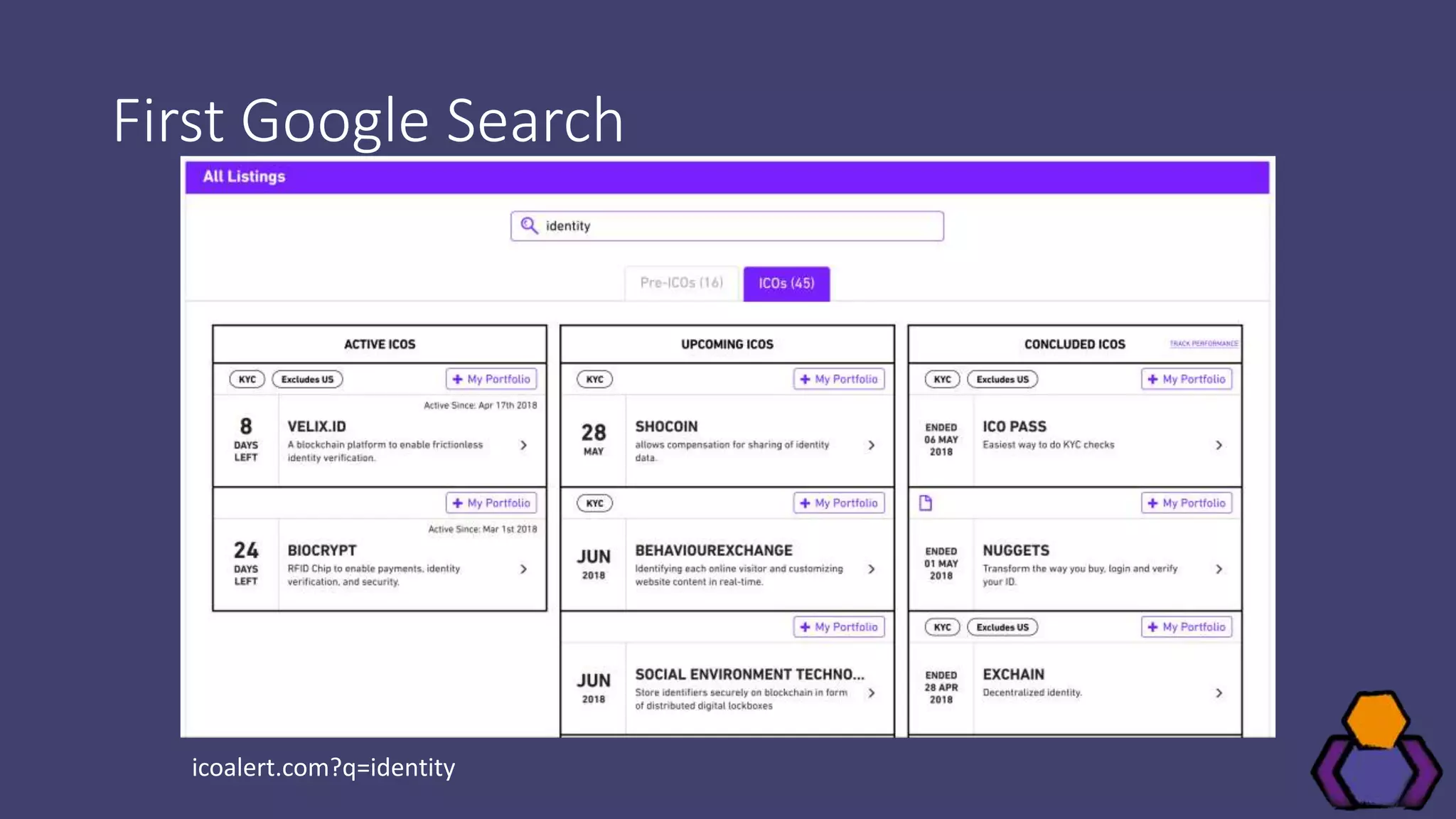
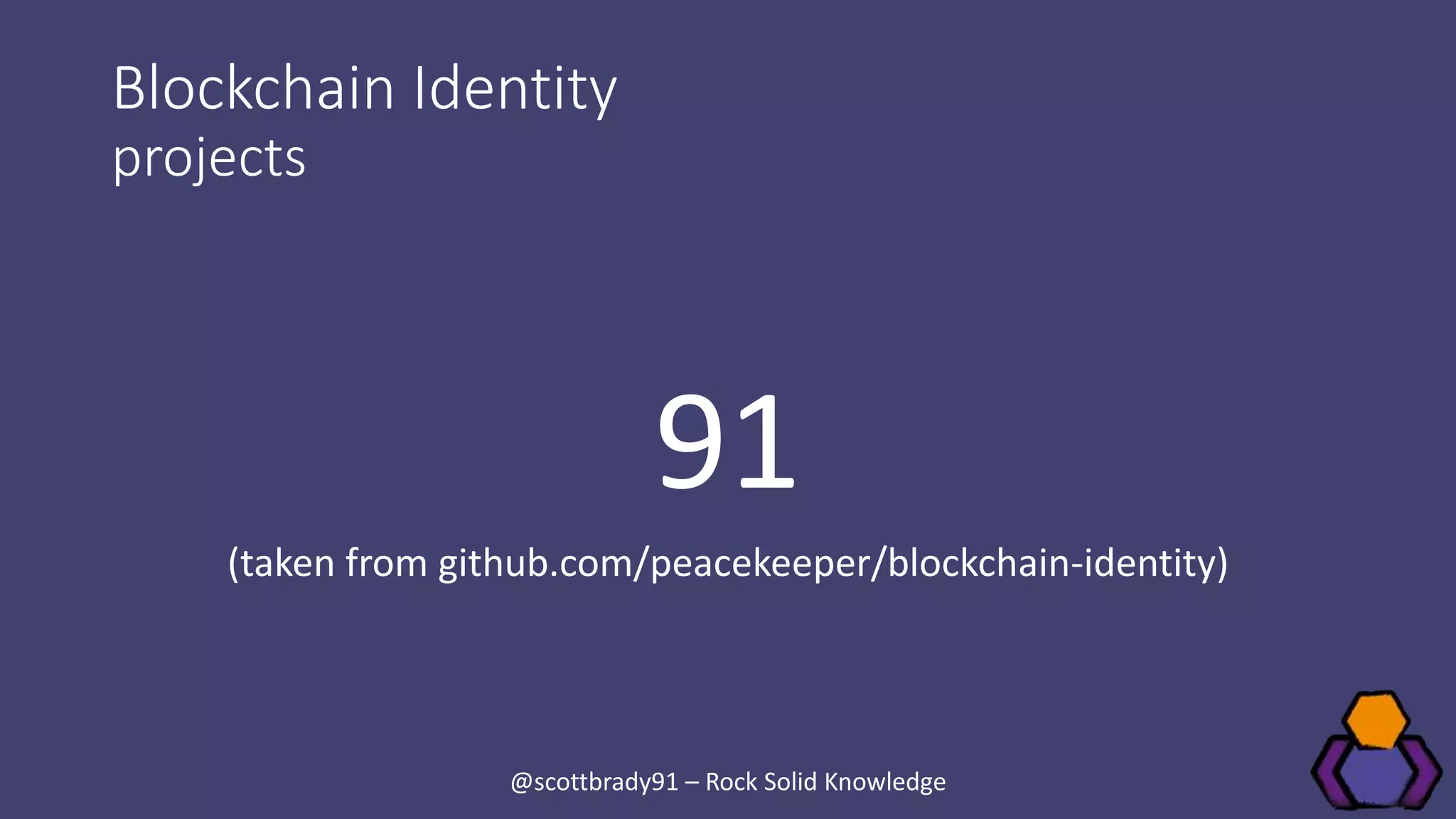
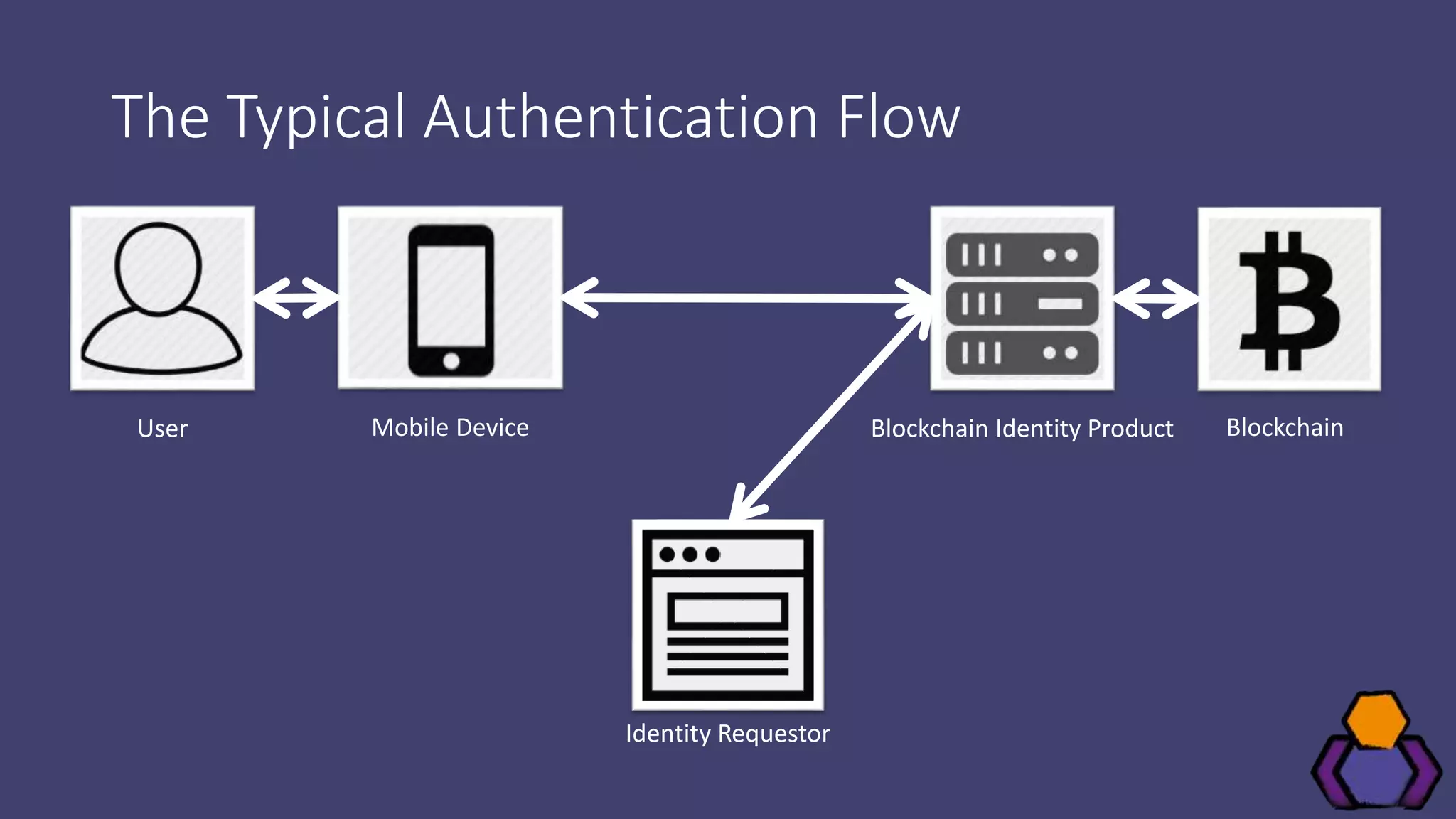
