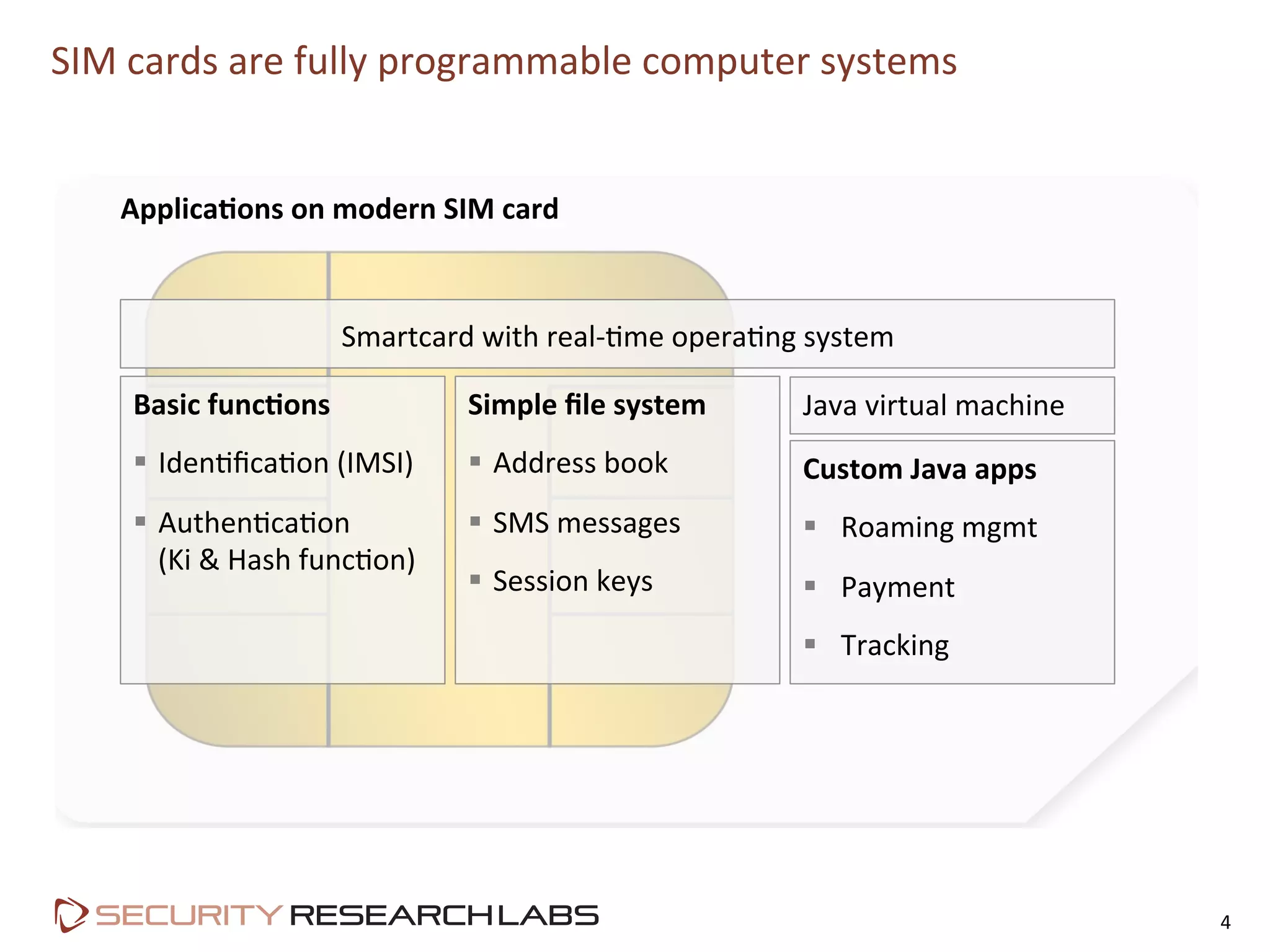
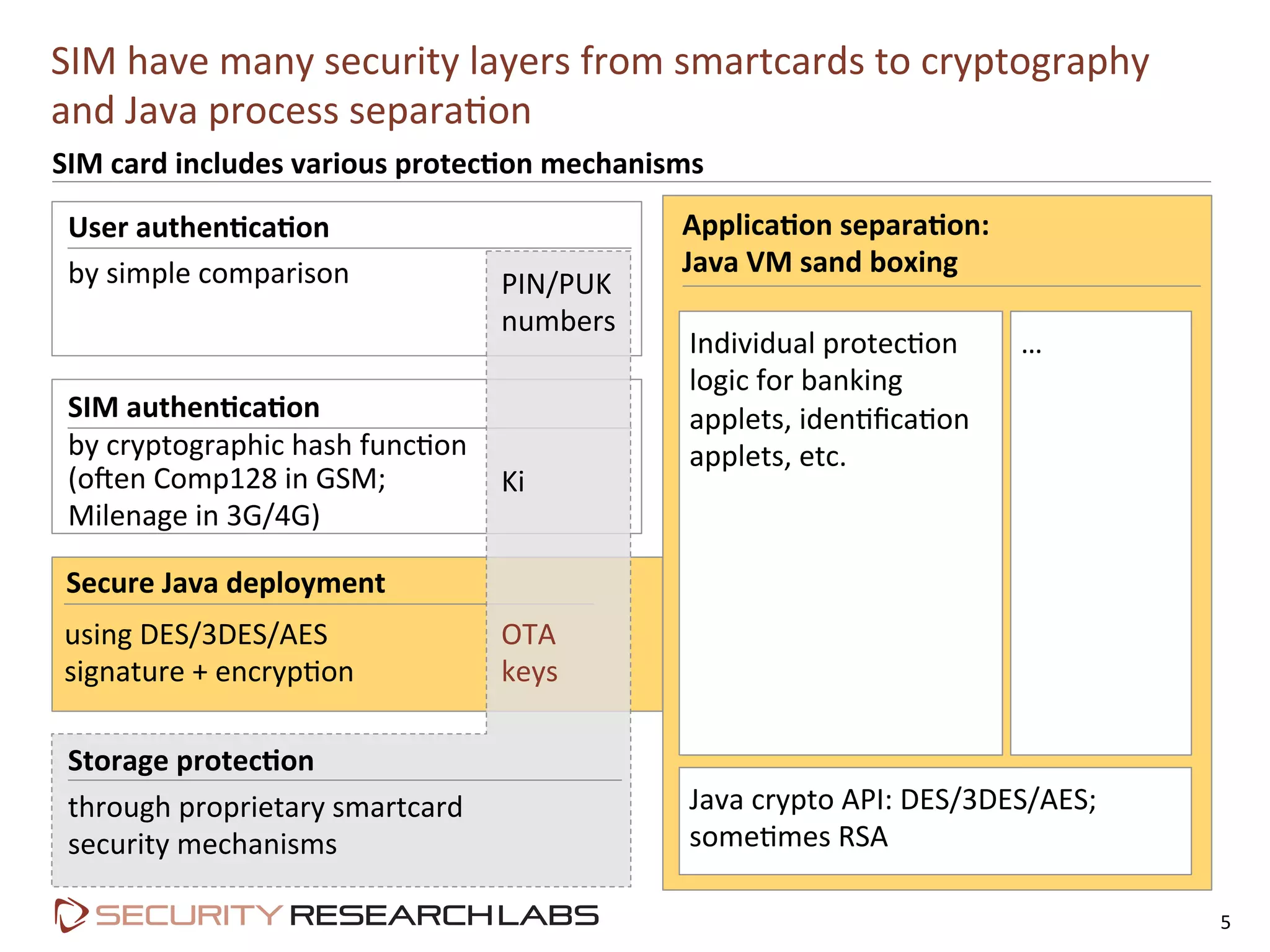
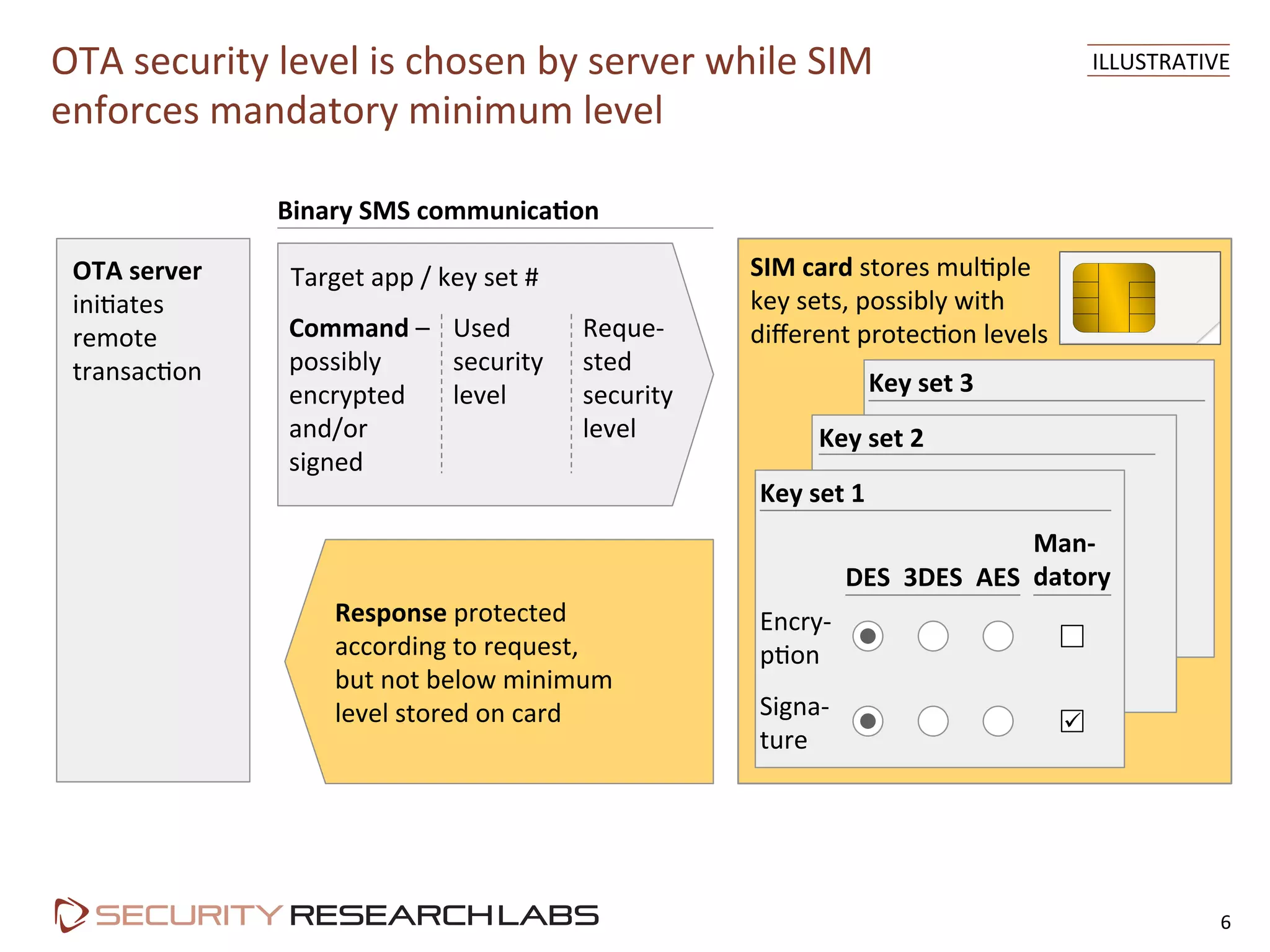
