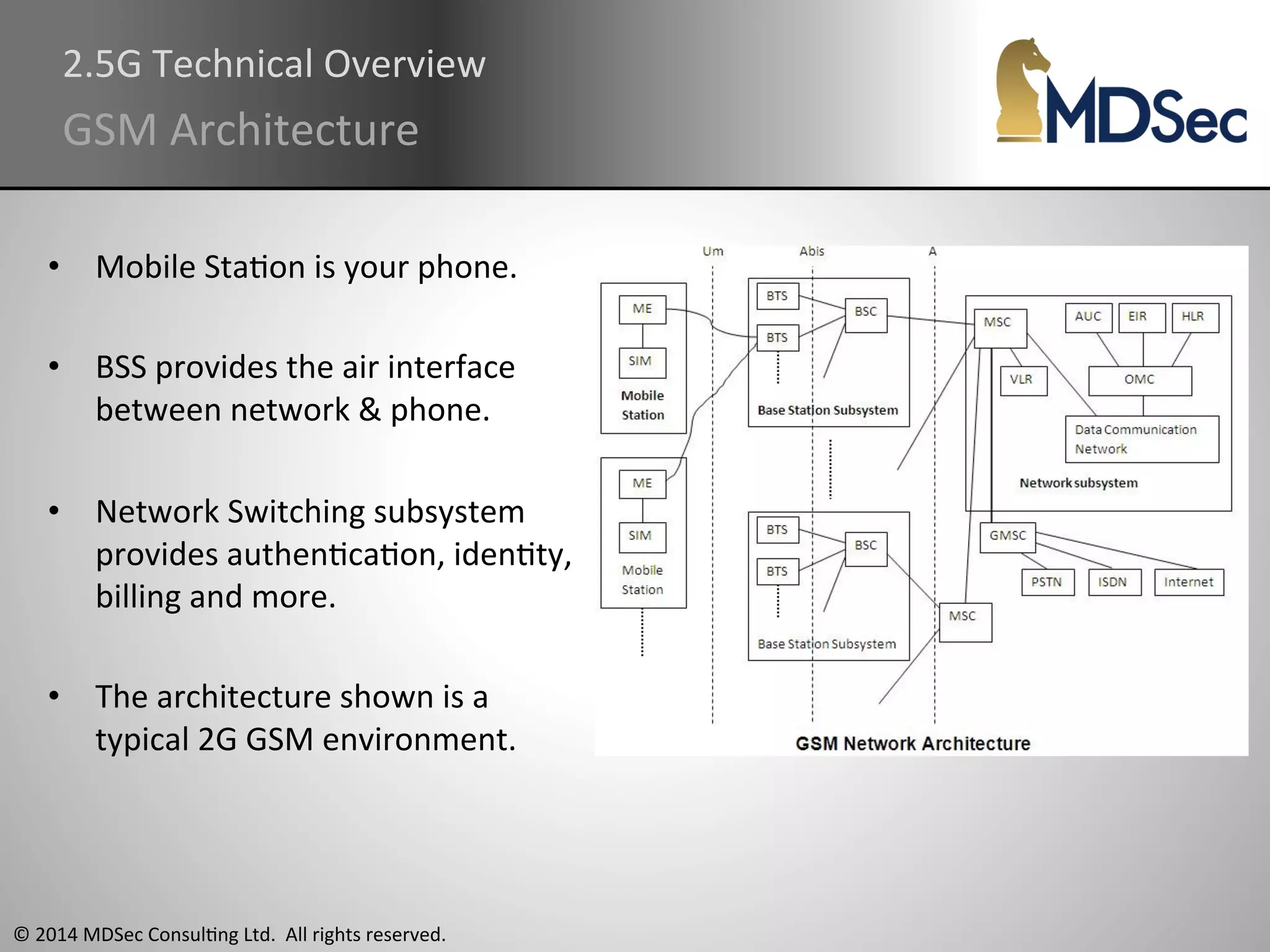
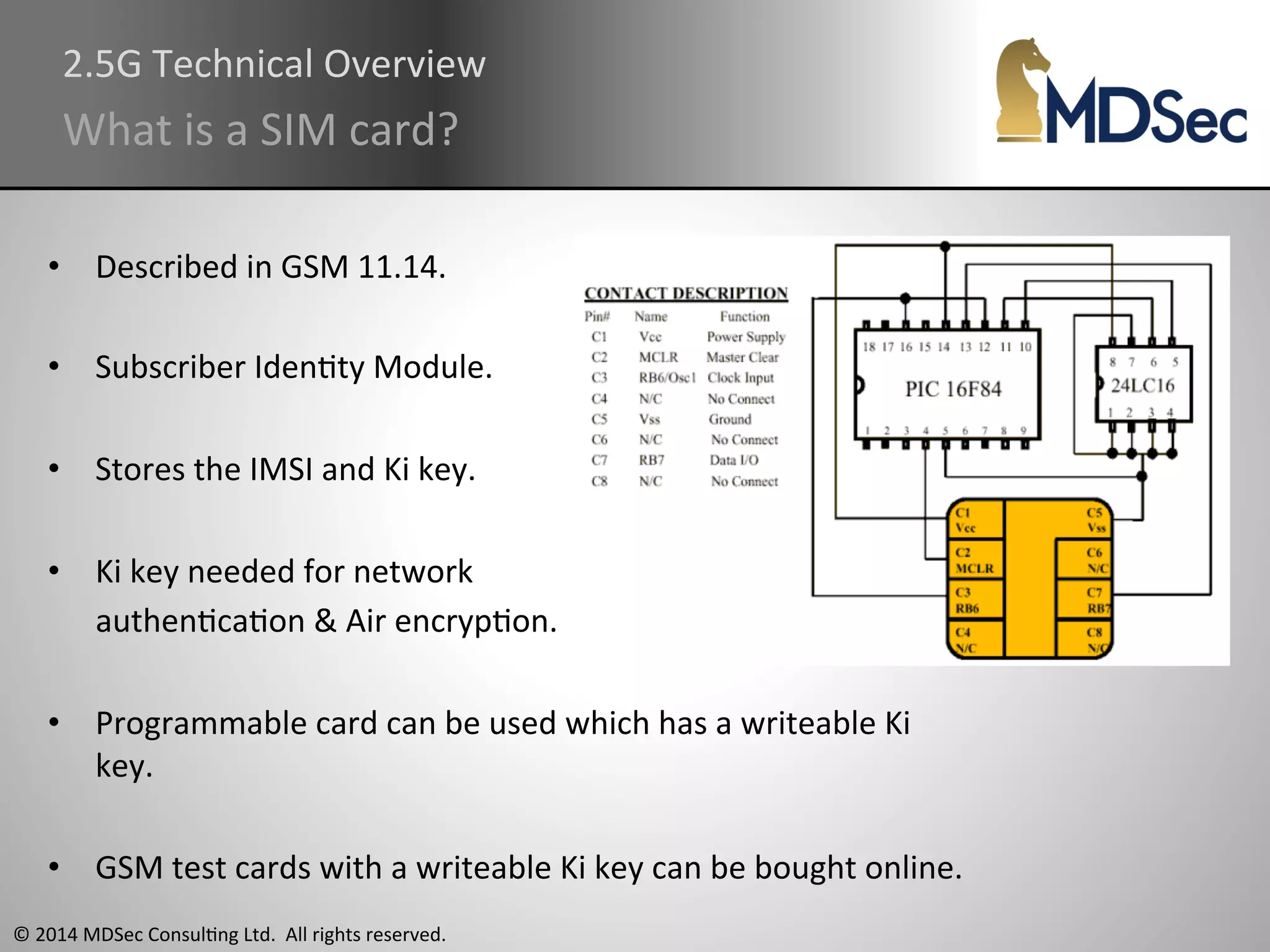
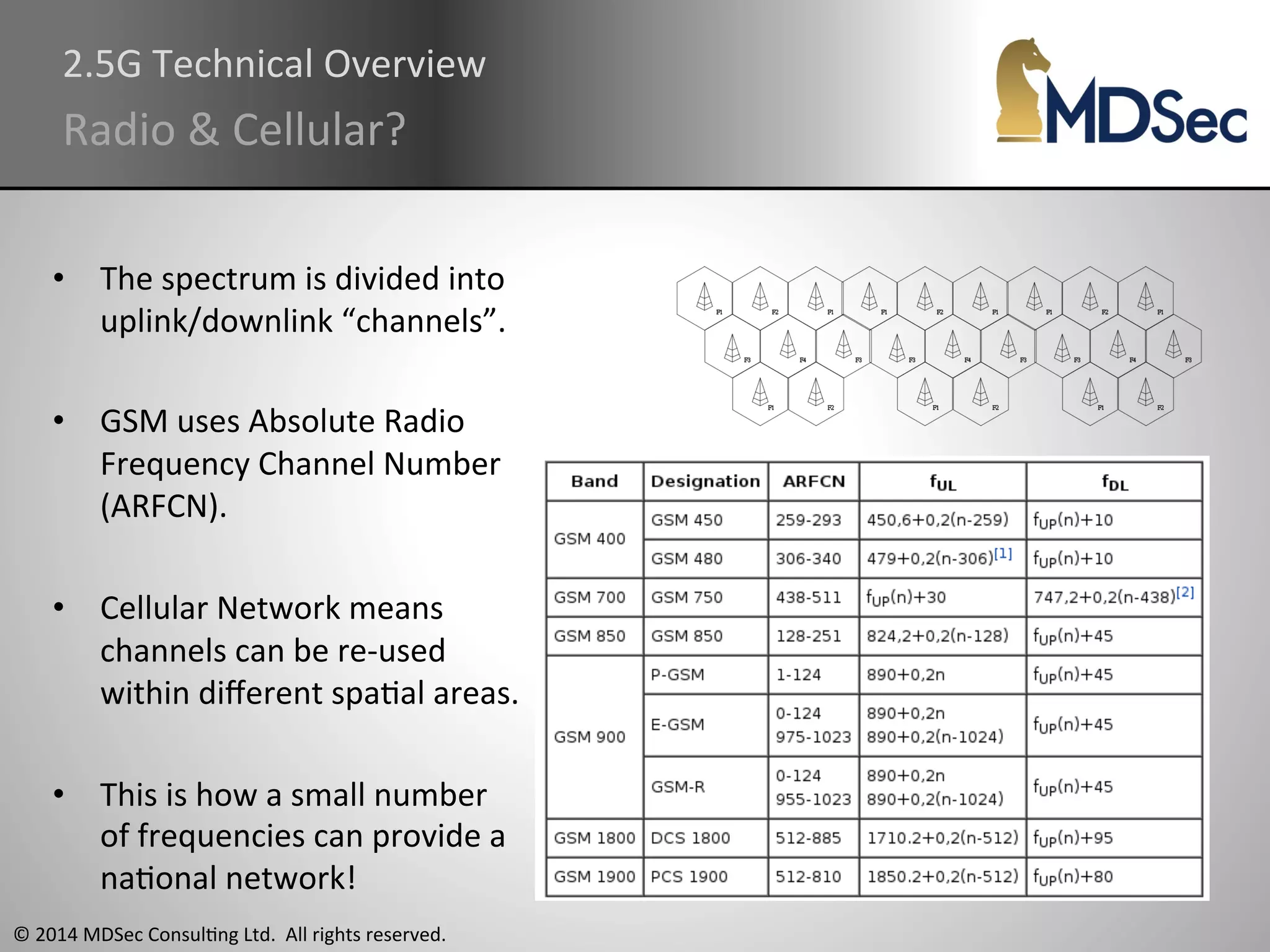
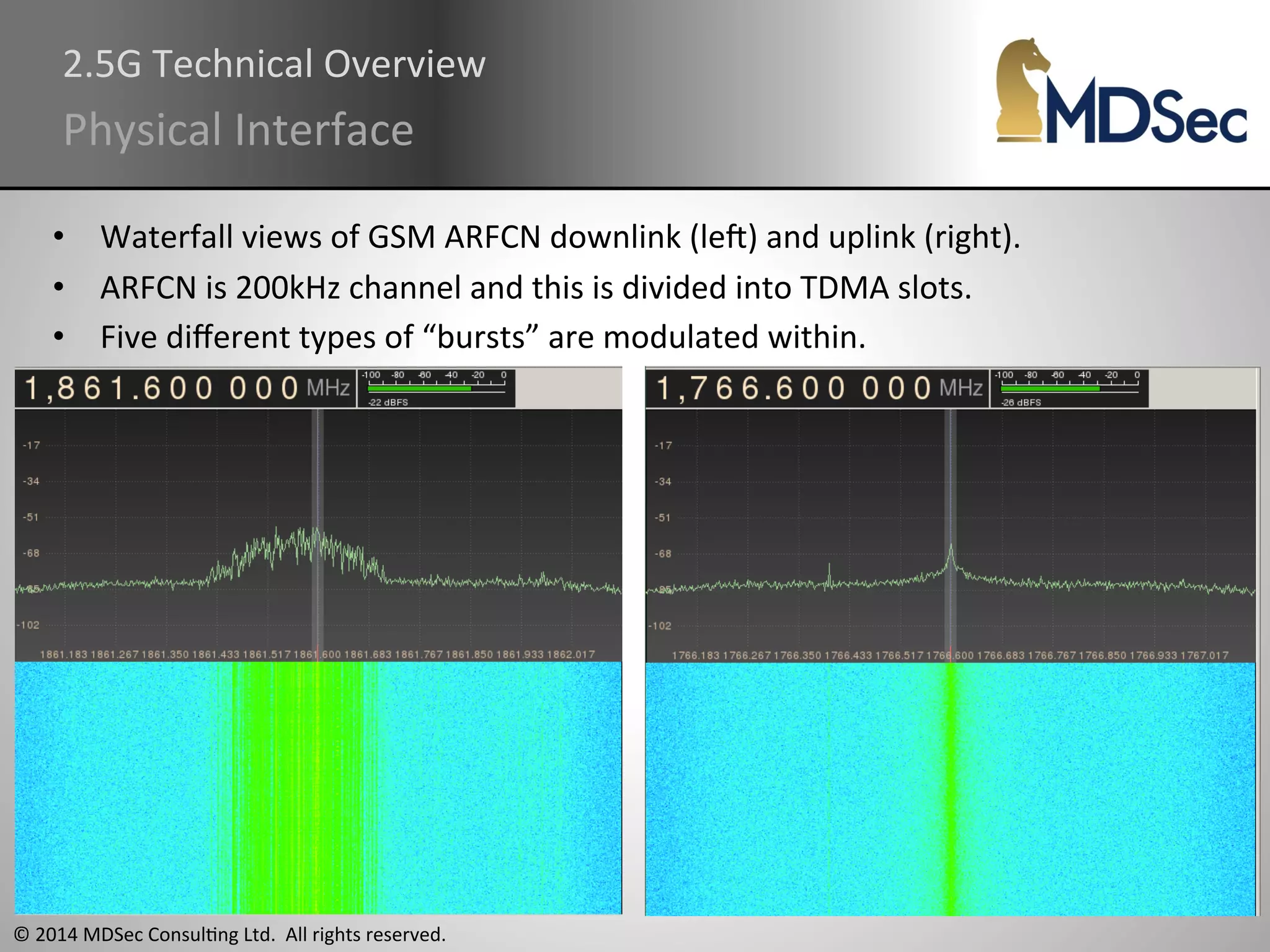
