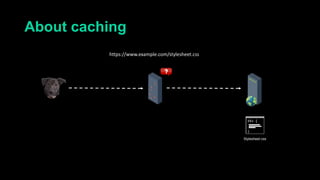
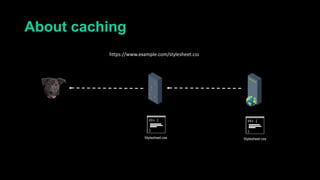
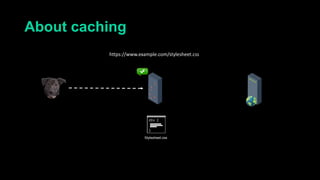
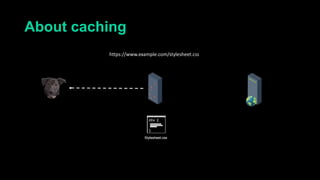
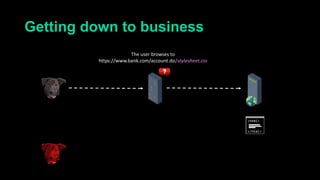
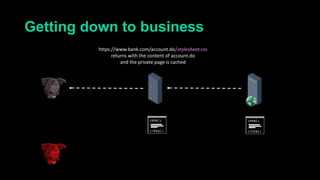
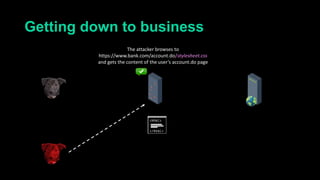
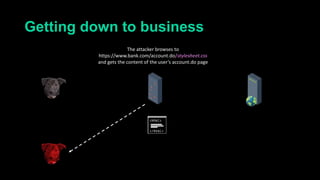
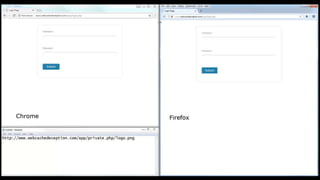
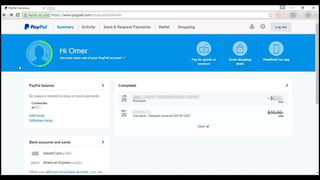
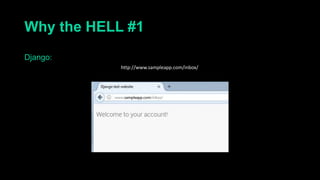
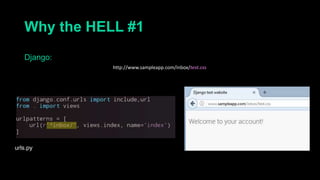
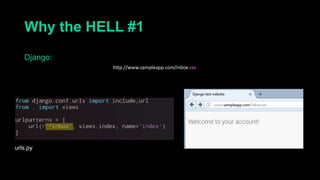
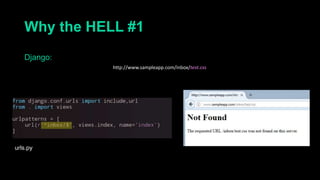
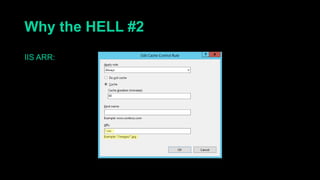
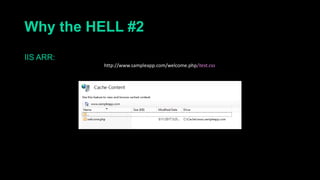
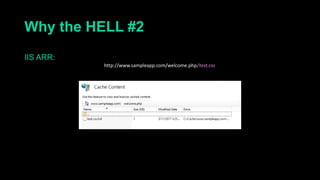
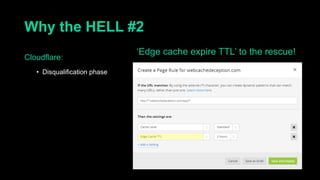
This document describes a web cache deception attack where an attacker can exploit how web servers and caching mechanisms handle requests for non-existent files. Specifically, if a request is made for a page plus a non-existent file extension, like http://www.example.com/account.php/stylesheet.css, some systems will return the content of the page rather than a 404. This allows an authenticated user's private page to be cached and then accessed by an attacker. The document provides examples of frameworks like Django and servers like IIS that can be exploited this way. It also discusses how caching services like Cloudflare have addressed this issue. Mitigations are proposed like only caching files if headers allow it and returning 302/404