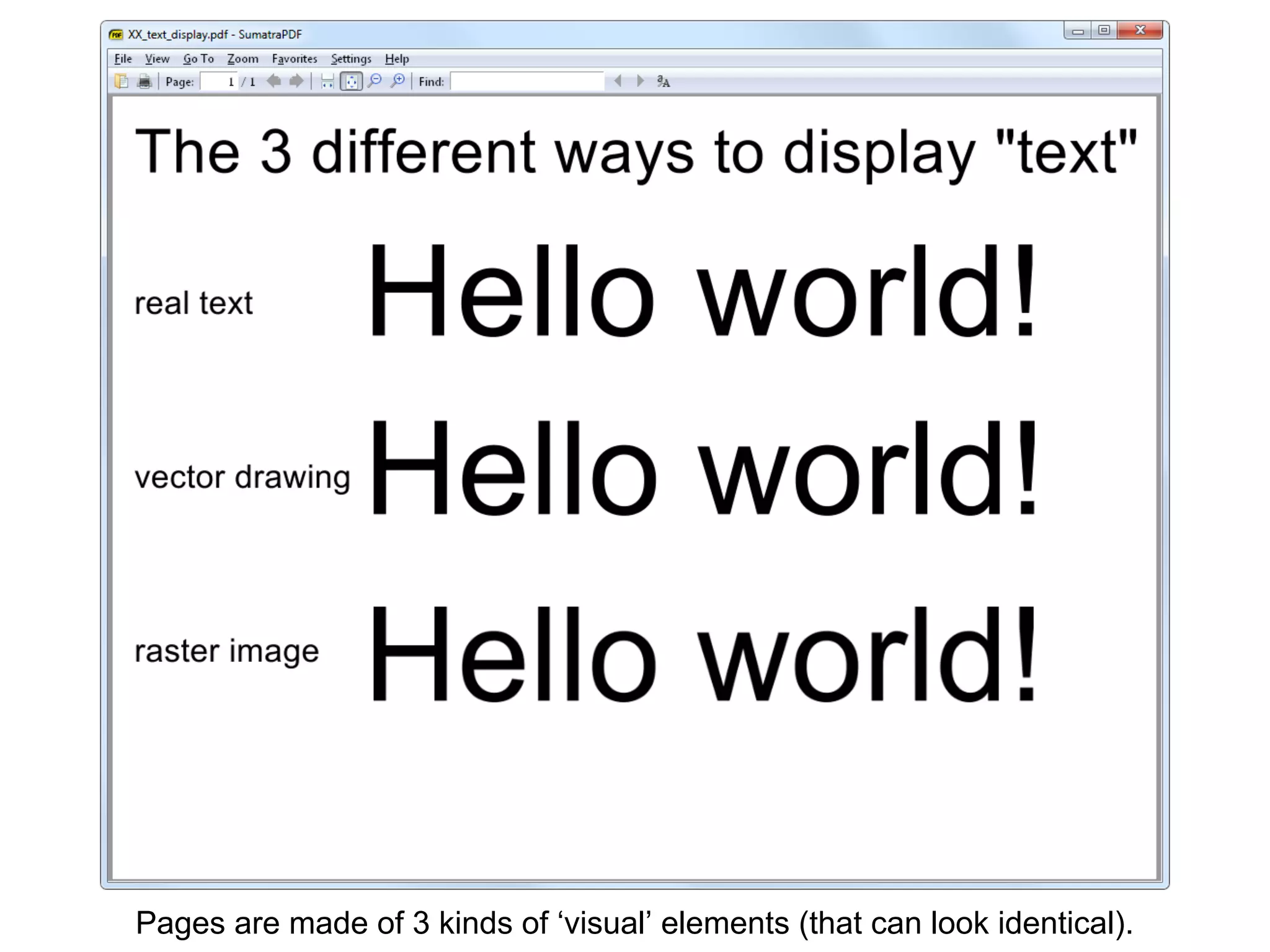
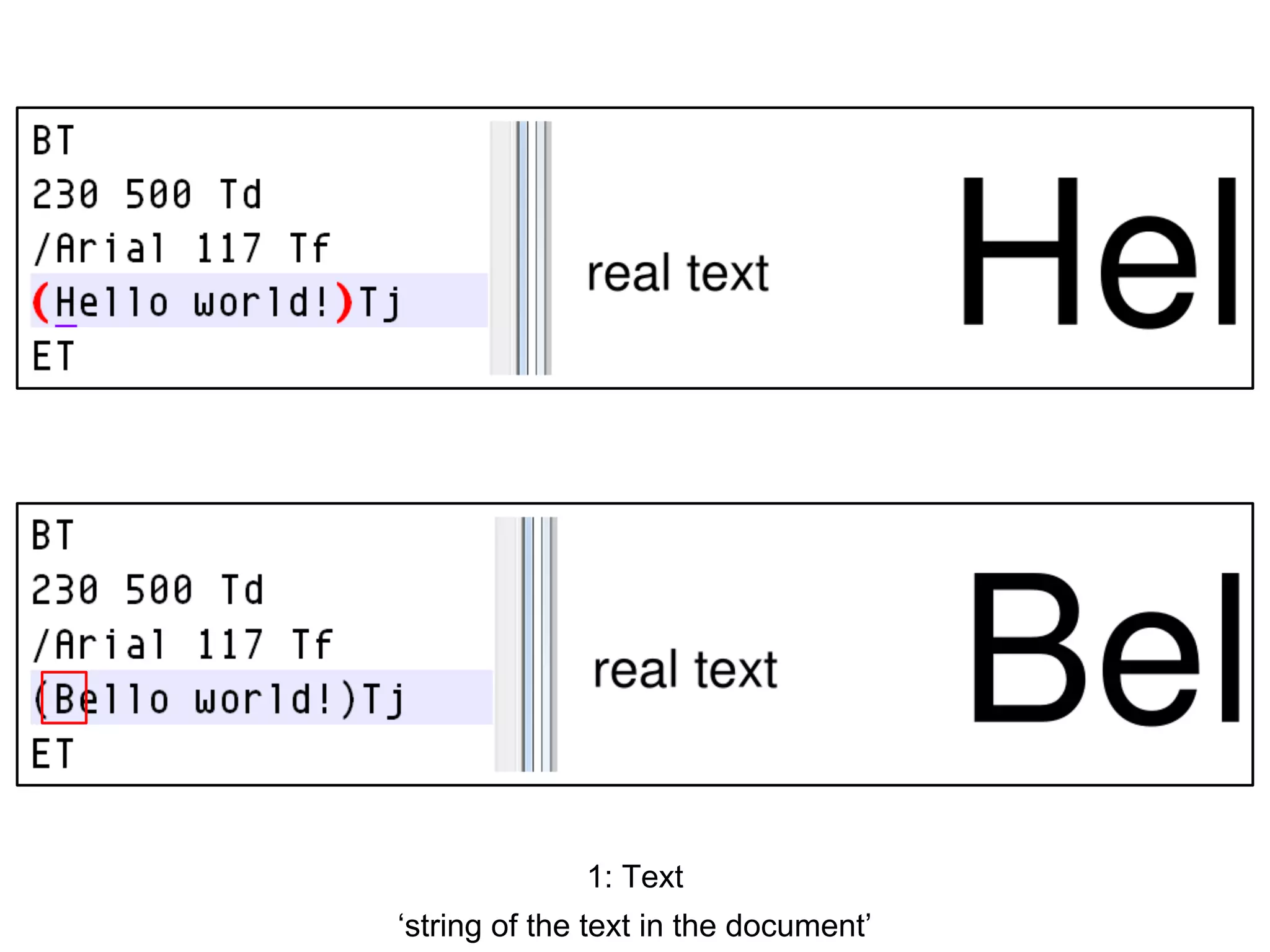
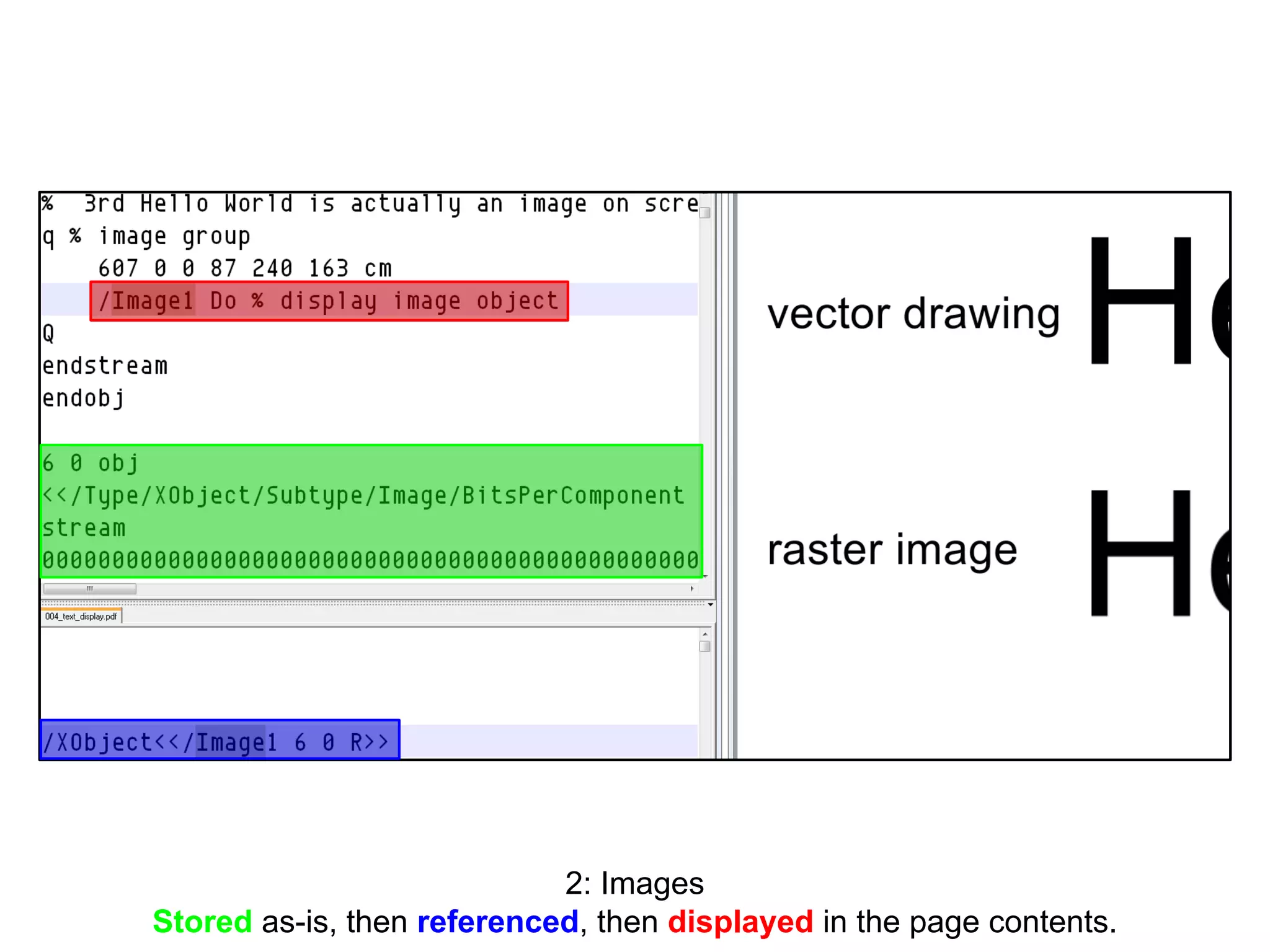