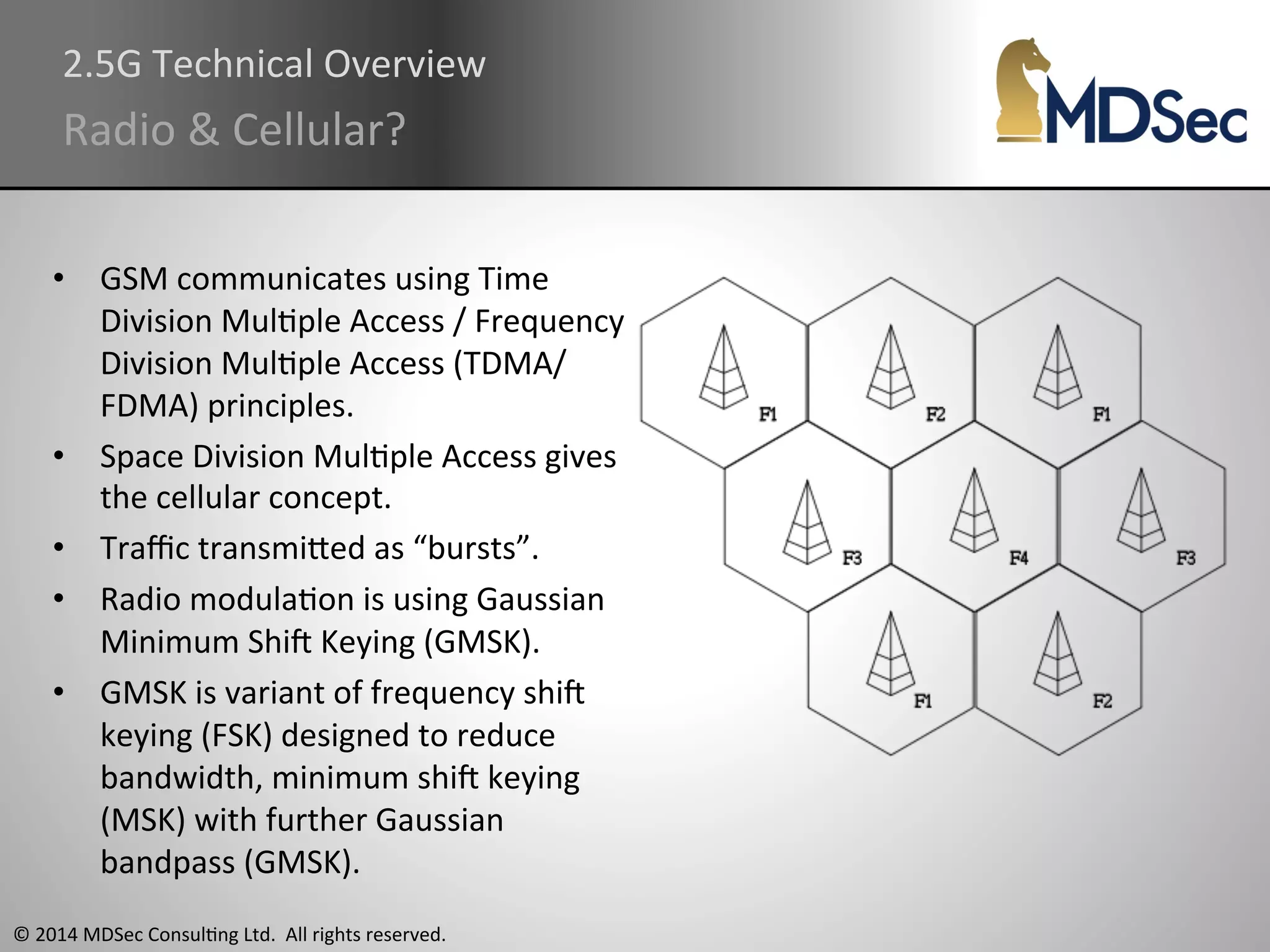
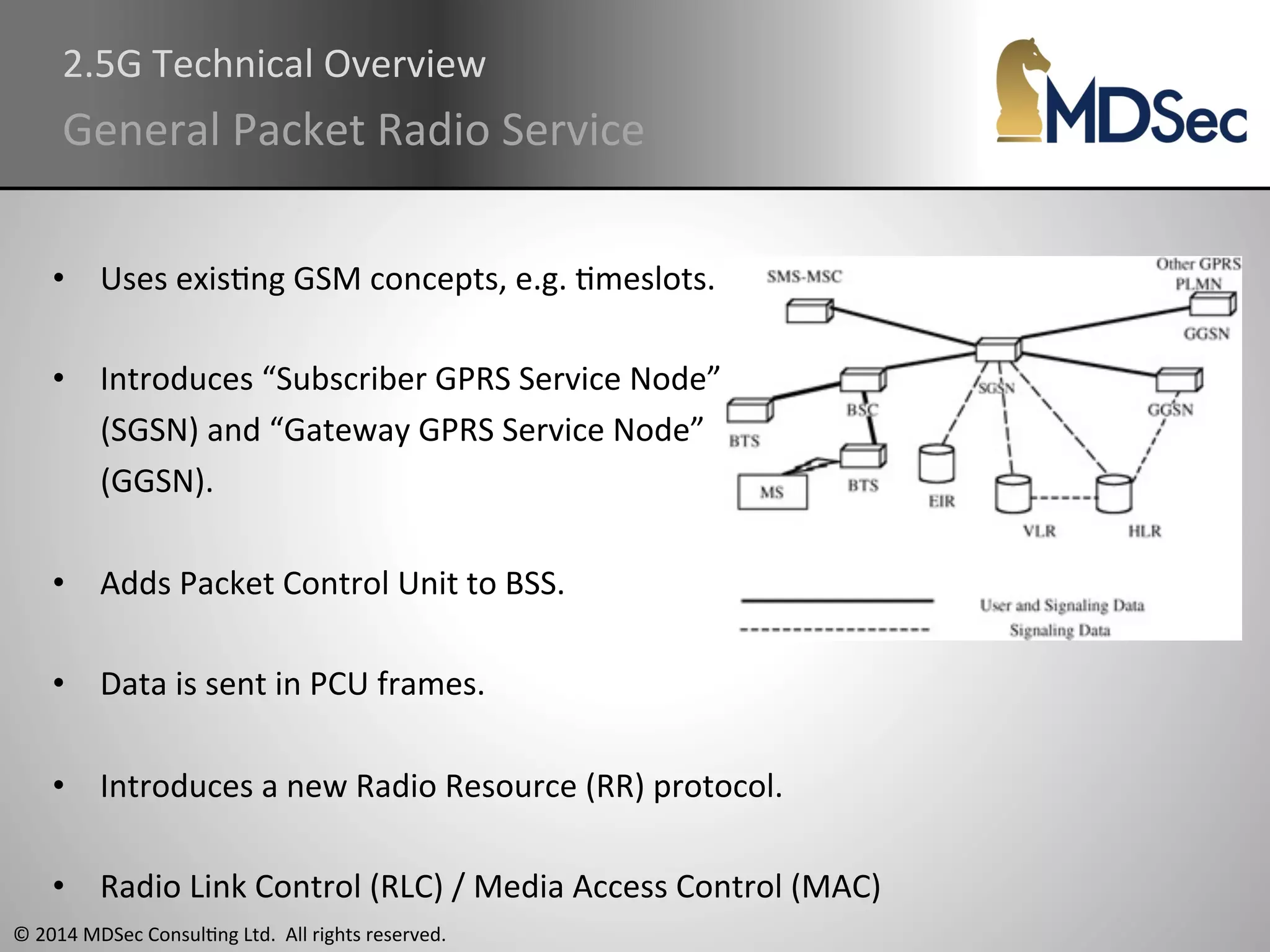
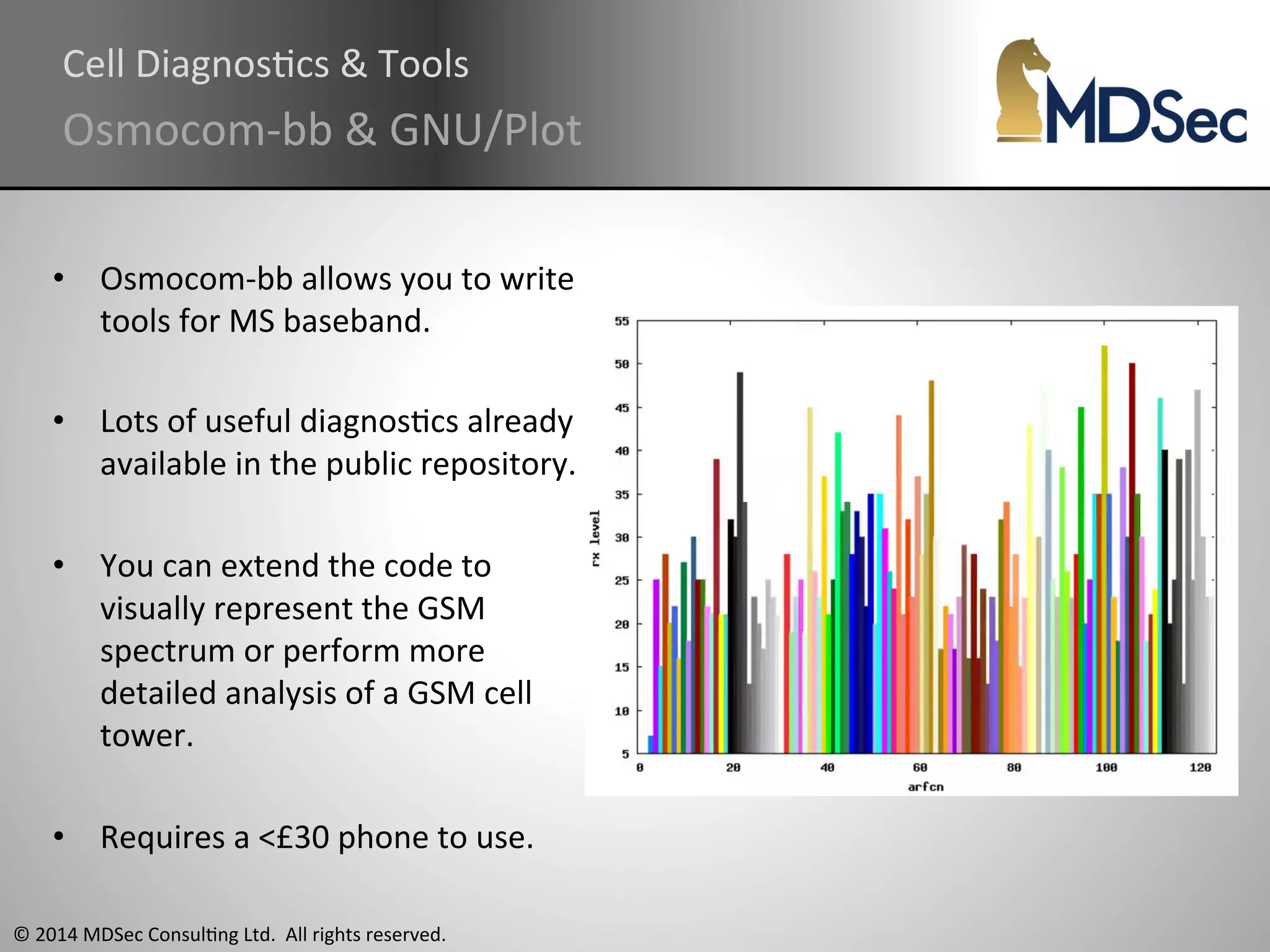
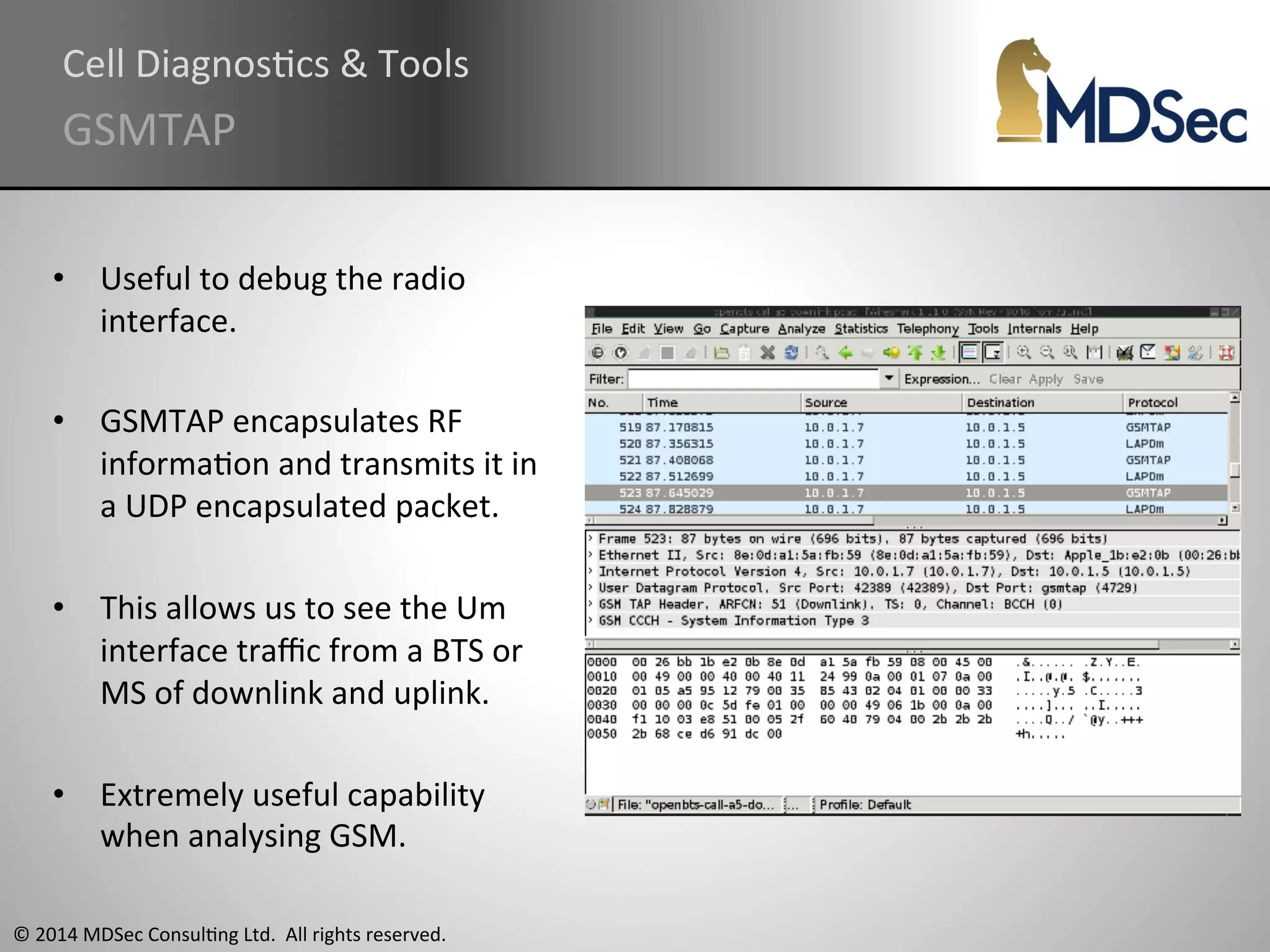
