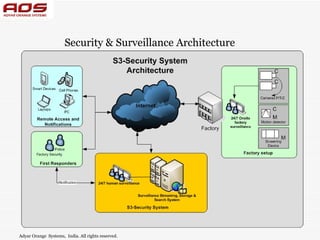
AOS is a company that provides innovative security solutions by combining the latest surveillance and access control technologies. They use IP cameras and cloud storage to provide remote video monitoring. AOS also offers on-site security personnel and a remote monitoring team to watch client video feeds in real-time. Their solutions are customized to each client's needs and provide multiple layers of security through electronic and human monitoring.