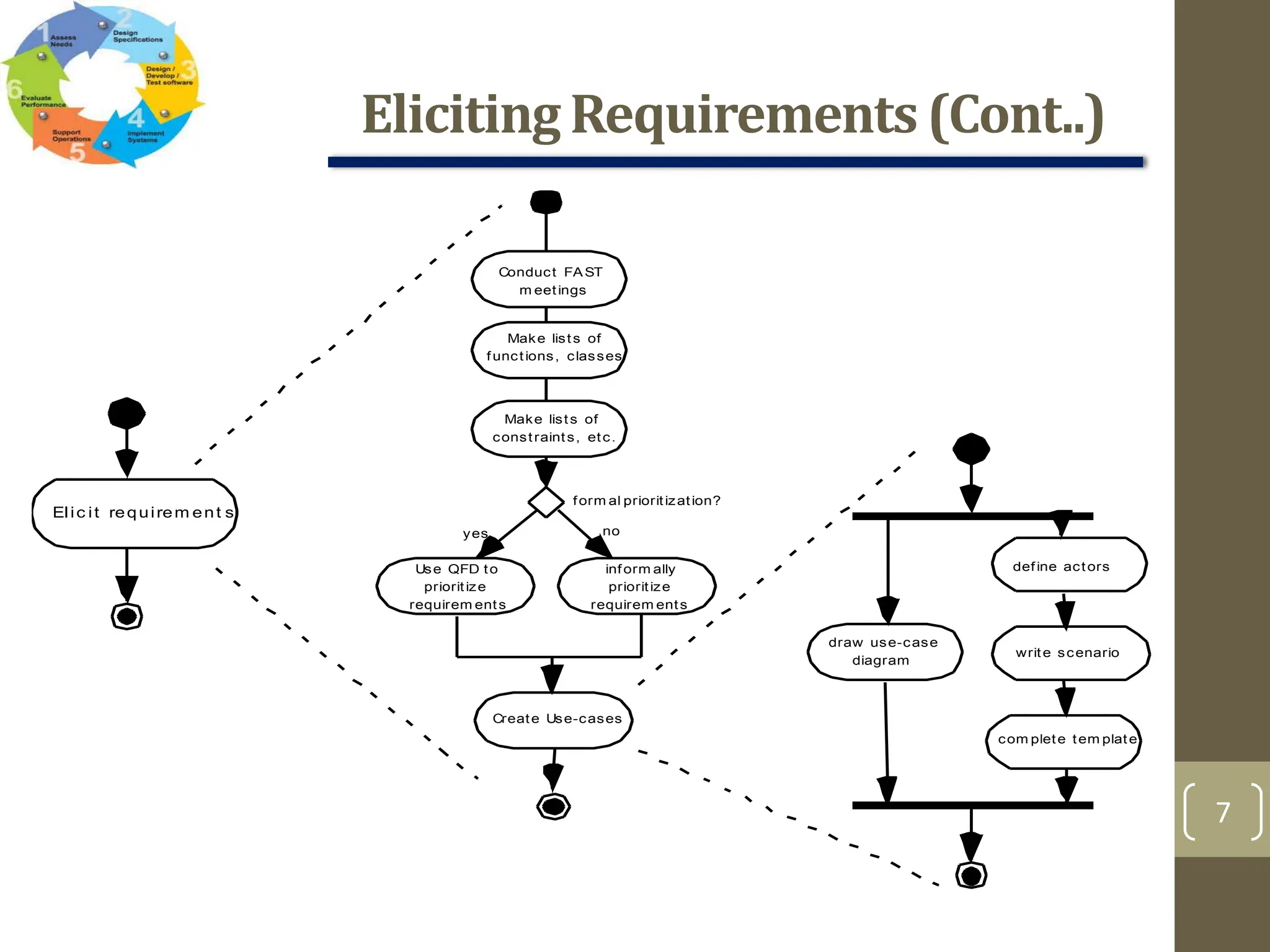
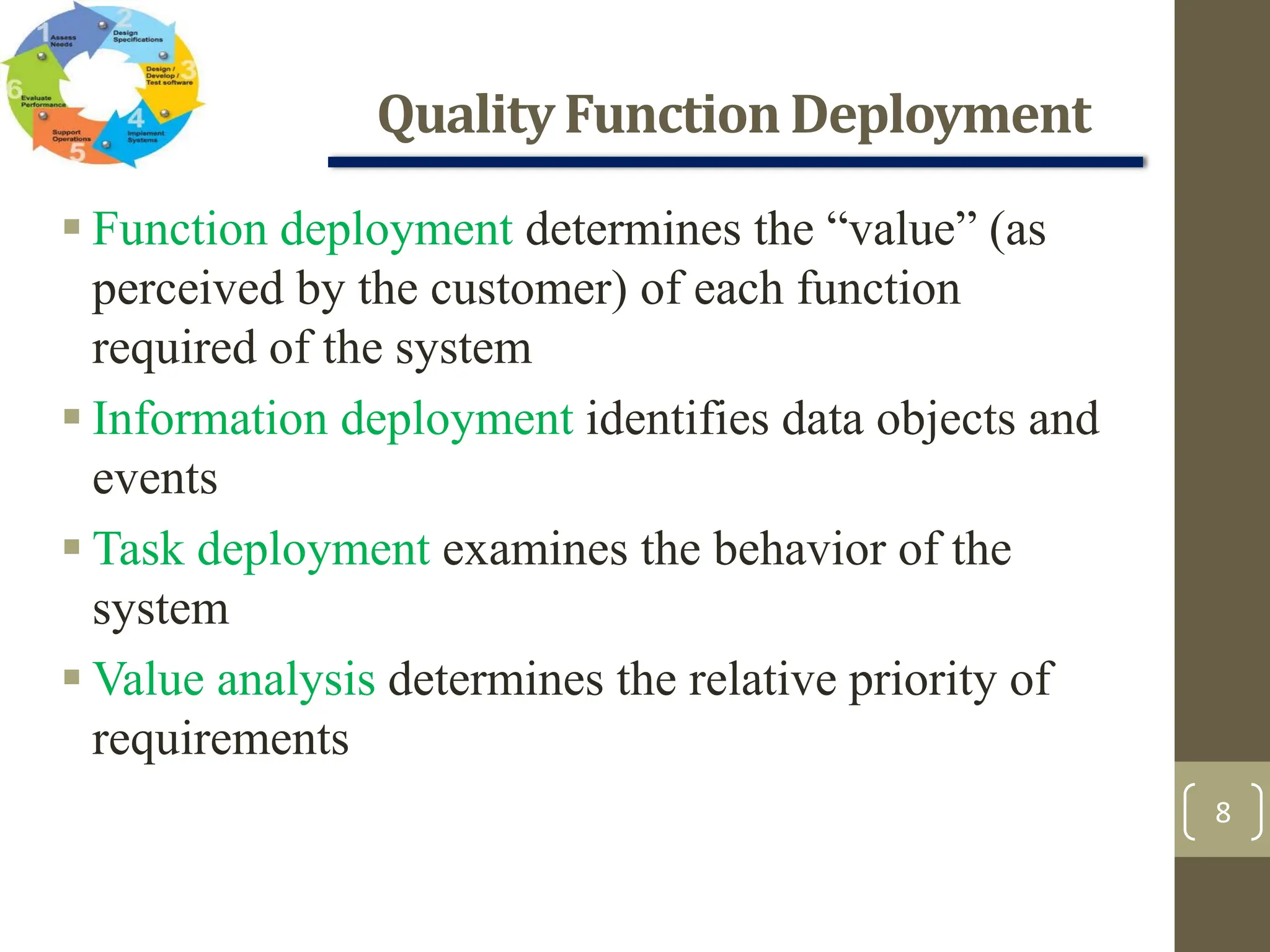
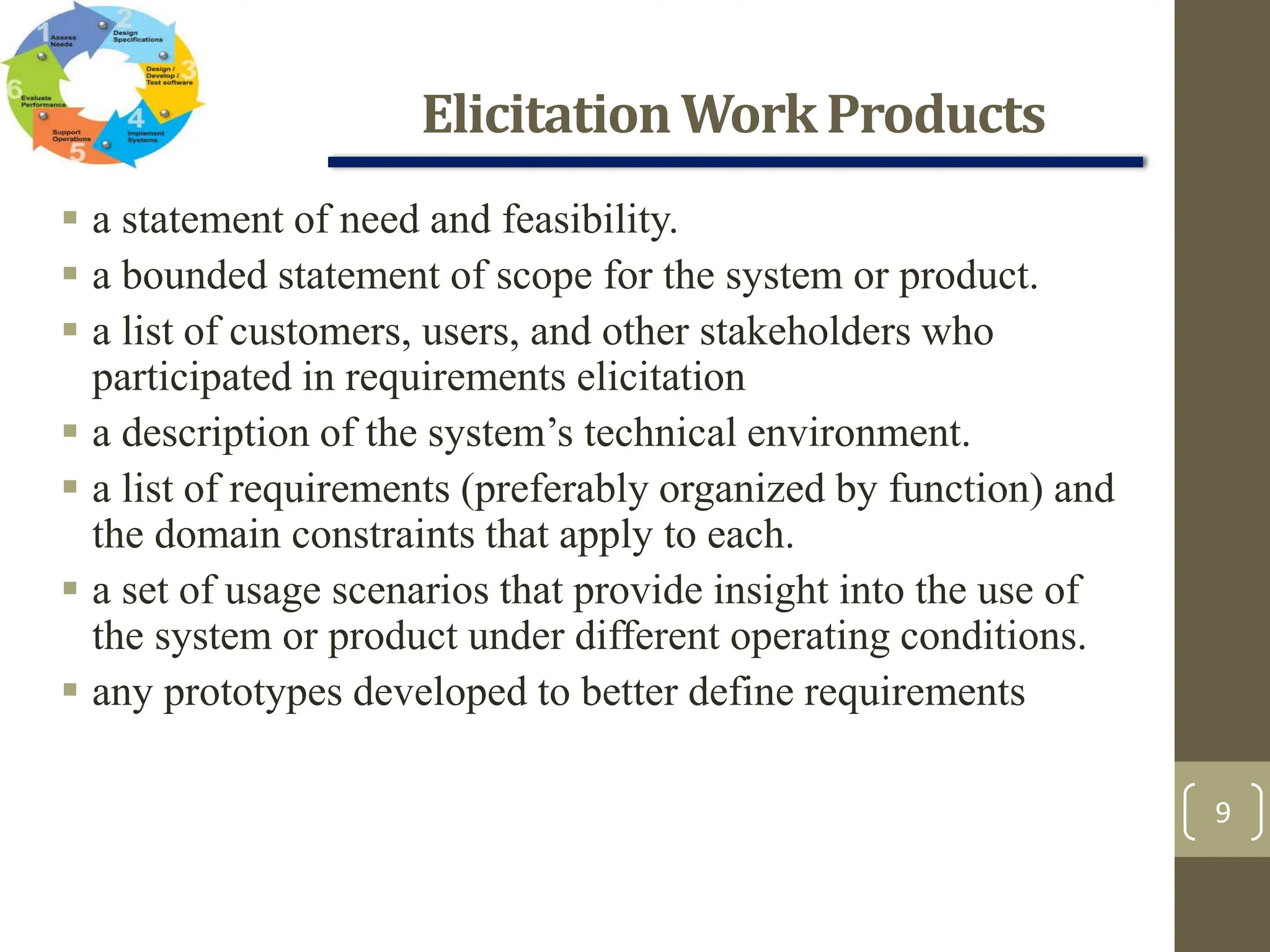
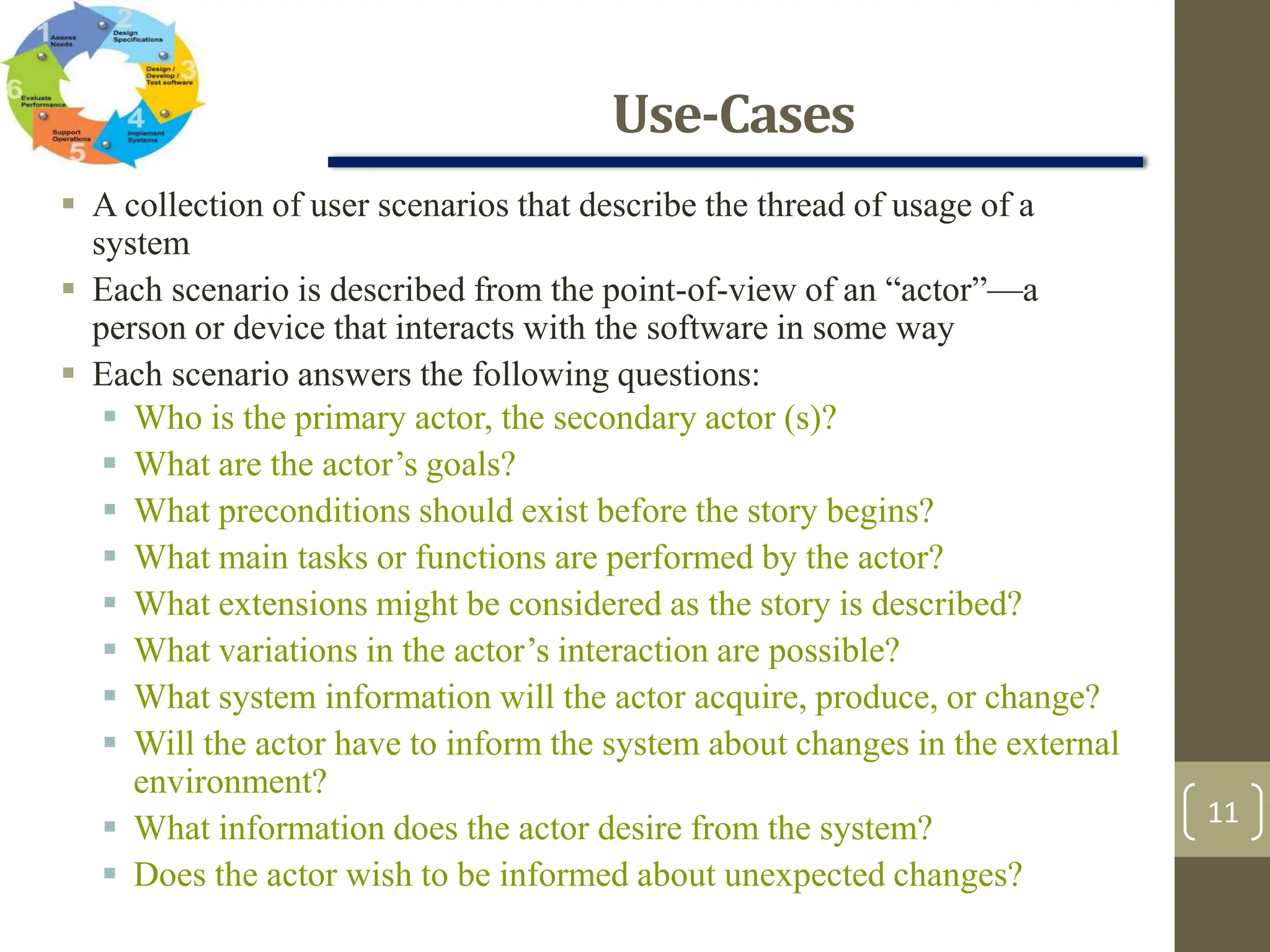
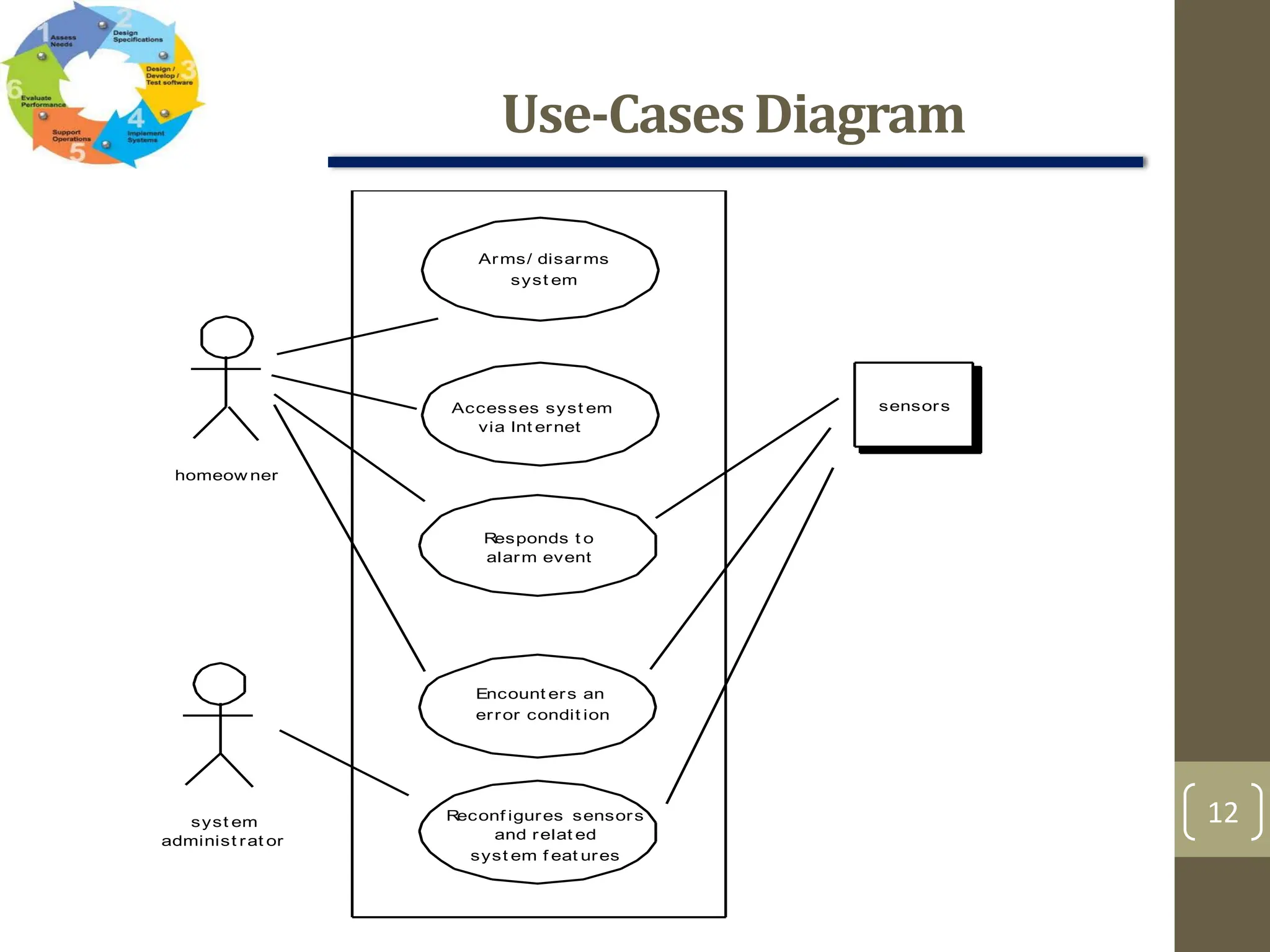