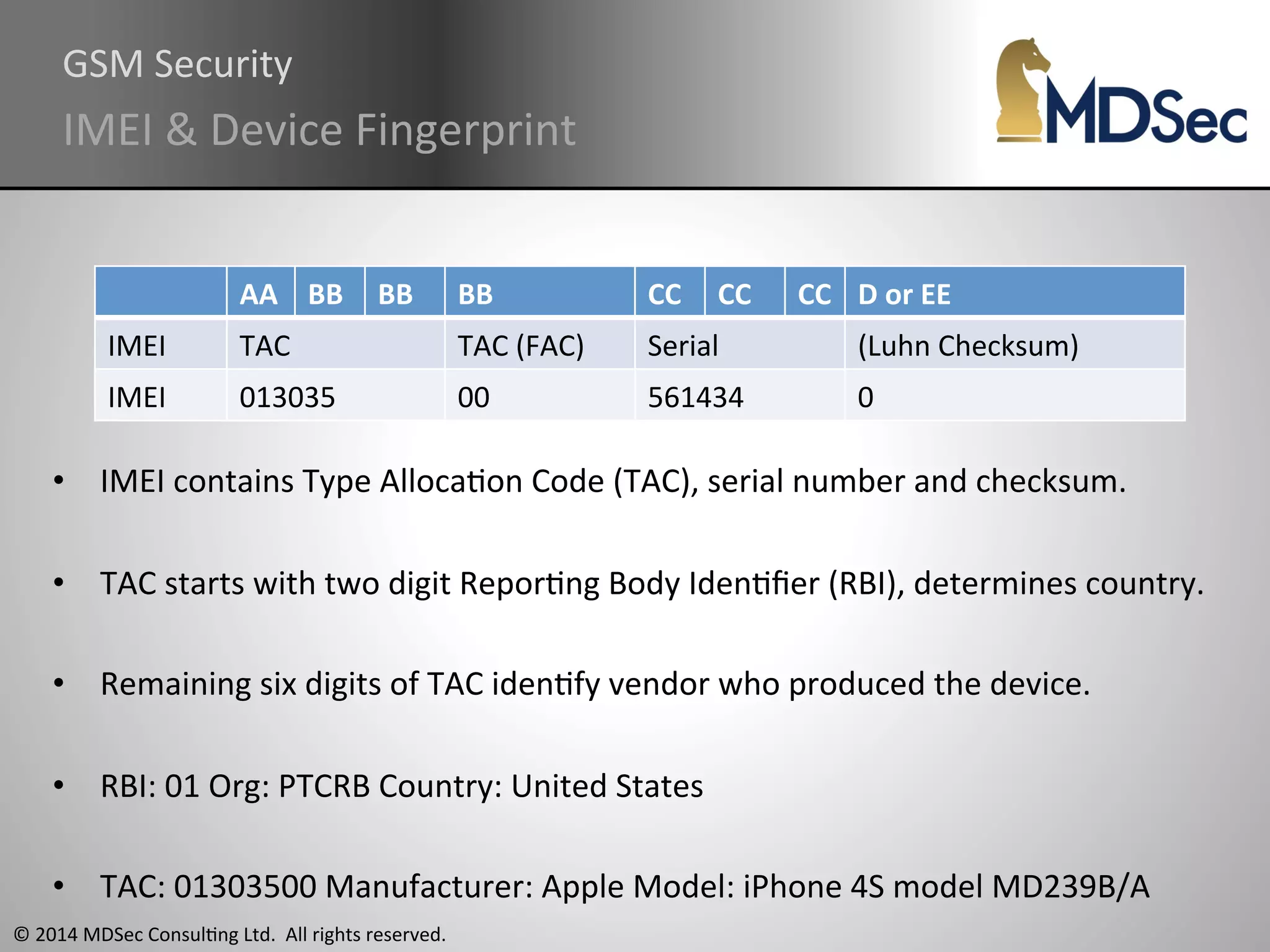
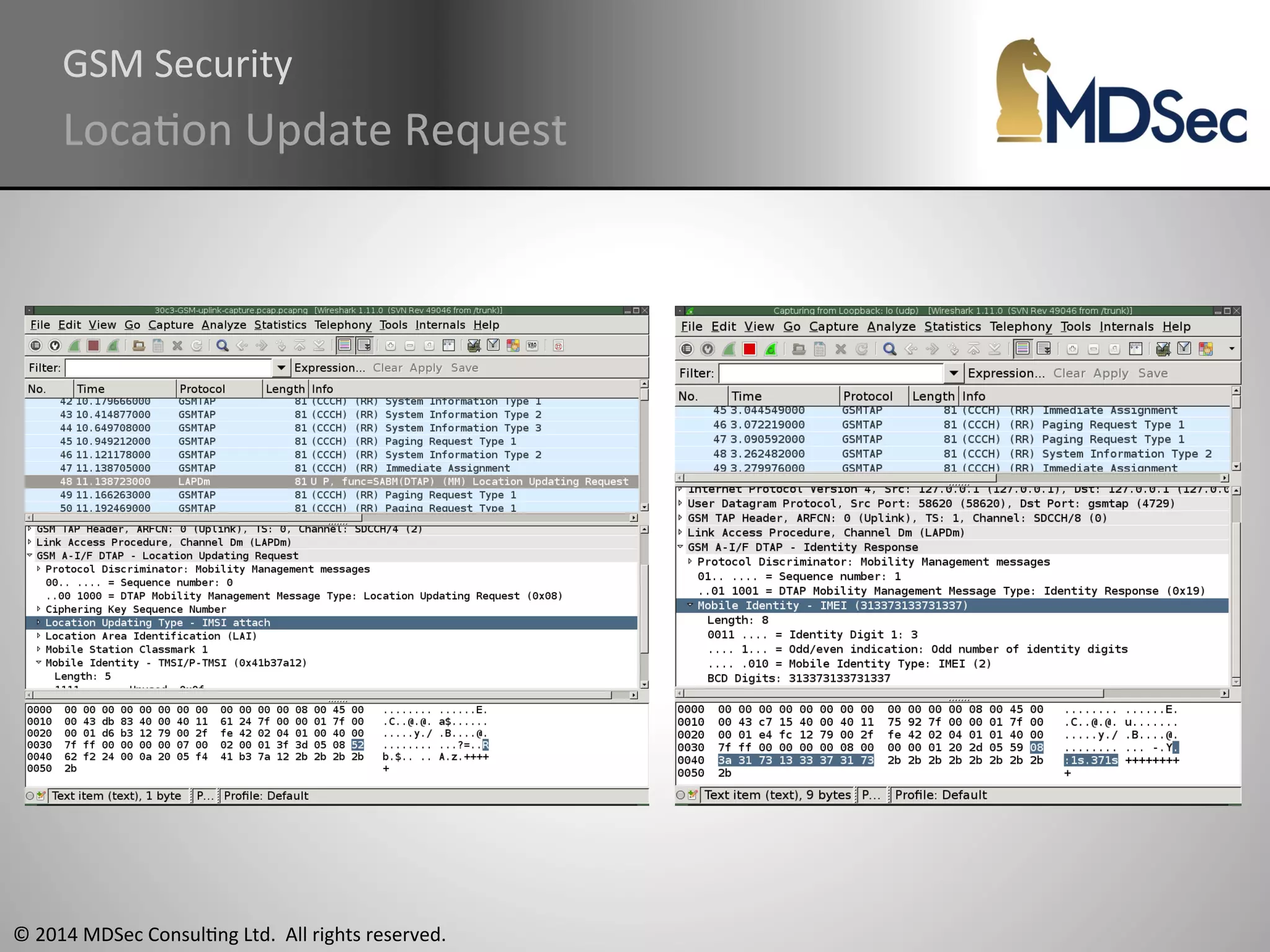
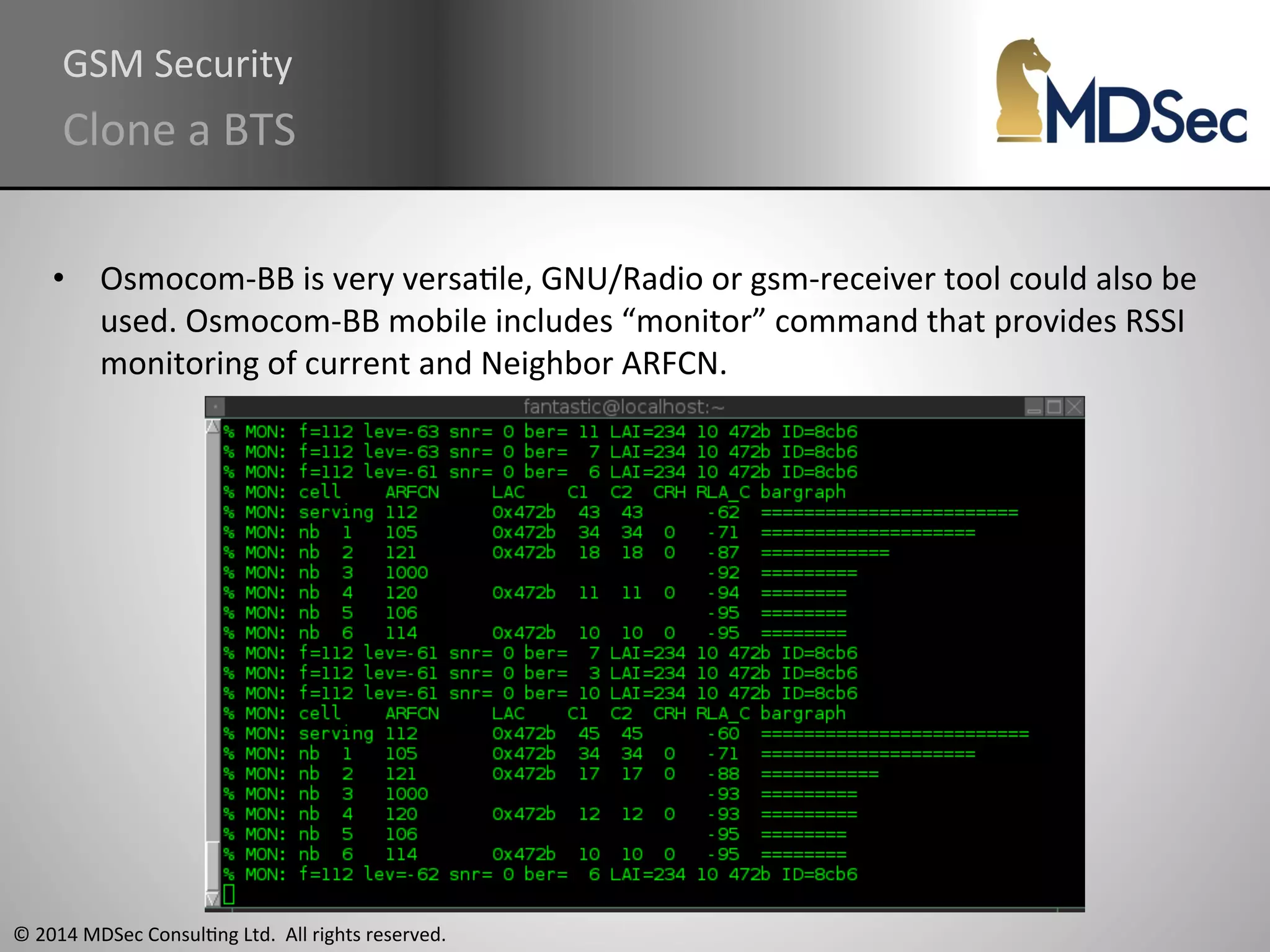
