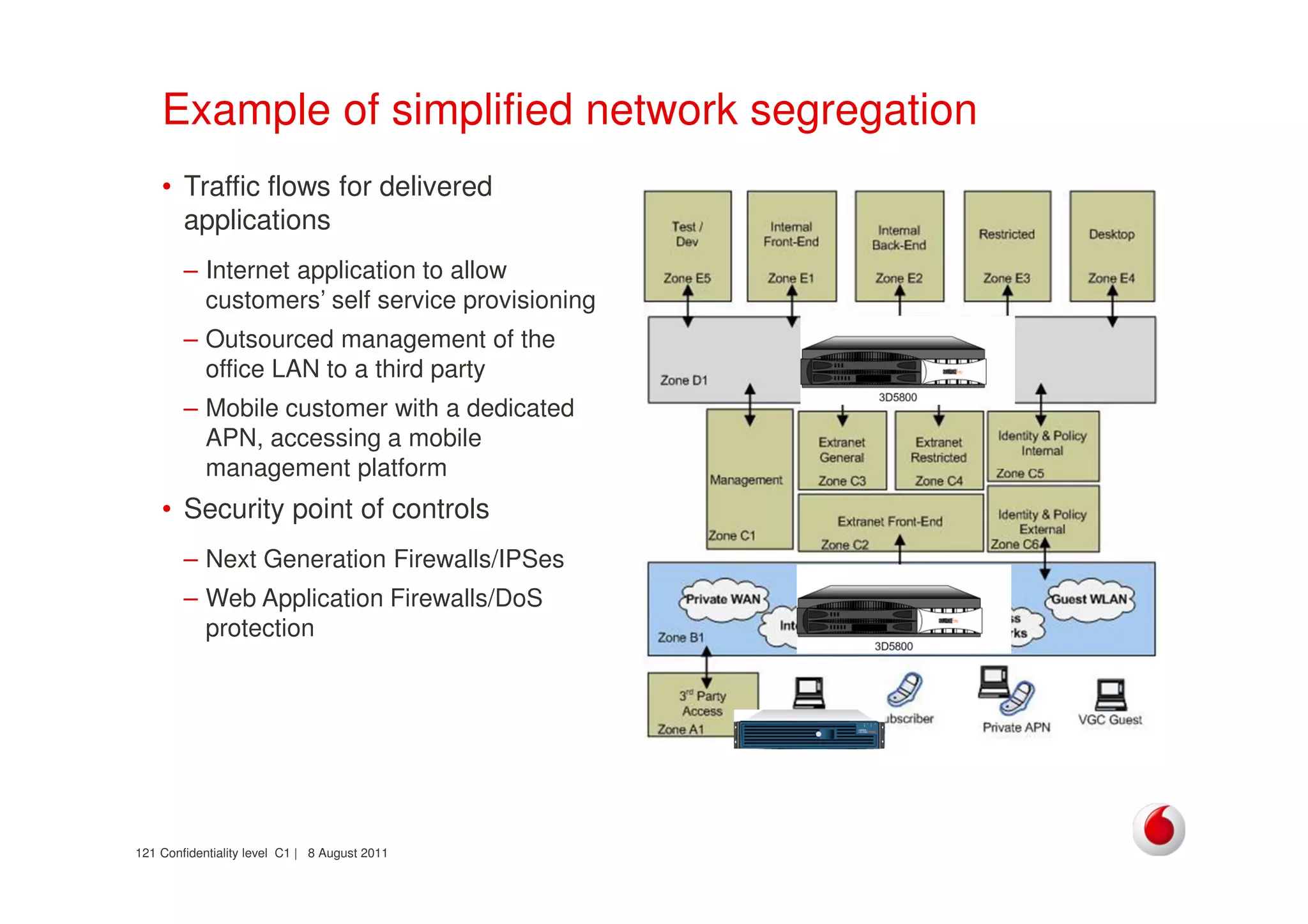
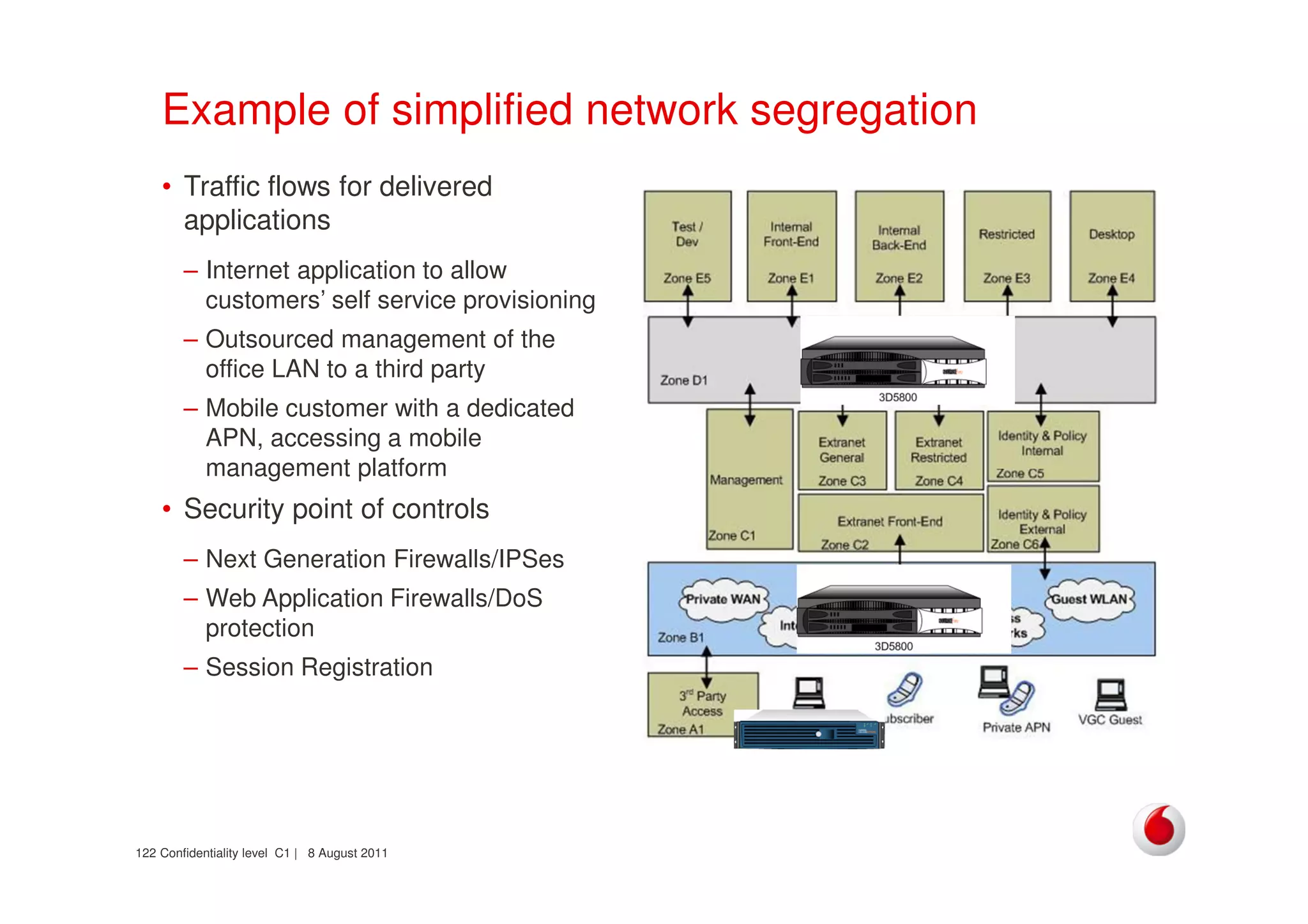
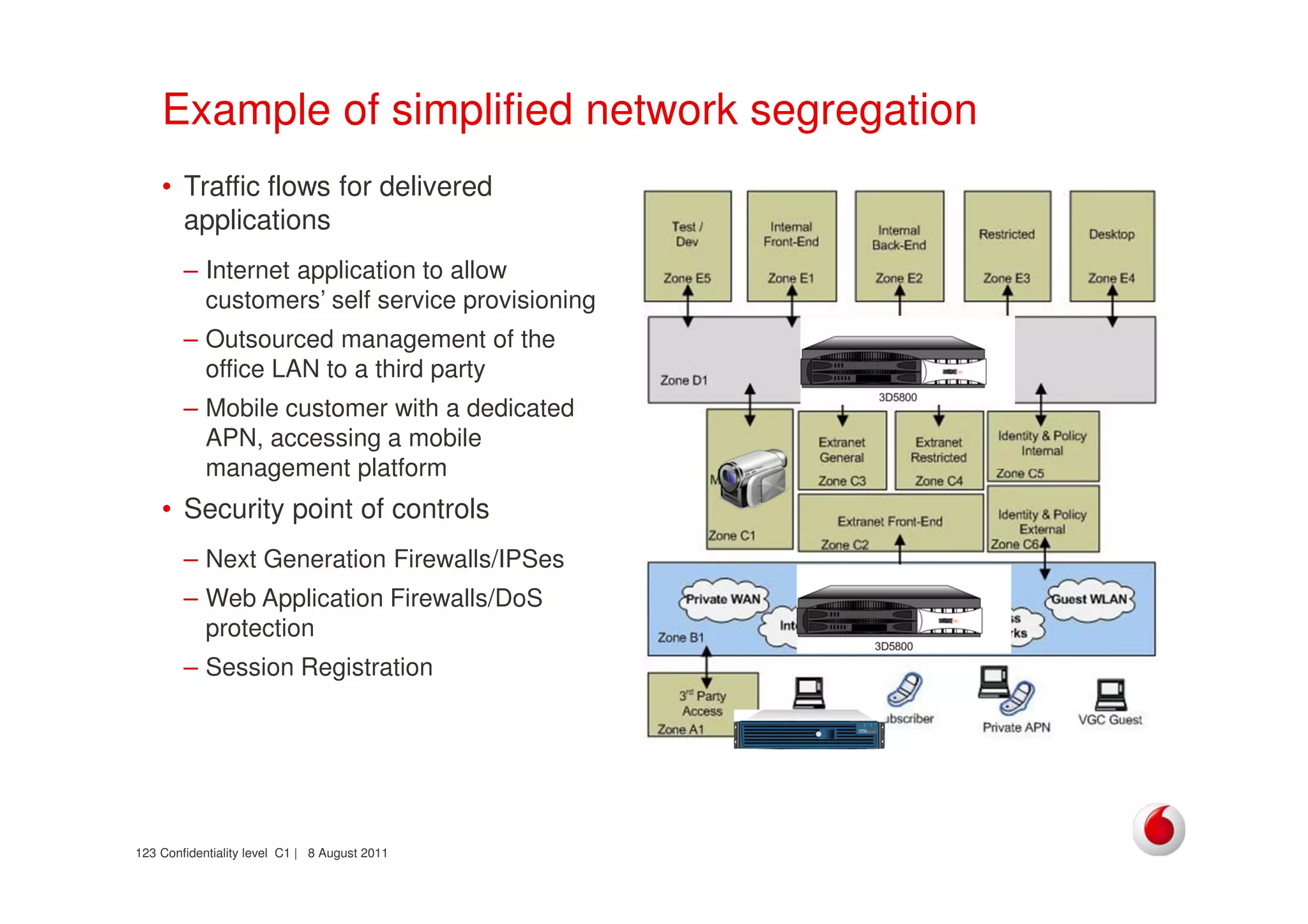
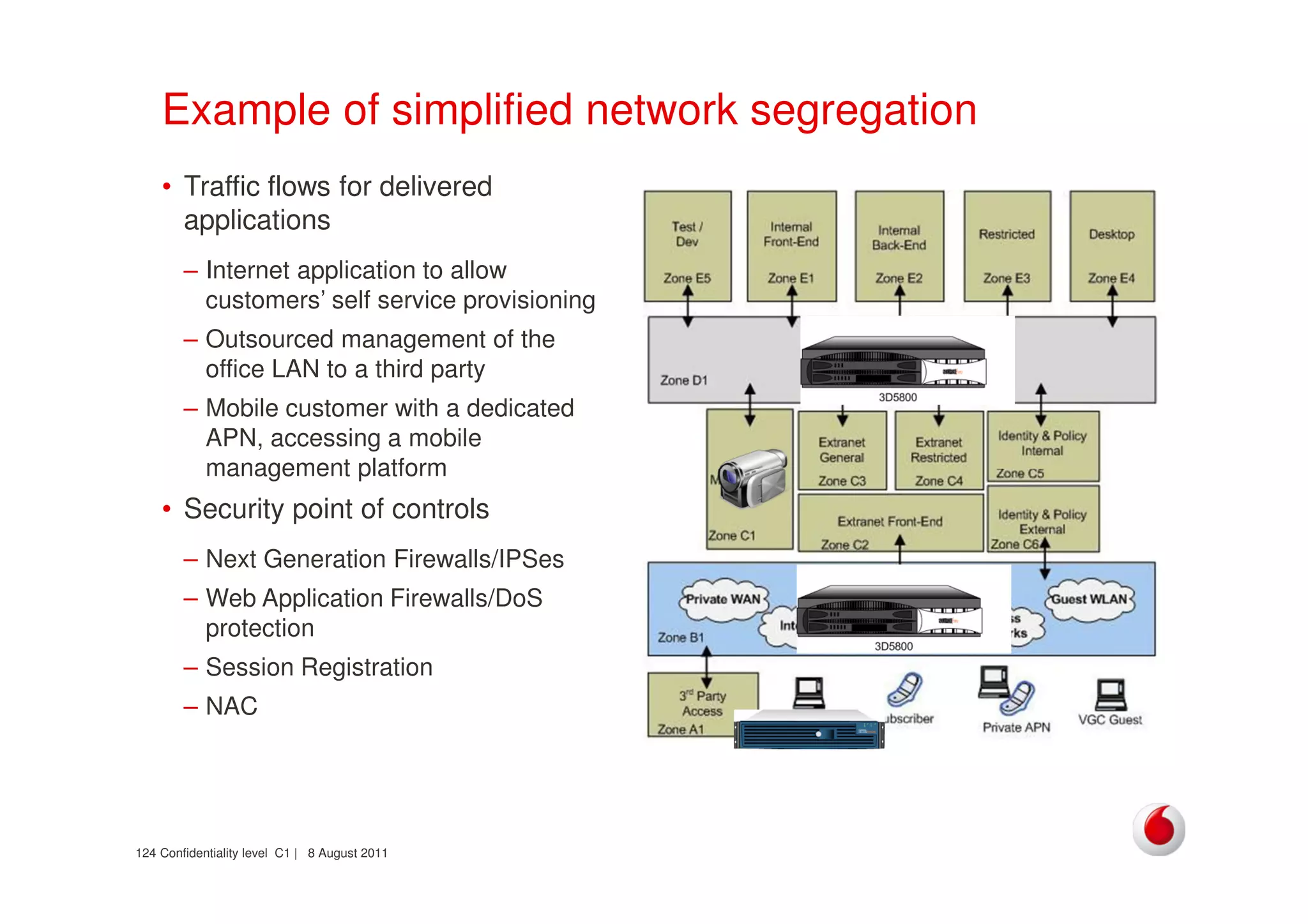
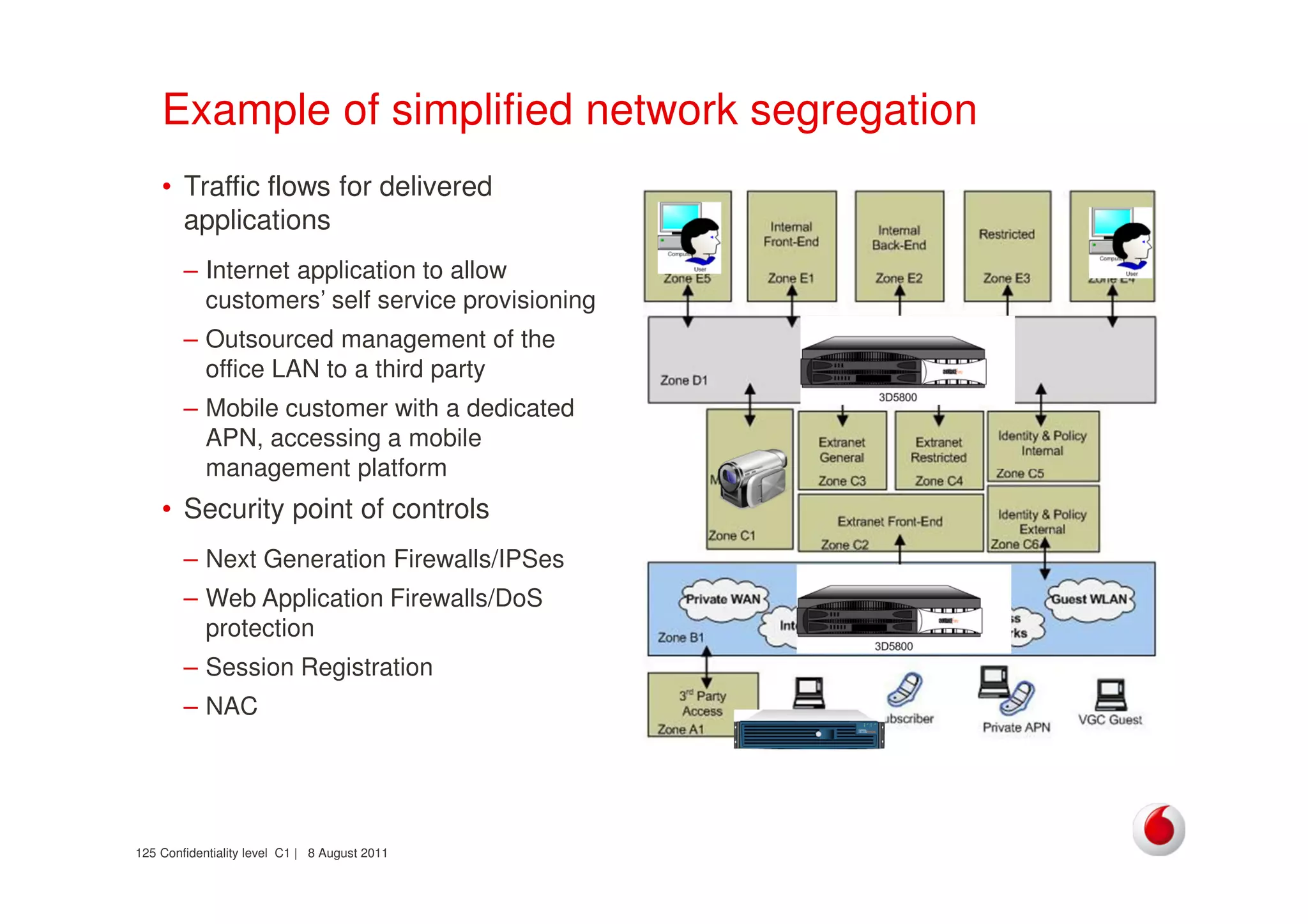