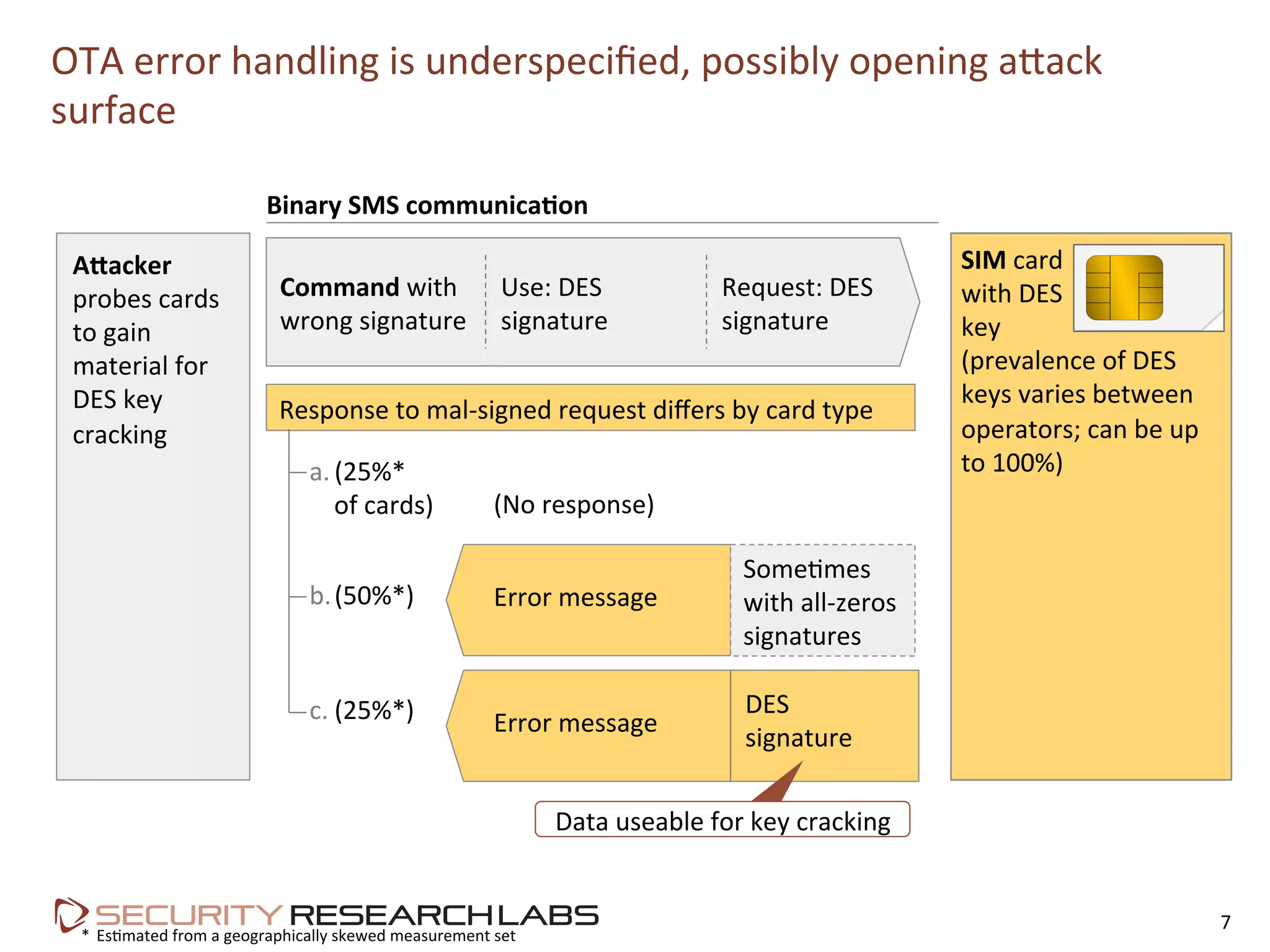
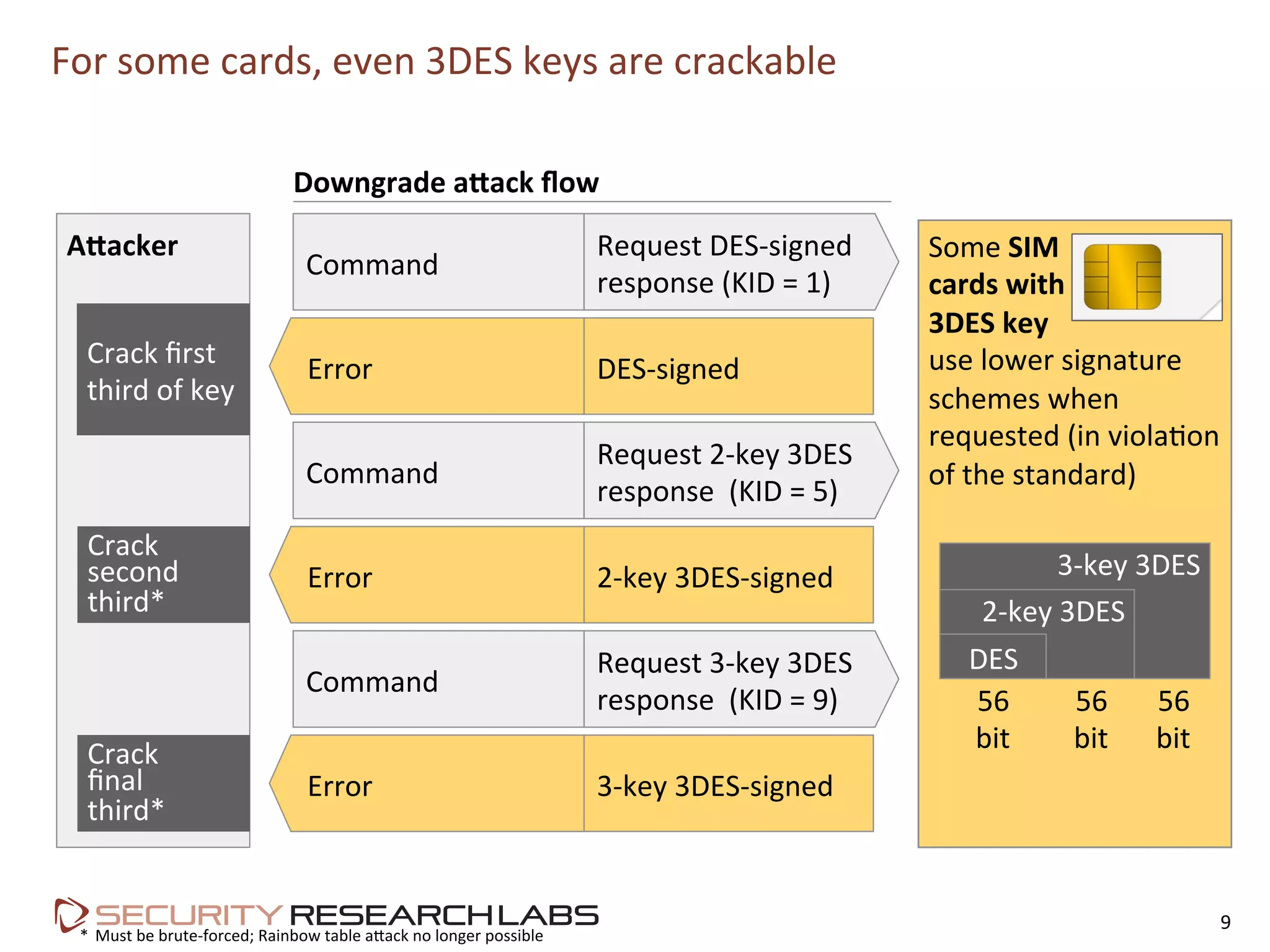
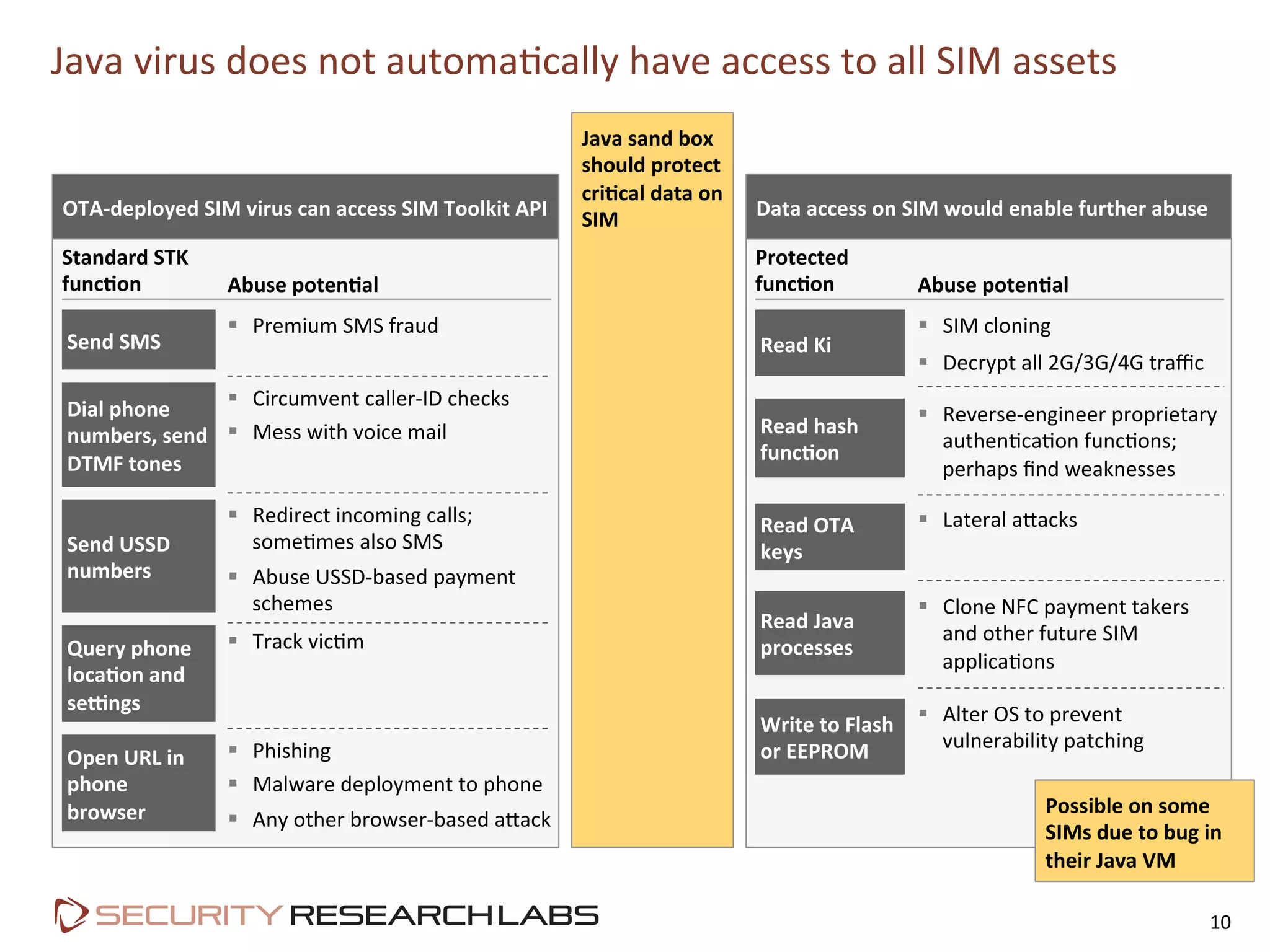
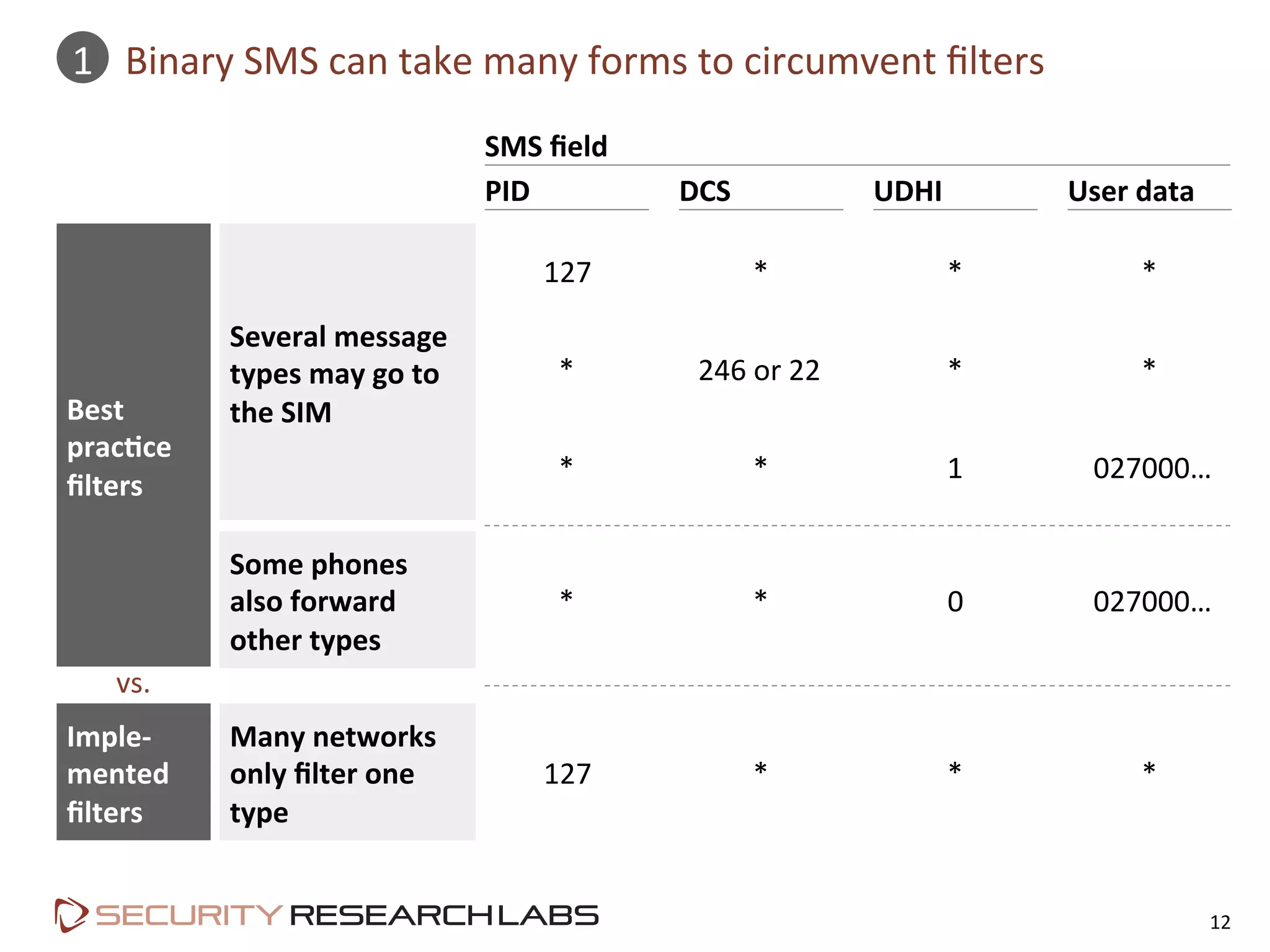
