Risk management overview
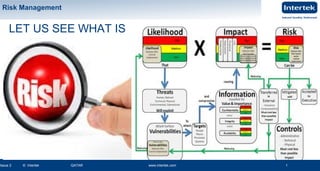
- 1. www.intertek.com1Issue 2 © Intertek QATAR www.intertek.com 1 Risk Management www.intertek.com1 Risk Management Issue 2 © Intertek QATAR www.intertek.com 1 LET US SEE WHAT IS
- 2. www.intertek.com2Issue 2 © Intertek QATAR www.intertek.com 2 Risk Management www.intertek.com2 Risk Management Issue 2 © Intertek QATAR www.intertek.com 2 Information Security RisksInformation Security Risks CONFIDENTIALITY Risks INTEGRITY Risks AVAILABILITY Risks Business Continuity RisksBusiness Continuity Risks Health & Safety Risks Product Risks Process Risks Information Security Risks Environmental Risks Process Risks Financial Risks Food Safety Risks Logistic Risks Accounting Risks Capacity Risks Competency Risks Etc. STOCKMARKET INSURANCE CATOSTROPHIES PRODUCT PROCESSES HUMAN DEPENDANCY LOGISTICS LEGAL INDUSTRY STANDARDS & ACCEPTANCE CRITERIA PRINCIPLES/ VISION/ POLICIES / STRATEFIES IT COMPETITORS NEIGHBOURS PRESSURE GROUPS TRANSPARANCY CULTURE COMPETENCY EXTERNALFACTORS INTERNALFACTORS
- 3. www.intertek.com3Issue 2 © Intertek QATAR www.intertek.com 3 Risk Management www.intertek.com3 Risk Management Issue 2 © Intertek QATAR www.intertek.com 3
- 4. www.intertek.com4Issue 2 © Intertek QATAR www.intertek.com 4 Risk Management www.intertek.com4 Risk Management Issue 2 © Intertek QATAR www.intertek.com 4 A Tyre company designs a tyre which has following features, based on market research to capture the market (market share from 40% TO 75%) : Long Lasting – 2 million miles Any Terrain - Desert & Rocky 100% Air Tight Result in one year captures the market (market share increased from 40% To 85% - more than targetted) BUTBUT New sales went downNew sales went down as there was no needas there was no need for customers to investfor customers to invest in new tyresin new tyres So both Risks (+ve & -ve ) be identified in Risk Assessment Positive Risks (Opportunities)
- 5. www.intertek.com5Issue 2 © Intertek QATAR www.intertek.com 5 Risk Management www.intertek.com5Issue 2 © Intertek QATAR www.intertek.com 5 RISK MANAGEMENT LIFE CYCLE
- 6. www.intertek.com6Issue 2 © Intertek QATAR www.intertek.com 6 Risk Management www.intertek.com6Issue 2 © Intertek QATAR www.intertek.com 6 6
- 7. www.intertek.com7Issue 2 © Intertek QATAR www.intertek.com 7 Risk Management www.intertek.com7Issue 2 © Intertek QATAR www.intertek.com 7 Risk Governance
- 8. www.intertek.com8Issue 2 © Intertek QATAR www.intertek.com 8 Risk Management www.intertek.com8Issue 2 © Intertek QATAR www.intertek.com 8 > RISK BASED THINING (RISK MANAGEMENT) & CORRECTIVE ACTIONS REQUIRE BIGGER VISION Importance of Vision
- 9. www.intertek.com9Issue 2 © Intertek QATAR www.intertek.com 9 Risk Management www.intertek.com9Issue 2 © Intertek QATAR www.intertek.com 9 ENTERPRISE RISK MANAGEMENT
- 10. www.intertek.com10Issue 2 © Intertek QATAR www.intertek.com 10 Risk Management www.intertek.com10Issue 1 © Intertek QATAR www.intertek.com Information Security OverviewInformation Security Overview Scenario 1 Occurrence CHANGESOccurrence CHANGES but Impact is SAMEImpact is SAME Scenario 2 Impact CHANGESImpact CHANGES but Occurrence isOccurrence is SAMESAME THERE ARE TWO SCENARIOS OF RISK Scenarios of Risk
- 11. www.intertek.com11Issue 2 © Intertek QATAR www.intertek.com 11 Risk Management www.intertek.com11Issue 1 © Intertek QATAR www.intertek.com Information Security OverviewInformation Security Overview 11 Probability of falling is LOW Probability of falling is HIGH Risk of Failure = Probability of Occurrence X Severity of the ImpactRisk of Failure = Probability of Occurrence X Severity of the Impact Scenario 1 = Probability of Occurrence CHANGES but Impact is SAME
- 12. www.intertek.com12Issue 2 © Intertek QATAR www.intertek.com 12 Risk Management www.intertek.com12Issue 1 © Intertek QATAR www.intertek.com Information Security OverviewInformation Security Overview Impact is LESS if speed is LESS @ 10k/ hr Impact is HIGH if speed is HIGH @ 150 km / hr Scenario 2 = Impact CHANGES but Probability of Occurrence is SAME Risk of Failure = Probability of Occurrence X Severity of the ImpactRisk of Failure = Probability of Occurrence X Severity of the Impact