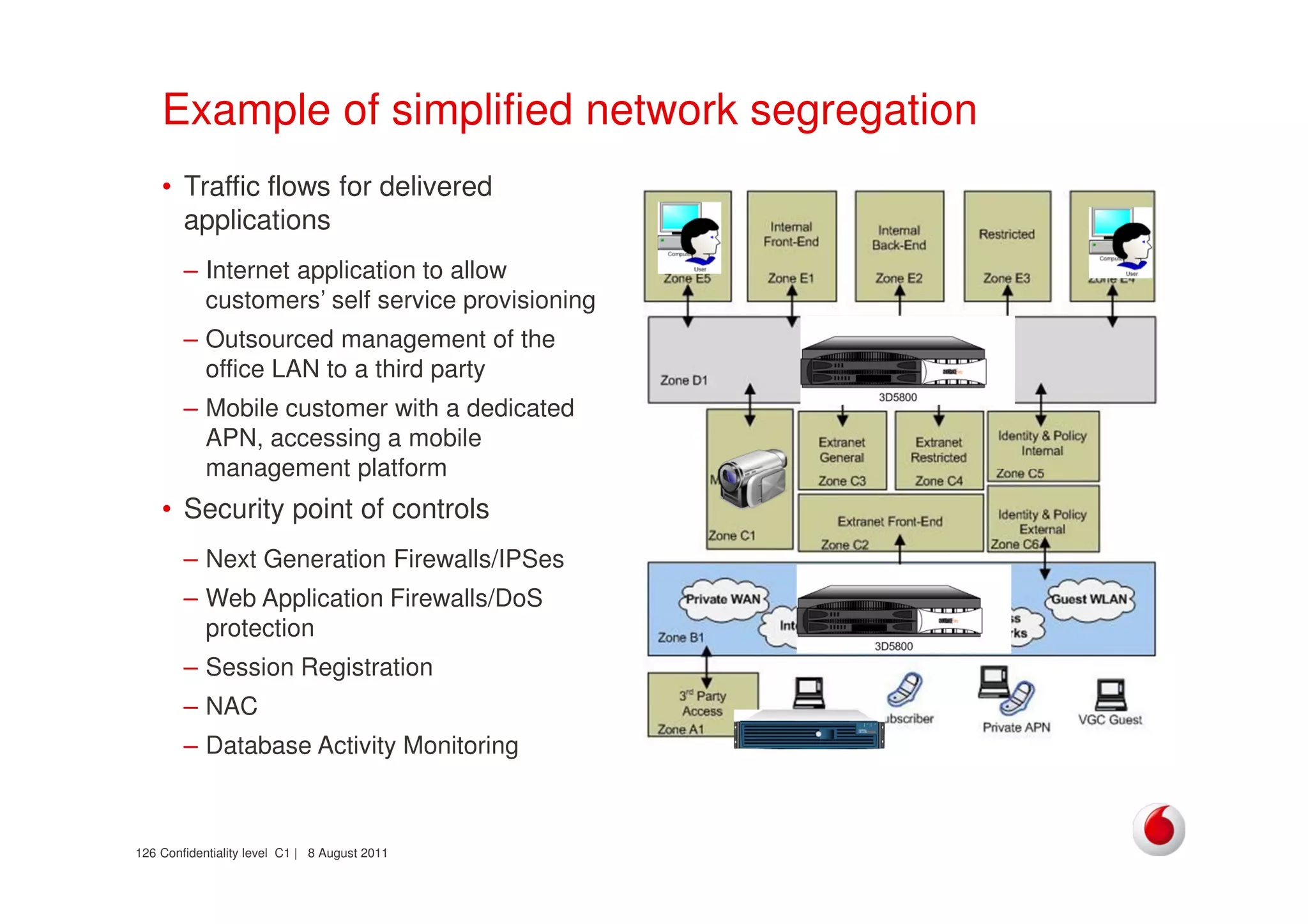
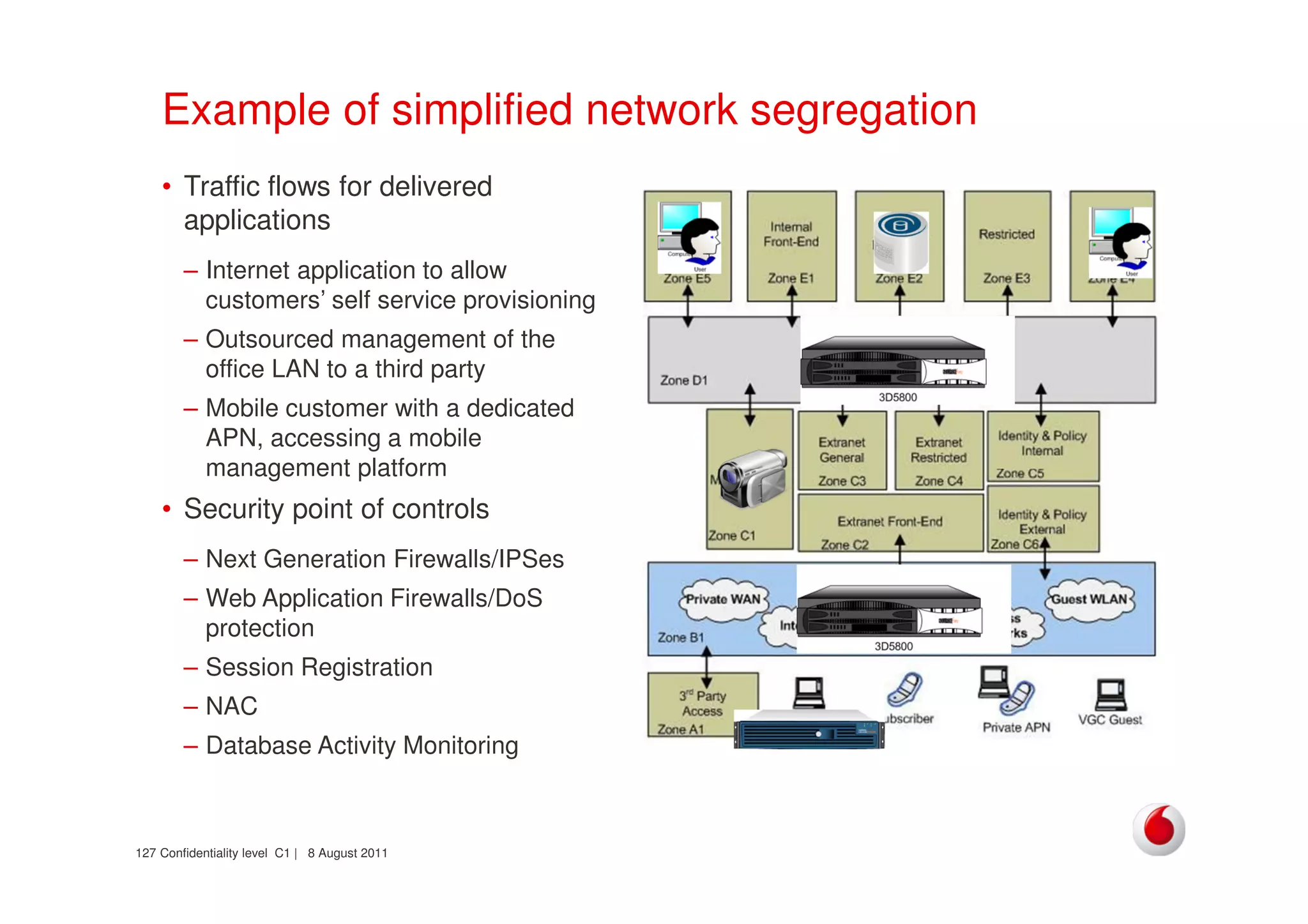
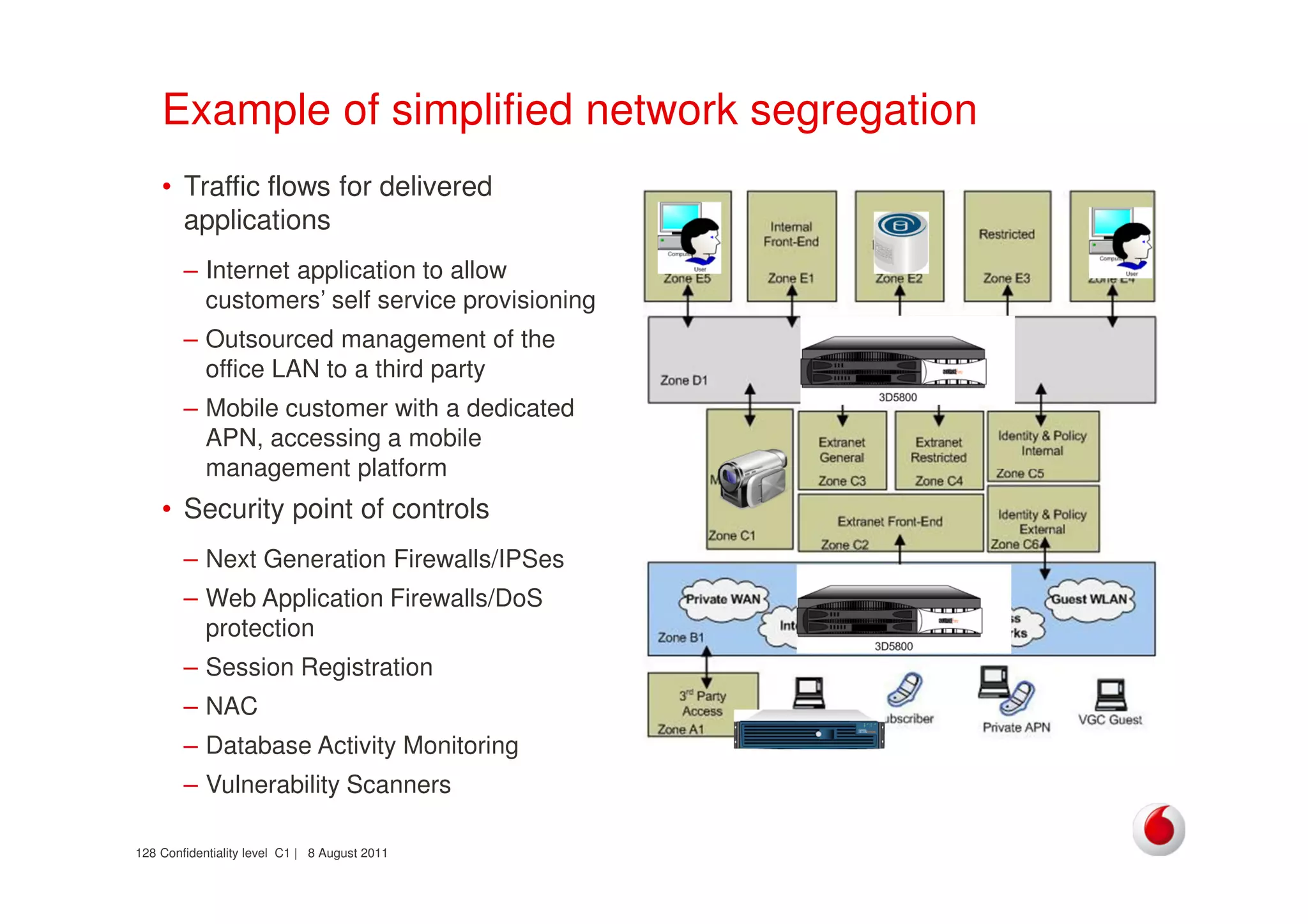
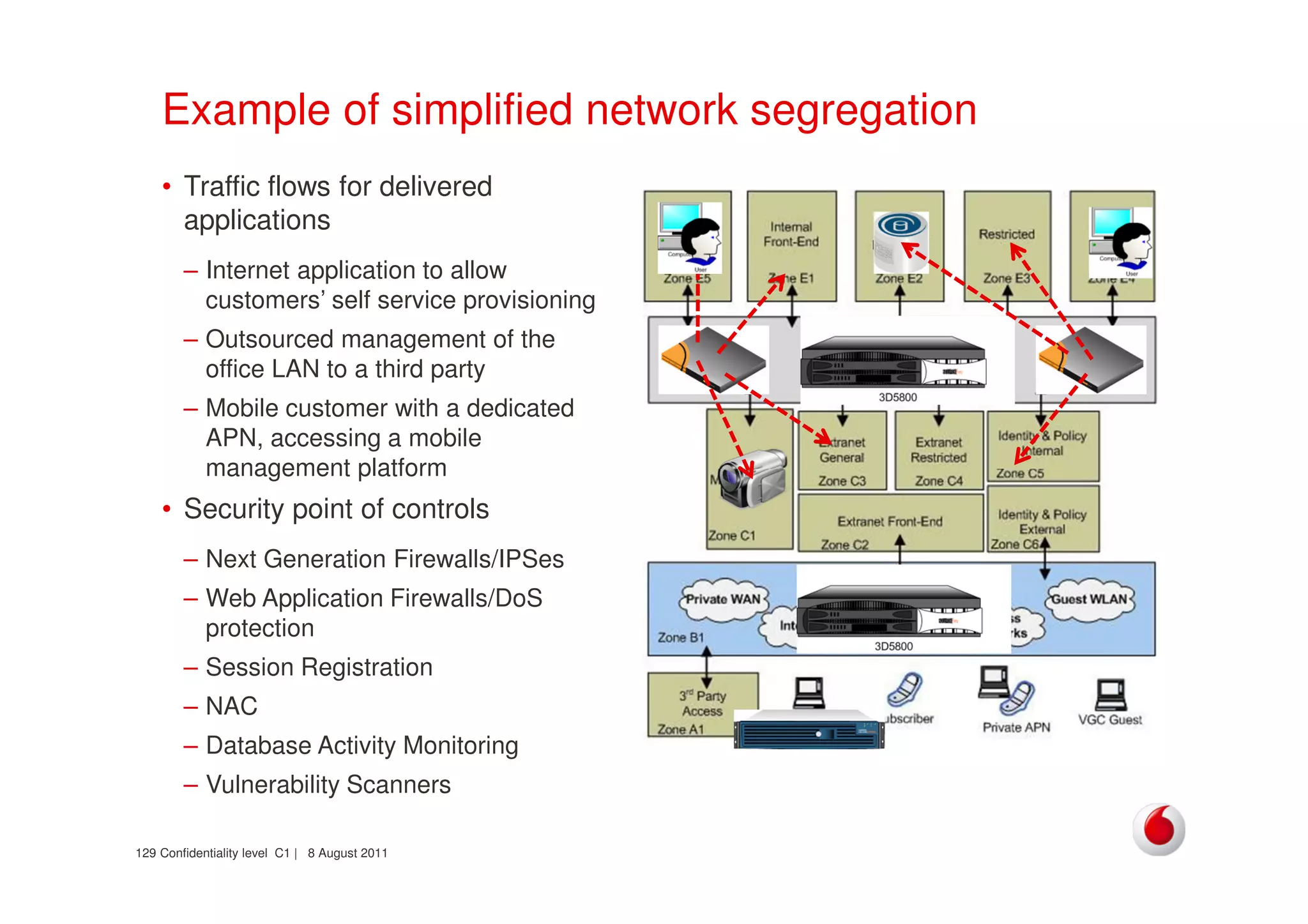
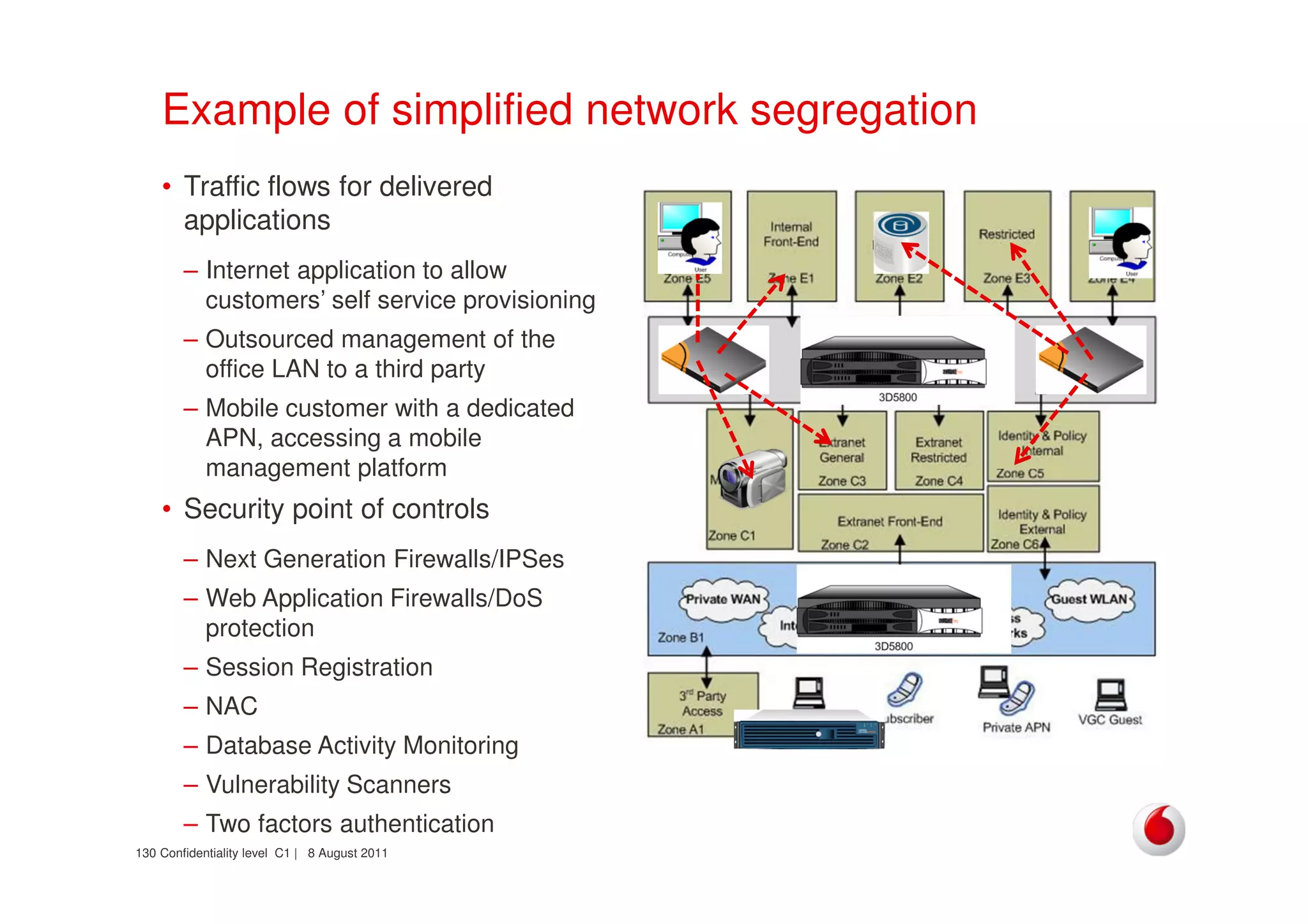
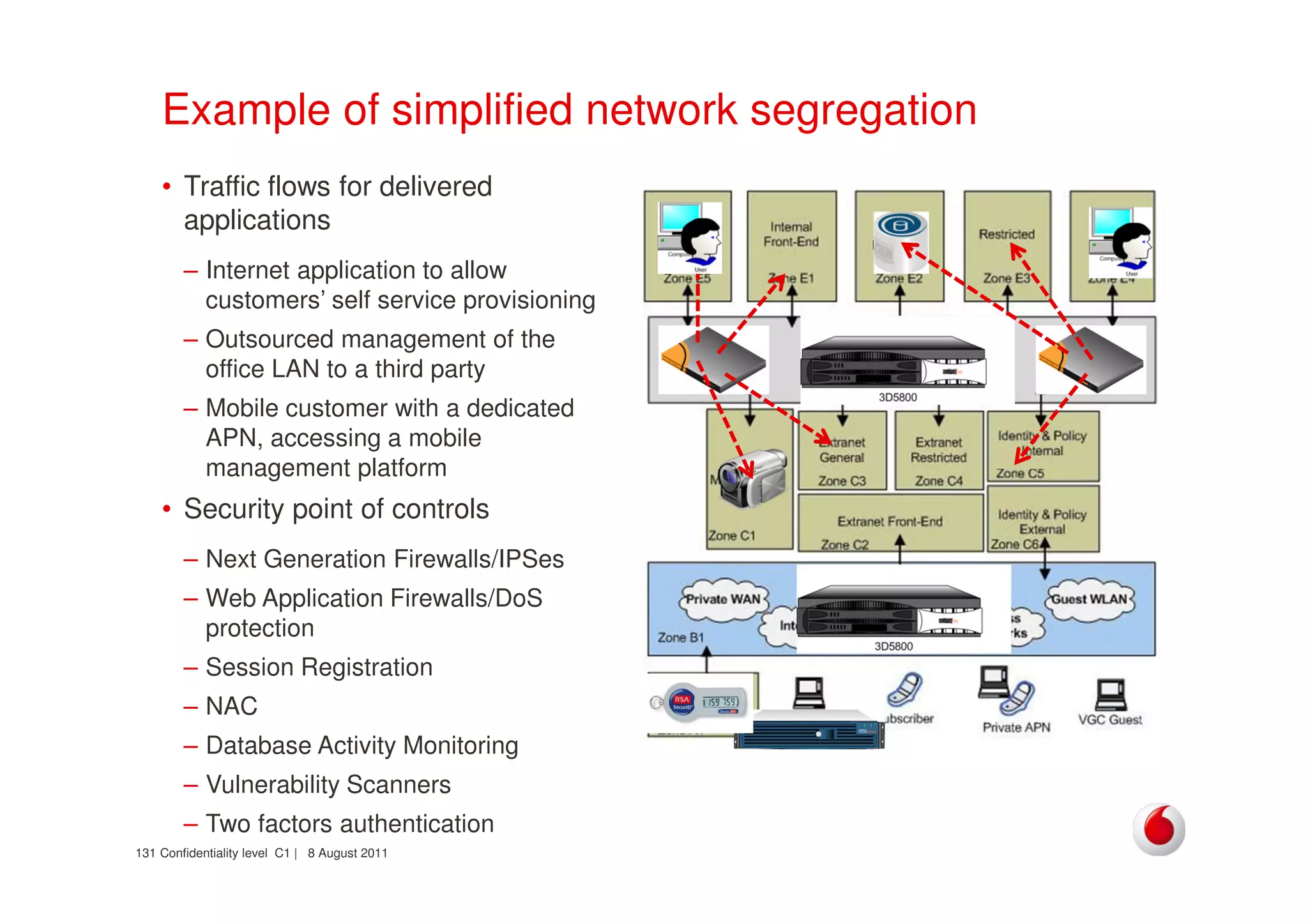
