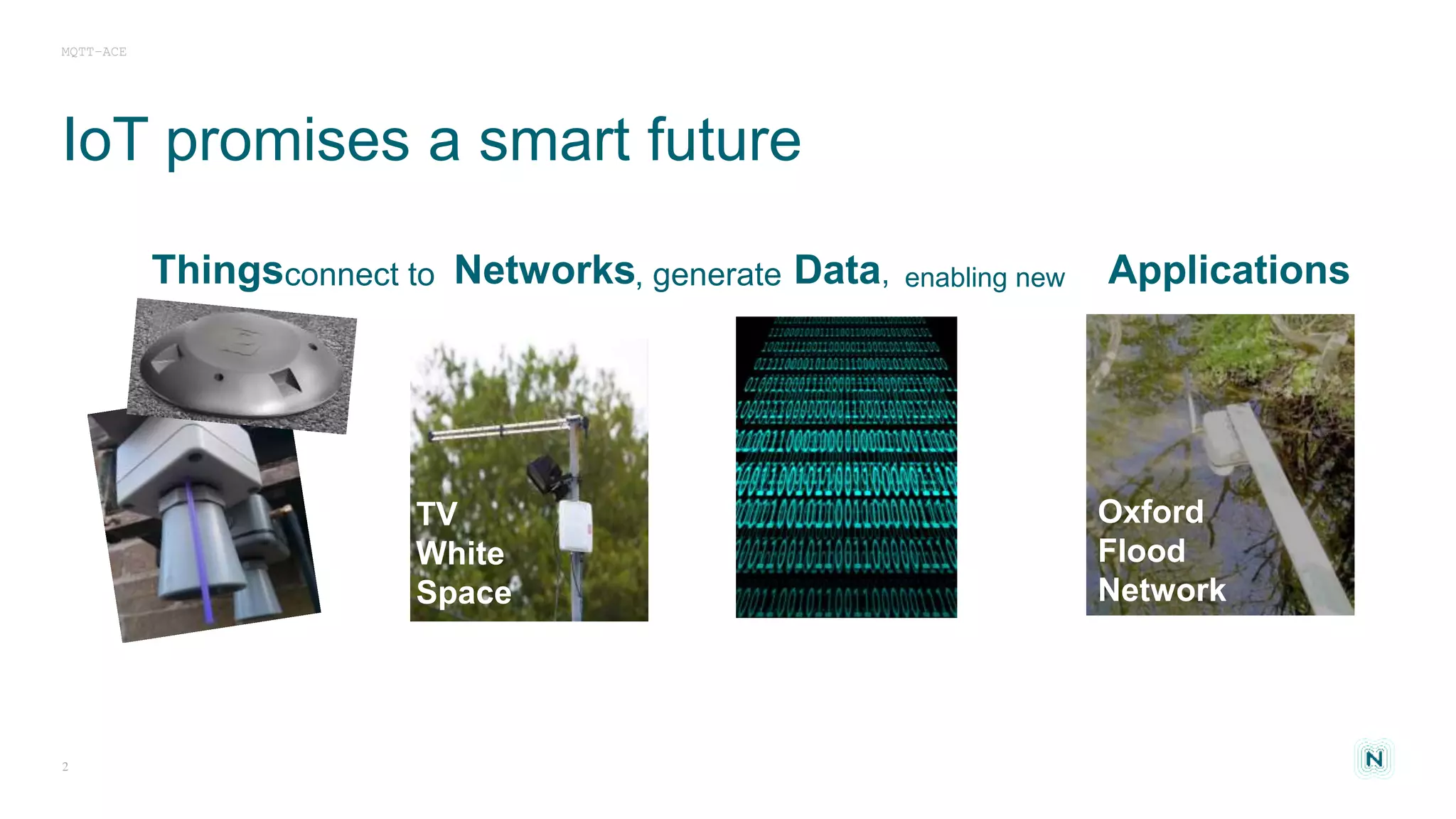
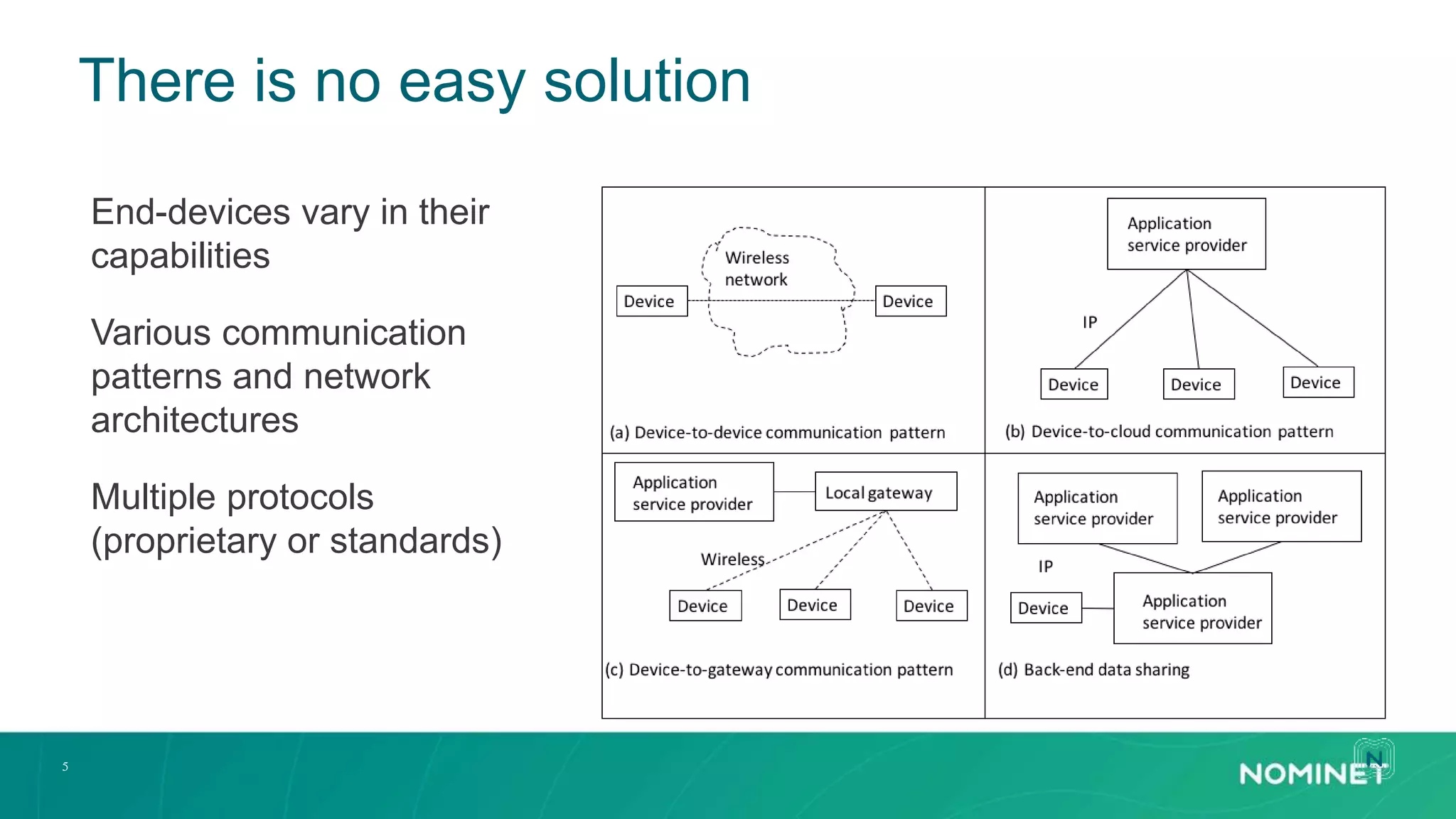
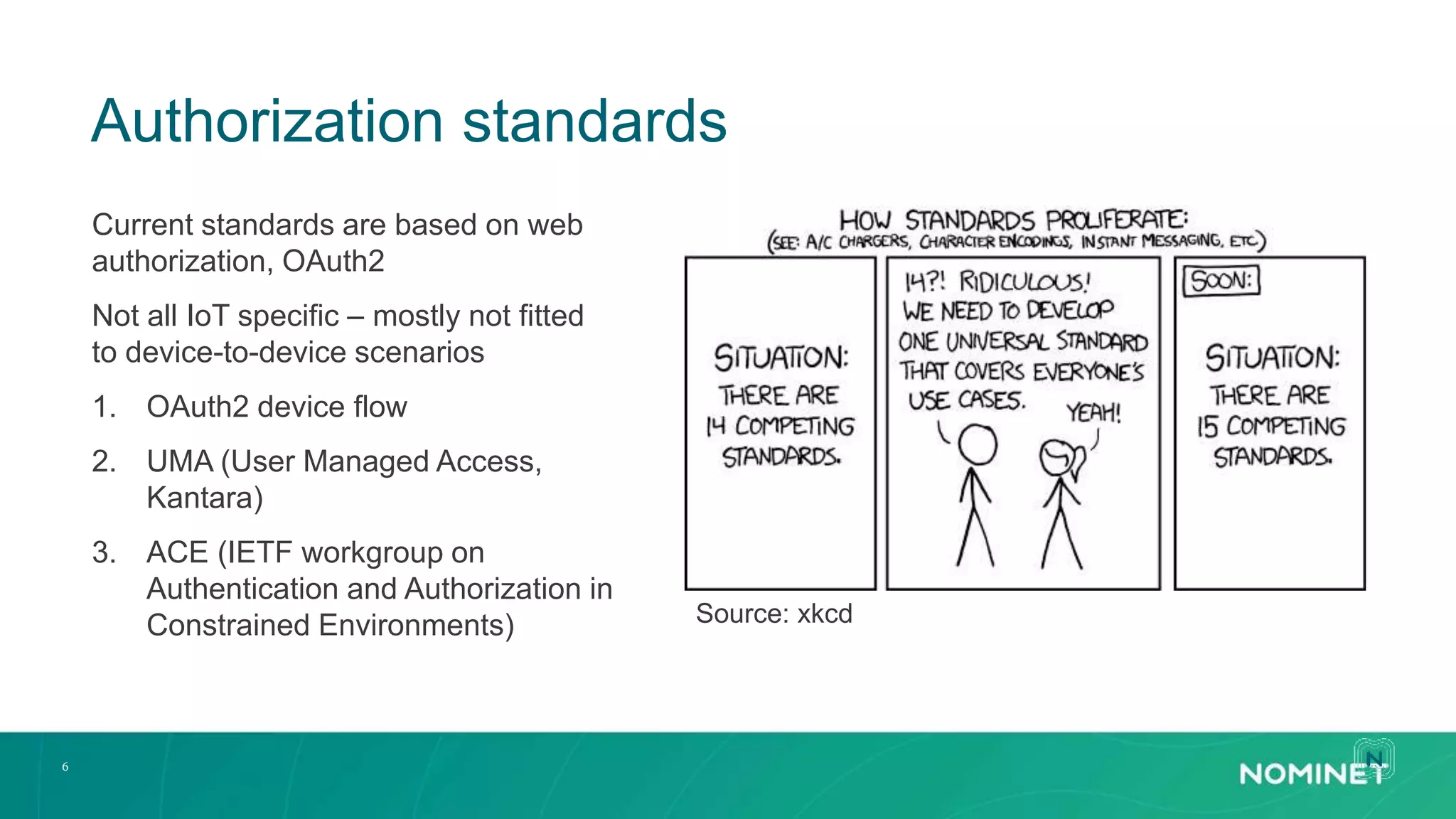