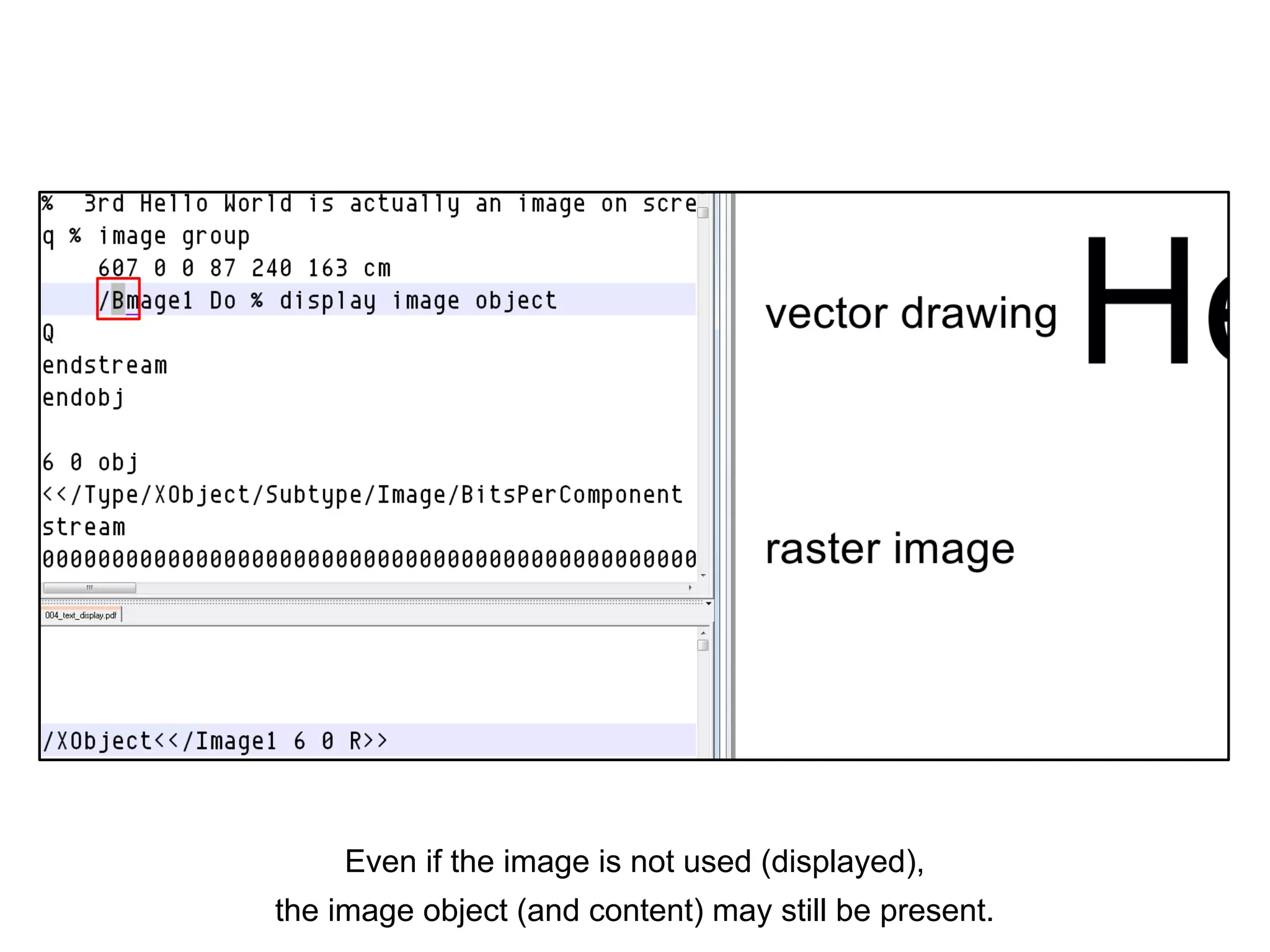
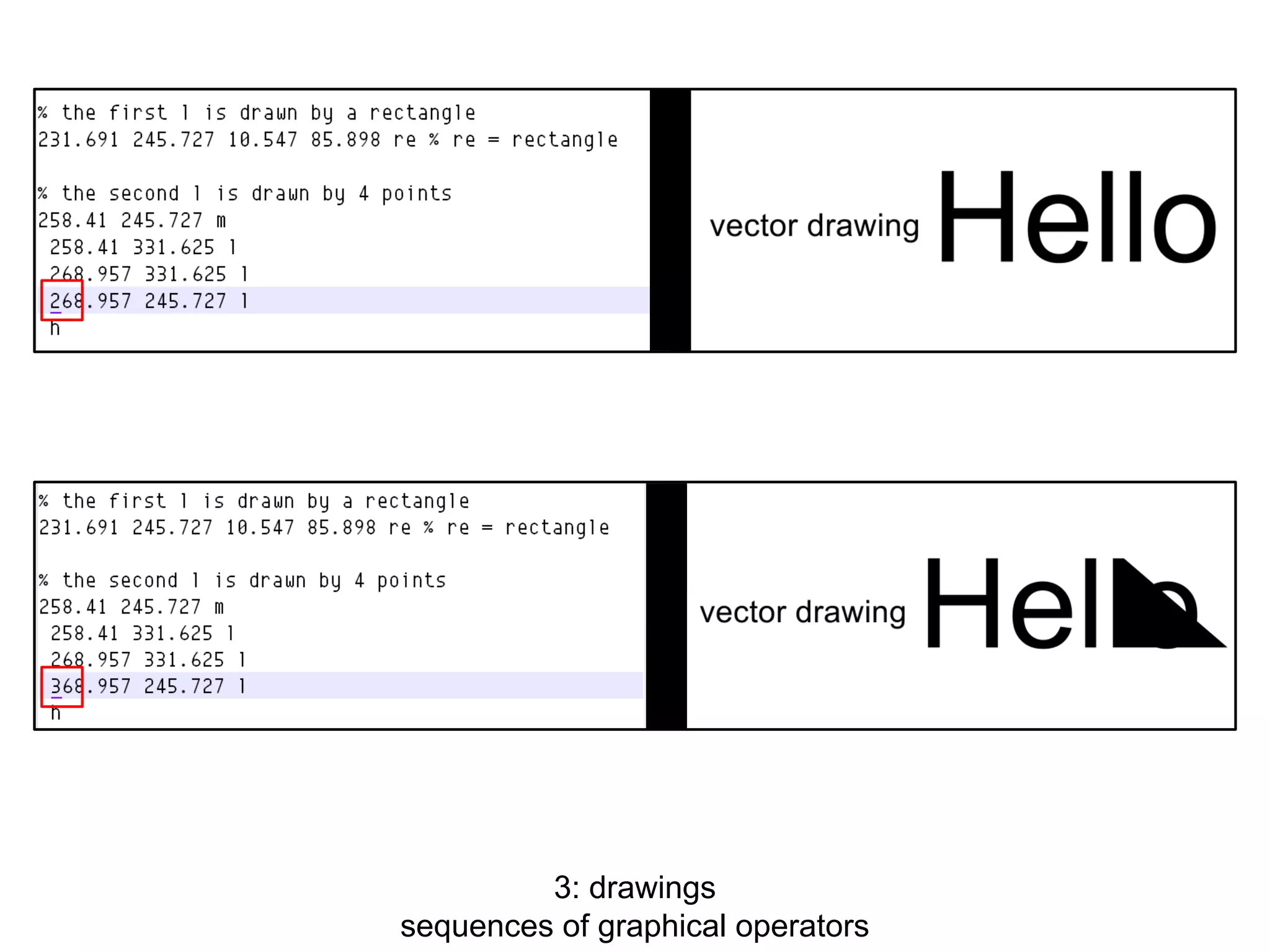
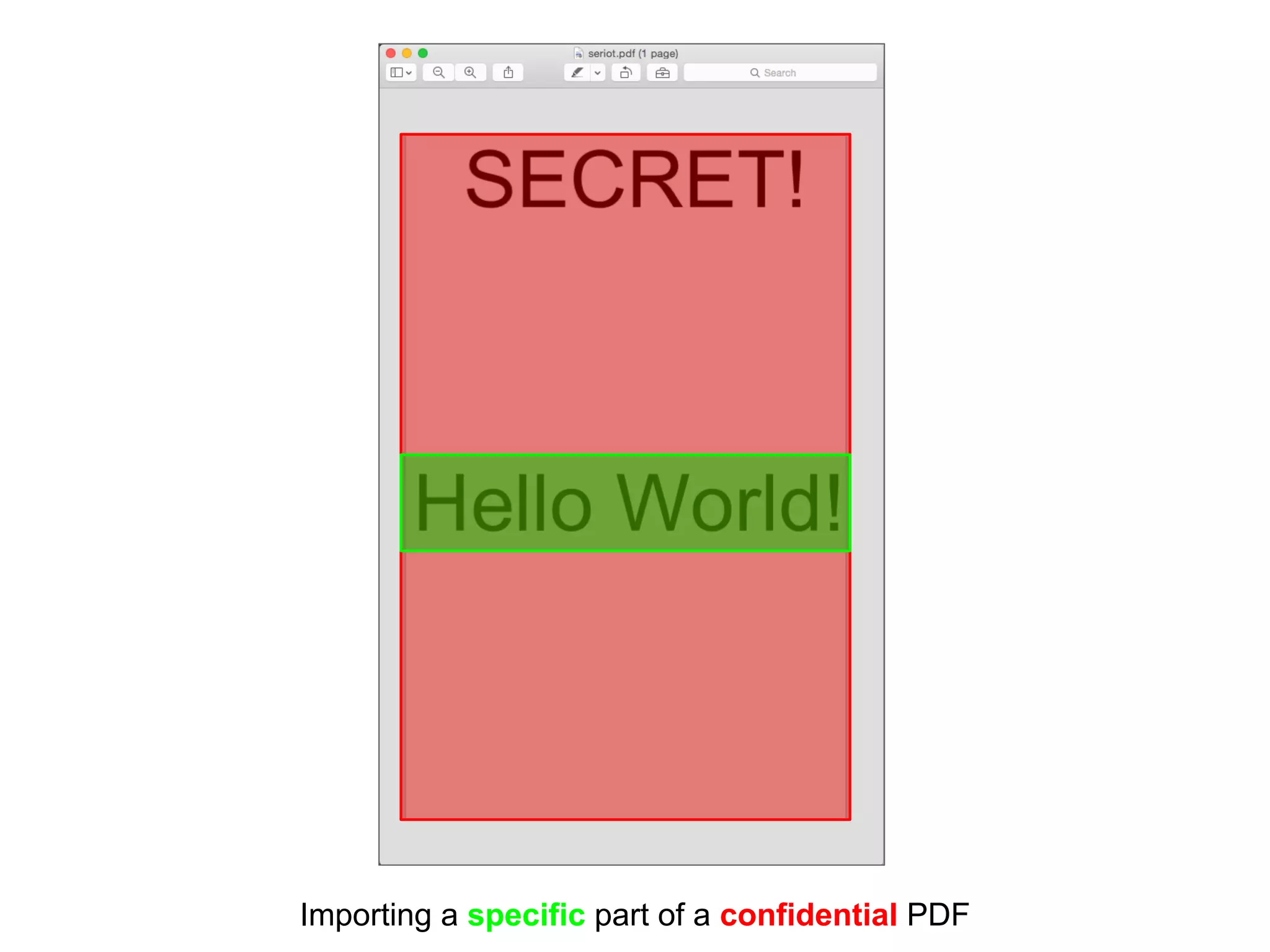
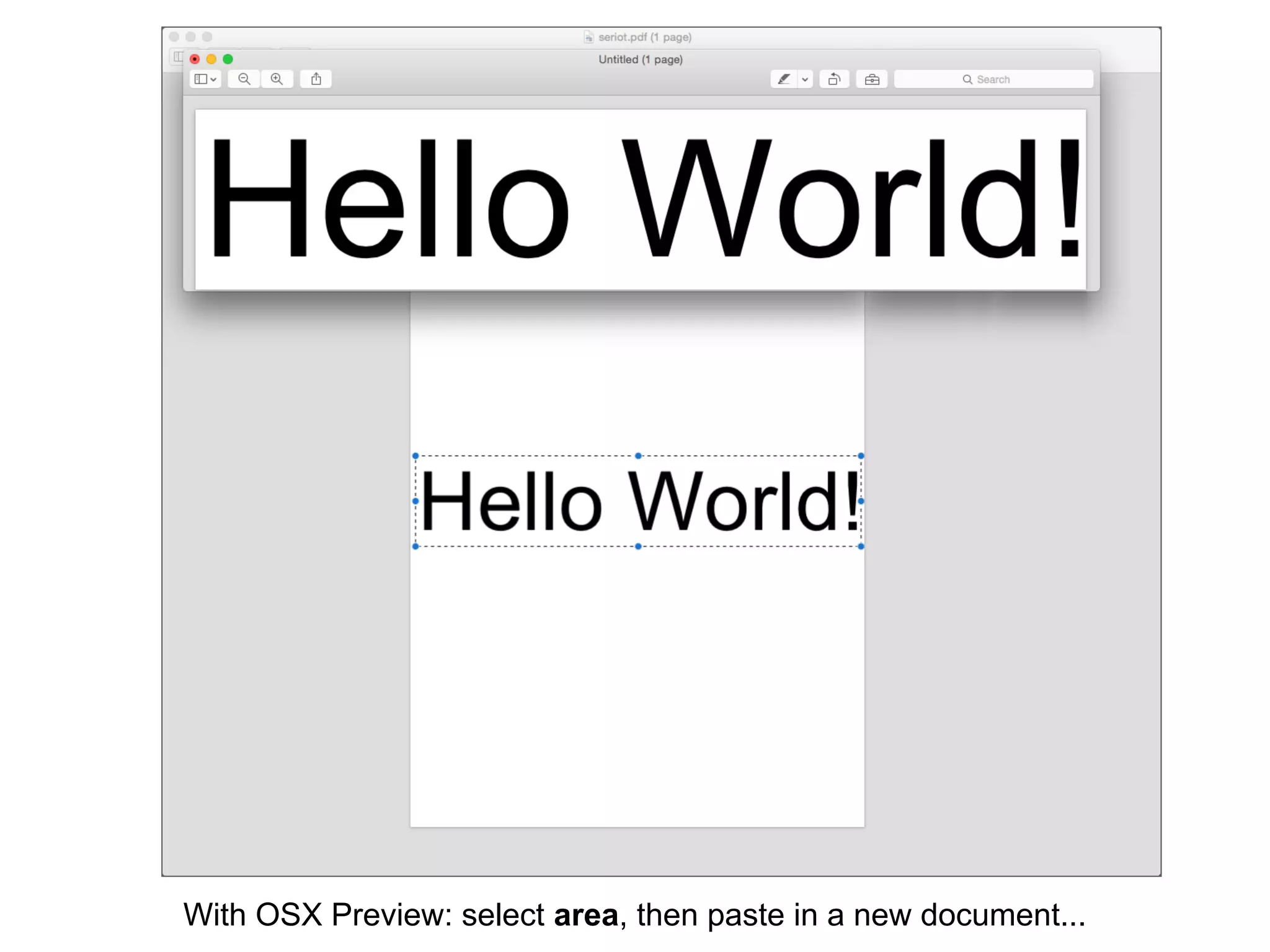