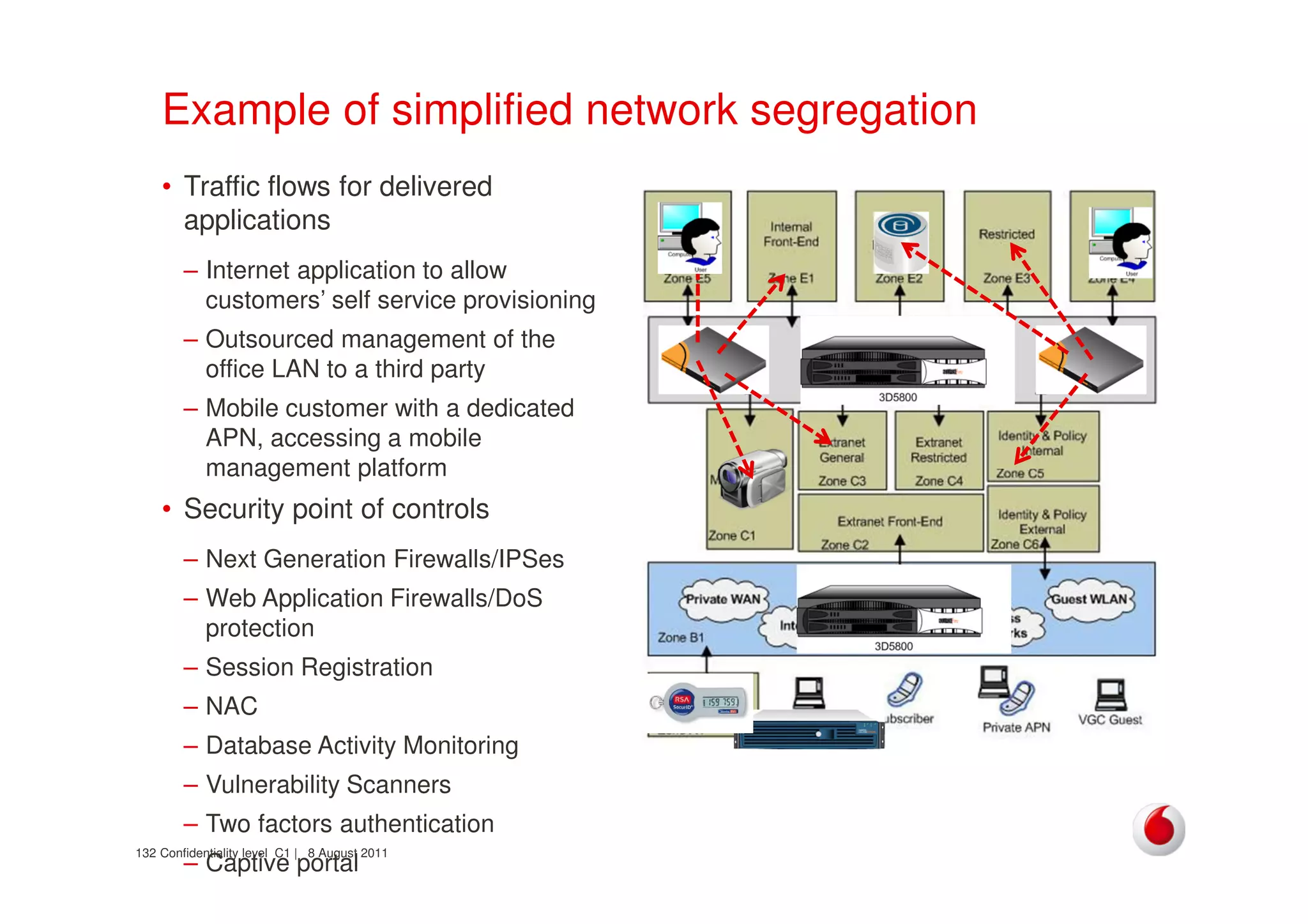
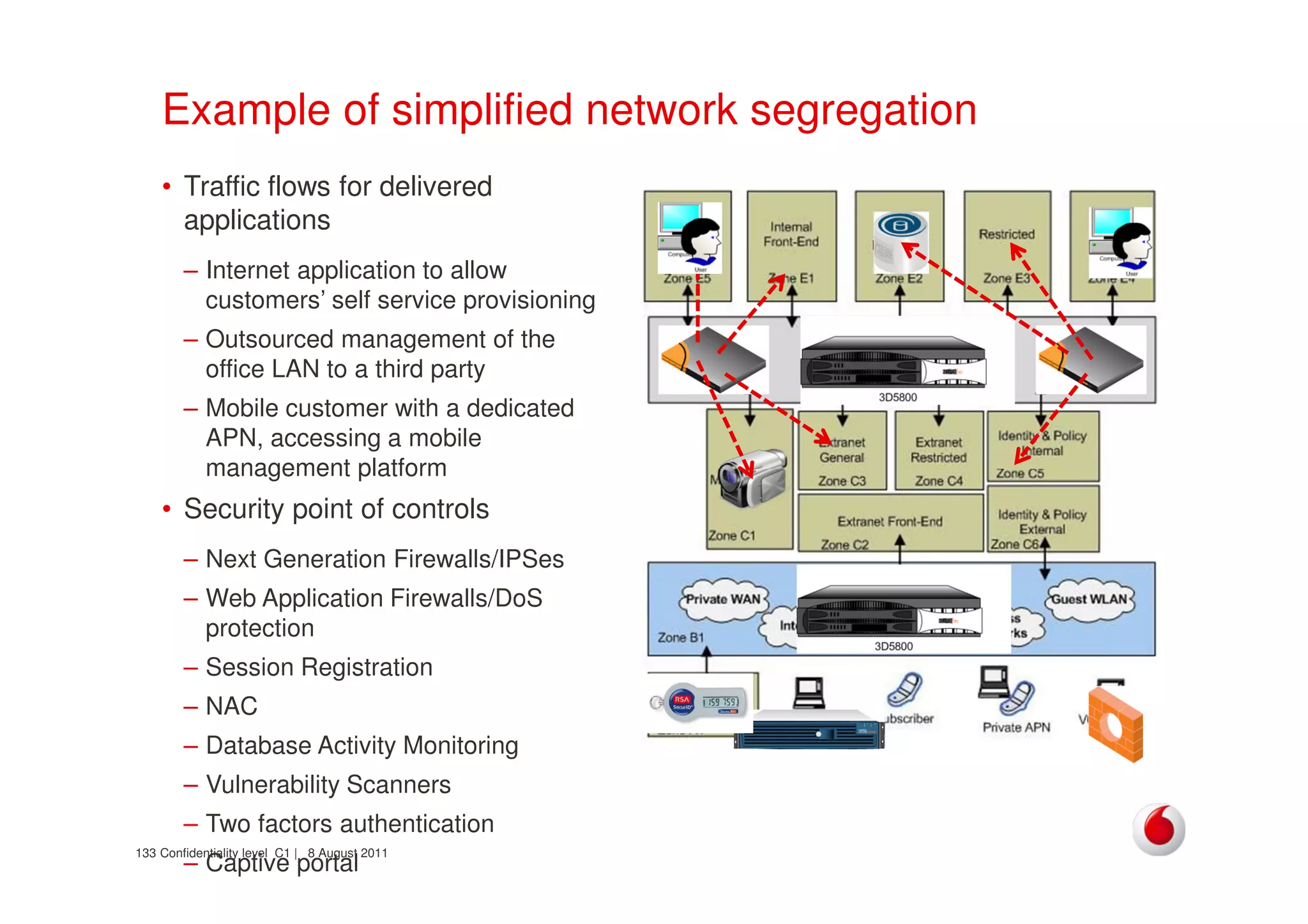
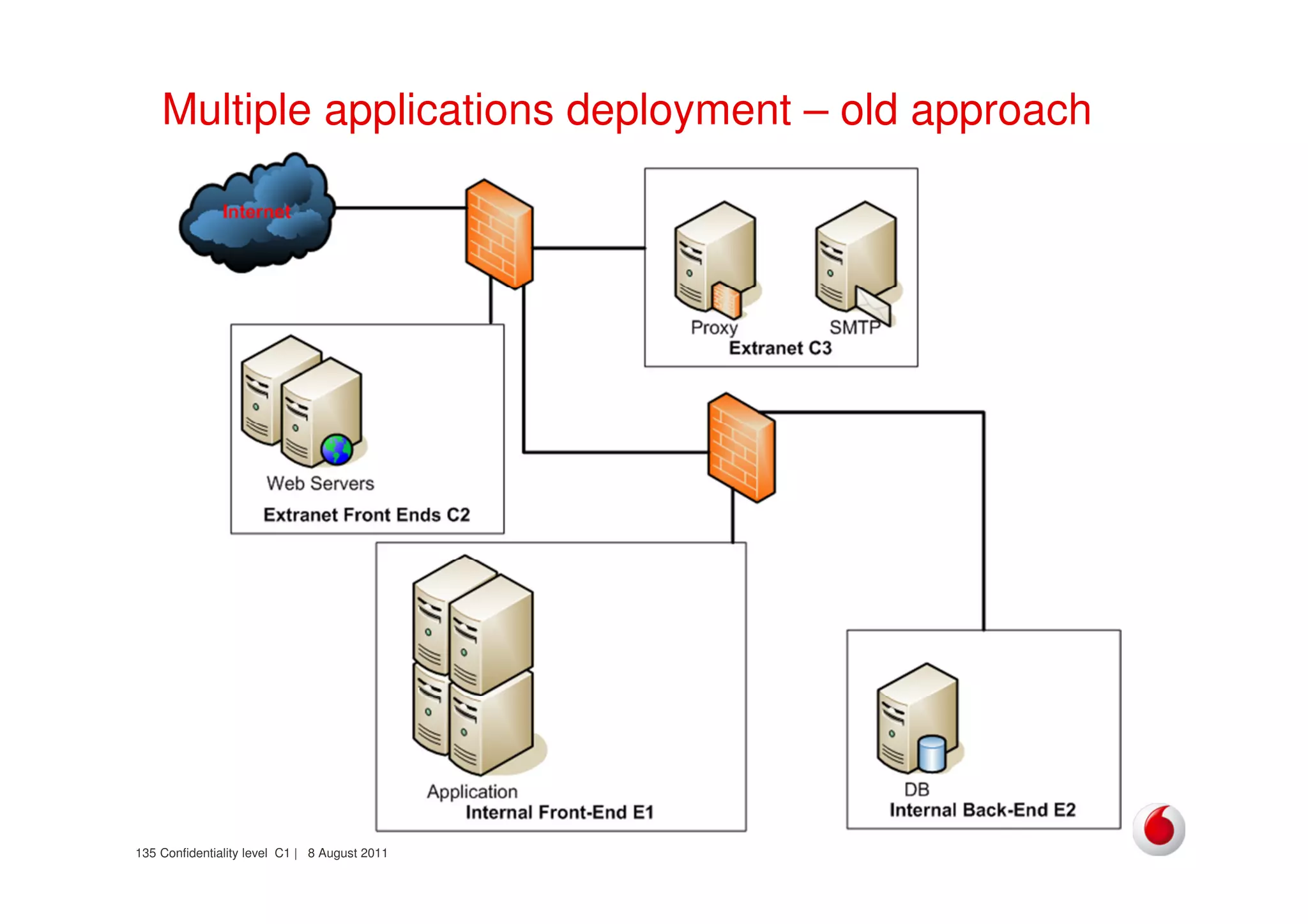
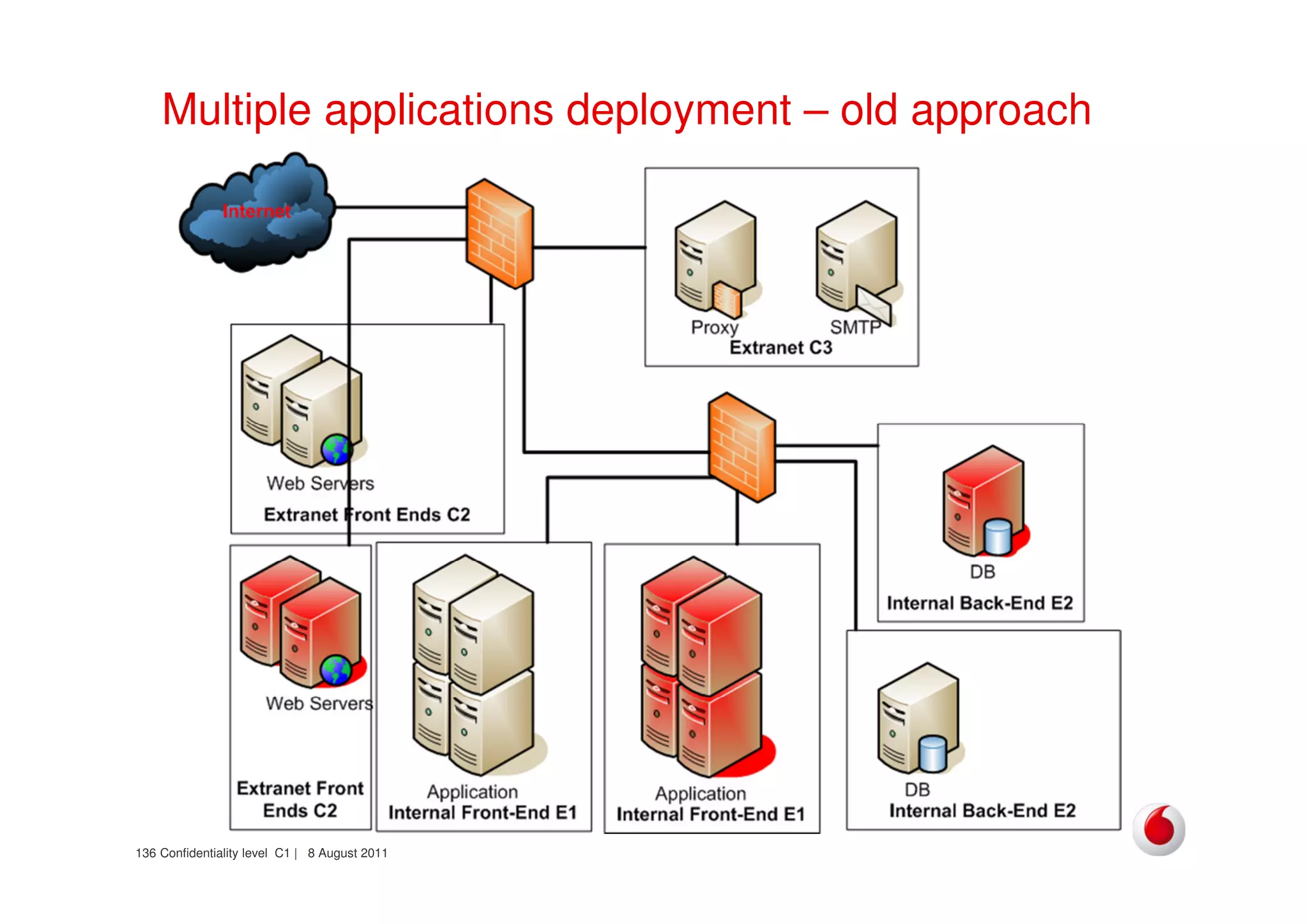
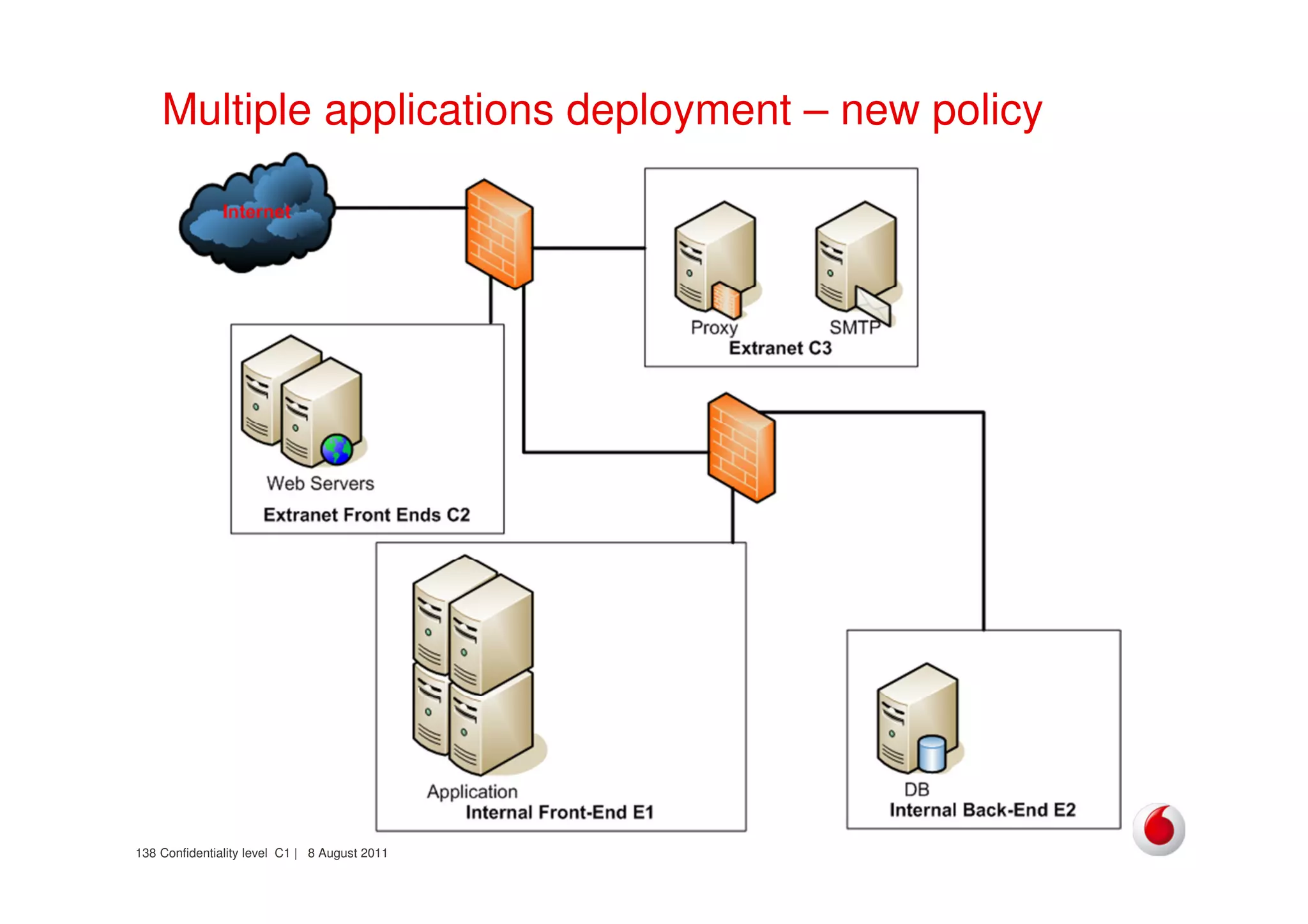
