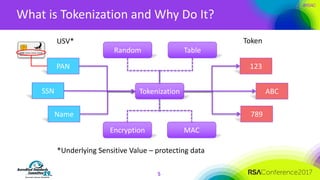
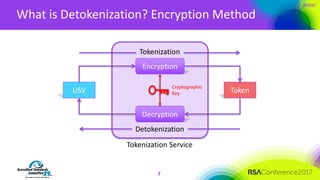
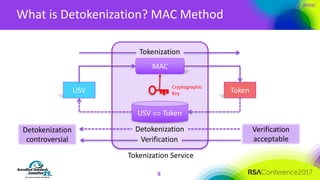
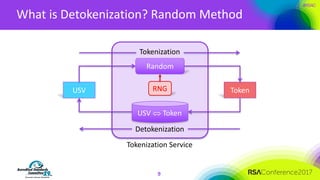
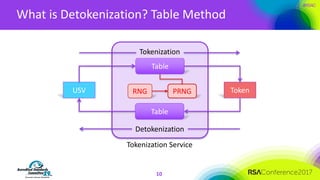
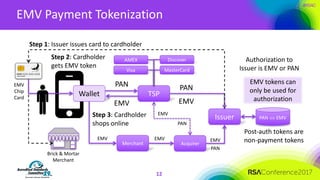
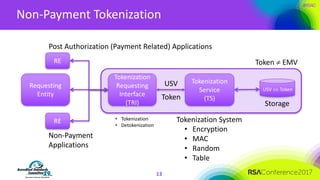
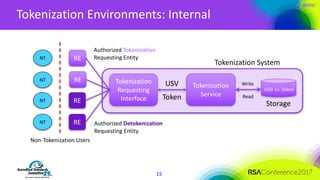
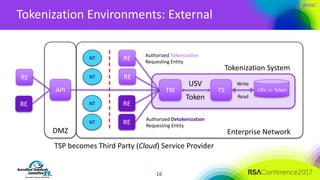
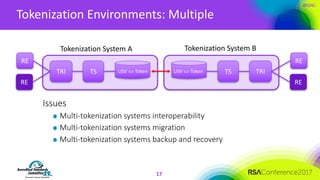
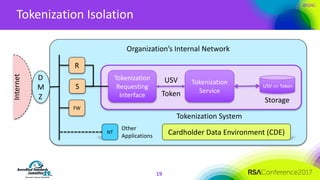
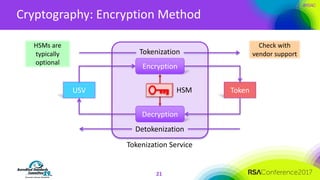
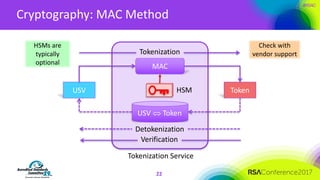
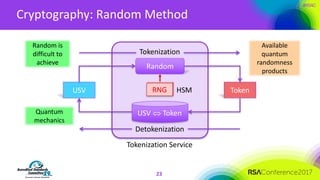
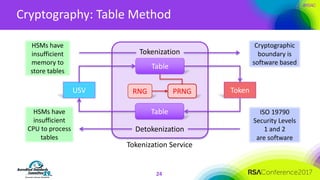
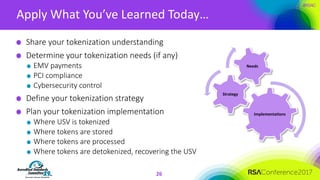
The document discusses the fundamentals and implementation issues related to tokenization in cybersecurity, emphasizing the process of replacing sensitive data with surrogate values called tokens. It outlines various definitions of tokenization, types of tokens, and the distinctions between payment and non-payment tokens, along with challenges in detokenization, system isolation, and cryptographic methods. Key conclusions highlight the importance of defining a tokenization strategy and incorporating it into broader cybersecurity policies while recognizing that tokenization may not be suitable for all scenarios.