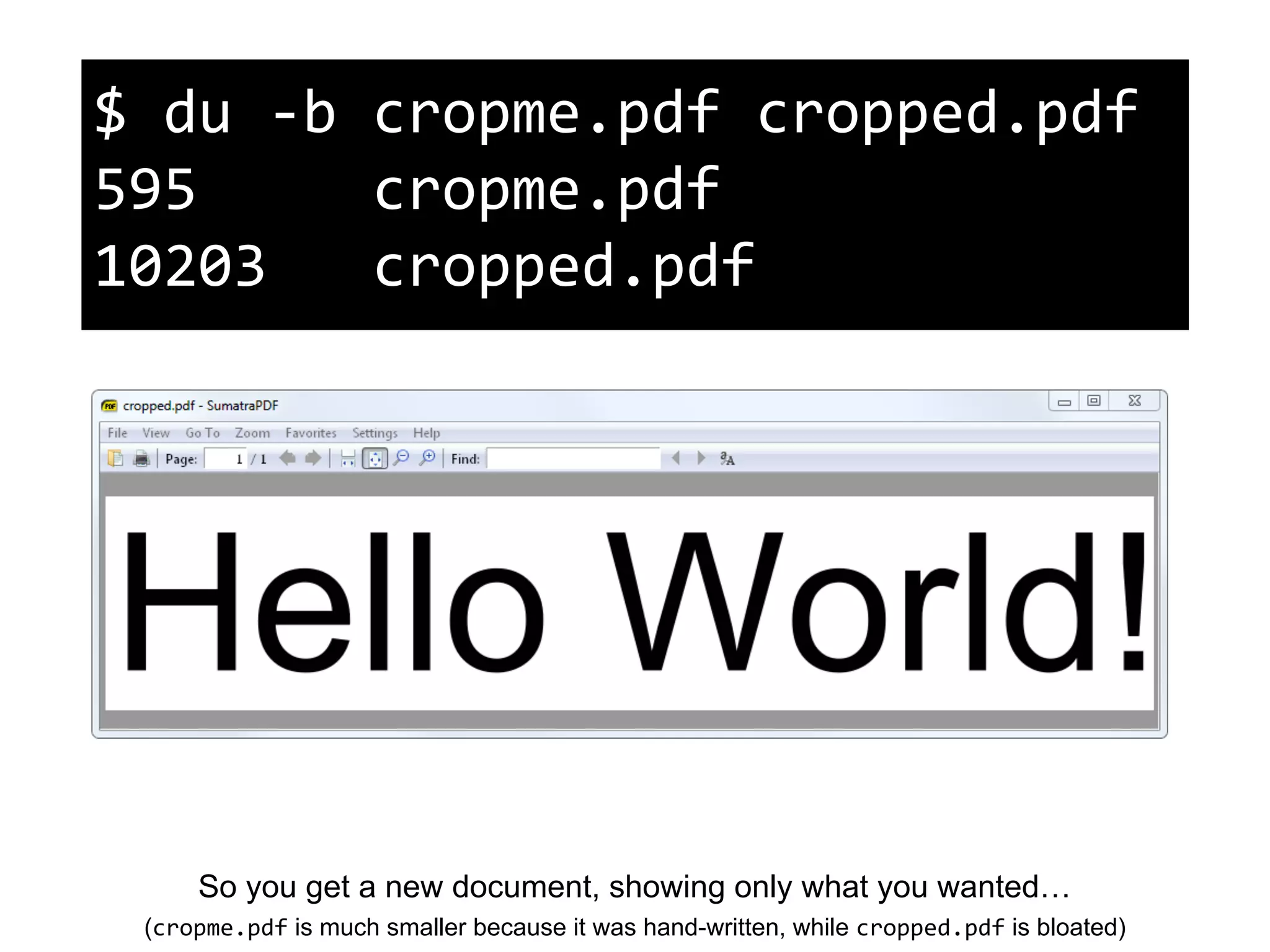
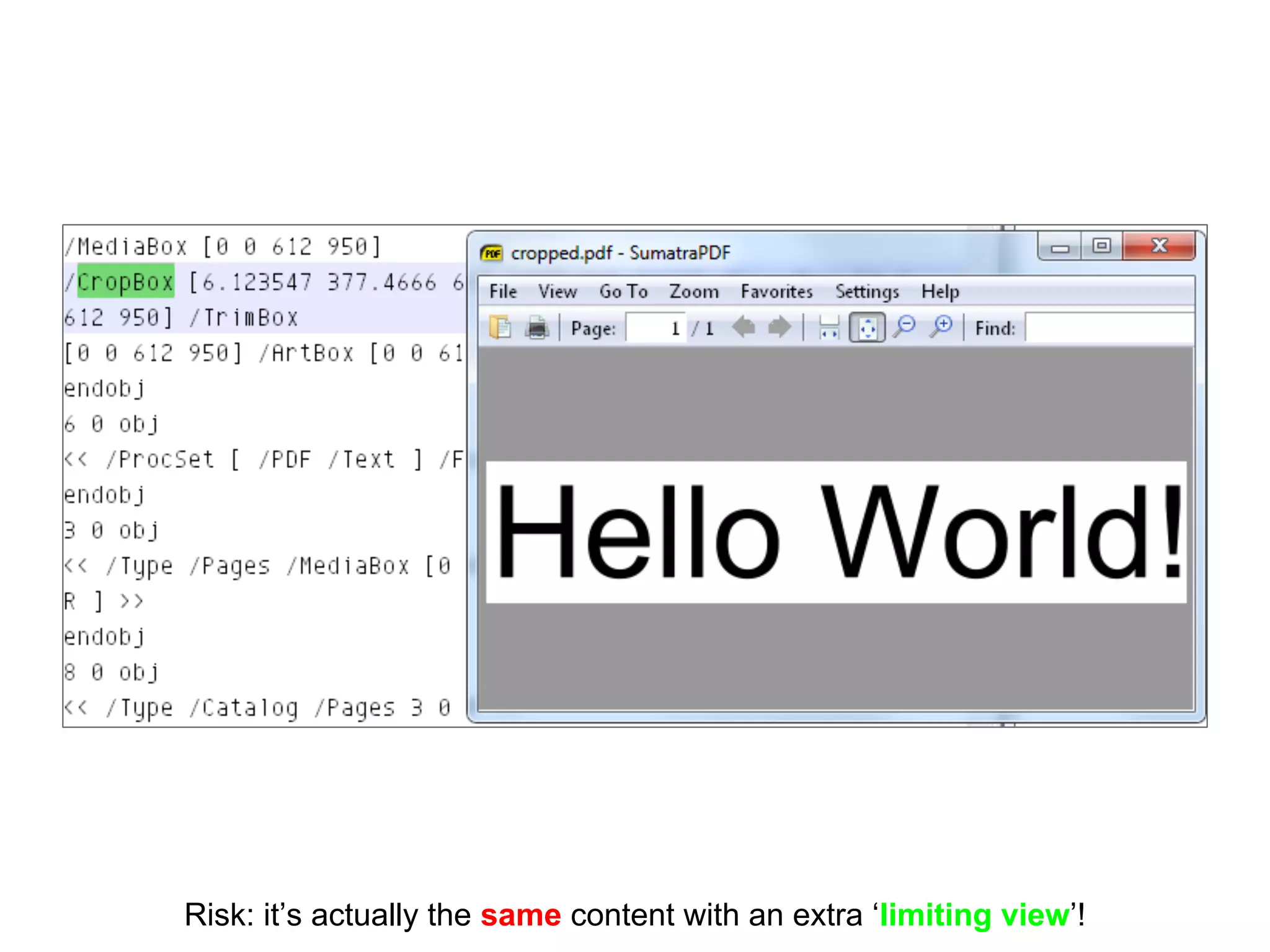
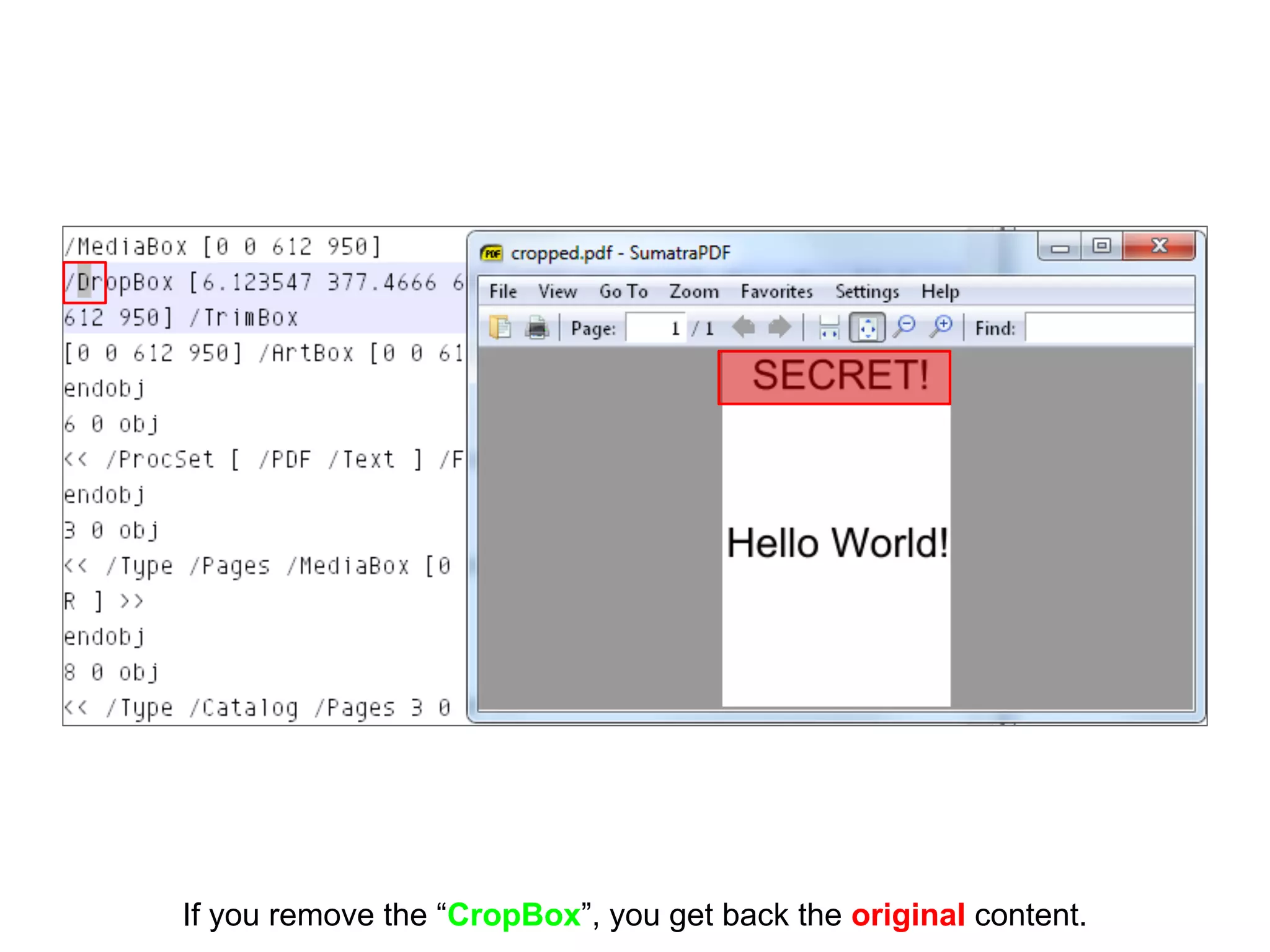