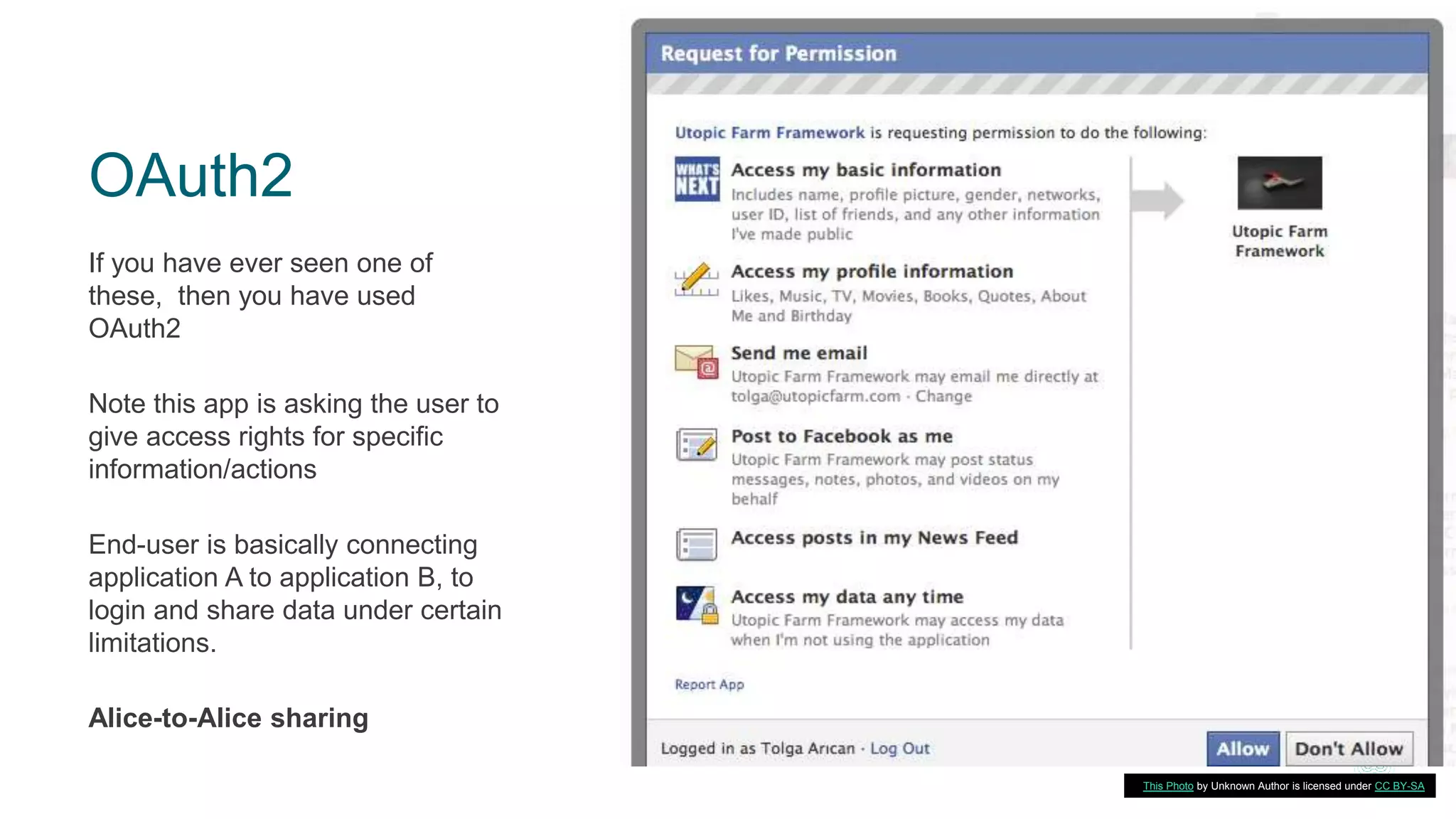
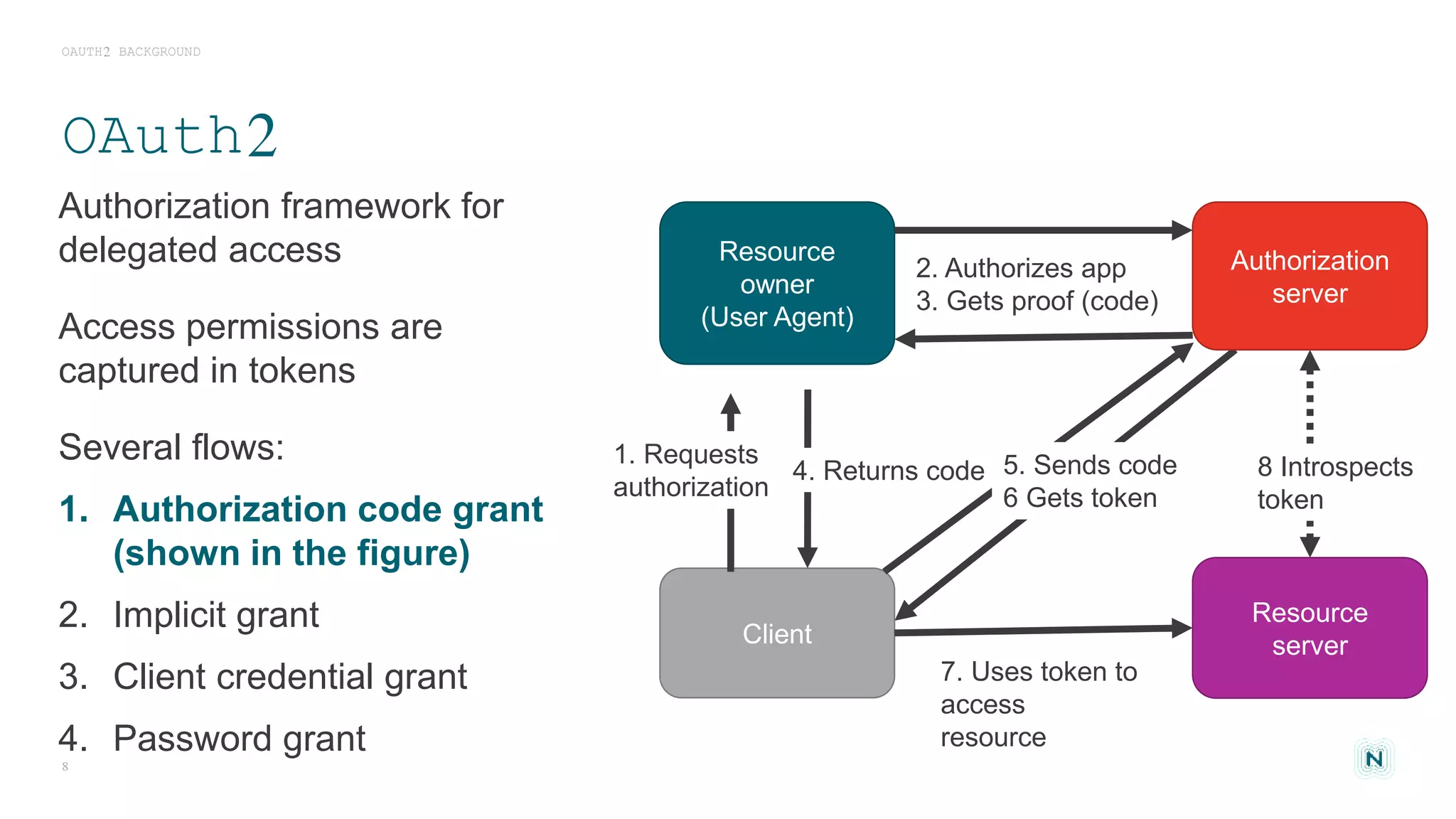
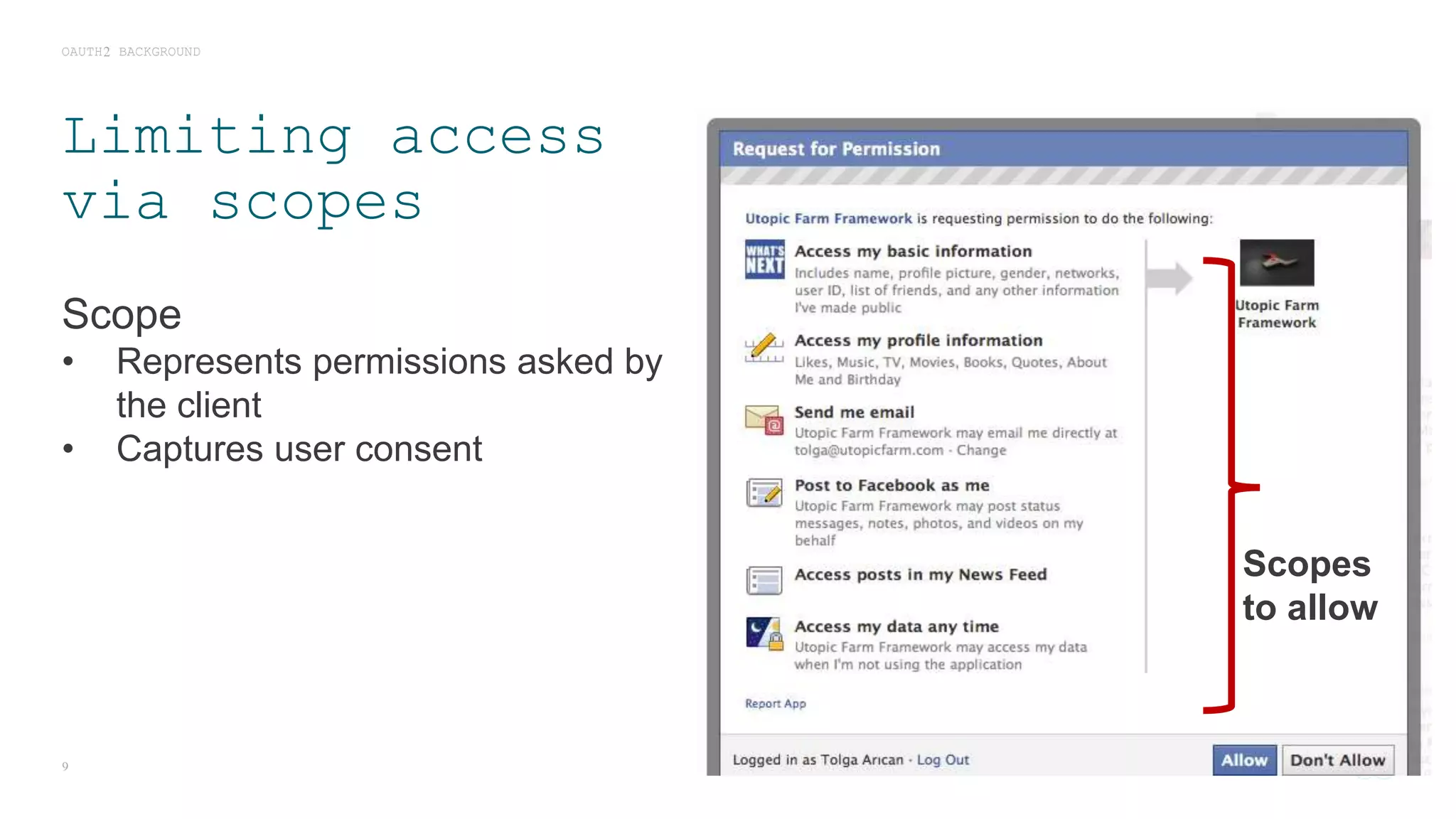