- 13. www.intertek.com13Issue 2 © Intertek QATAR www.intertek.com 13 Risk Management 13 0.3 Selecting controls Controls can be selected from this standard or from other control sets, or new controls can be designed to meet specific needs as appropriate. The selection of controls is dependent upon organizational decisions based on the criteria for risk acceptance, risk treatment options and the general risk management approach applied to the organization, and should also be subject to all relevant national and international legislation and regulations. Control selection also depends on the manner in which controls interact to provide defence in depth. Some of the controls in this standard can be considered as guiding principles for information security management and applicable for most organizations. The controls are explained in more detail below along with implementation guidance. More information about selecting controls and other risk treatment options can be found in ISO/IEC 27005.[11] RISK MITIGATION IN INFORMATION SECURITY
- 14. www.intertek.com14Issue 2 © Intertek QATAR www.intertek.com 14 Risk Management www.intertek.com14Issue 2 © Intertek QATAR www.intertek.com 14 Logical Flow of Risk Assessment in ISMS 1. Identification of Vulnerability for Information Risk of C, I & A 2. Identification of Existing Controls (if any already there) for Information Risk of C, I & A 3. Performing the Risk Evaluation to understand the level of existing risk ( Example > High / Medium / Low) - of C, I & A 4. Deciding if this is acceptable or requires further treatment to reduce the risk of C, I & A 5. Deciding treatment from Annexure A Controls / Newly designed Control to reduce the risk of C, I & A 6. Analysing the Controls effective and Approving Residual Risks of C, I & A So we do Risk Evaluation twice - one after existing controls and one after new controls to understand the level of risk reduction of C, I & A
- 15. www.intertek.com15Issue 2 © Intertek QATAR www.intertek.com 15 Risk Management www.intertek.com15 Risk Management Issue 2 © Intertek QATAR www.intertek.com 15 RISK MITIGATION IN BCMS
- 16. www.intertek.com16Issue 2 © Intertek QATAR www.intertek.com 16 Risk Management www.intertek.com16 Risk Management Issue 2 © Intertek QATAR www.intertek.com 16 Logical Flow of Risk Assessment in BCMS 1. Identification of Vulnerability for Information Risk of C, I & A 2. Identification of Existing Controls (if any already there) for BC Plans 3. Performing the Risk Evaluation to understand the level of existing risk ( Example > High / Medium / Low) - of BC 4. Deciding if this is acceptable or requires further treatment to reduce the risk of BC 5. Deciding treatment from Annexure A Controls / Newly designed Control to reduce the risk of BC 6. Analysing the Controls effective and Approving Residual Risks of BC So we do Risk Evaluation twice - one after existing controls and one after new controls to understand the level of risk reduction in BCMS
- 17. www.intertek.com17Issue 2 © Intertek QATAR www.intertek.com 17 Risk Management www.intertek.com17Issue 2 © Intertek QATAR www.intertek.com 17 RISKLEVEL HIGH / 71 - 100 Medium / 41 - 70 Low / 1 - 40 RISK MITIGATION ( Risk Reduction ) Risk Mitigation – Implemeting Controls for Risk Reduction No matter which ever controls implemented, following are the facts: 1. Shall definitely bring down the risk of C, I & A – till the time control is effective; 2. What ever control – risk cannot be brought to ZERO – can only reduce the risk; 3. In IT, controls can reduce the “PROBABILITY” only; 4. Residual risks shall always be there – one must remember 24x7; NO CONTROL CAN BRING ANY RISK TO ZERO LEVEL SHALL ALWAYS HAVE RESIDUAL RISK
- 18. www.intertek.com18Issue 2 © Intertek QATAR www.intertek.com 18 Risk Management www.intertek.com18Issue 2 © Intertek QATAR www.intertek.com 18 Risk Evaluation Methodologies (samples only)