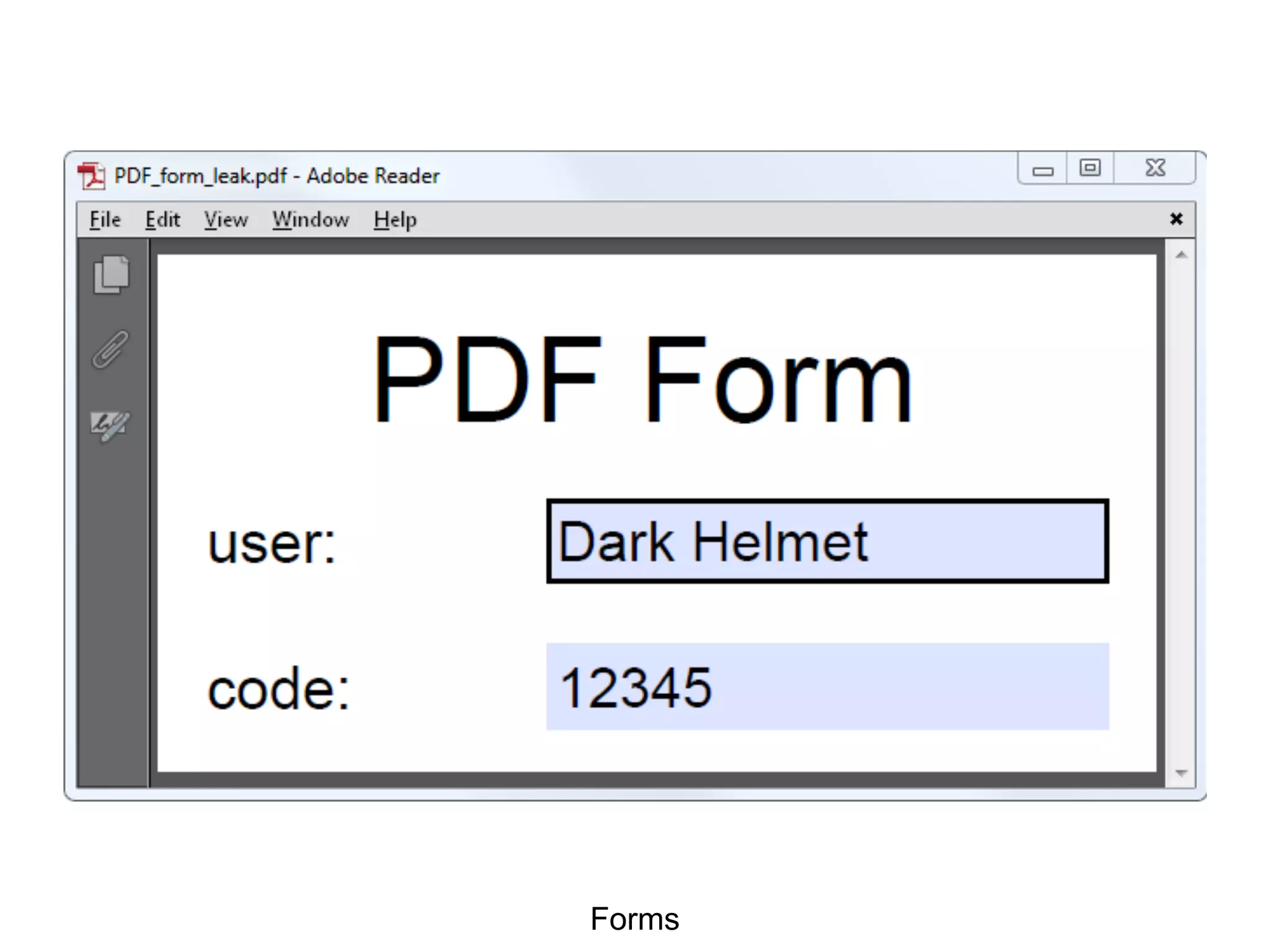
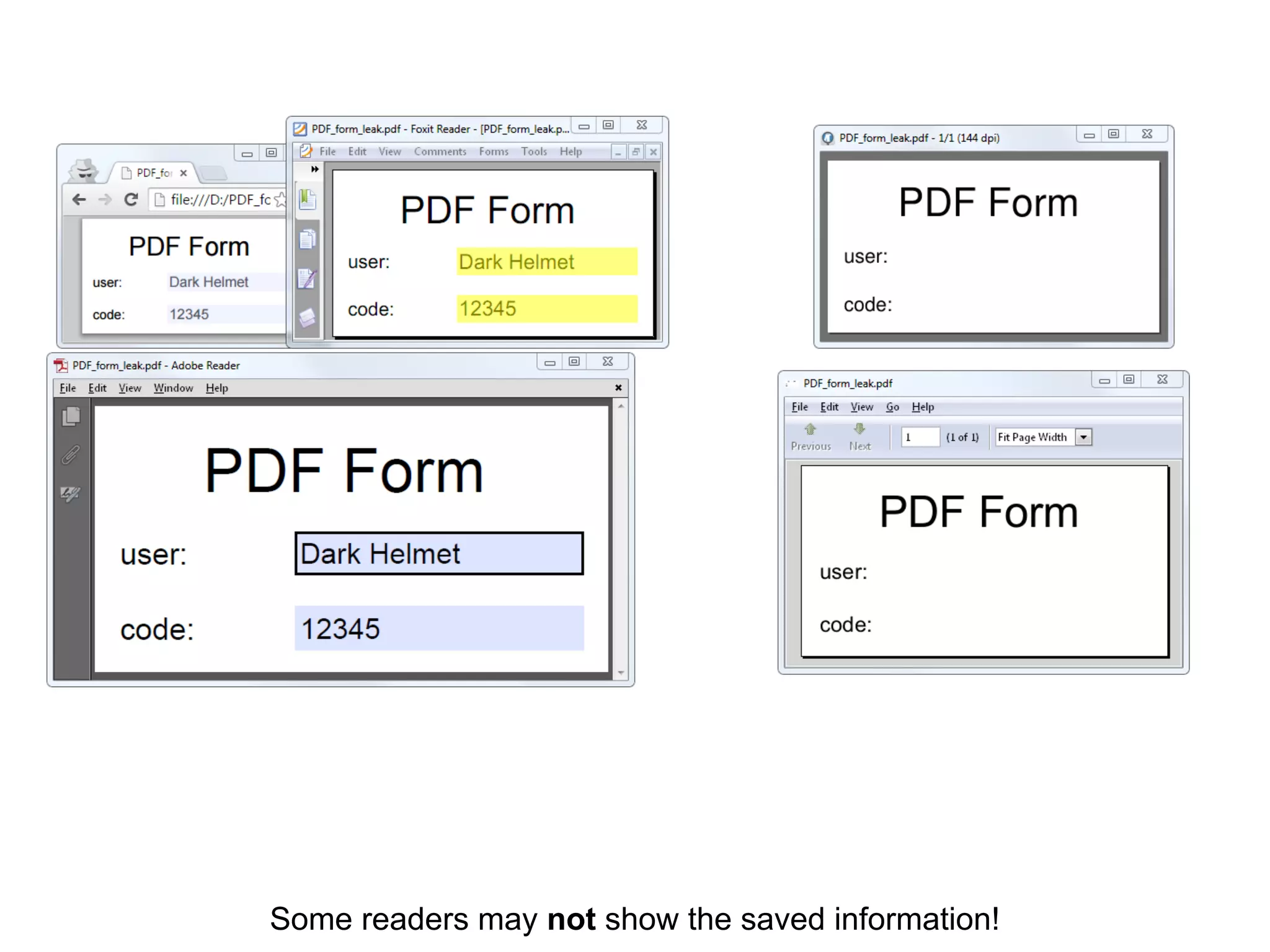
This document discusses potential leaks that can occur from PDF documents, specifically from text, images, and drawings embedded in the pages. Even if text is invisible, images are not displayed, or drawings are covered, this information can still be extracted from the PDF. Importing or copying parts of a PDF does not necessarily limit the content, as the full document is often brought in and only a "limiting view" is applied. The only fully reliable way to prevent leaks is to convert the PDF pages to individual image files. In general, the PDF format has many issues preventing leaks and poses a large attack surface due to embedded metadata.