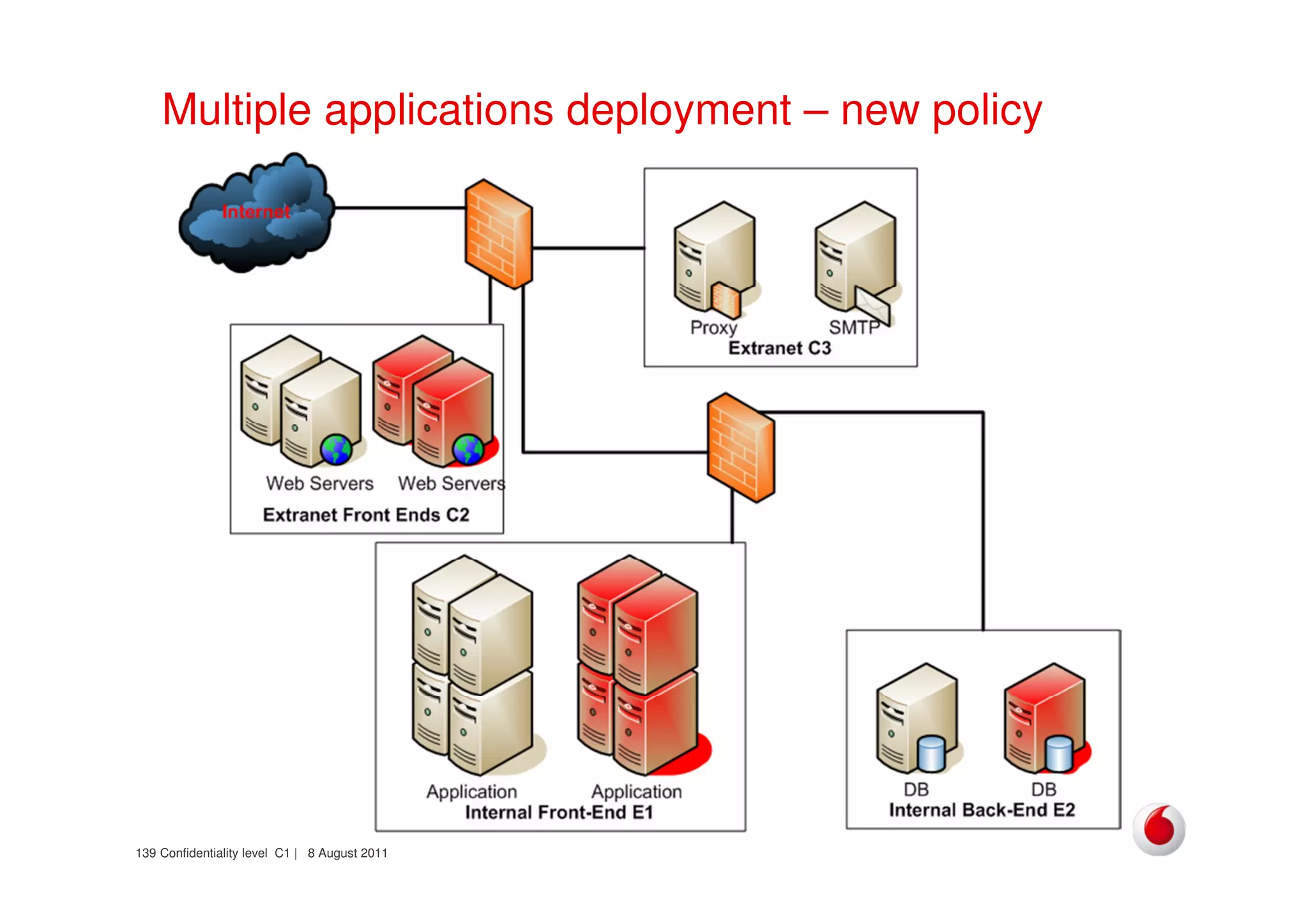
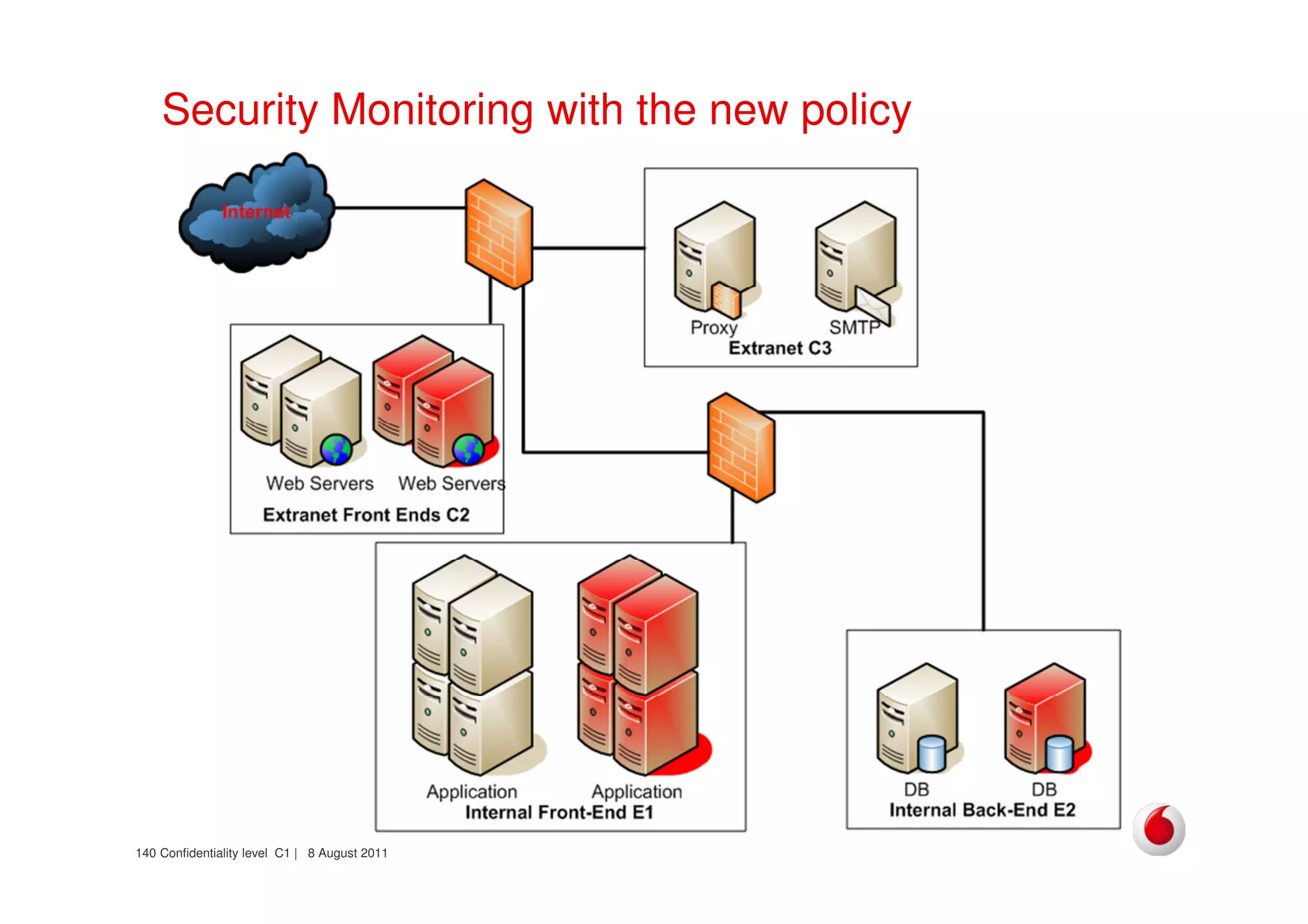
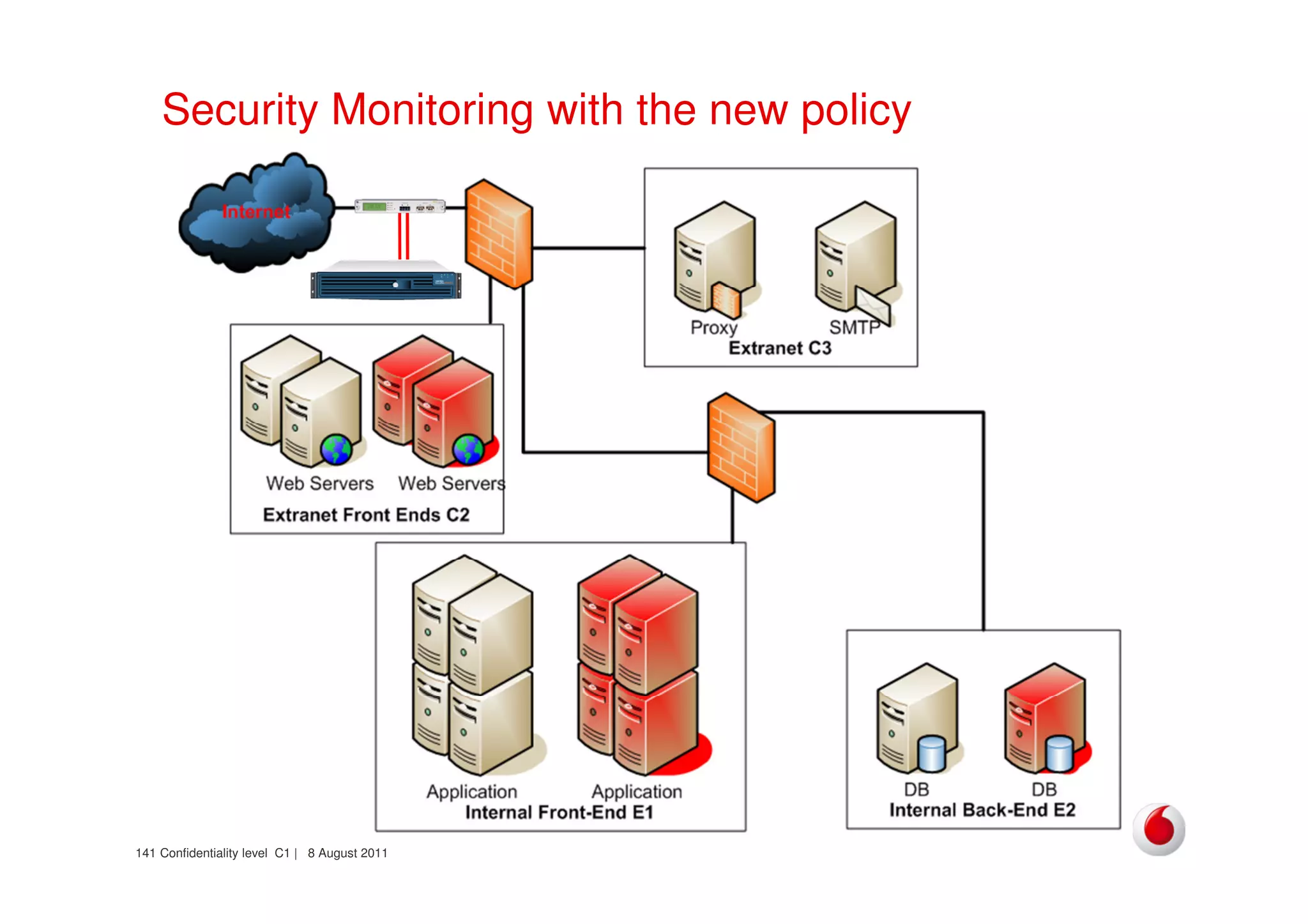
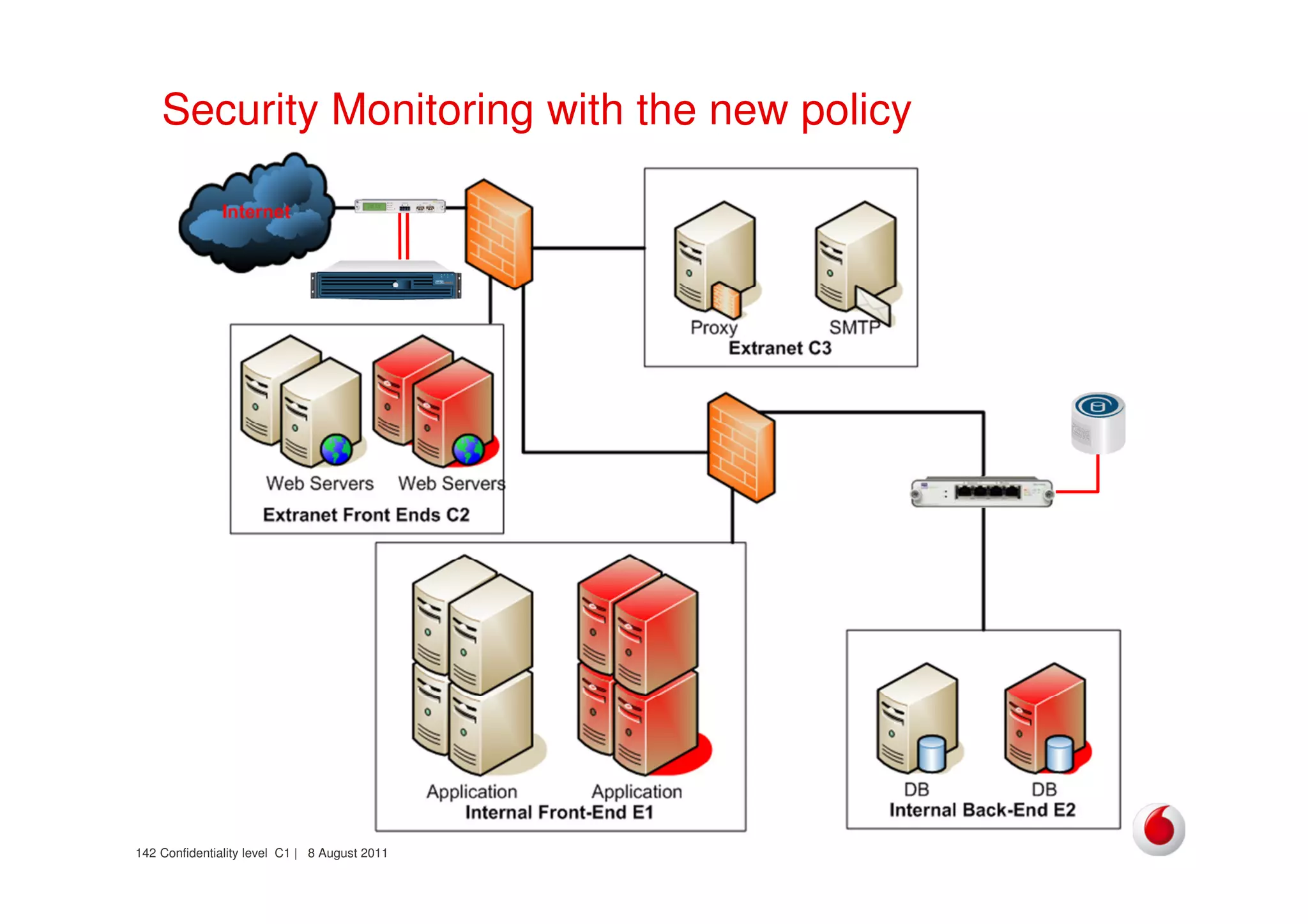
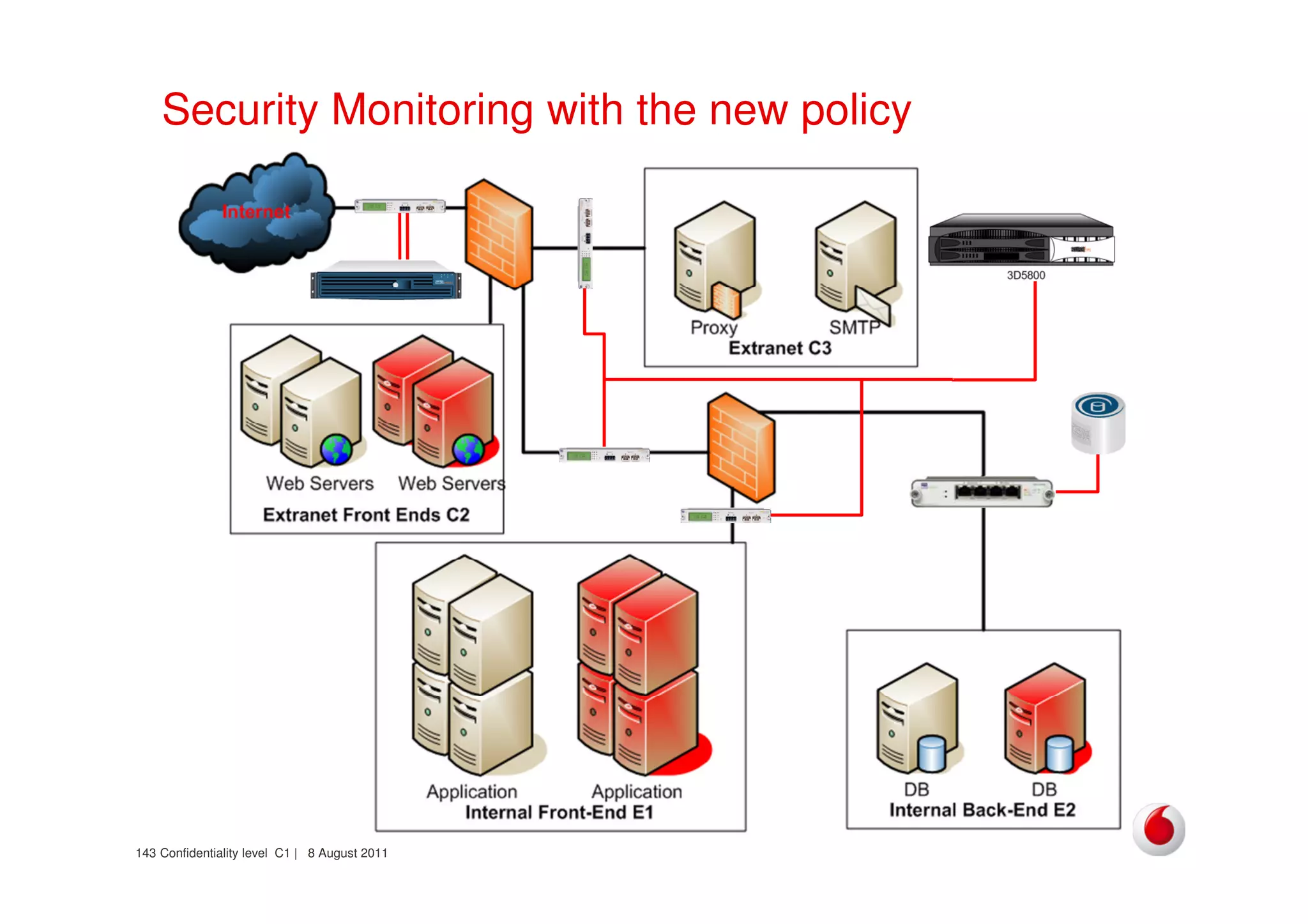
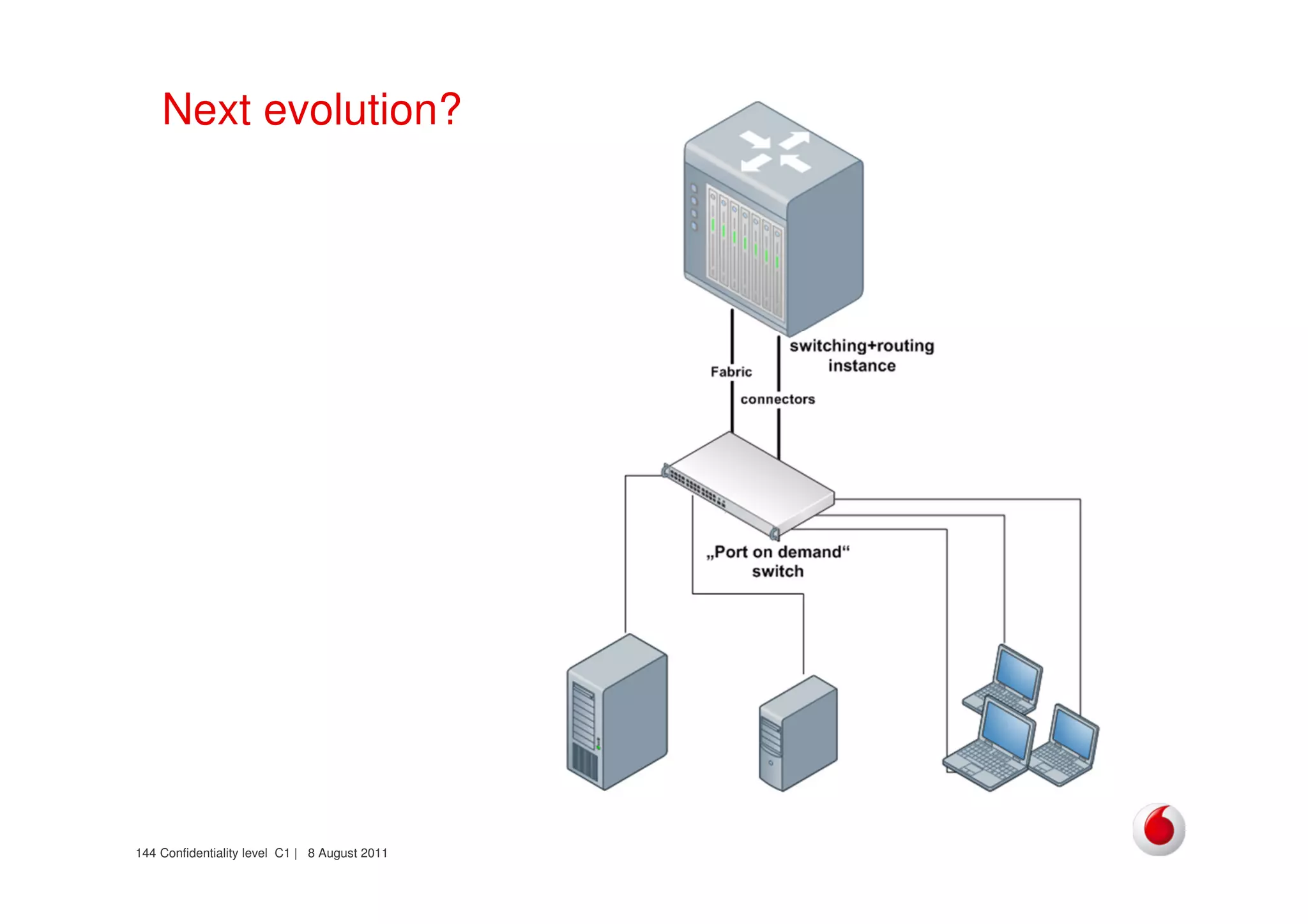