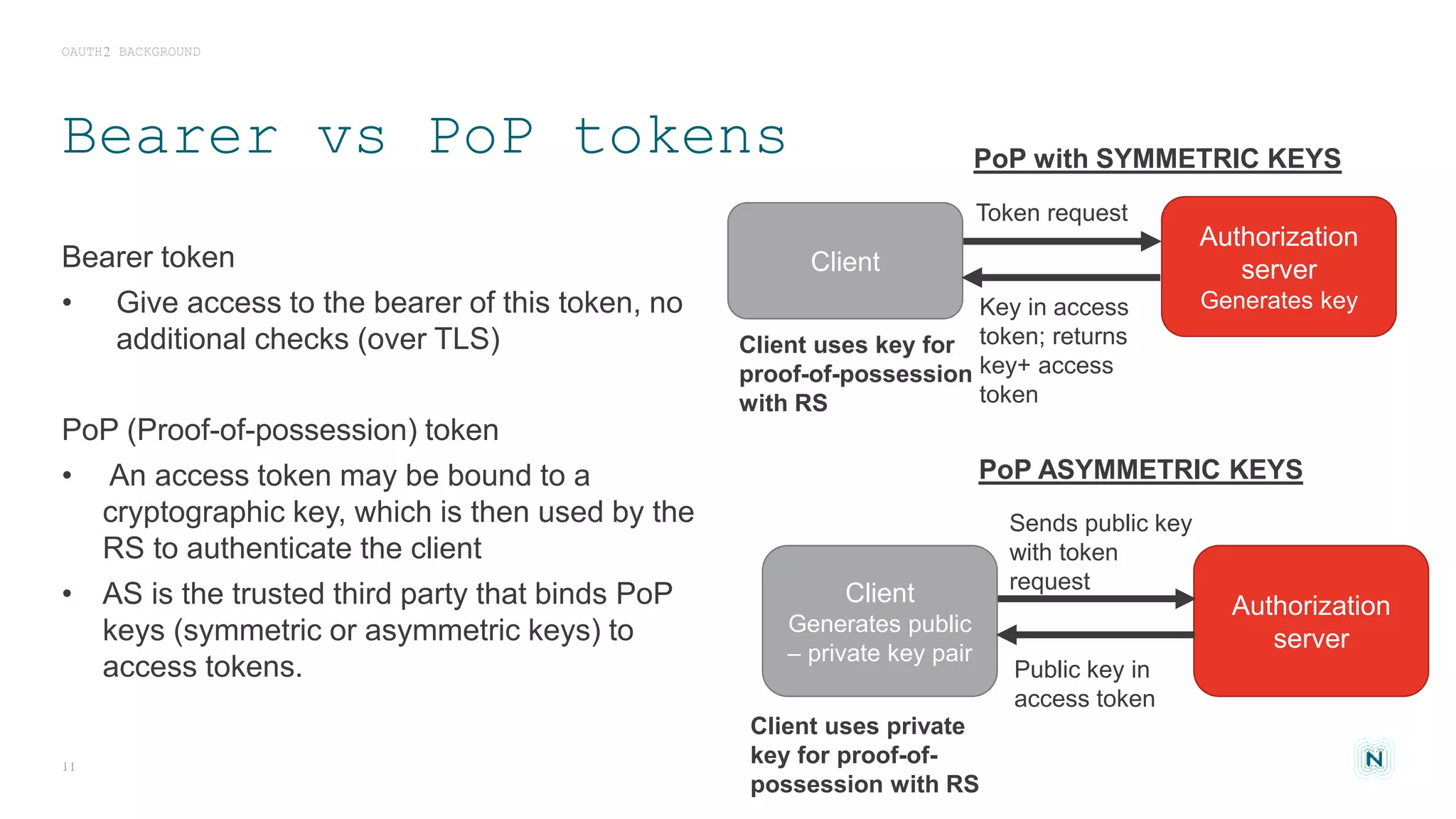
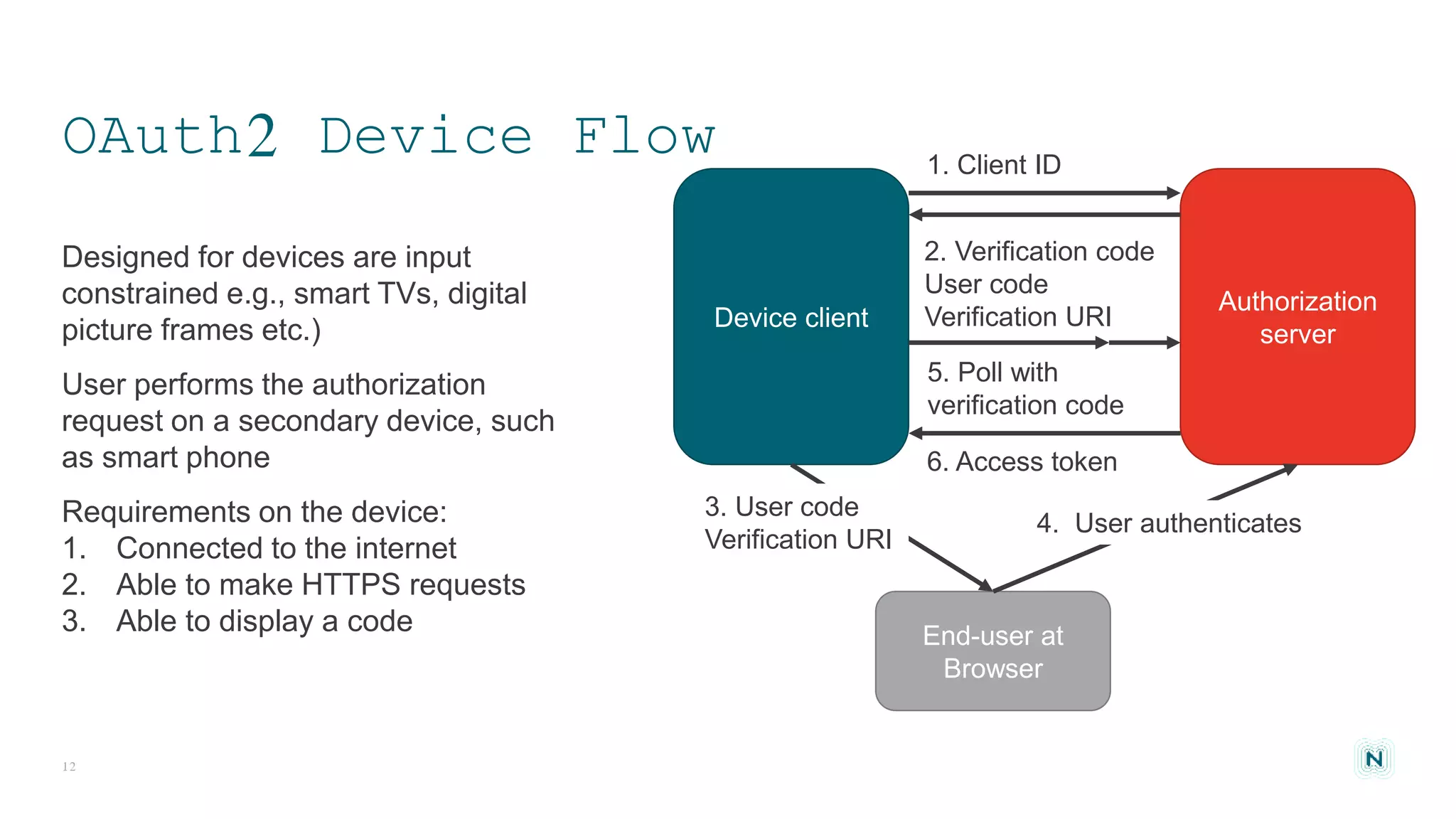
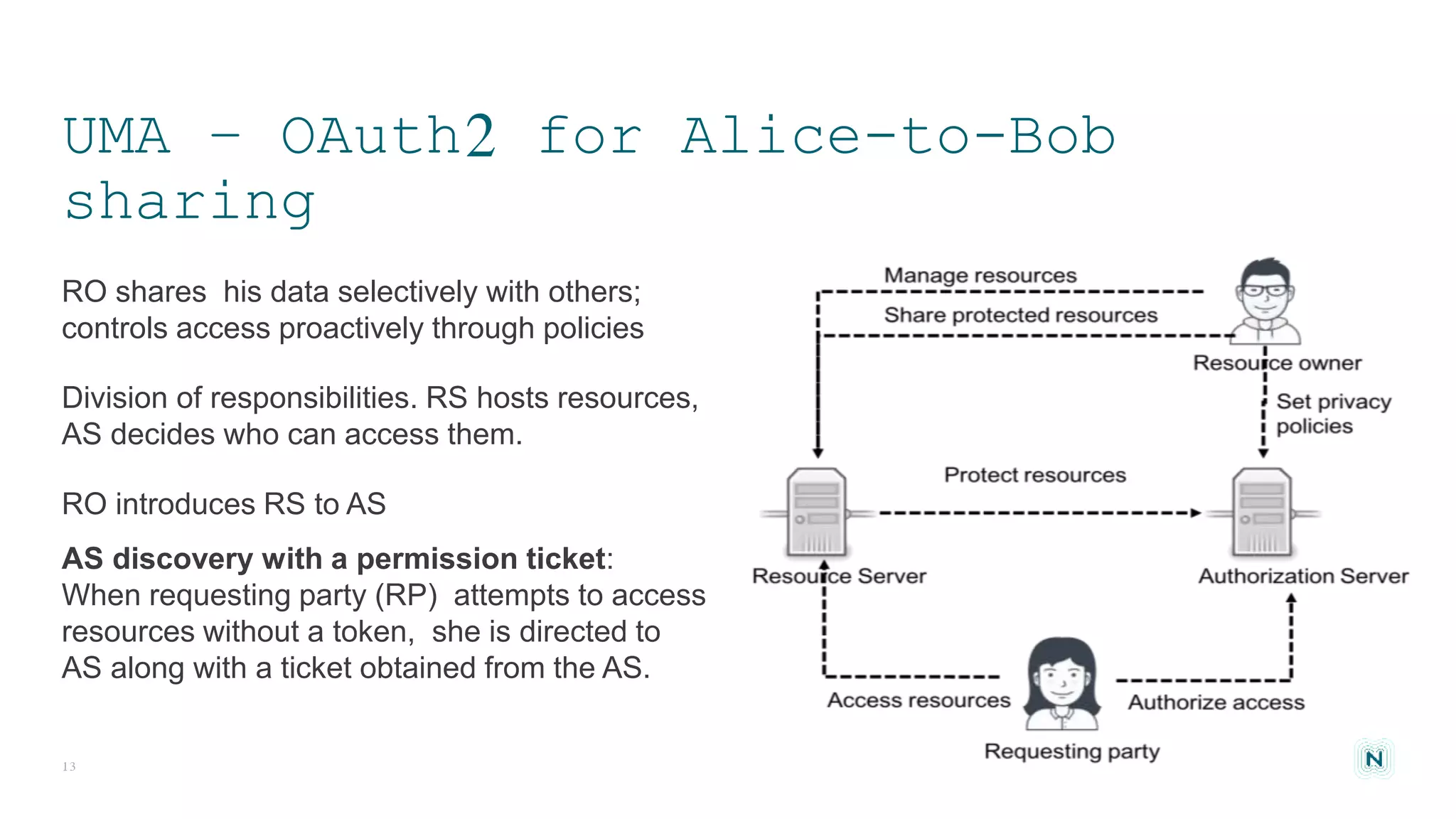
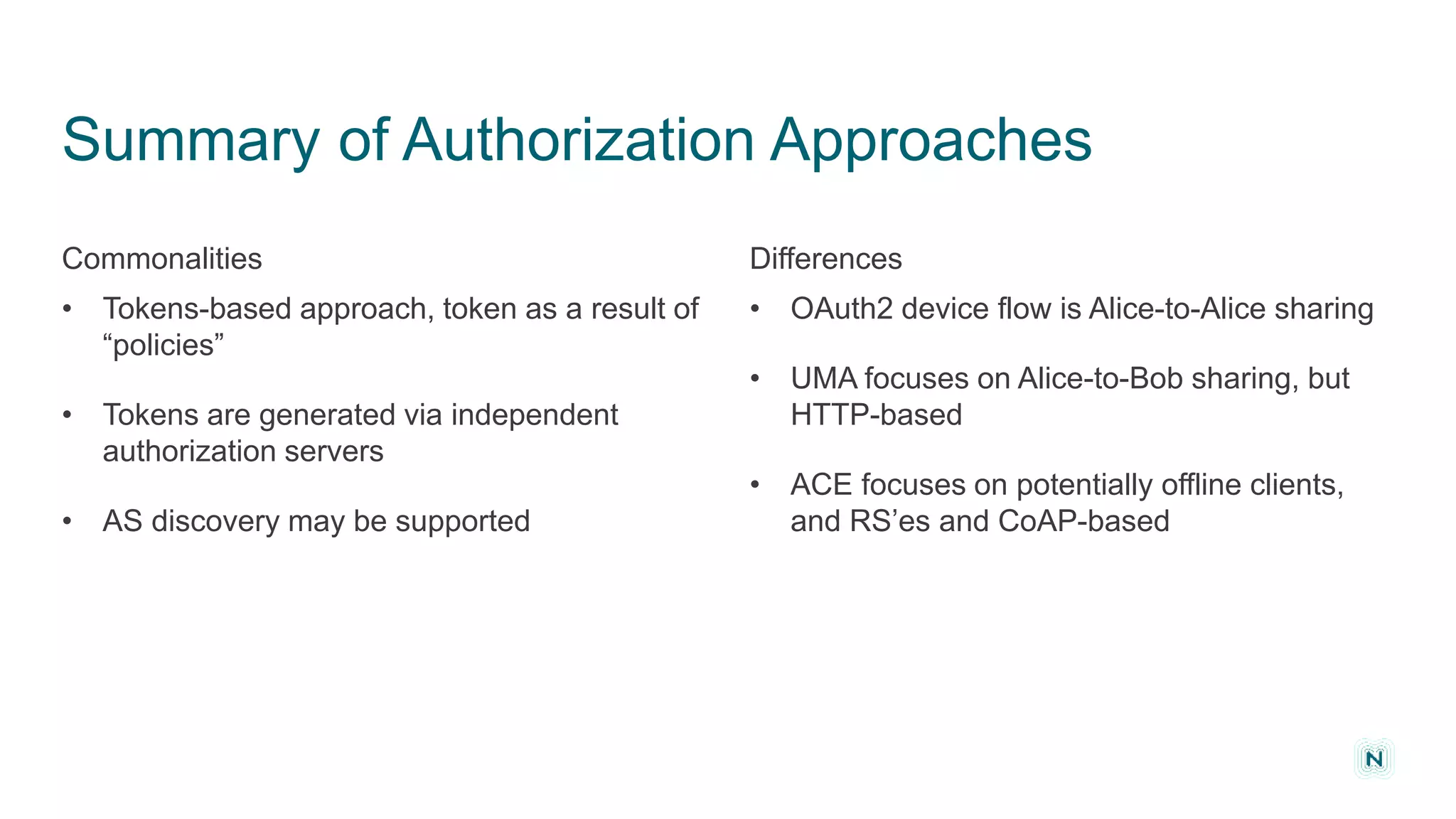
