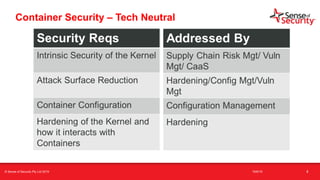
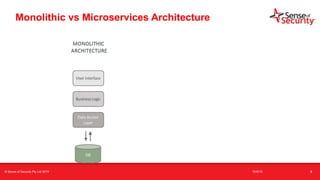
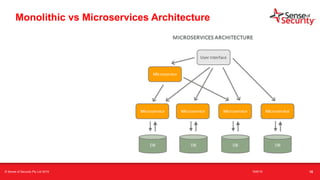
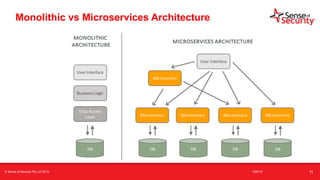
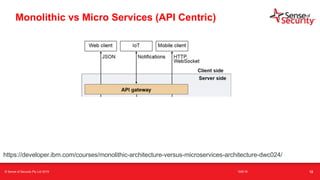
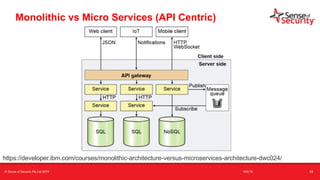
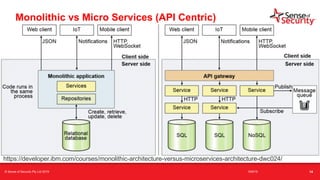
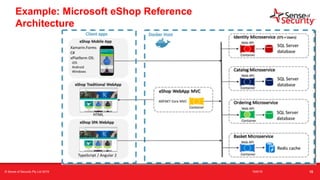
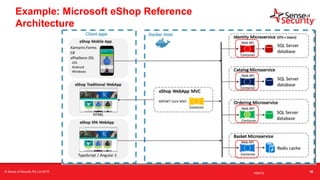
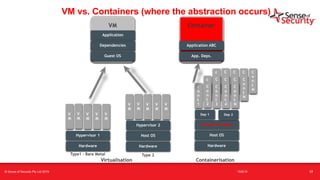
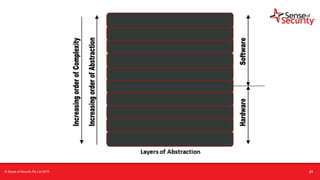
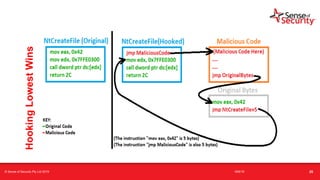
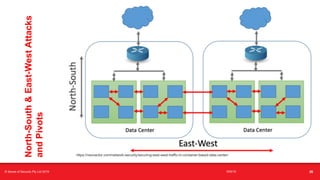
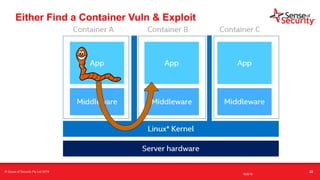
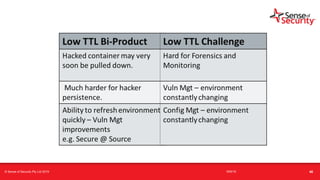
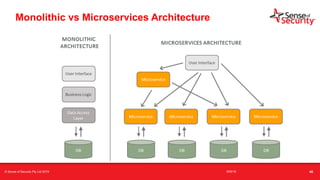
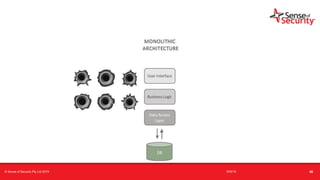
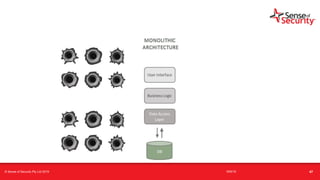
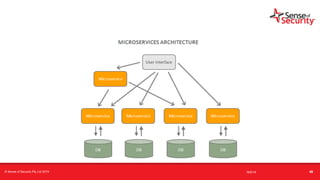
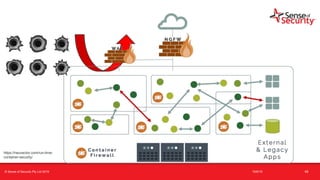
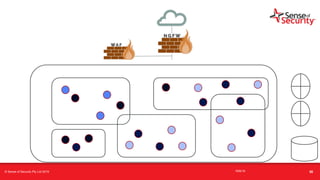
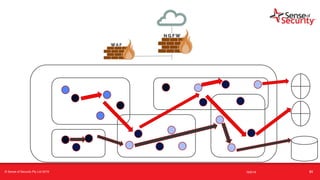
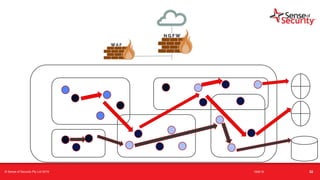
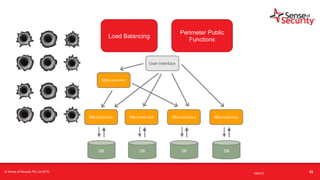
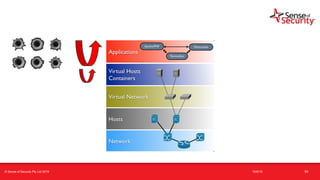
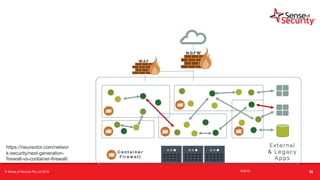
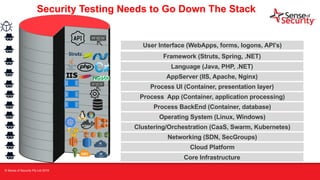
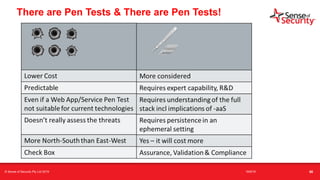
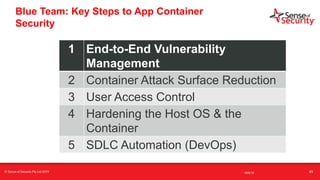
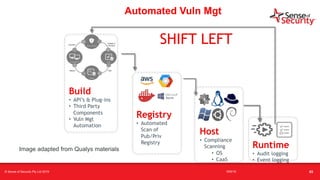
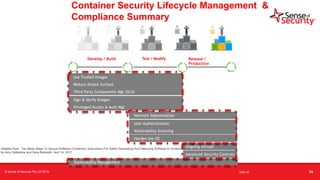
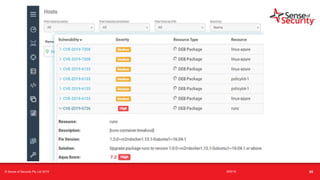
The document provides an overview of security considerations related to serverless architectures, microservices, and containers, emphasizing the importance of vulnerability management and penetration testing. It discusses the isolation benefits of containerization and the challenges posed by potential vulnerabilities and exploitation methods. The presentation outlines key security features necessary for container deployments and suggests steps for improving security practices in cloud environments.