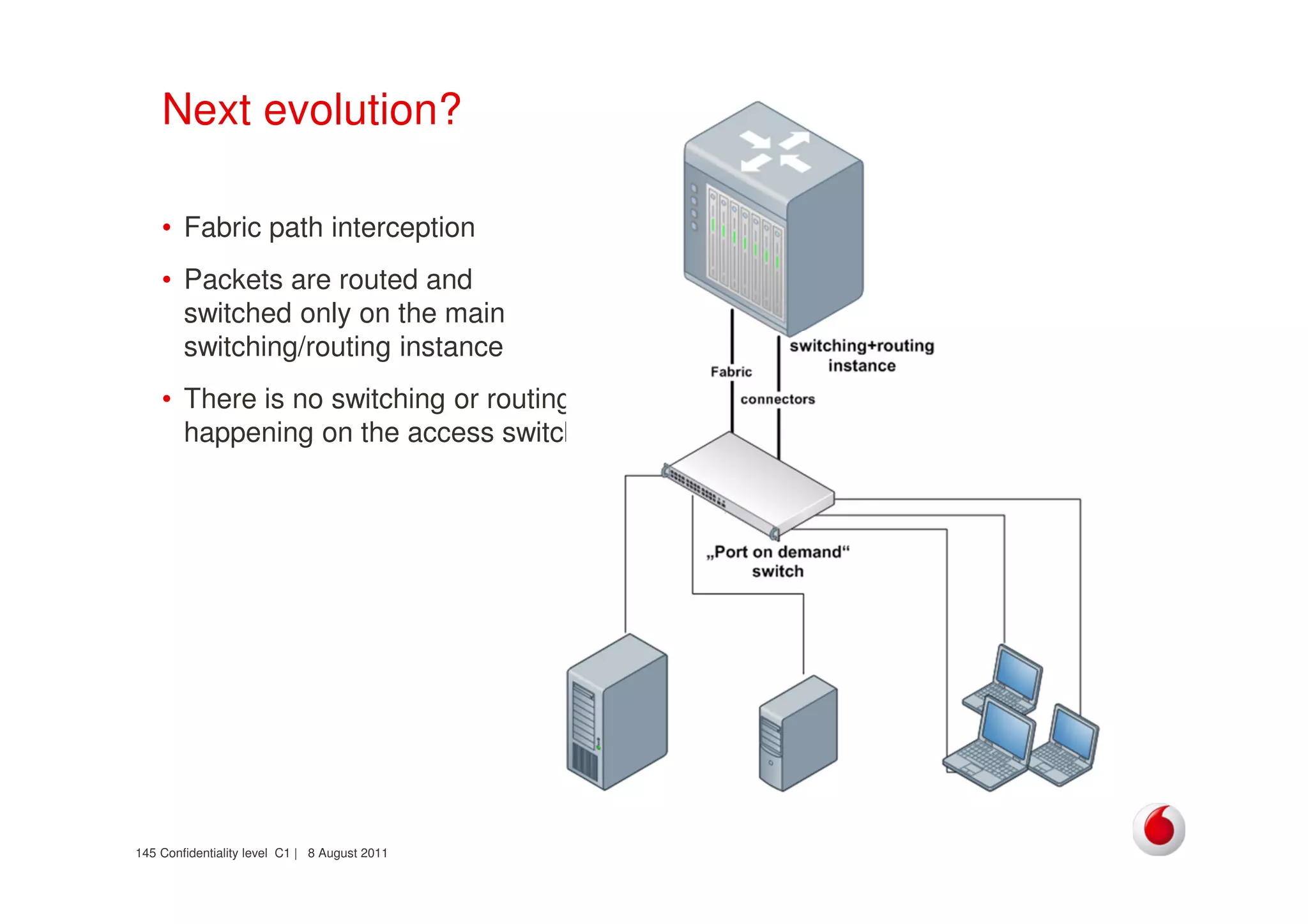
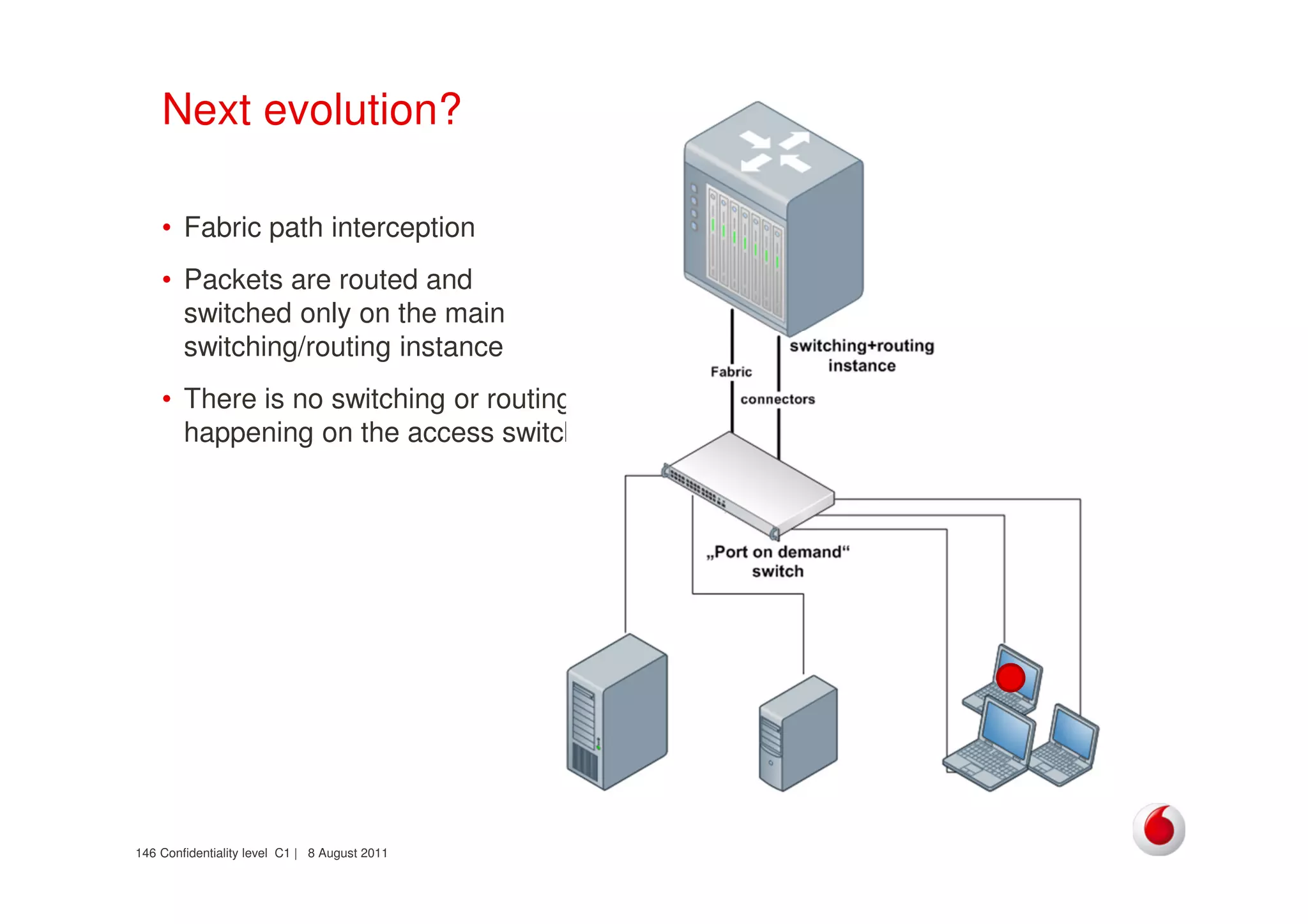
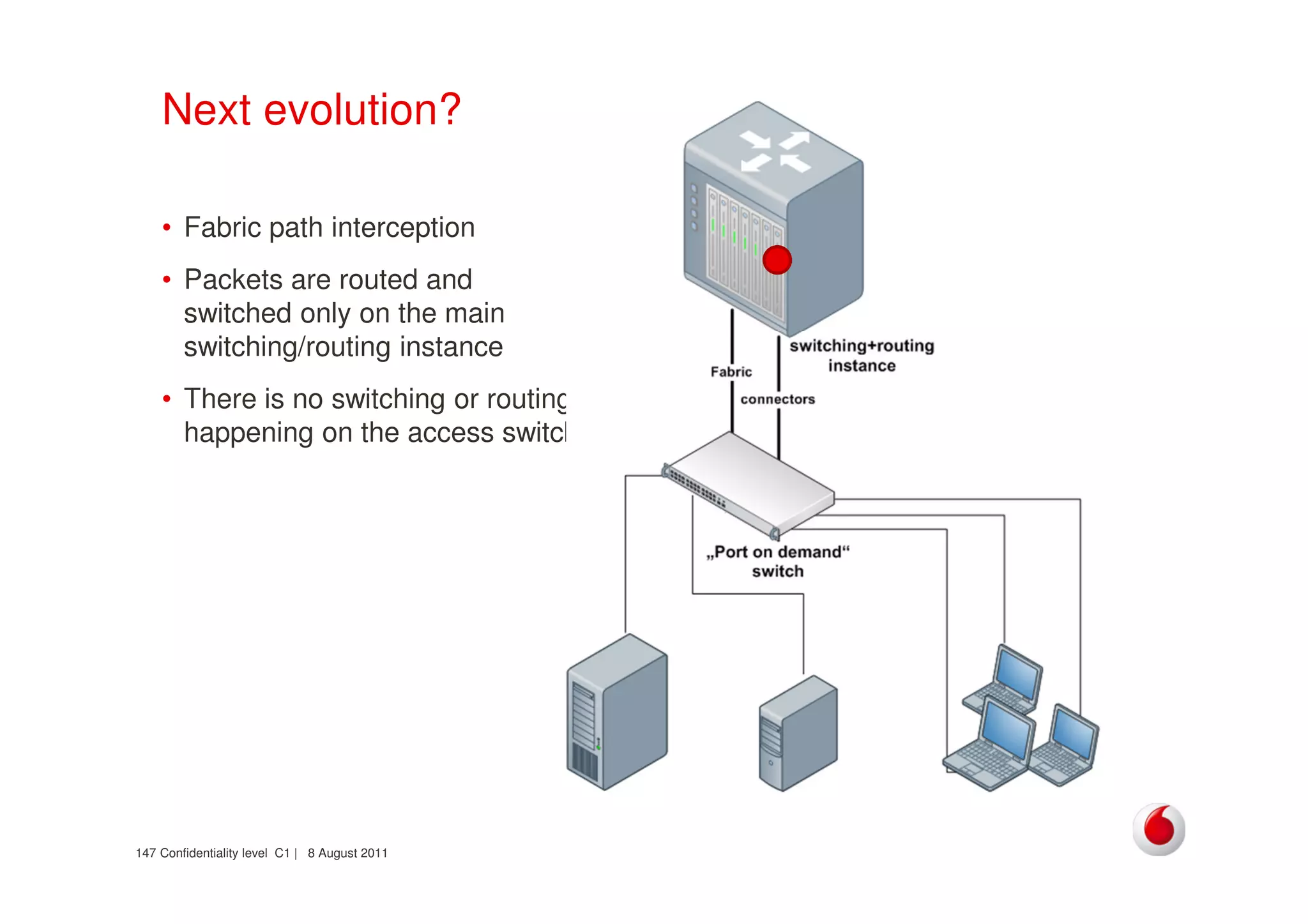
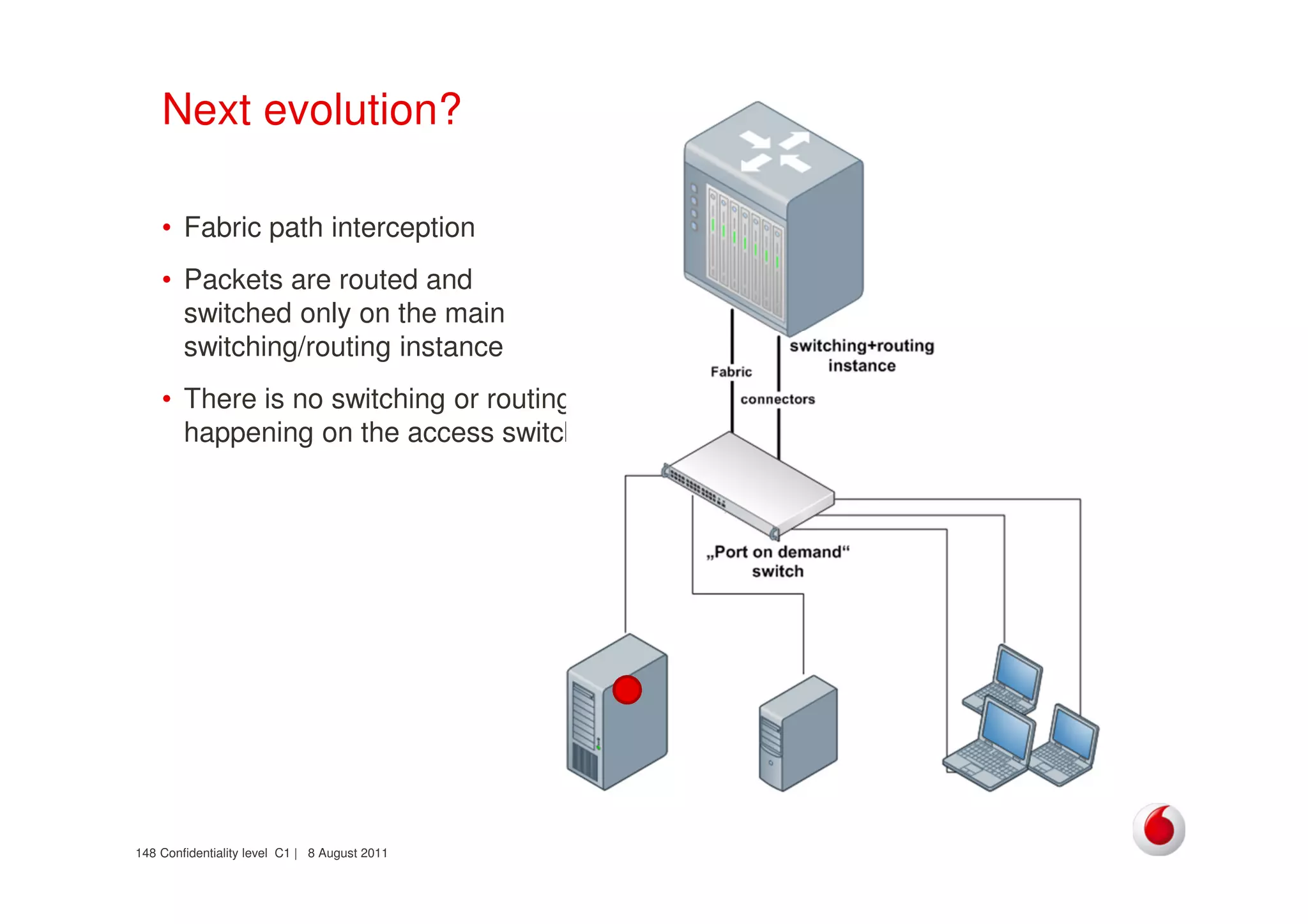
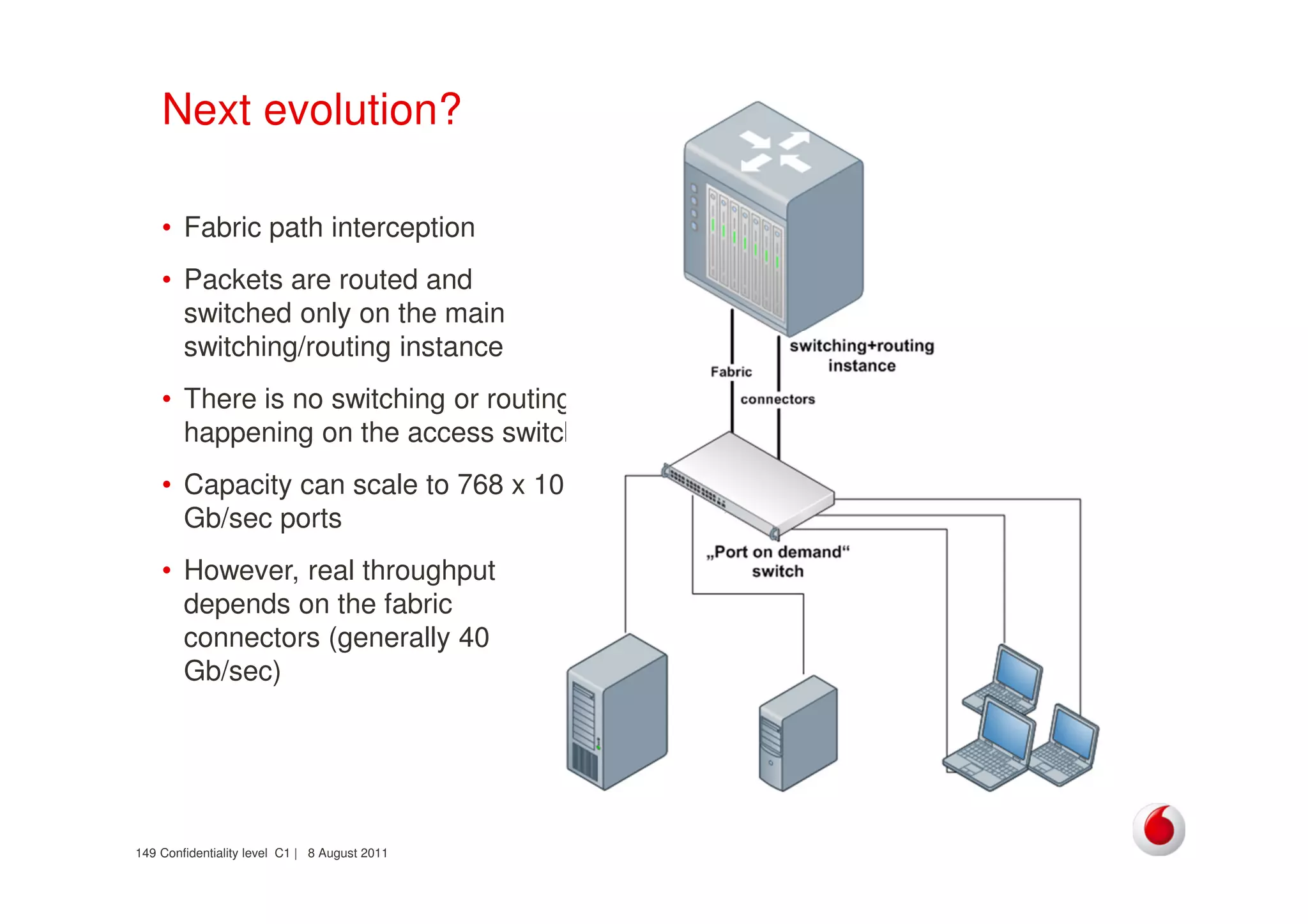