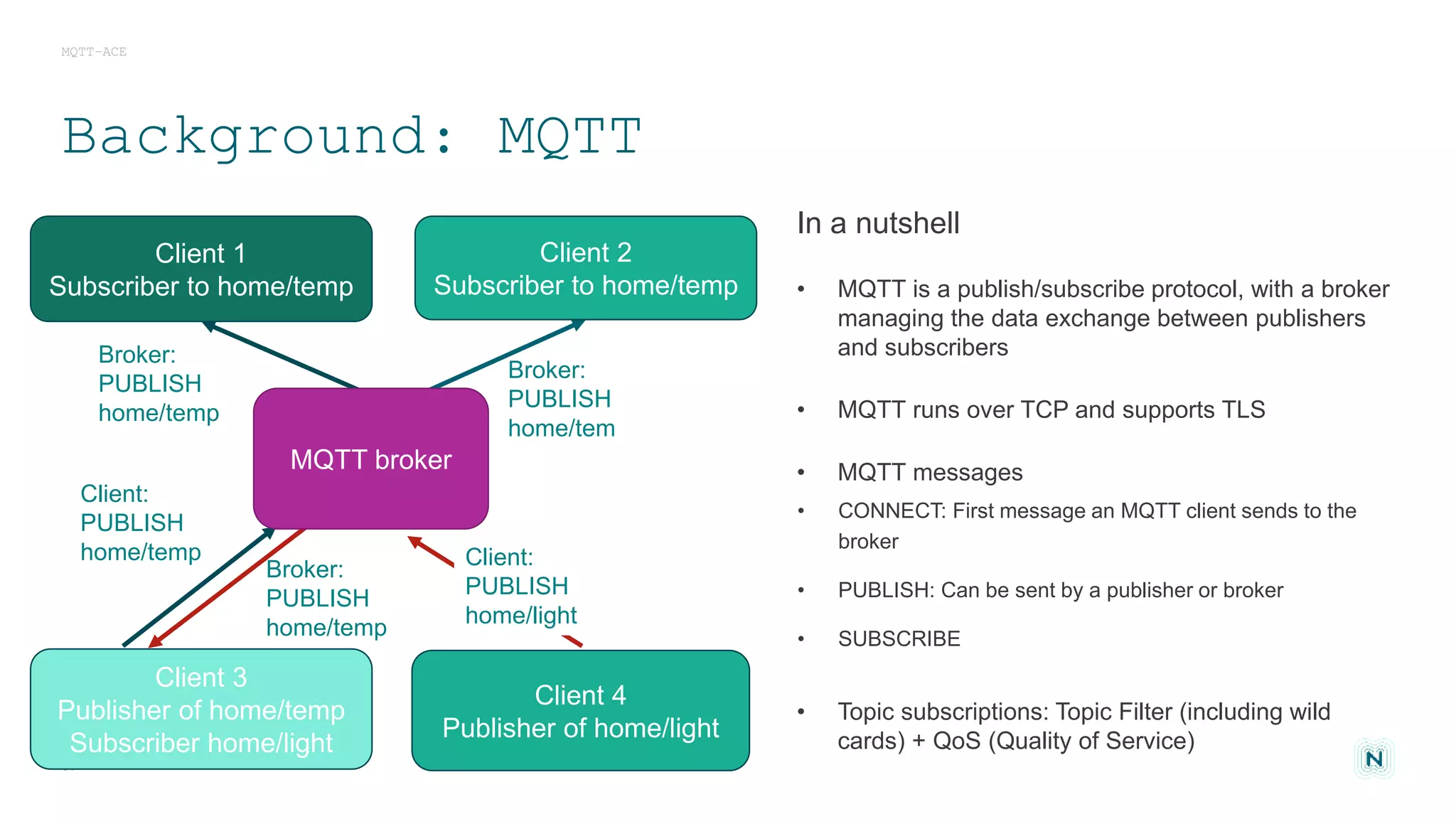
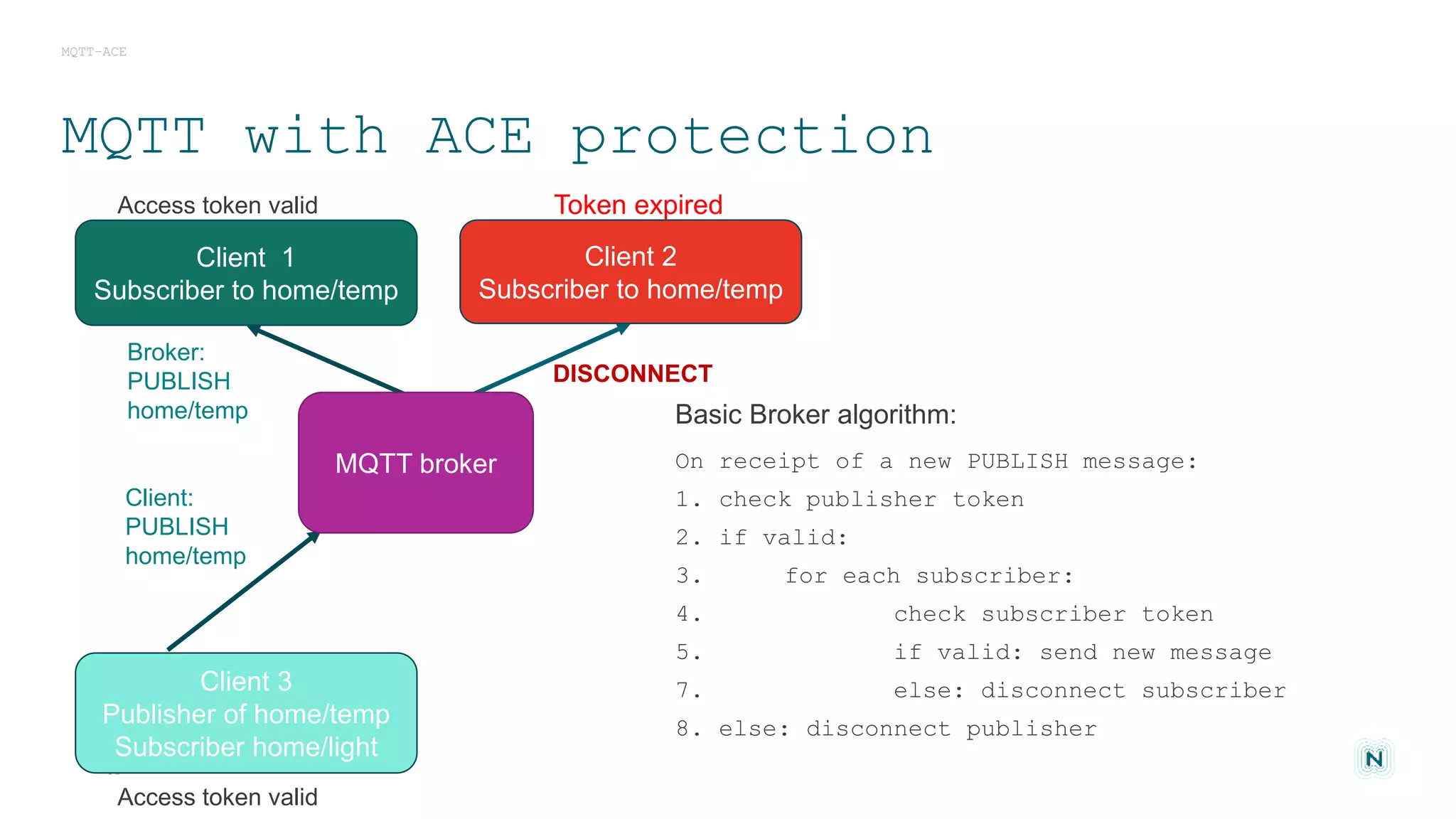
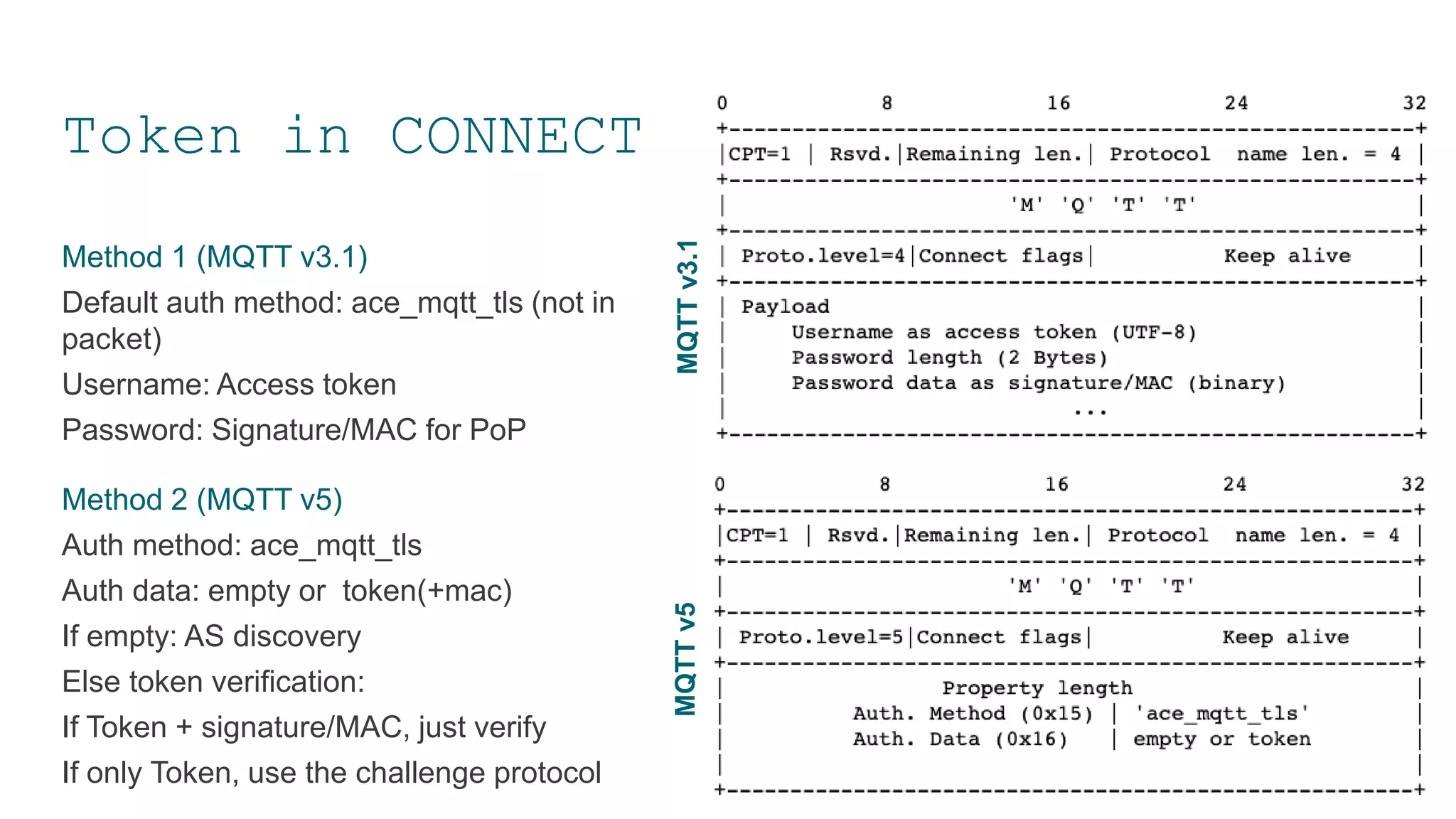