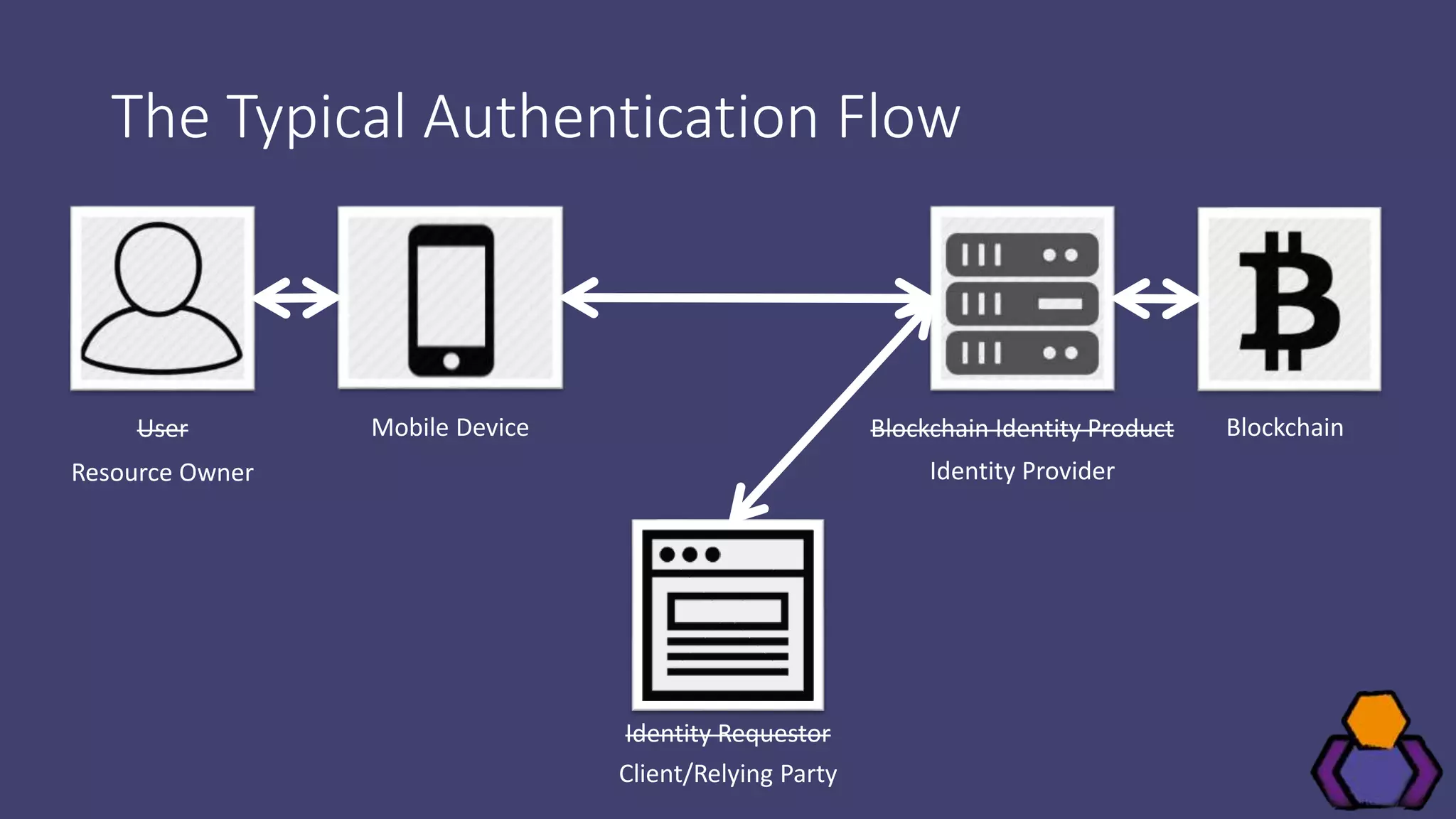
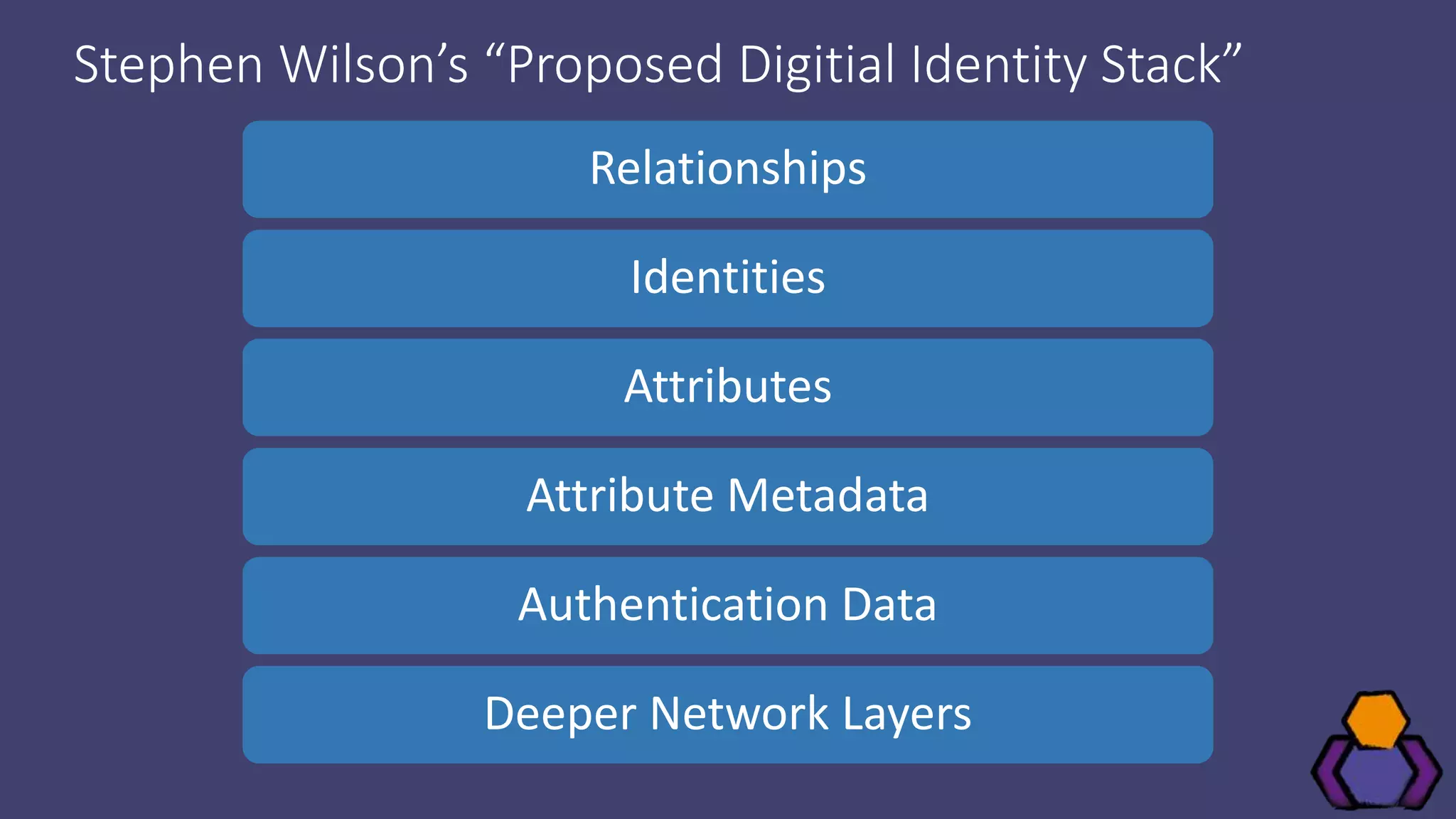
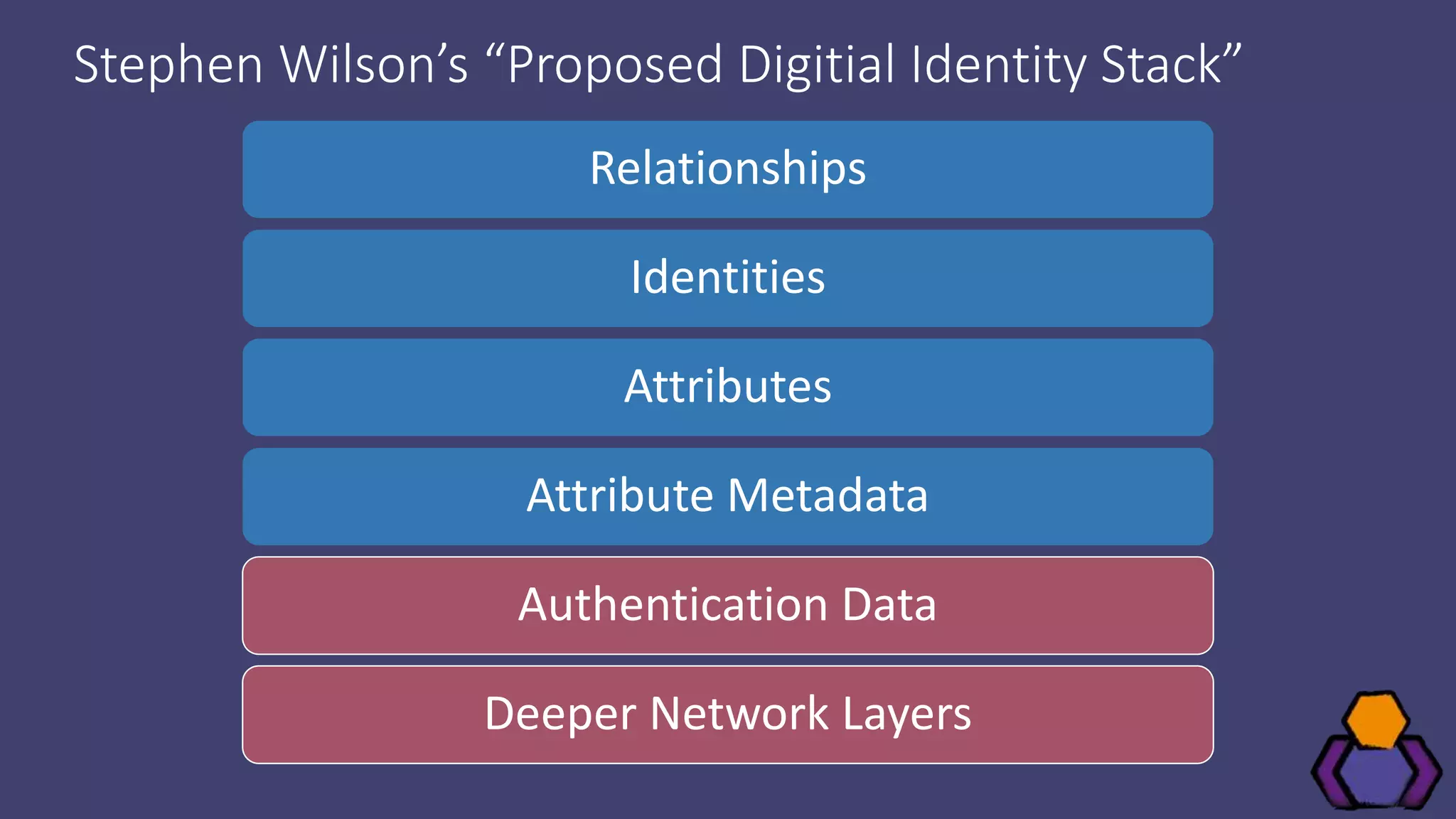
Scott Brady discusses the challenges and lessons learned from integrating with blockchain identity providers, focusing on the initial research and findings from available identity projects. He highlights issues such as inadequate documentation, integration difficulties, and the lack of standard practices in the blockchain identity field. Despite these challenges, he remains optimistic about the future due to the emergence of open standards and collaborative working groups.