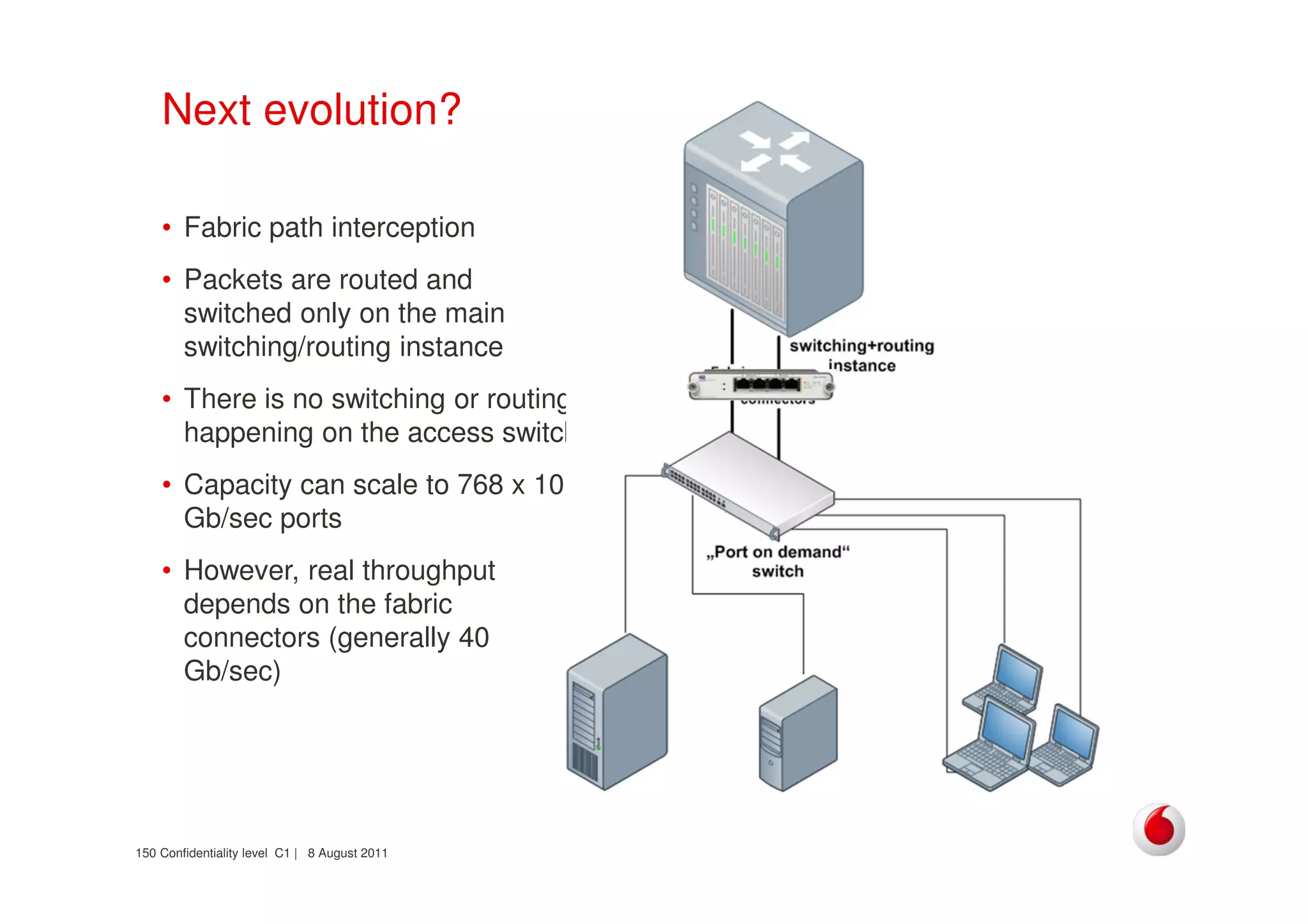
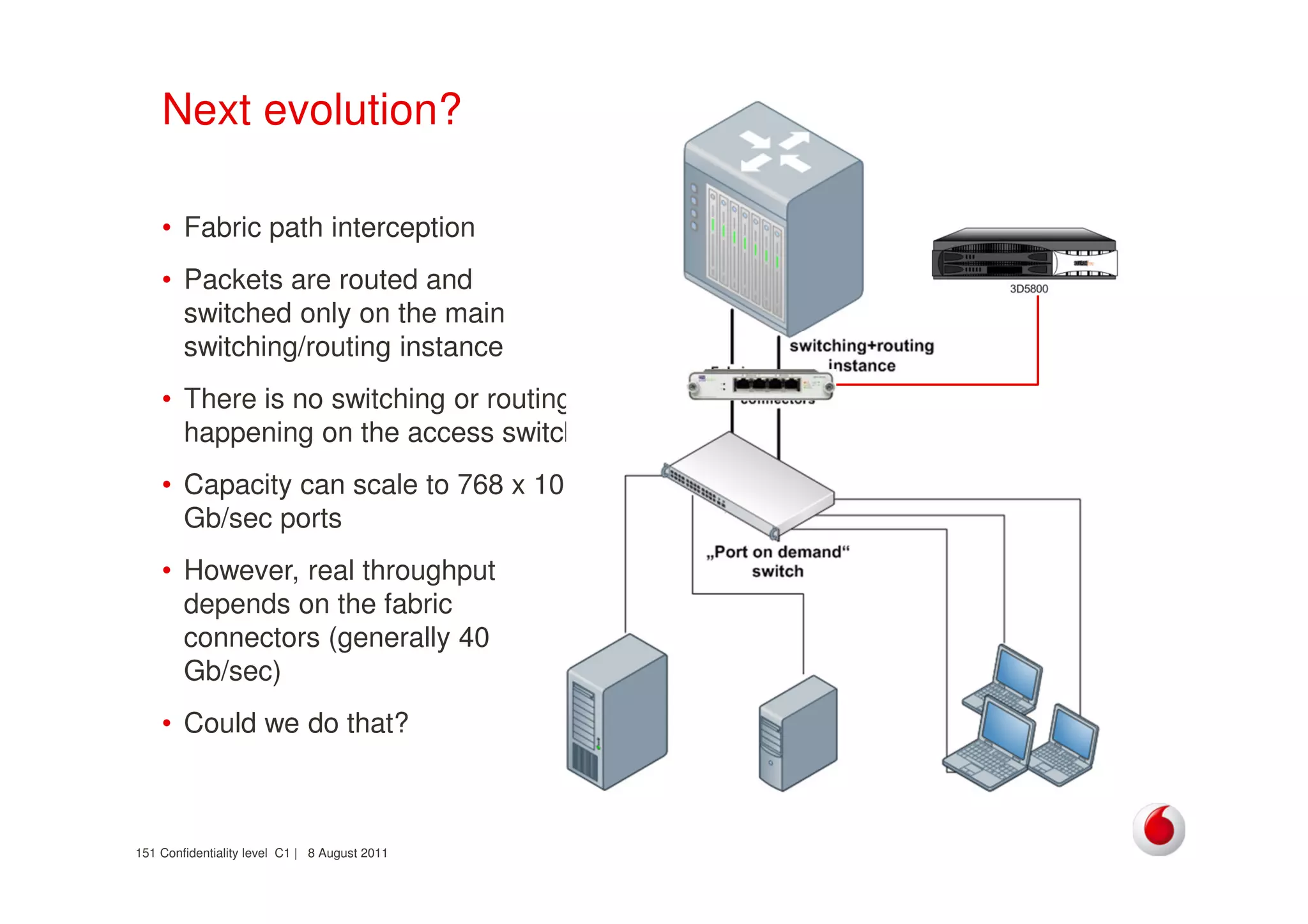
The document discusses identifying networks in a complex company. It describes challenges with the company's asset database, including many outdated or duplicate entries for operating systems and support groups. It also notes the network maps and asset database do not have a clear correspondence to the physical network. The document advocates identifying currently used versus legacy systems, their functions, vulnerabilities, and how they are arranged on the network. It contrasts firewall-based versus routing-based network planning and some pros and cons of the firewall approach.