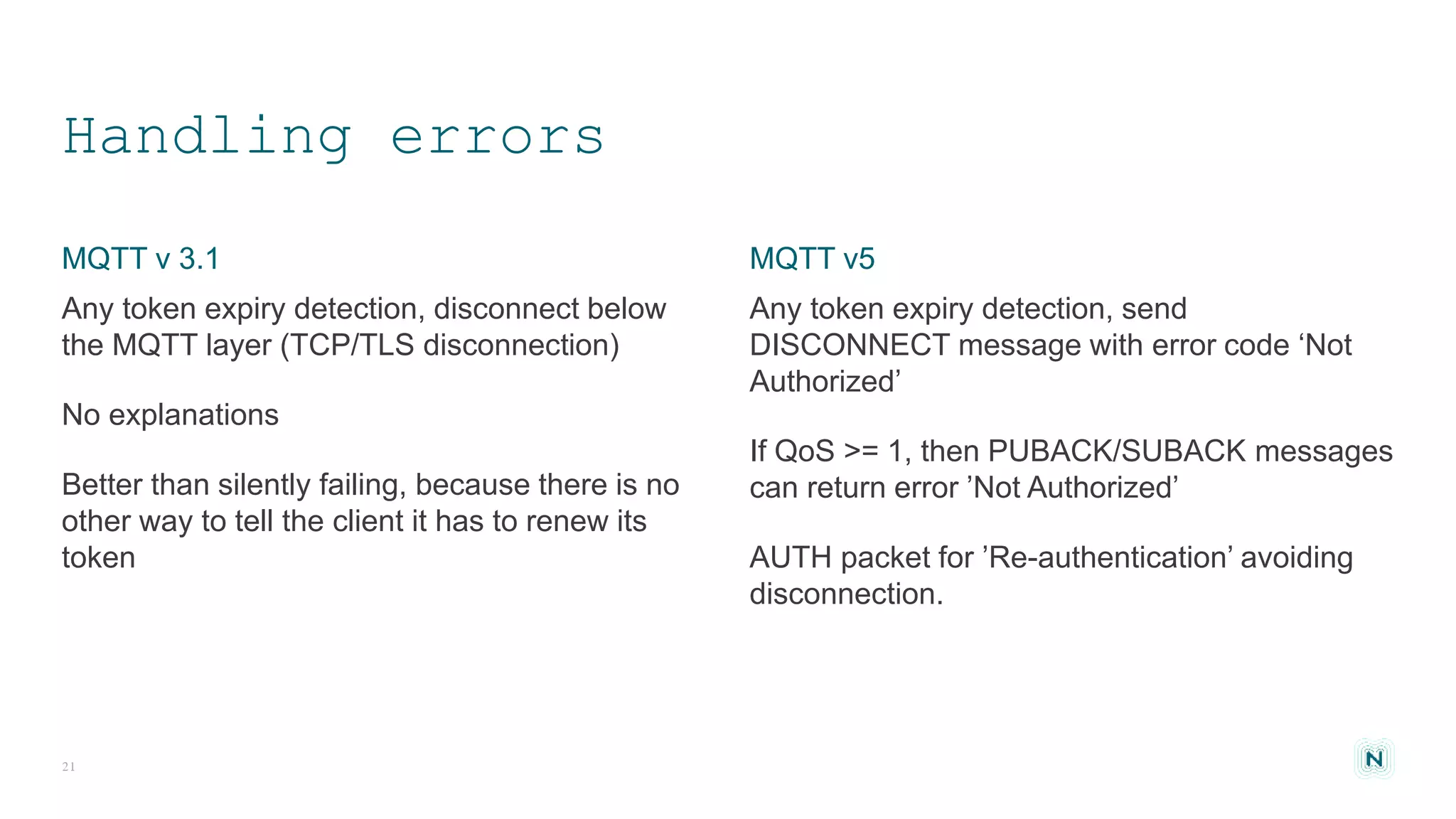
The document discusses access control challenges in the Internet of Things (IoT), emphasizing the need for improved security and privacy. It covers various authorization frameworks such as OAuth2, UMA, and ACE, detailing how they apply to device-to-device communications and specifically in constrained environments. Additionally, it addresses the MQTT protocol's role in ensuring secure data exchange and the importance of token management for maintaining privacy.