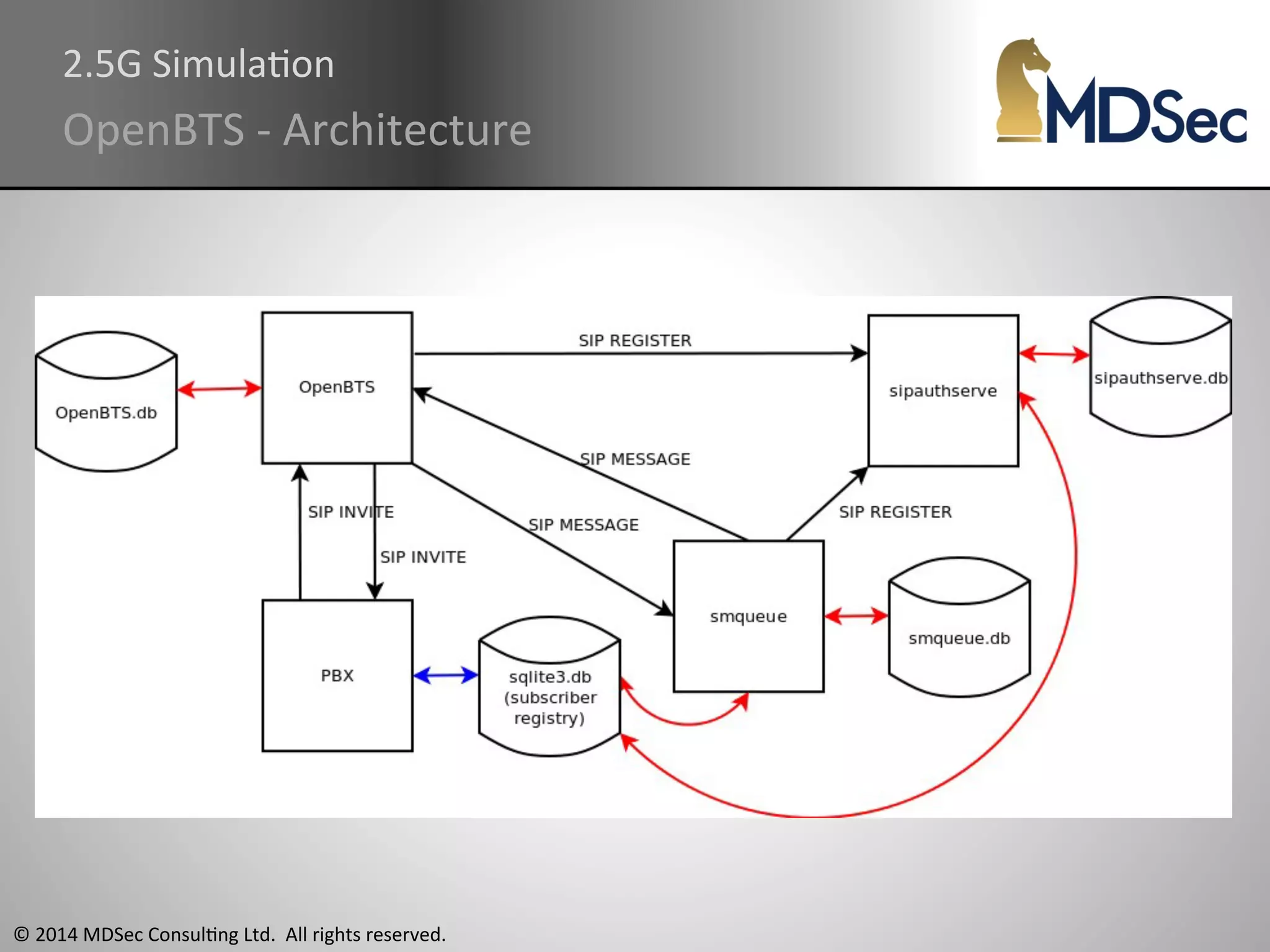
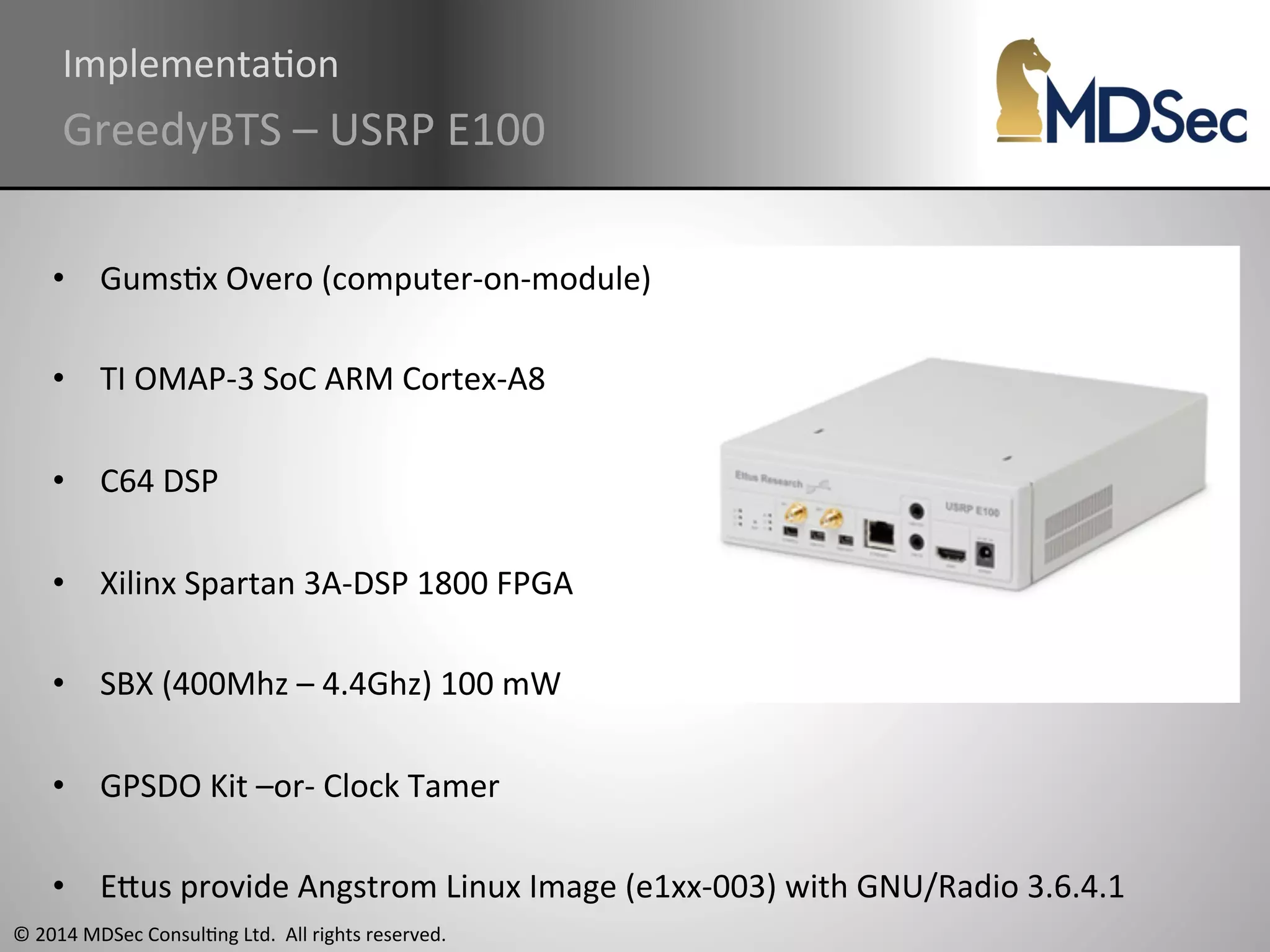
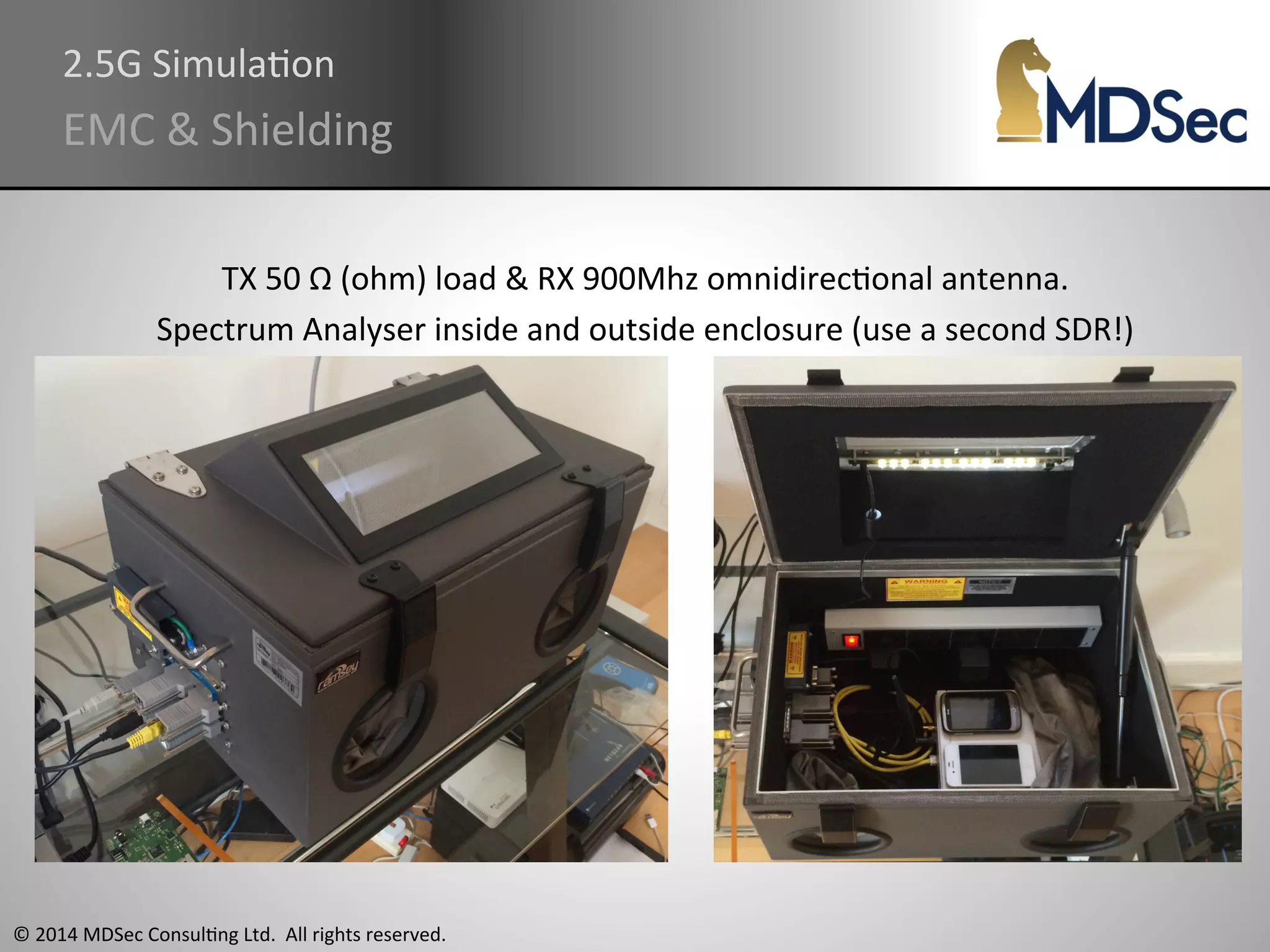
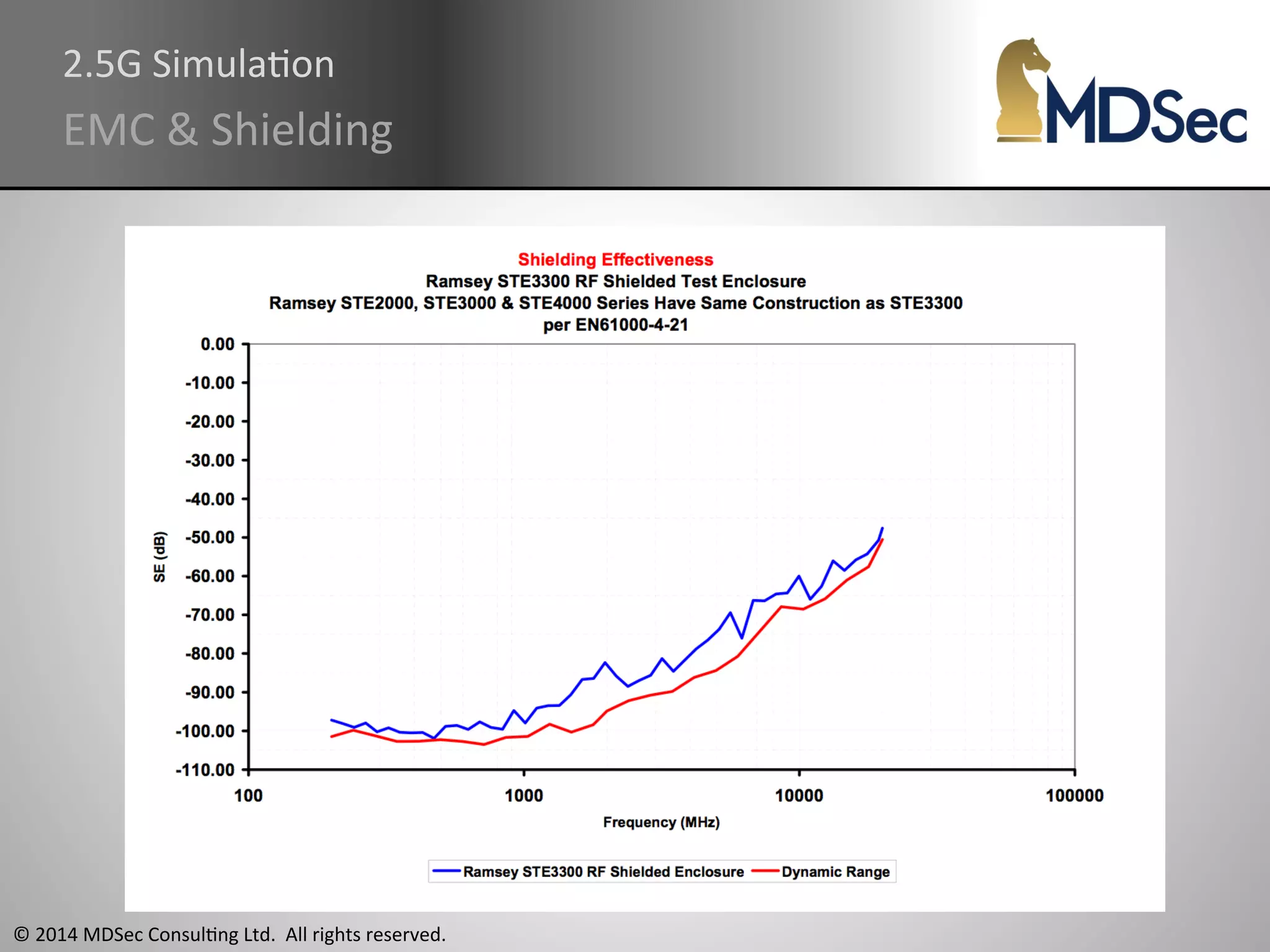
