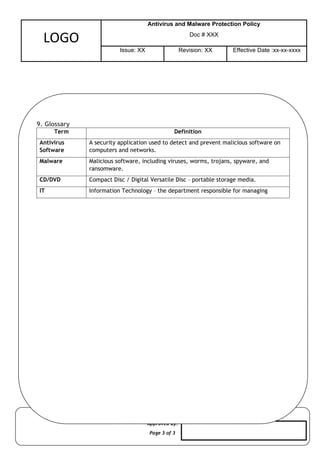
The Antivirus and Malware Protection Policy defines the procedures and responsibilities for protecting organizational systems and data from viruses, spyware, ransomware, and other forms of malicious software. It includes guidelines for installing and updating antivirus software, scanning devices regularly, user awareness, incident response, and reporting suspicious activity. This policy ensures a proactive defense against cybersecurity threats and supports the integrity, confidentiality, and availability of IT assets.