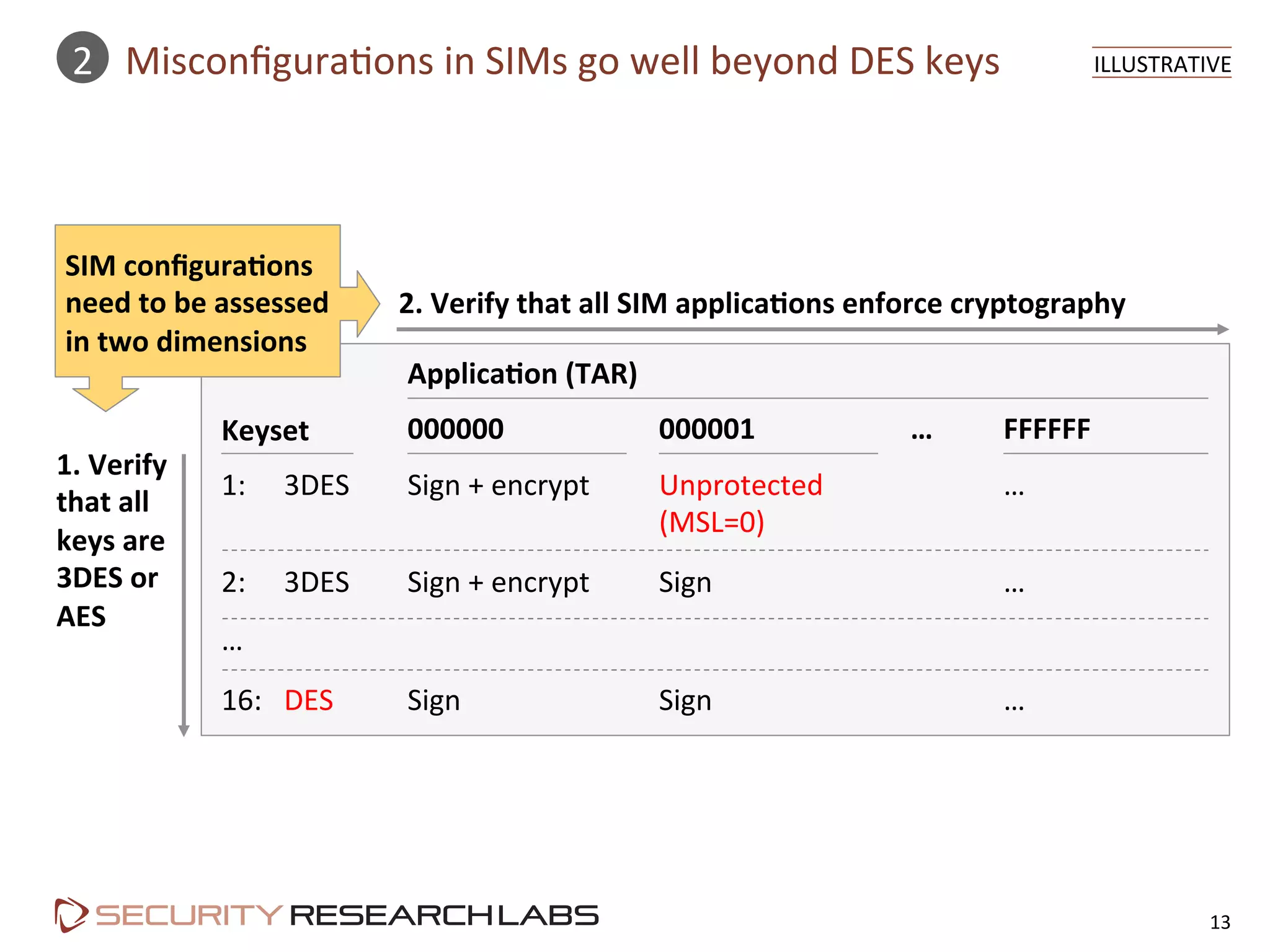
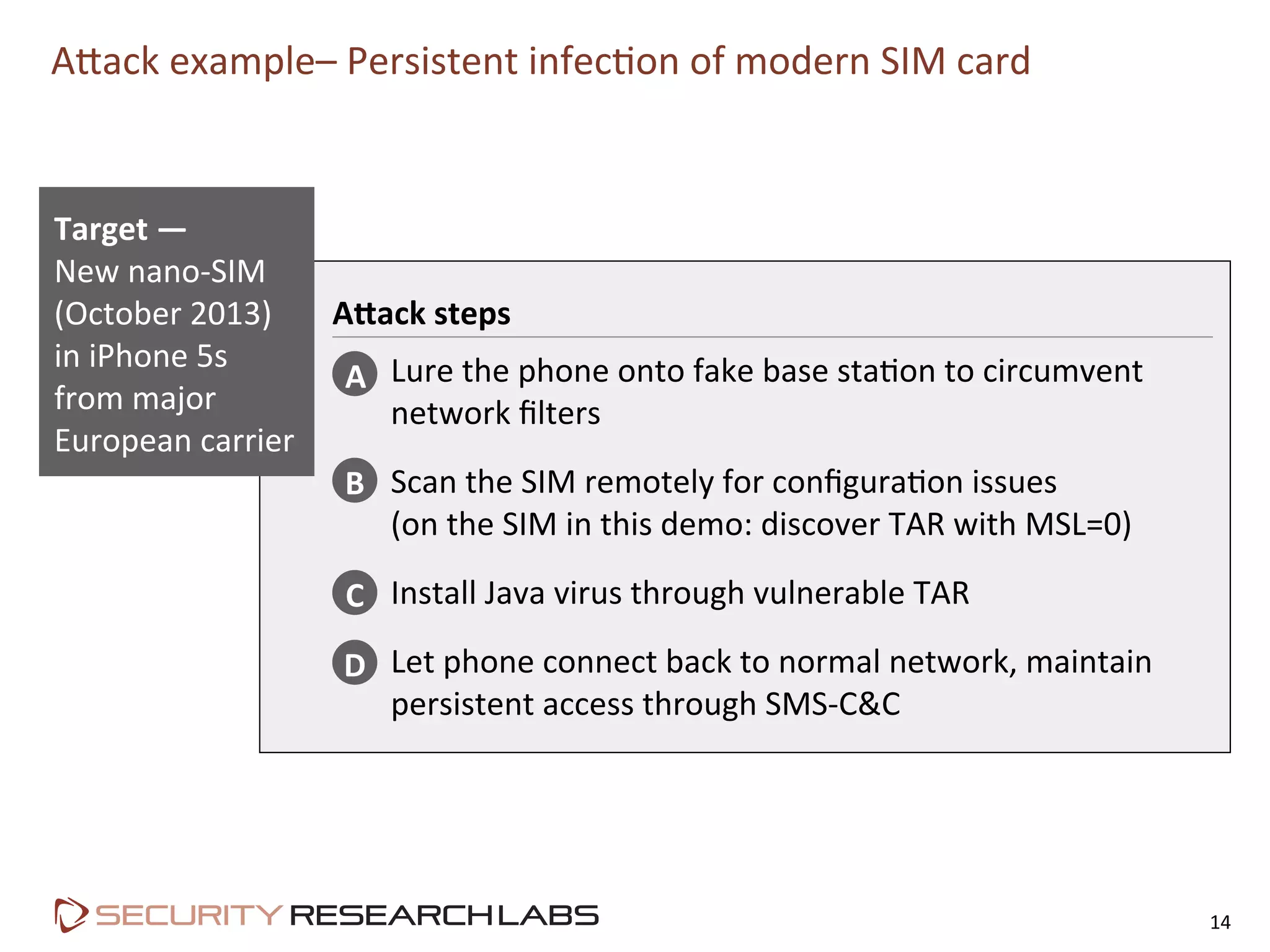
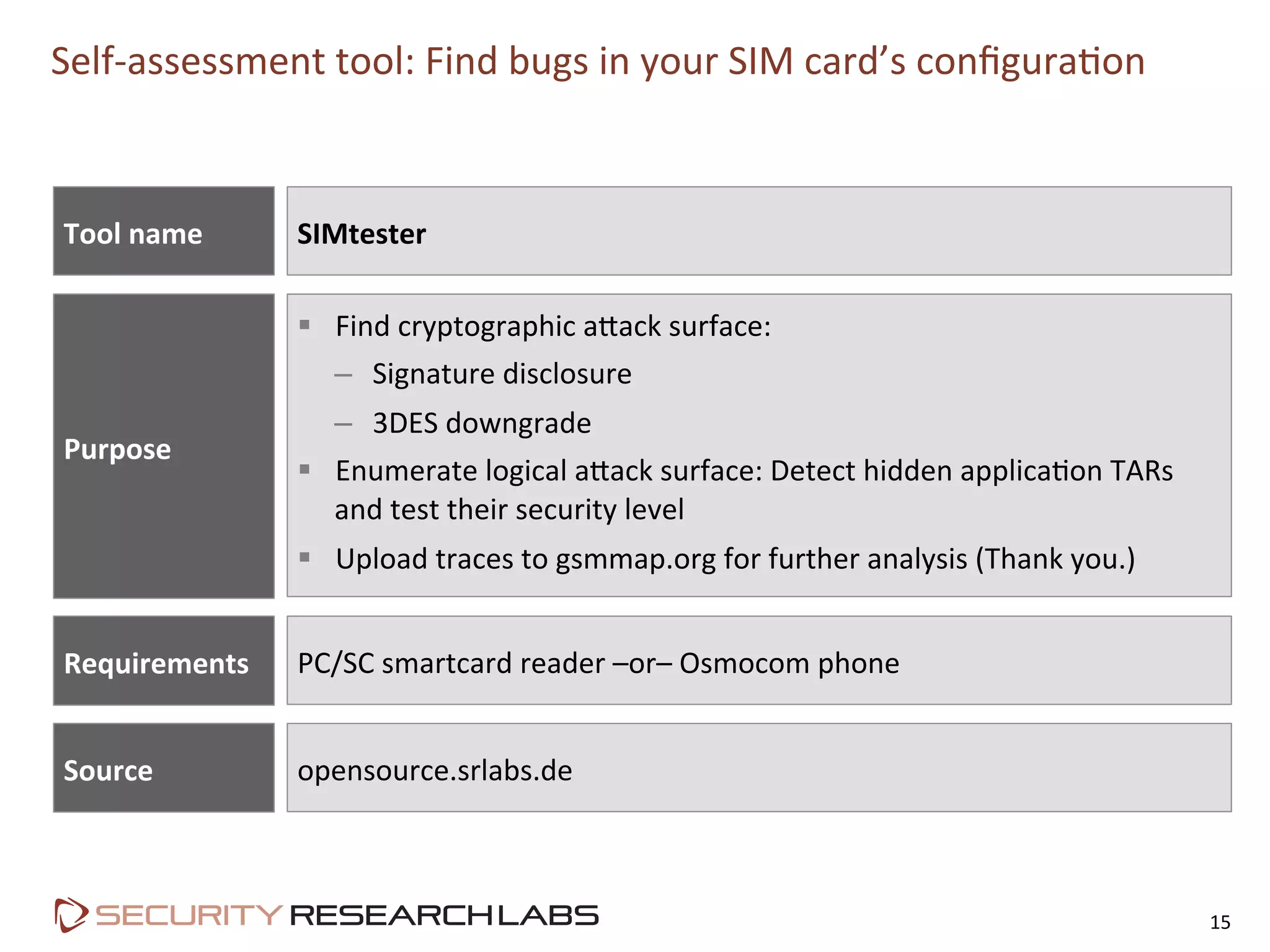
