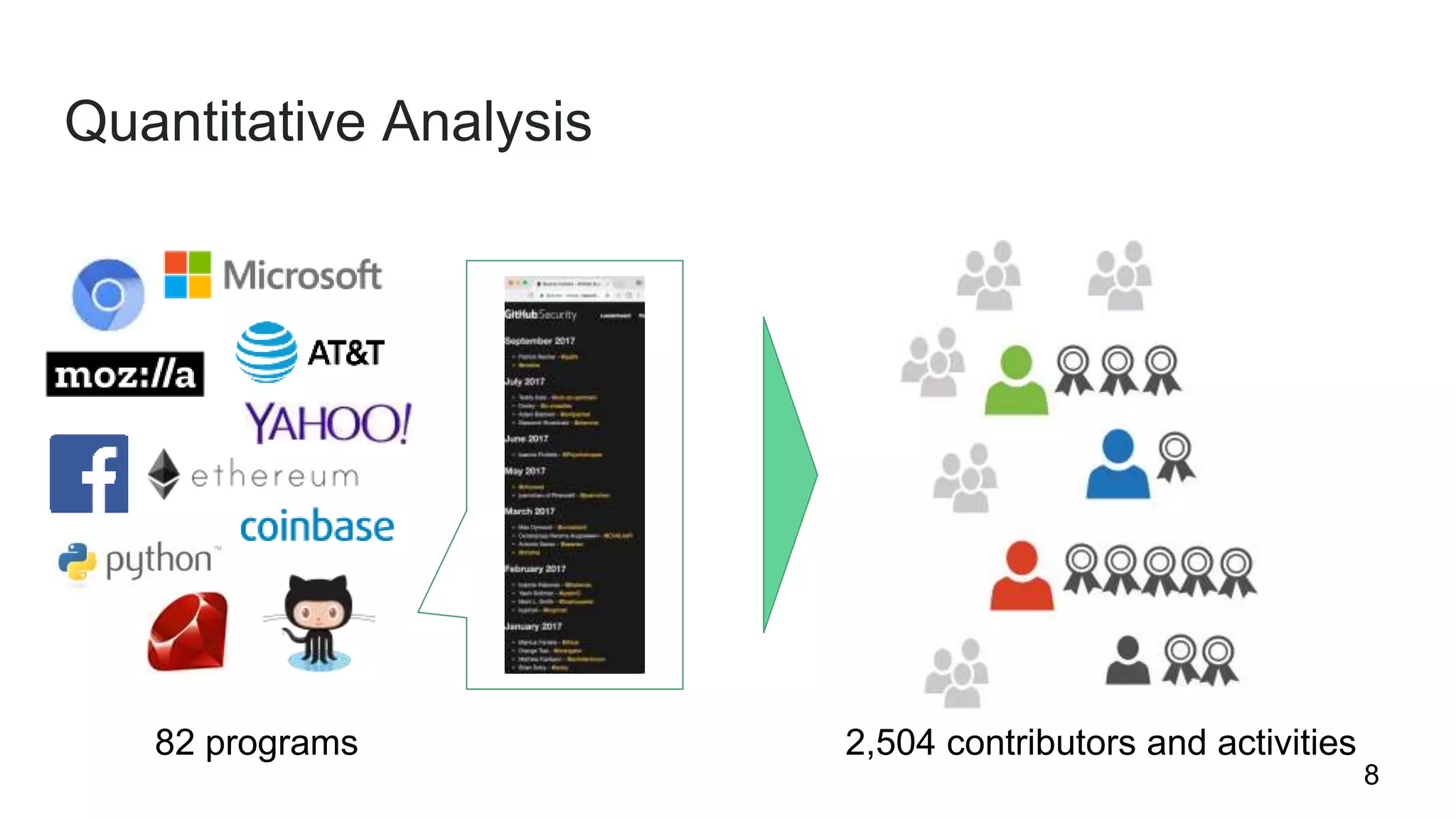
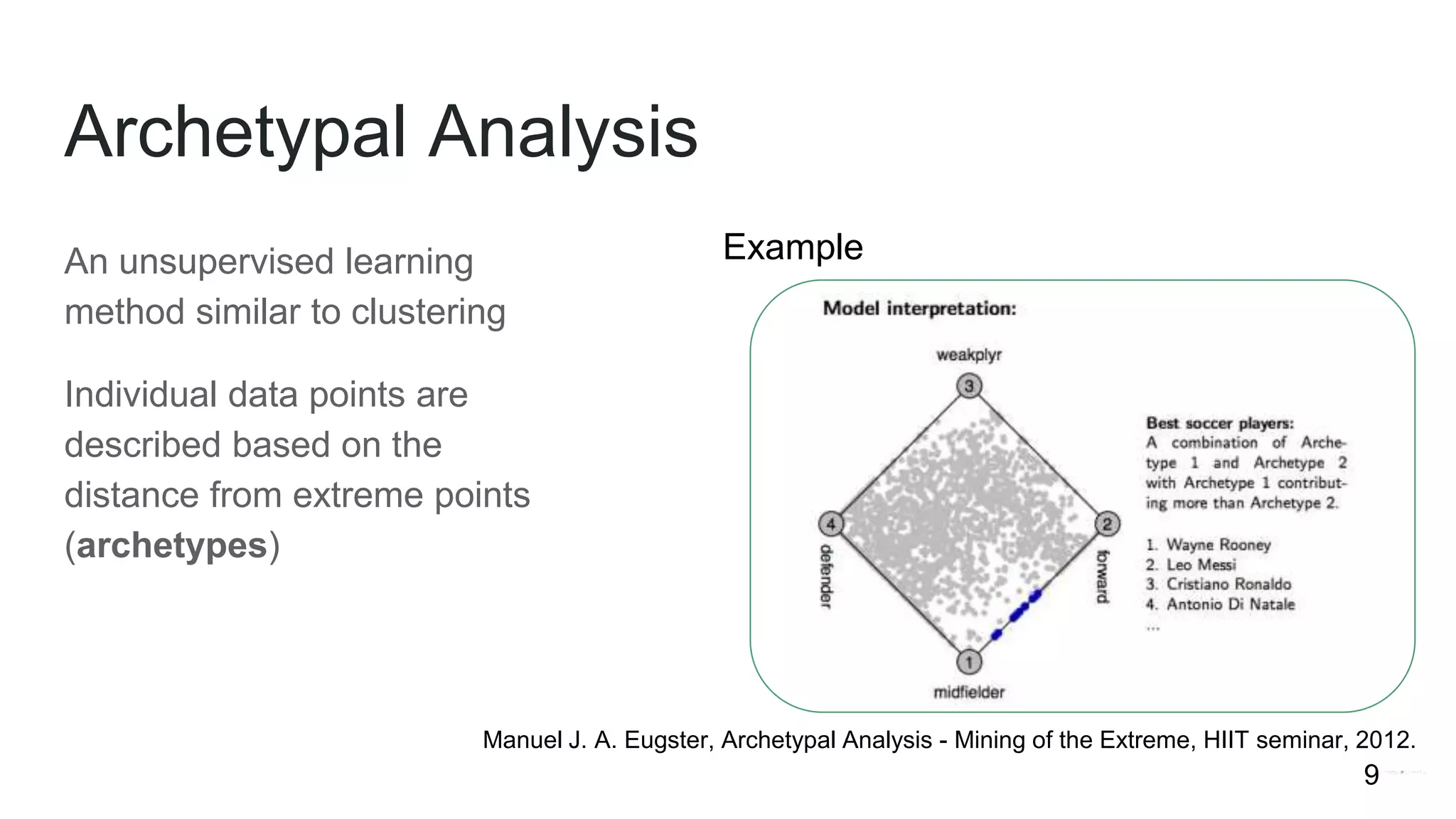
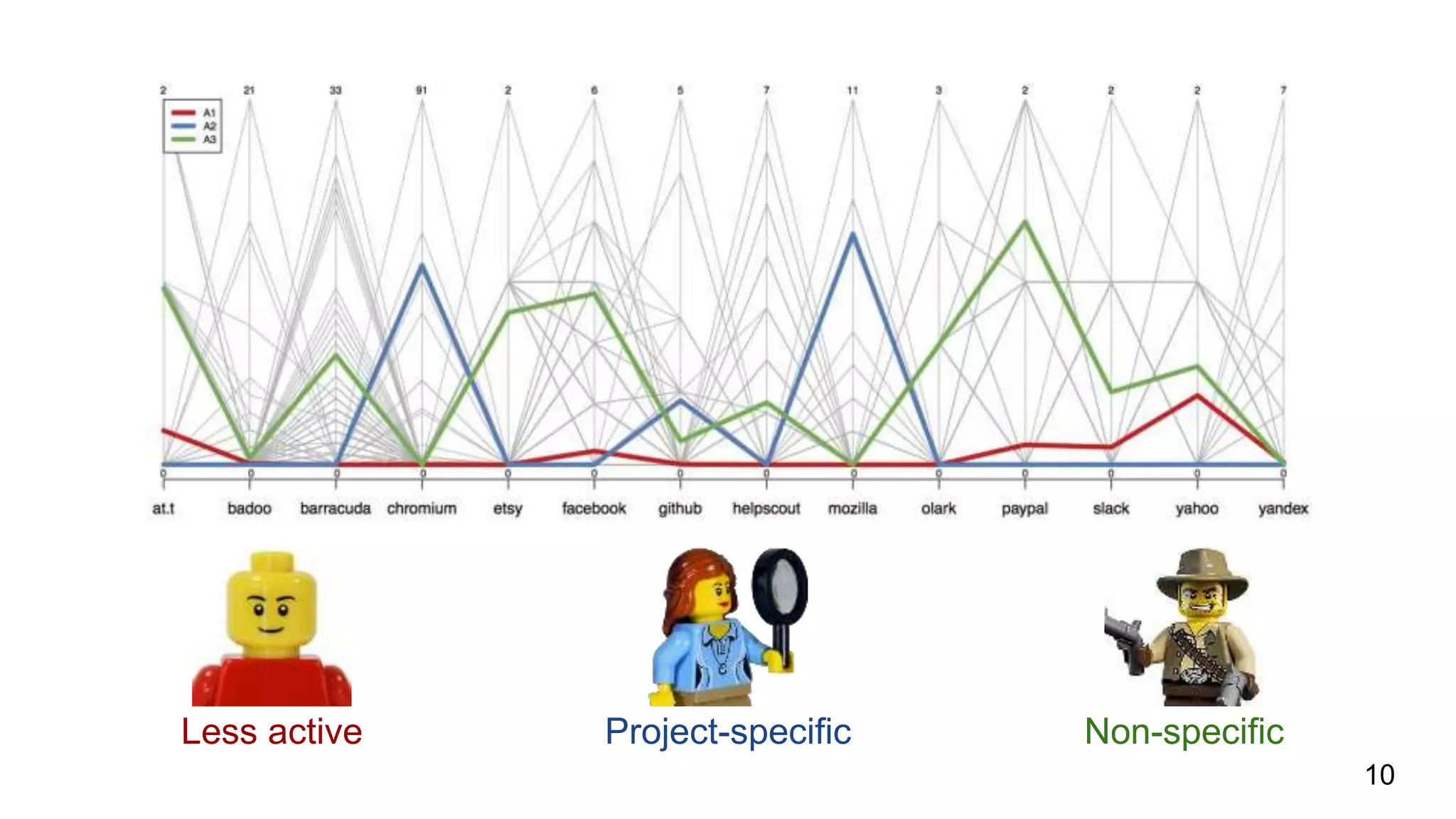
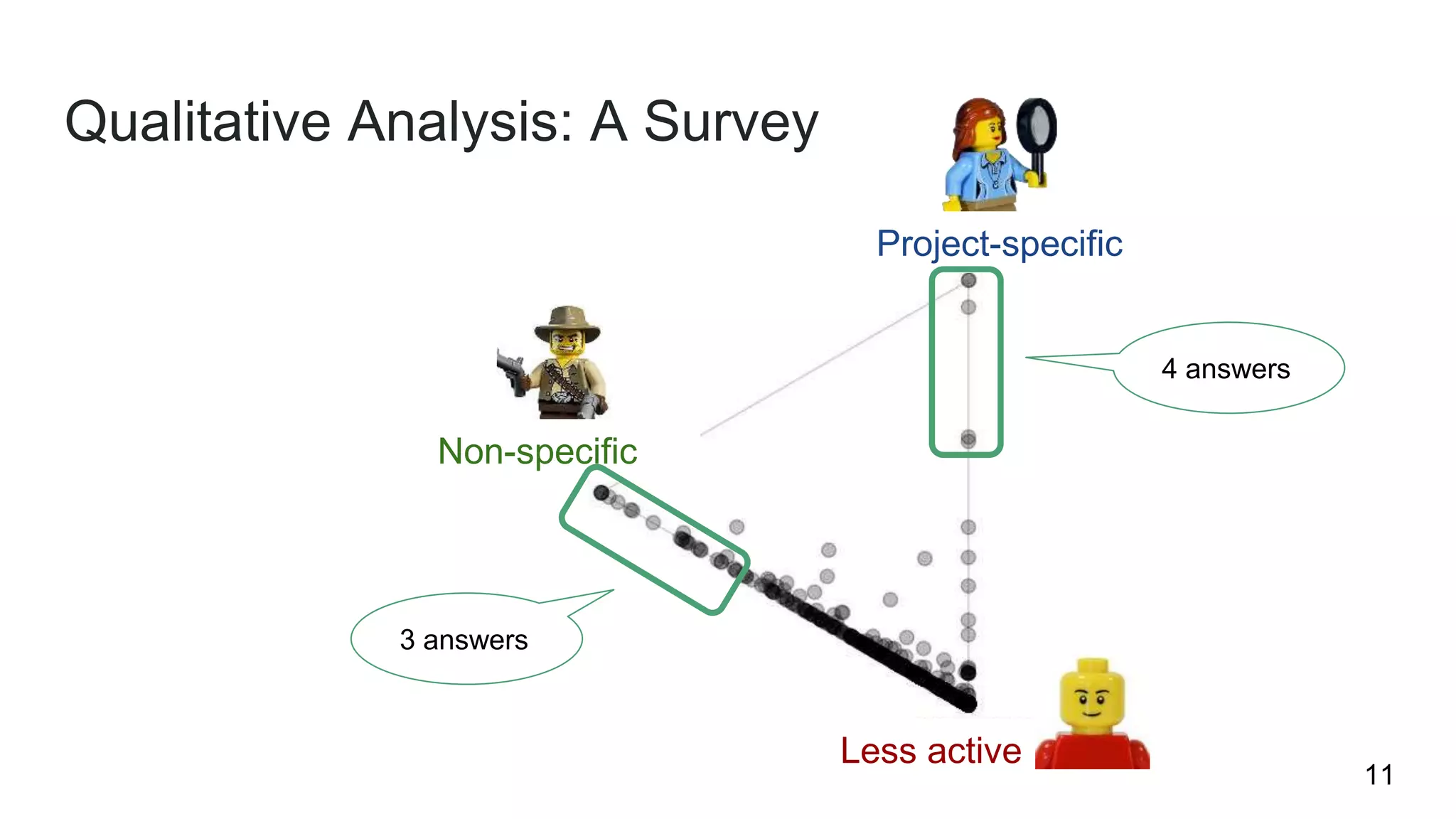
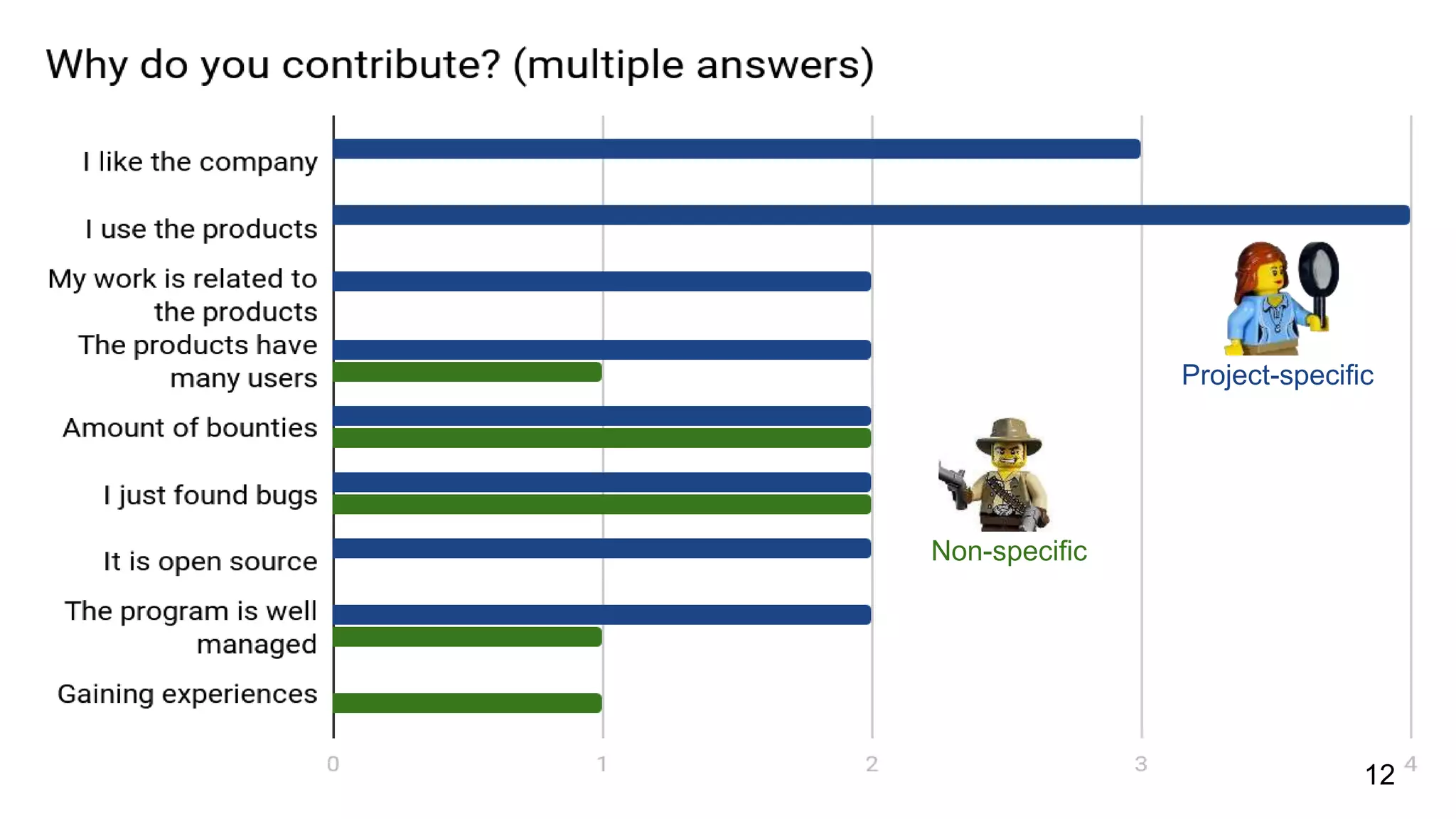
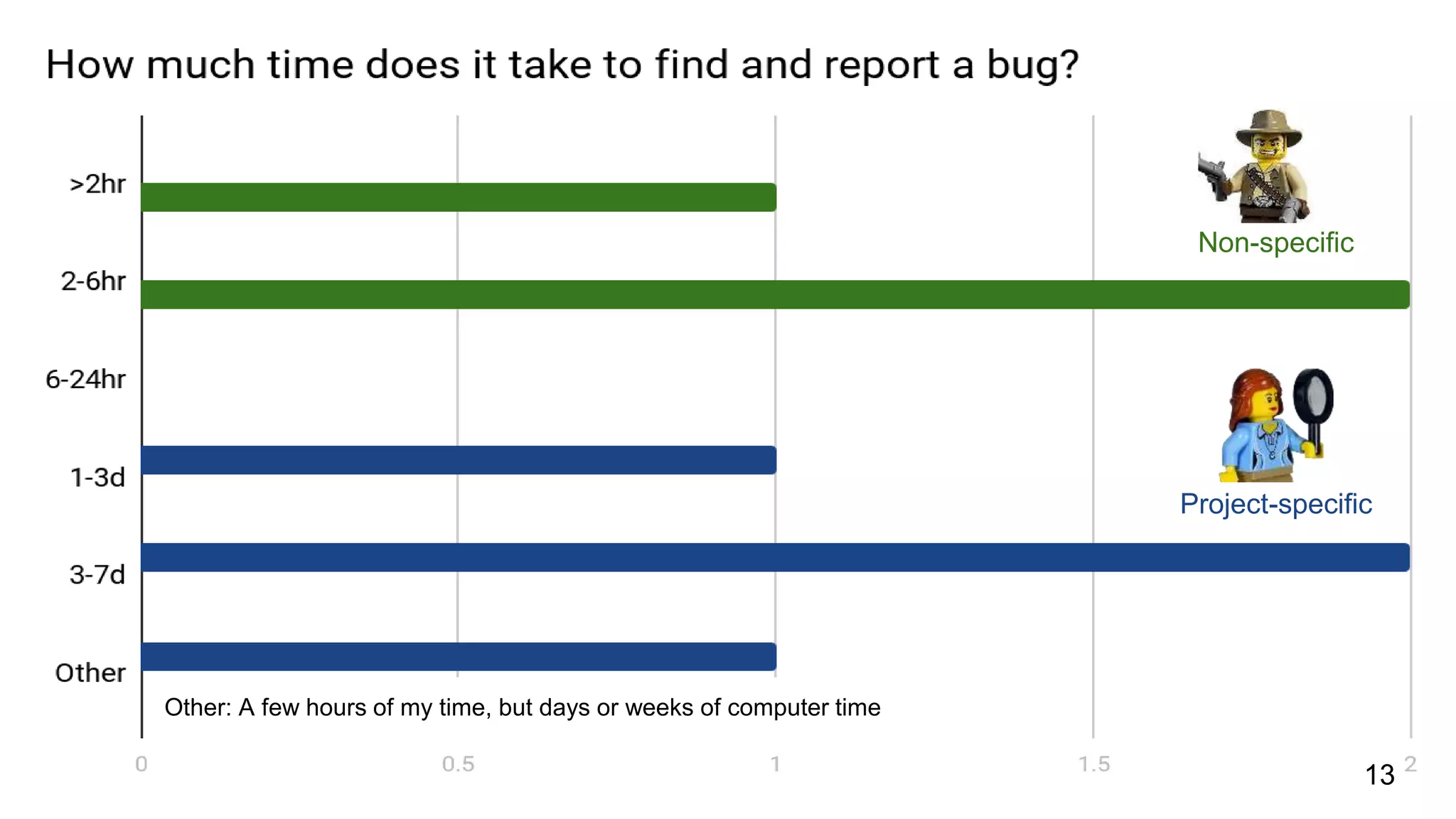
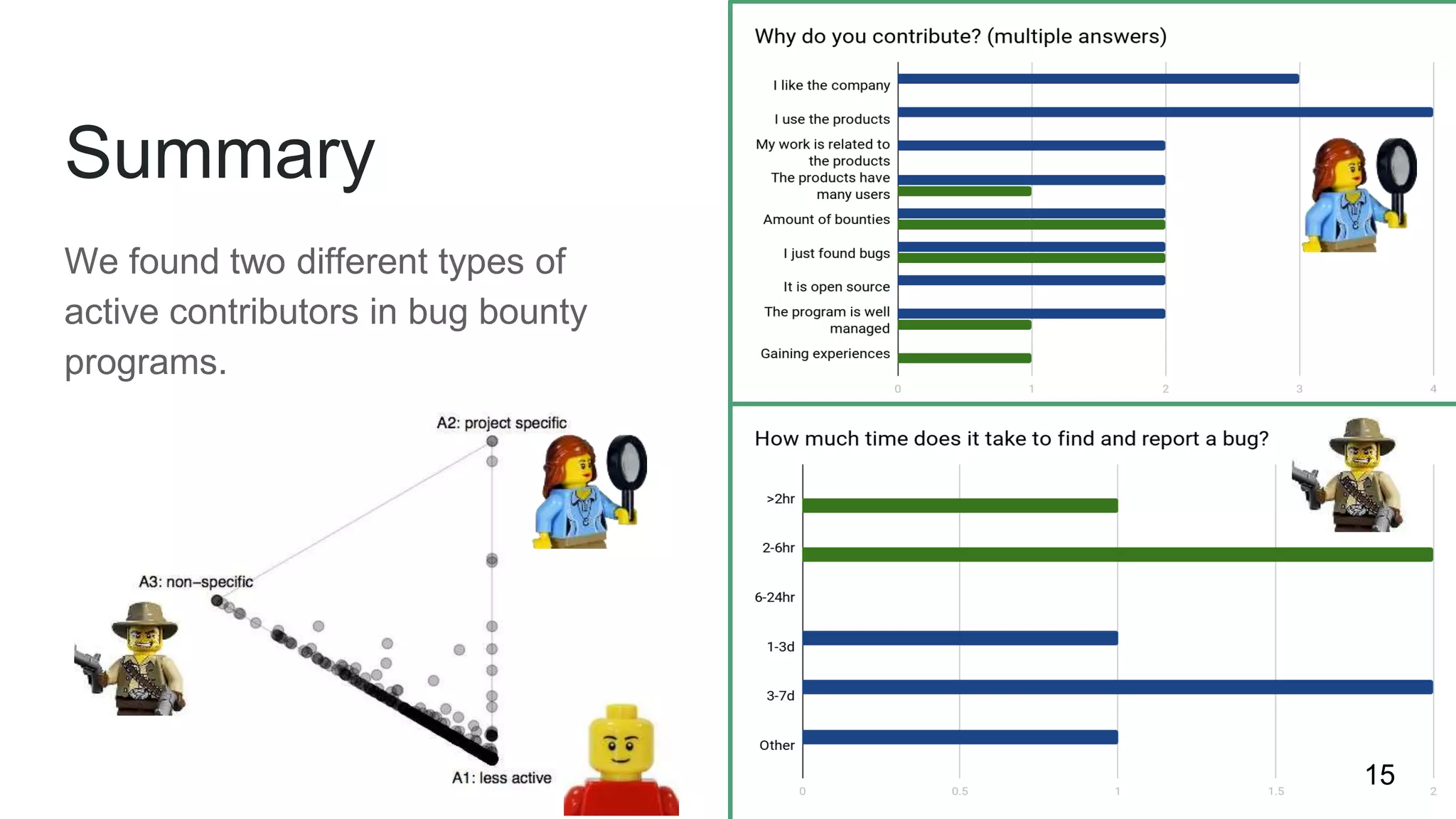
