How to Secure Your Mobile Commerce App.pdf
- 1. How to Secure Your Mobile Commerce App? M-commerce development services are growing very rapidly in the market as more and more users are using their mobile and tablets for online transactions. Mobile commerce applications are now processing a lot more data than ever which includes sensitive information about users and their transactions. Before going deep into this, Let’s first understand : What is mobile commerce? M-commerce (mobile commerce) is the buying and selling of goods and services through wireless handheld devices such as smartphones and tablets. Basically, transactions that happen online via a mobile or tablet are known as mobile commerce. Mobile commerce is a form of e-commerce and thus it enables users to access online shopping platforms without using a desktop computer. Some of the examples of m-commerce include mobile banking, in-app purchasing, virtual marketplace apps
- 2. like the Amazon mobile app or a digital wallet such as Apple Pay, Android Pay and Samsung Pay. Why does Mobile commerce require more security these days? Because of the increasing volume of transitions through mobile devices, it has become a necessity for businesses to step up and provide security. Businesses must ensure security of sensitive data of people’s transactions in order to win the trust of customers and build a good reputation. Providing security is even more important to sectors that deal with a lot of such data with healthcare and financial services. And because these transactions are done through smartphones using the internet, m-commerce is required to create more security for their users than traditional e-commerce has to. If you are looking for a customized mobile application development company connect with Ozonesoft Solutions. Why is mobile commerce security crucial for your business? Securing m-commerce is crucial to businesses for such reasons : ● As businesses provide mobile transactions, they must secure their m-commerce application. They are responsible for securing themselves against chargebacks and they must ensure safety of the data for both the business and customers. ● Lack of security or breach in security can cause their users to abandon their application or it might even drop their revenue stream. ● Security problems can cause trust issues towards your application or even towards your brand.
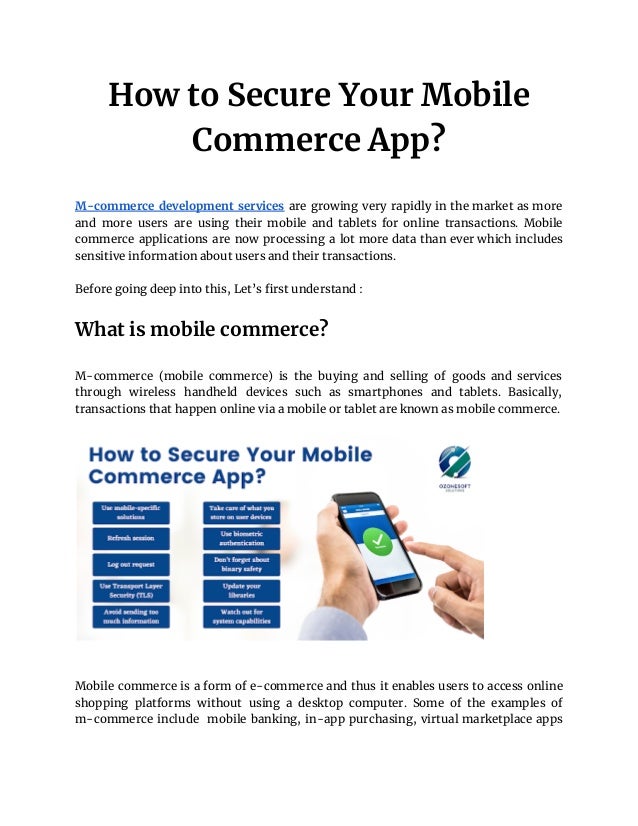
- 3. No business can guarantee a 100% data security for transactions. But that does not mean your data can be breached or exposed easily. Businesses need to make sure that their security measures can slow down the attackers for long enough that their app becomes an unattractive target. Ways to secure your mobile commerce app Mobile commerce developers are constantly dealing with cyber-attacks and harmful viruses, thus security is a top priority. Hackers are always attempting to gain access to your mobile commerce app through security flaws and cause you harm. So, here are ways to secure your mobile commerce app : Backend communication security tips ● Use mobile-specific solutions : Trusting users is much easier when they create an account with phone verification. Moreover, for mobile apps, using phone verification is much more convenient than using email, which needs launching another app/web browser. ● Refresh session : Shorten the life of access tokens to several minutes, it will still keep the app user-friendly by introducing refresh tokens. These tokens can be used to obtain a new token. If the attacker tries to acquire a token, it will be useless after some minutes. ● Log out request : Tokens that are no longer in use should be signaled invalidate, stating that the session is closed. ● Use Transport Layer Security (TLS) : TLS creates an end-to-end encryption, which ensures that nobody reads our messages even if messages are sent through an unencrypted channel (for example, a WiFi access point without a password). ● Avoid sending too much information : Stop sending unnecessary data or splitting them to many requests, this way it will become harder for the
- 4. attacker to obtain the personal data. Even if an attacker intercepts a single request, the information obtained by them may not be sufficient to do harm. Mobile app security tips ● Take care of what you store on user devices : There are chances that unencrypted data on a mobile device can be stolen. Encrypt every sensitive information that you need to store. Nowadays, phones provide secure storage for sensitive data, so we should also remove unnecessary and temporary files as soon as possible. ● Use biometric authentication : Biometric authentication is now supported by almost all devices. It can be used as a convenient means of access or an additional layer of security for sensitive data. ● Don’t forget about binary safety : Compilers can also protect the app from data interception attempts from the produced source code. This makes it impossible for attackers to fake attacks or learn about the app's security weaknesses. ● Update your libraries : Mobile systems and libraries receive updates regularly, so the app should stay up to date as well. Attacks can be prevented, if people update libraries to the newest versions. Attackers can easily exploit a bug that has been announced to the public at least a few months prior. ● Watch out for system capabilities : Capabilities such as clipboards can store data across all applications. There exist some apps or websites that can steal data from clipboards or place their tracking data there. See if the app should share data with other apps, don't permit third party apps to open an unsupported file for preview. Conclusion
- 5. As mentioned above, strengthen your mobile app development process and include the essential security measures. It will assist you in protecting both your audience and your company from potential risks. If you are looking for someone who can build a mobile commerce app for you with all the security, contact Ozonesoft Solutions. We are the pioneers in mobile app development with expertise in Android app development and iPhone app development. Our еxtеnѕіvе experience in the mobile world enables uѕ to develop and deliver breakthrough mоbіlе solutions in vаrіоuѕ vеrtісаlѕ including Entеrрrіѕе, Navigation, Hеаlth Cаrе, Wearable Technology, Augmented Rеаlіtу, E-commerce, News, Utility, Events and Organizers, and Education еtс. We Redefine your Business or Startup Goals with Advanced Website & Mobile App Development Solutions Powered by Robust Architecture and AI-based Algorithms. So if you are looking for mobile app development services contact Ozonesoft Solutions. Source : https://bit.ly/3Mdxs1S