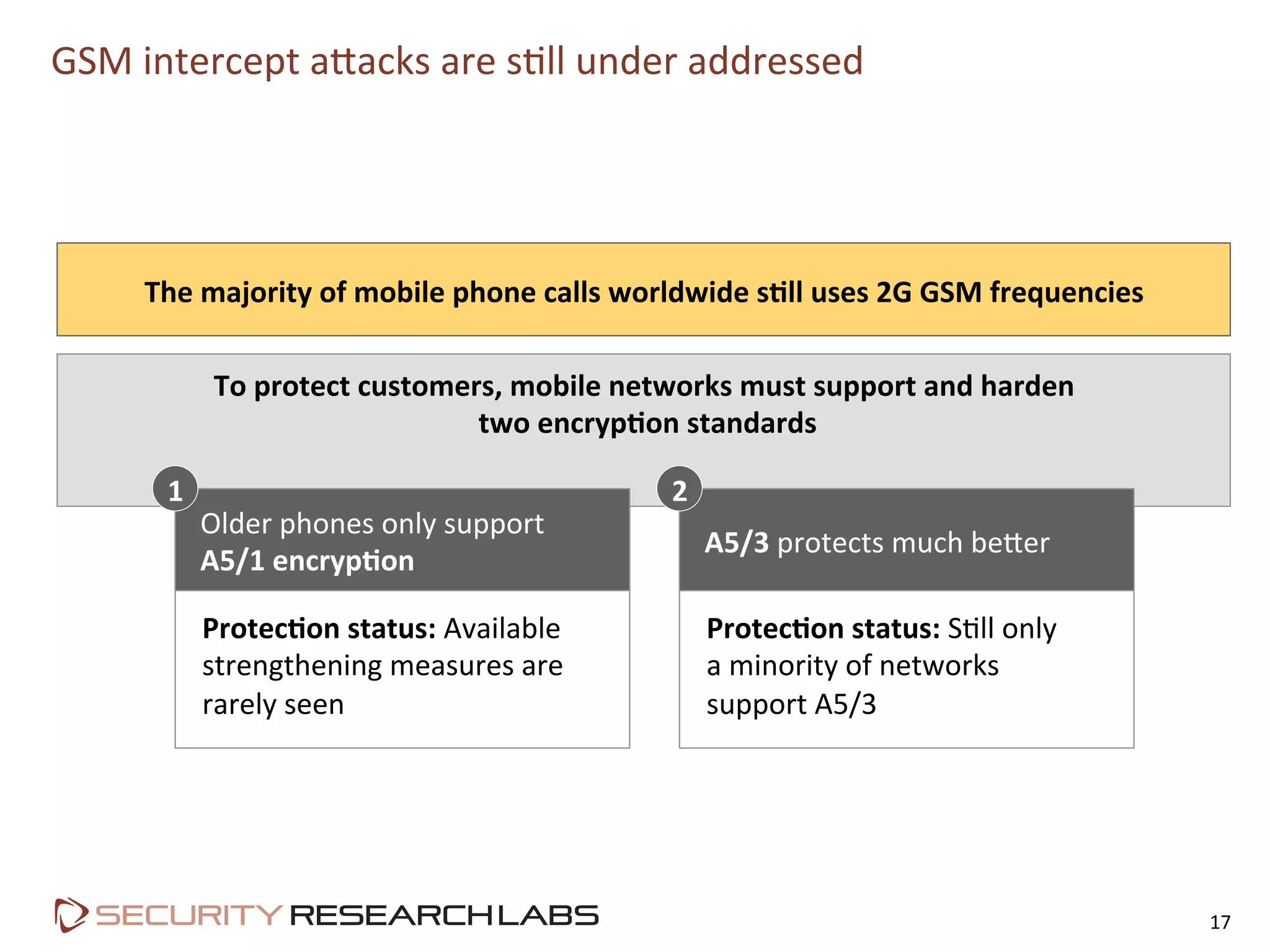
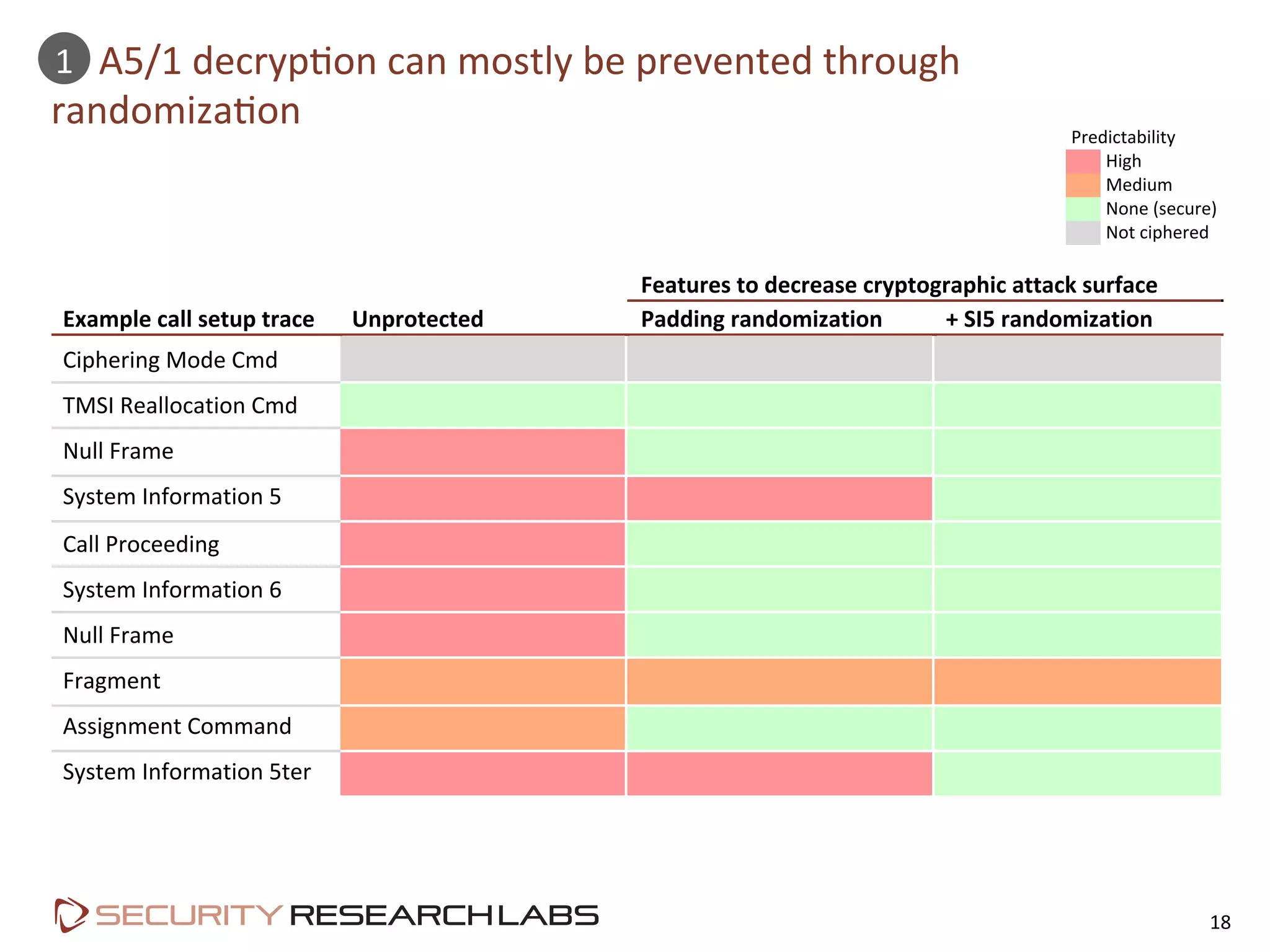
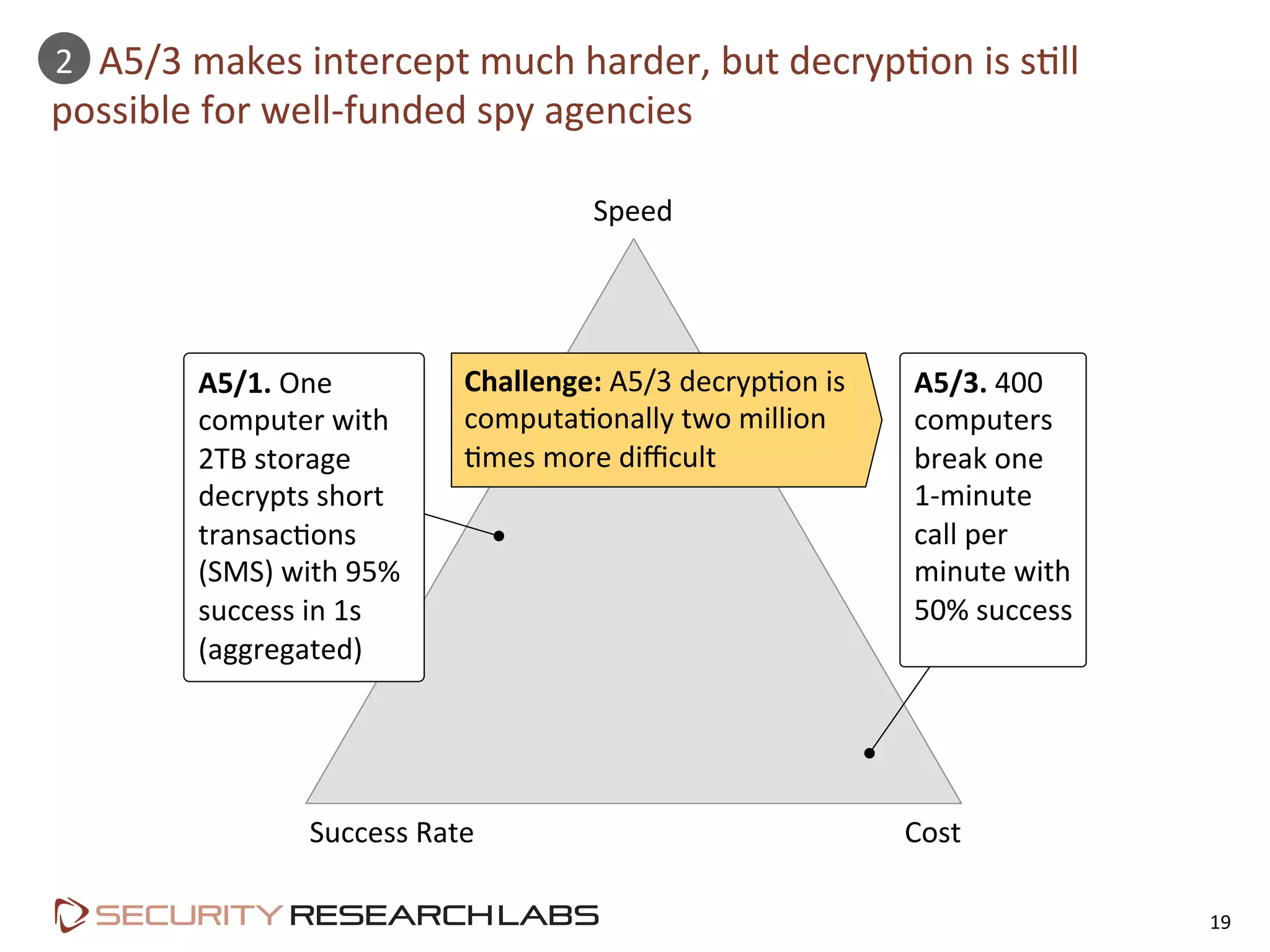