This document summarizes research into understanding the heterogeneity of contributors in bug bounty programs. Through quantitative analysis of 2,504 contributors across 82 programs and qualitative analysis via surveys, the researchers identified two main types of active contributors: project-specific contributors who work on specific programs for days finding bugs due to interest in the organizations/products, and non-specific contributors who spend at most 6 hours on a project.



![A rewards program offered by
an organization to external
parties, authorizing them to
perform security
assessments on the
organization’s assets.
Economically efficient
compared to the cost of hiring
full-time security researchers
[*].
Bug Bounty Programs (White Markets)
Esben Friis-Jensen, The History of Bug Bounty Programs, Cobalt, 2014.
5
[*] M. Finifter, D. Akhawe, and D. Wagner, An empirical study of vulnerability rewards programs,
USENIX Conf. on Security, 2013.](https://image.slidesharecdn.com/esem2017-171111135216/75/Understanding-the-Heterogeneity-of-Contributors-in-Bug-Bounty-Programs-5-2048.jpg)



![Beyond Onion Models
Bug bounty program contributors
are almost outside of traditional
software development onion models
[+]. However, talented contributors
are highly required and have a
significant impact on software
development.
Like_the_Grand_Canyon, Red onion, CC BY 2.0
16
[+] . Nakakoji et al., Evolution patterns of open-source
software systems and communities, IWPSE, 2002.](https://image.slidesharecdn.com/esem2017-171111135216/75/Understanding-the-Heterogeneity-of-Contributors-in-Bug-Bounty-Programs-16-2048.jpg)