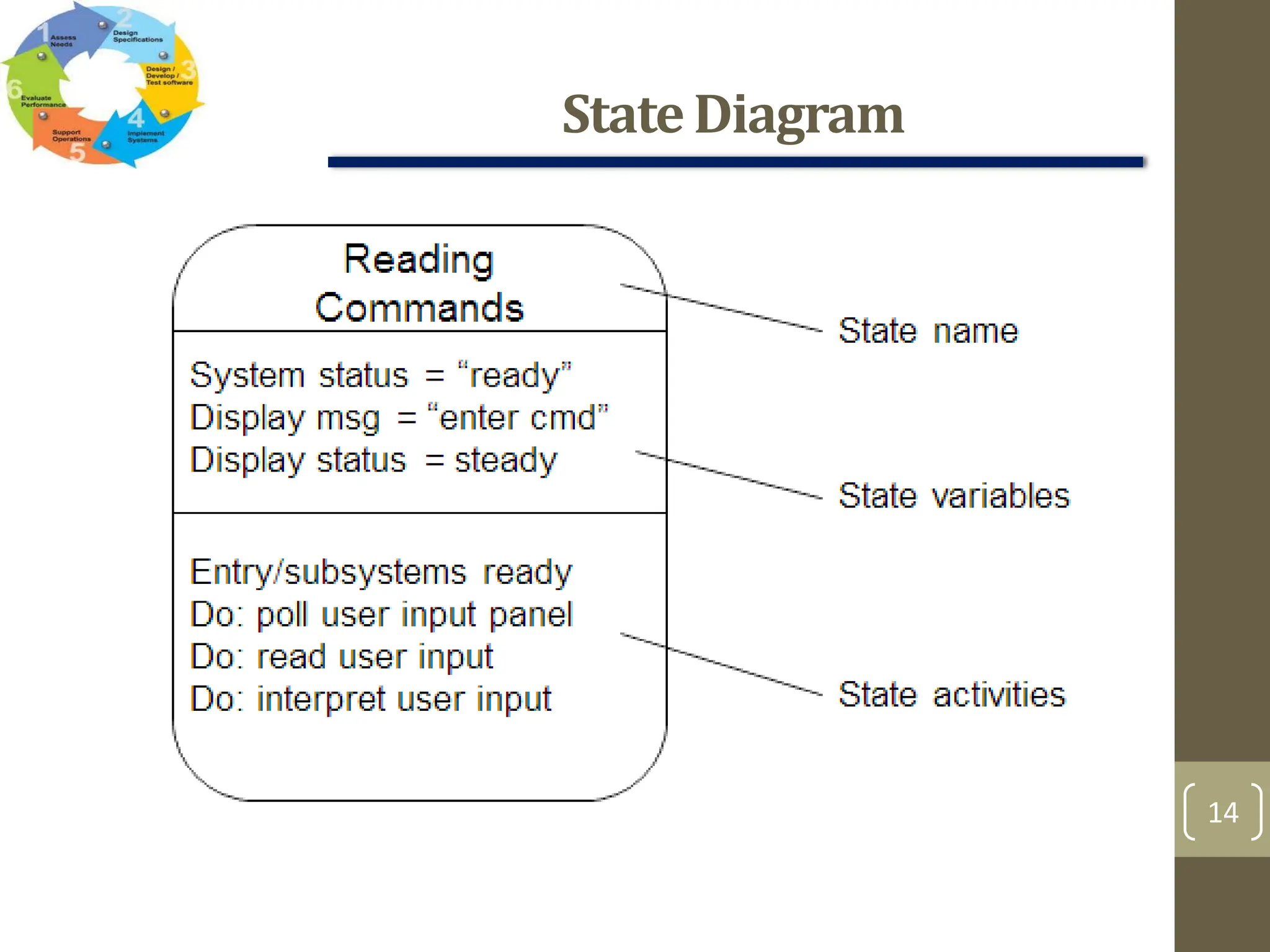
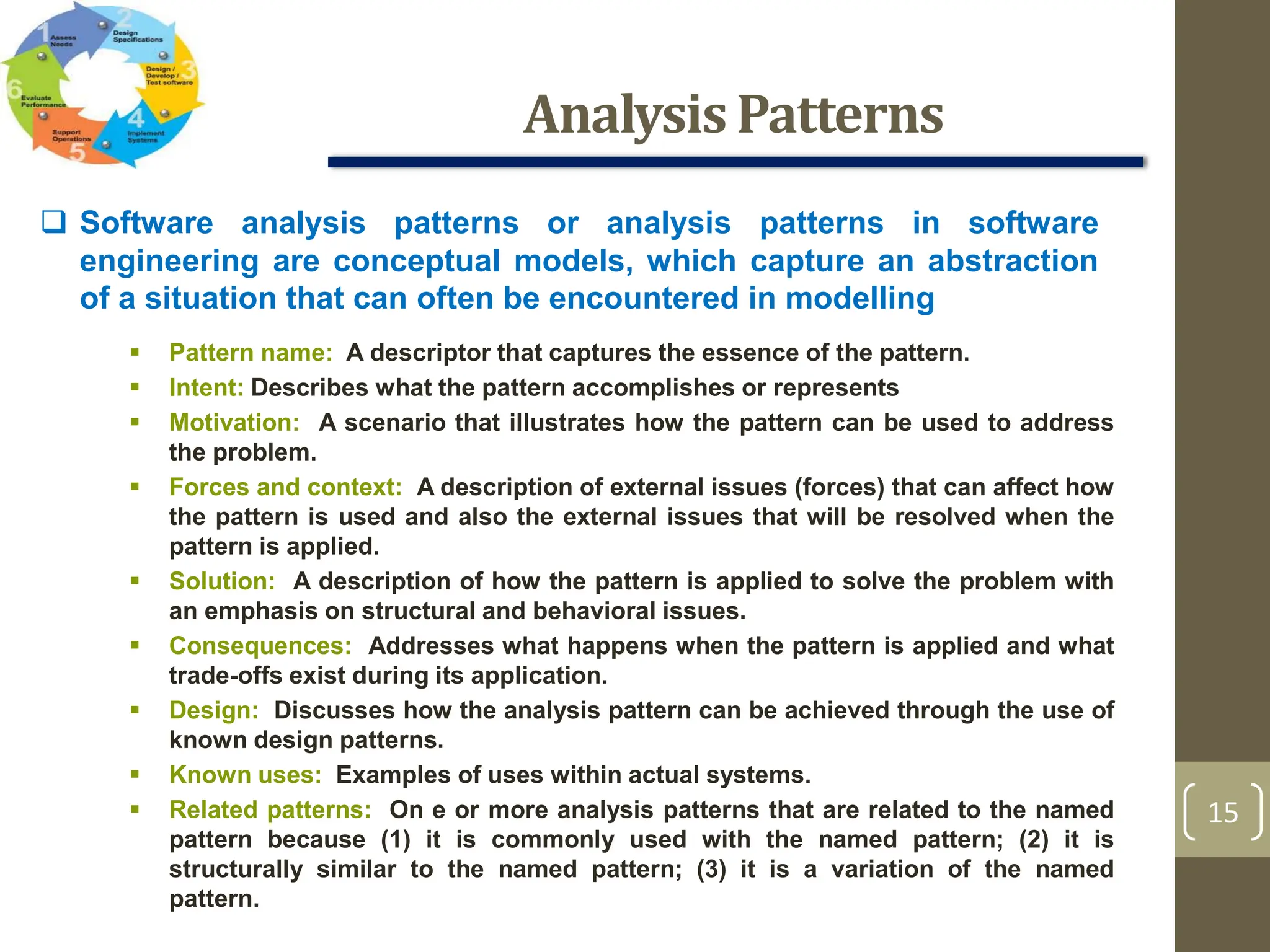
The document outlines the concept of requirements engineering, detailing the systematic techniques for gathering and managing system requirements through seven tasks: inception, elicitation, elaboration, negotiation, specification, validation, and management. It emphasizes collaboration among stakeholders, the creation of analysis models, and prioritization of requirements, with various methods for validation and negotiation to ensure the completeness and relevance of requirements. Additionally, it discusses the use of use-cases and analysis patterns to model requirements effectively.

![RequirementsEngineering
Requirements are statements of what the system must do,
how it must behave, the properties it must exhibit, the
qualities it must possess, and the constraints that the system
and its development must satisfy.
Requirements engineering emphasizes the use of systematic
and repeatable techniques that ensure the completeness,
consistency, and relevance of the system requirements
[Sommerville 1997a].
It encompasses seven distinct tasks: inception, elicitation,
elaboration, negotiation, specification, validation and
management.
2](https://image.slidesharecdn.com/6-180117160306-240717130737-810473c8/75/6-180117160306-software-engineering-concepts-2-2048.jpg)