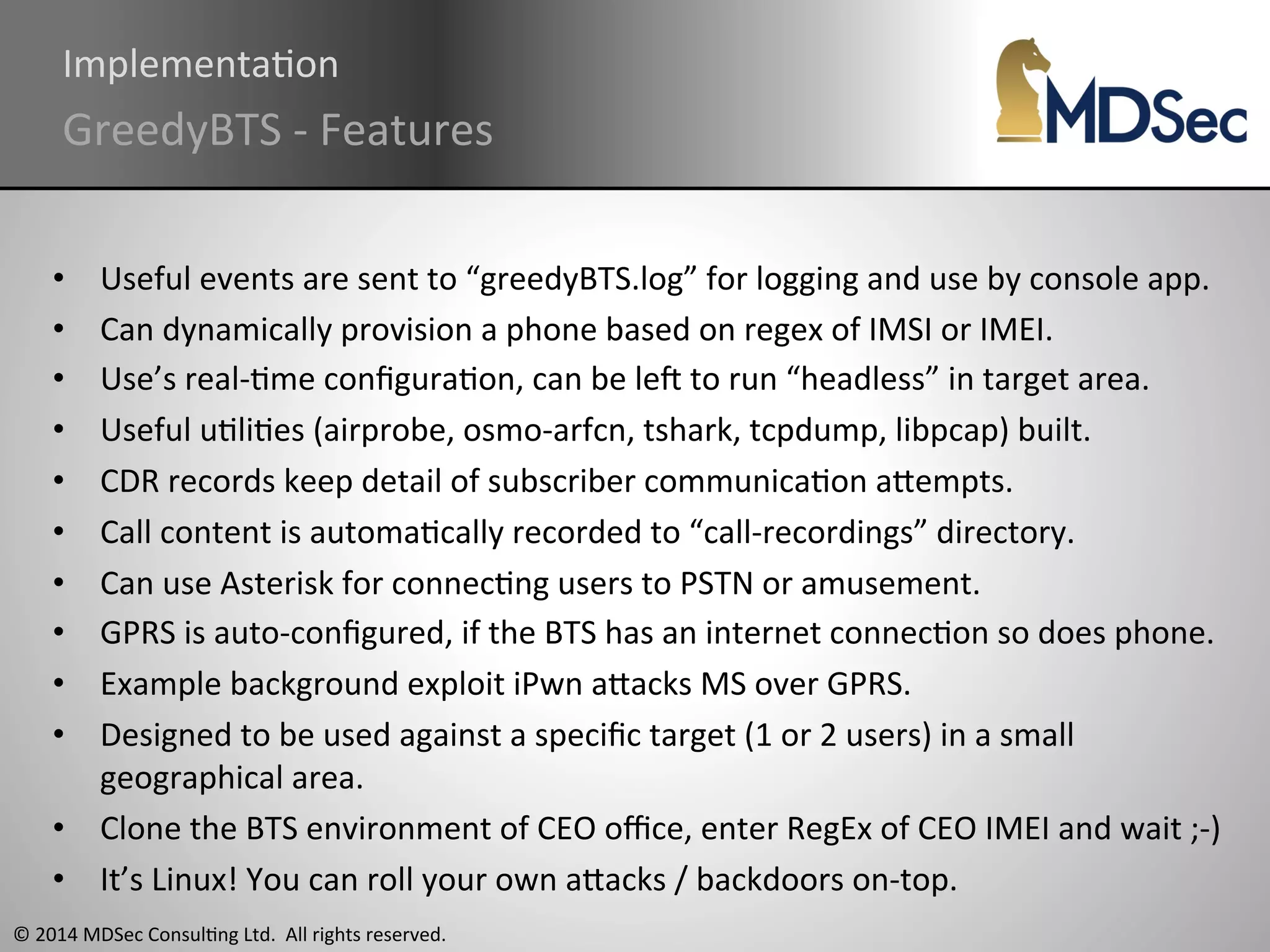
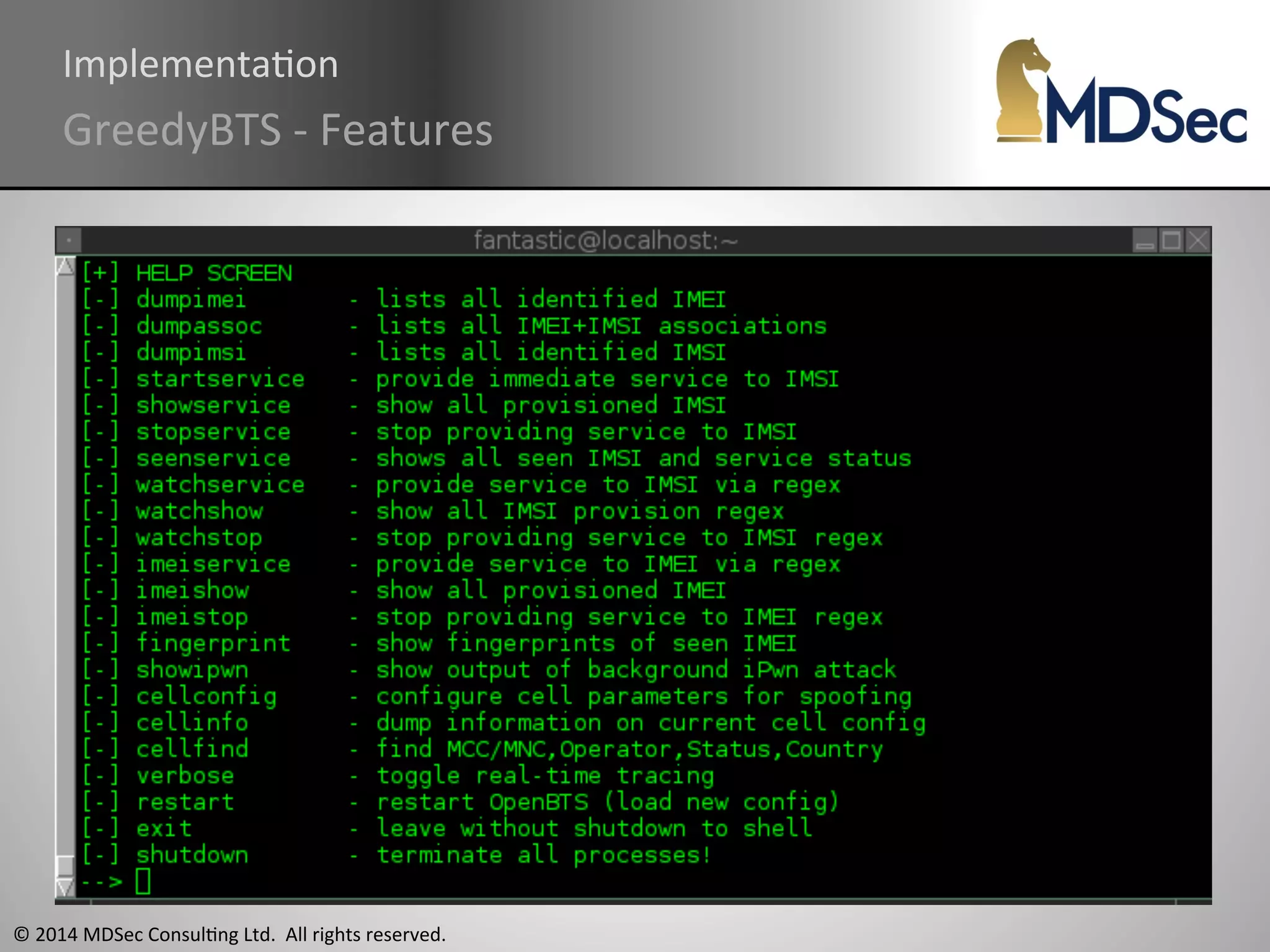
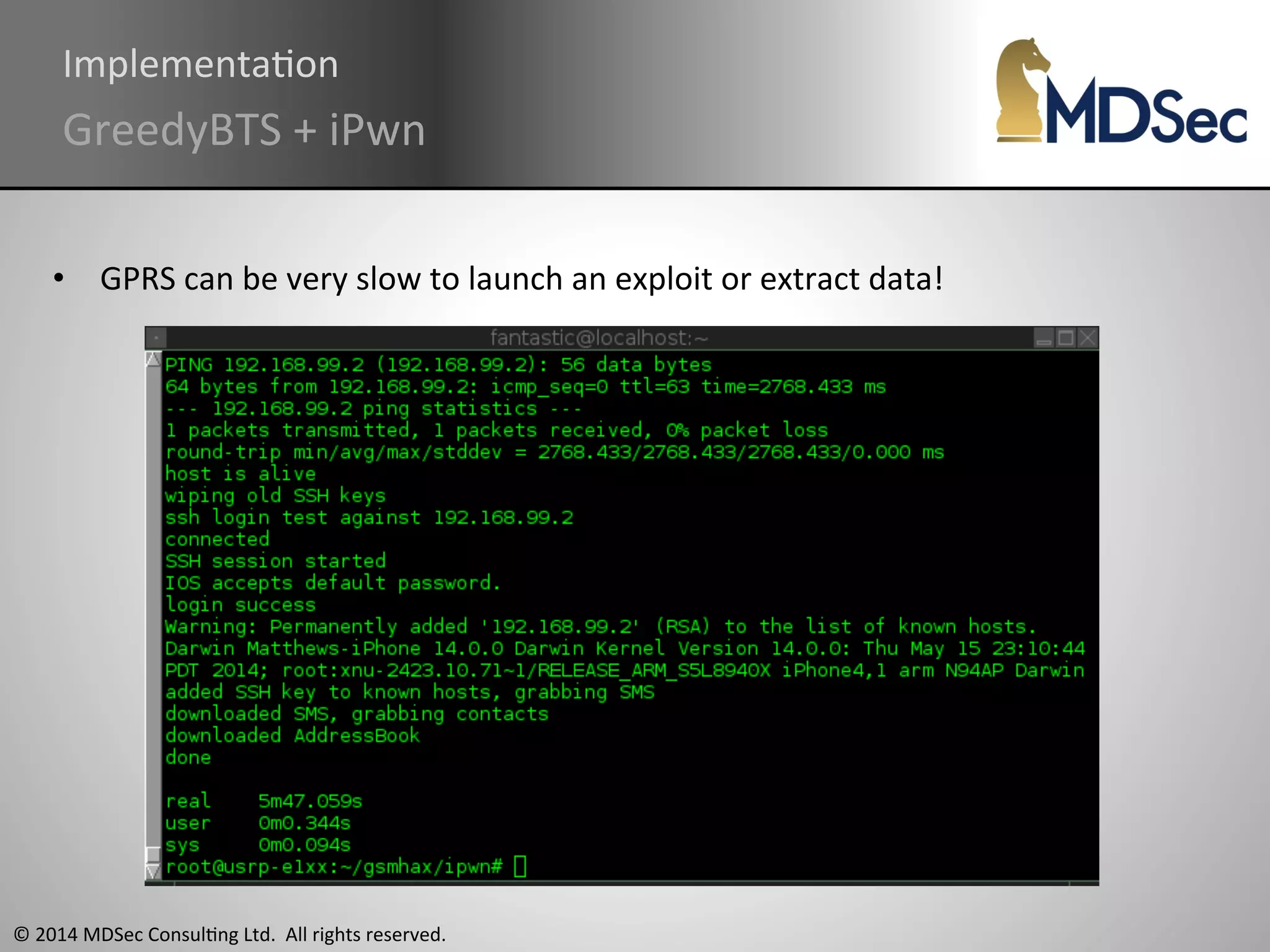
The document provides a comprehensive overview of the vulnerabilities and technical aspects of 2.5G GSM networks, including discussions on architecture, signal processing, and security flaws. It highlights various attacks that can be implemented against GSM, the components involved such as SIM cards and base transceiver systems, and tools available for analysis. Key topics include encryption weaknesses, diagnostic tools, and methods for cloning base transceiver stations (BTS) to exploit network vulnerabilities.