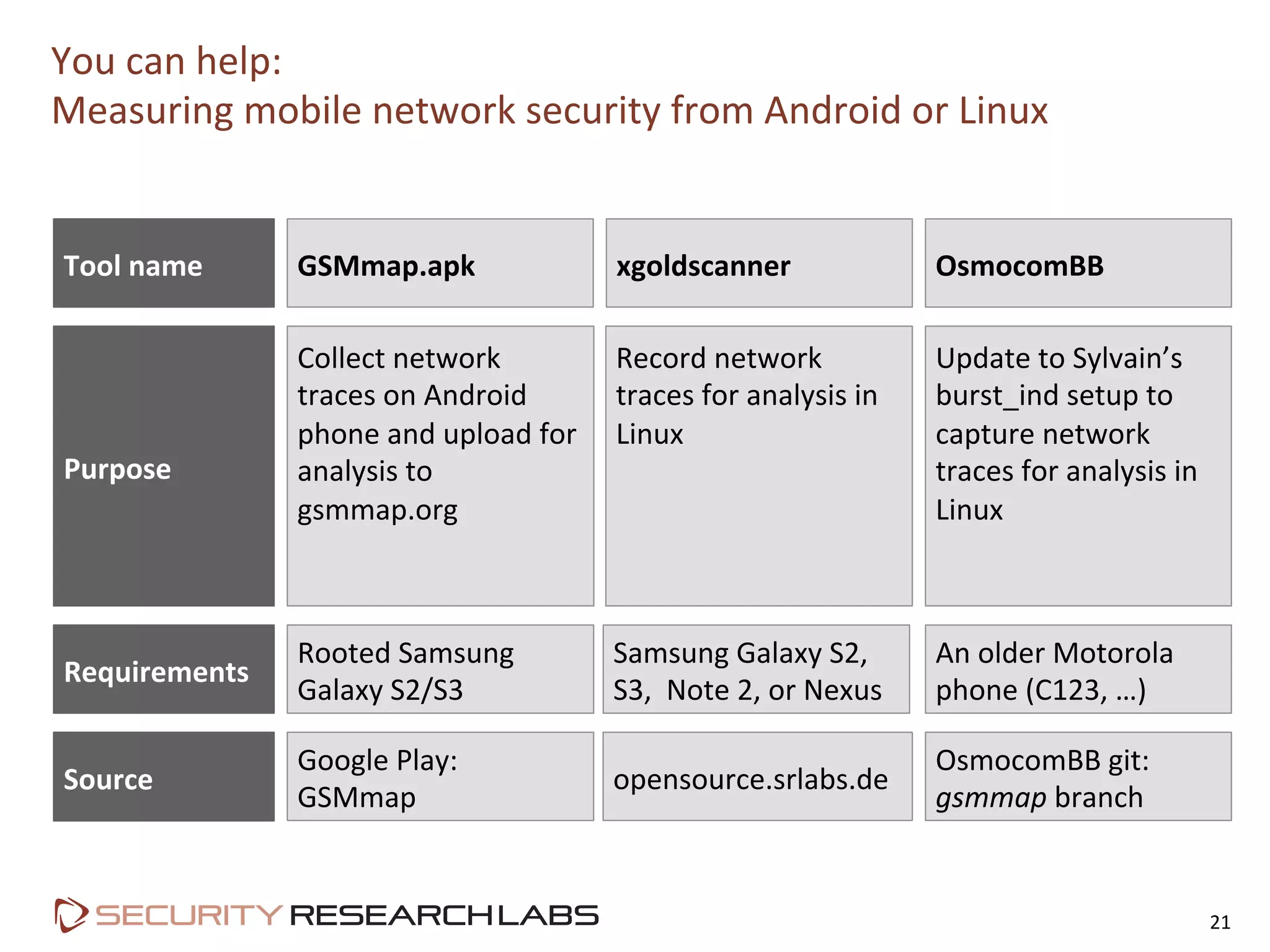
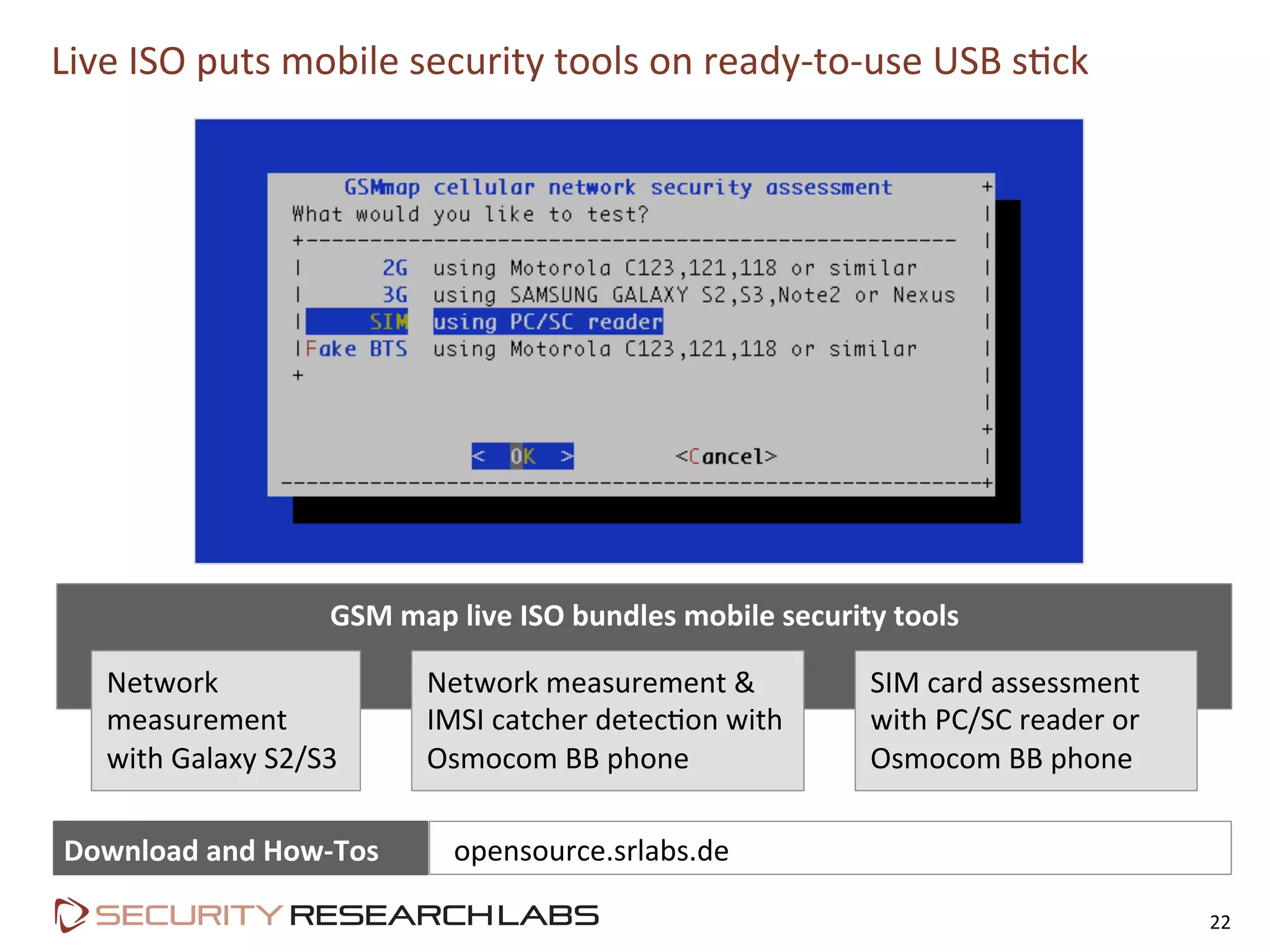
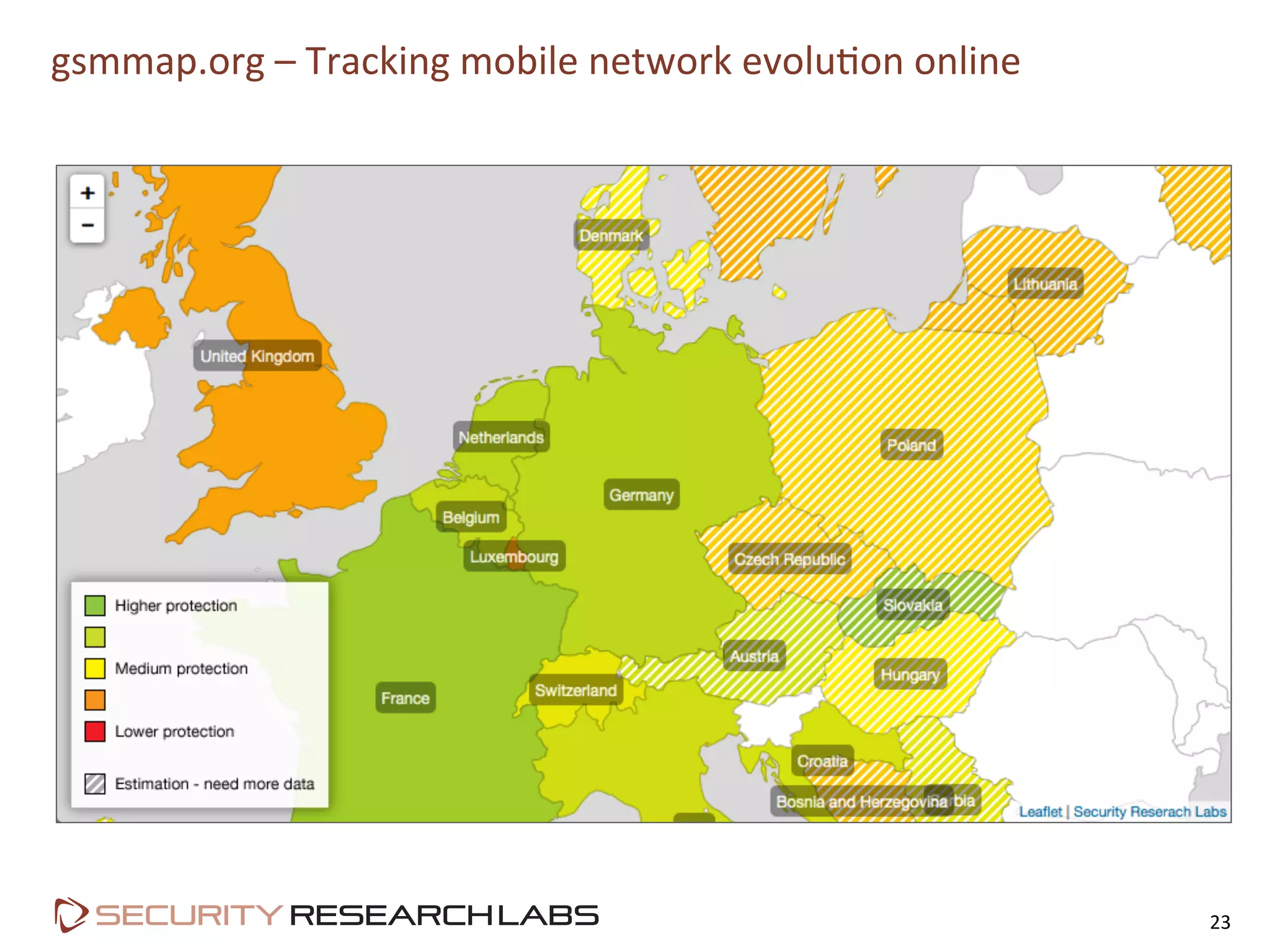
This document summarizes the evolution of attacks against mobile networks and industry responses. It discusses past attacks against SIM cards, including cracking DES keys using error responses. More advanced SIMs are fully programmable computers running Java with various security layers, but some still have crackable cryptographic keys. The talk will cover SIM attacks, GSM intercept techniques, and efforts to ensure network operator honesty.