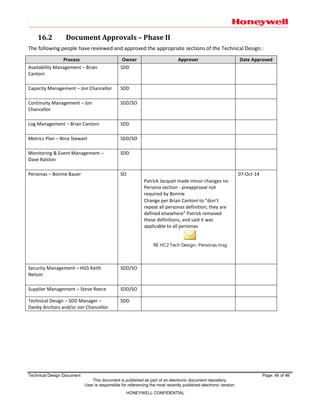
The document provides a technical design for a Hybrid Cloud Computing (HC2) platform in 4 phases. Phase I will provide infrastructure as a service (IaaS) on Windows and Linux to simplify development environments. It will leverage existing assets where possible. Future phases will expand services and integrate additional tools to provide a flexible, scalable and highly available cloud platform behind the company firewall for development workloads. The design prioritizes simplicity, customer experience, and leveraging existing technologies.


















![Technical Design Document Page: 20 of 46
This document is published as part of an electronic document repository.
User is responsible for referencing the most recently published electronic version.
HONEYWELL CONFIDENTIAL
4.4Host Name Database
4.4.1 Phase I
This service integrates with the Host Name database. After receiving a Hostname, the workflow will
proceed to Infoblox to receive IP and DNS. The following list details the interaction:
CMP interaction occurs via a WSDL API call to the host name db
http://10.192.24.109:90/CreateHostNameUtil.asmx?WSDL Host Name QA
http://10.192.24.108:91/CreateHostNameUtil.asmx?WSDL Host Name Prod
CMP will have to pass the following variables to request a hostname:
o Static
LID code – unique for cloud
Type = Virtual Host
ISR#
Model #
o Dynamic
OS Type = W (= Windows) or U (=Linux)
Assigned To:
Assigned By:
Notes (optional field)
Example of the return; hccpw12345
o NOTE: A Host name must never be reused
4.4.2 Phase II
No changes are to be made to the Host Name Database architecture for Phase II.
4.5Infoblox
4.5.1 Phase I
This service integrates with Infoblox, which will be configured identically in DCE and DCW.
Stand up a dedicated Infoblox environment
CMP will interact with Infoblox via a provided plug-in for the Cisco process orchestrator
o CMP will be able to reserve IP addresses
o CMP will be able to create DNS ‘A’ records
o Return IP addresses back to the pool upon deprovisioning
o Remove ‘A’ records upon deprovisioning
Will act as authoritative for a dedicated TLD for cloud
o The existing enterprise DNS system [IP control] will have a forwarder record that points
to Infoblox for the cloud TLD
CIAC comes with sample code for Infoblox integration out of the box via Perl Infoblox module
Customers can also invoke Infoblox via the WAPI REST API**, which was tested using Infoblox
IPAM Express free software through the following steps:
o Retrieve Port groups and UCS VLANs
o Infoblox Get IP Address via WAPI
o Set Multiple Variables](https://image.slidesharecdn.com/31e12727-d1fd-4510-903f-28b7746bfc63-150312154245-conversion-gate01/85/09-HC-SDP-Tech-Design-20-320.jpg)