How to Configure Port-Security on Cisco Switch for Enhanced Network Security .pptx
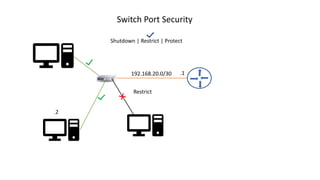
- 1. 192.168.20.0/30 .1 .2 Restrict Switch Port Security Shutdown | Restrict | Protect
- 2. Switchport security-part-01 Violation: shutdown Step 1: Enter interface configuration mode and input the physical interface to configure. We will be using FastEthernet 0/2 as an example. Switch(config)# interface FastEthernet 0/2 Step 2: Set the interface mode to access. The default mode, which is dynamic desirable, cannot be configured to be a secured port. Switch(config-if)# switchport mode access Step 3: Enable port security on the interface. Switch(config-if)# switchport port-security Step 4: Set the maximum number of secure MAC addresses for the interface, which ranges from 1 to 3072, wherein the default value is 1. Switch(config-if)# switchport port-security maximum {1-3072}
- 3. Switch port Action During the Port security Violation Protect Restrict Shutdown Discard Offending Traffic Yes Yes Yes Sends log and SNMP message No Yes Yes Disable the interface by putting it in an err-disabled state, discarding all No No Yes Step 5: Configure the violation mode on the port. Actions that shall be taken when a security violation is detected. Refer to the table below for the actions to be taken. Switch(config-if)# switchport port-security violation {protect| restrict | shutdown} NOTE: When a secure port is in an error-disabled state, you can bring it out of the state by issuing the command ‘errdisable recovery cause psecure-violation’ at the global configuration mode, or you can manually reenable it by entering the ‘shutdown’ and ‘no shutdown’ commands.
- 4. Step 6: Set the rate limit for bad packets. Switch(config-if)# switchport port-security limit rate invalid-source-mac Step 7: Input the identified secure MAC addresses for the interface. You can use this command to limit the maximum number of secure MAC addresses. If in case, you configure fewer secure MAC addresses than the maximum, then the remaining MAC addresses are dynamically learned. Switch(config-if)# switchport port-security mac-address {mac_address} Step 8: Verify your configuration by the following commands below. Switch# show port-security address interface FastEthernet 2/1 Switch# show port-security address