- 19. www.intertek.com19Issue 2 © Intertek QATAR www.intertek.com 19 Risk Management www.intertek.com19Issue 2 © Intertek QATAR www.intertek.com 19 19 STEP 1 = Identifying the Potential Causes + % of Impact on business + Current Risk Level (considering existing controls) IDENTIFICATION OF THREATS AND VULNERABILITIES FOR RISKS CONSIDER THE EXISTING CONTROS AS CURRENT BASELINE ISMS RISK ASSESSMENT RISK EVALUATION 1 – IMPACTS ON CONFIDENTIALITY , INTEGRITY AND AVAILABILITY CURRENT RISK LEVEL
- 20. www.intertek.com20Issue 2 © Intertek QATAR www.intertek.com 20 Risk Management www.intertek.com20Issue 2 © Intertek QATAR www.intertek.com 20 20 NEW CONTROLS – RISK MITIGATION PLANS OVERALL RESIDUAL RISKS Stage 2 = Plan the actions / controls to reduce the risks and calculate RPN again to demonstrate reduction of the identified risks and also record the residual risks. ISMS RISK ASSESSMENT MEW RISK LEVEL NEW BASELINE RESIDUAL RISKS OF CONFIDENTIALITY, INTEGRITY & AVAILABILITY
- 21. www.intertek.com21Issue 2 © Intertek QATAR www.intertek.com 21 Risk Management www.intertek.com21Issue 2 © Intertek QATAR www.intertek.com 21 STATEMENT OF APPLICABILITY [ SOA ] SOA IS A STATEMENT CONTAINING The list of controls used in the Risk Assessment – with JUSTIFICATIONS for INCLUSIONS The list of controls not used in the Risk Assessment – with JUSTIFICATIONS for NON-INCLUSIONS BEST PRACTICE 1. The SOA and RA have to be considered as Synchronized Cis (CI = Configuration Item) Synchronized CI = VERSION OF SOA AND RA BE SAME > EVERY CHANGE ONCE DONE IN RA , SOA BE REVIEWED AND VERSION OF SOA BE UPGRADED = SAME AS THAT OF RA
- 22. www.intertek.com22Issue 2 © Intertek QATAR www.intertek.com 22 Risk Management www.intertek.com22Issue 2 © Intertek QATAR www.intertek.com 22 Applicab le Cross reference/ YES / NO In Risk Assessment A.6.2.1 Mobile device policy YES To ensure that confidential information is not carried outside through laptop computers & cellphones Risk Number 43 A.12.1.4 Separation of development, testing environments NO Document Bank is involved only in operational activities such as scanning and storage etc. Not Applicable Control Number Control Objectives/ Controls Justification SAMPLE
- 23. www.intertek.com23Issue 2 © Intertek QATAR www.intertek.com 23 Risk Management NEW CONTROLS – RISK MITIGATION PLANS FROM RISK ASSESSMENT BUSINESS CONTINUITY PLANS
- 24. www.intertek.com24Issue 2 © Intertek QATAR www.intertek.com 24 Risk Management www.intertek.com24Issue 2 © Intertek QATAR www.intertek.com 24 IncidentIncident
- 25. www.intertek.com25Issue 2 © Intertek QATAR www.intertek.com 25 Risk Management www.intertek.com25Issue 2 © Intertek QATAR www.intertek.com 25 Whowasinvolved? Whohastobeinformedabouttheincident? Whowillinform? Where Impacted? WasitaProductDesignFault/ProcessFailure? When? WhendidtheIncidentoccur? Who? STEP 1 > RECORD THE INCIDENT INCIDENT MANAGEMENT – RISK VALIDATION & CORRECTIVE ACTIONS STEP 2 > IDENTIFY THE CAUSES OF THE INCIDENT
- 26. www.intertek.com26Issue 2 © Intertek QATAR www.intertek.com 26 Risk Management www.intertek.com26Issue 2 © Intertek QATAR www.intertek.com 2626 Incident > Product Withdrawal and Product Recall Mattel recalls 1.5 million toys: http://www.youtube.com/watch?v=NlsvfXAQ5v8&fea Lead contamination – Toxic levels of Lead pain lawsuit: http://www.youtube.com/watch?v=3DL4dleEz7I
- 27. www.intertek.com27Issue 2 © Intertek QATAR www.intertek.com 27 Risk Management www.intertek.com27Issue 2 © Intertek QATAR www.intertek.com 27 The 2009 Toyota 9 Million Car Recall Toyota Motor Corp. recalled approximately 9 million vehicles in the United States, which was the company’s largest-ever U.S. recall. The purpose of the recall was to address quality assurance and quality control problems with a removable floor mat that could cause accelerators to get stuck and potentially lead to a crash. (Source: Toyota recalls 3.8 million vehicles, MSNBC.com) Incident > Product Withdrawal and Product Recall
- 28. www.intertek.com28Issue 2 © Intertek QATAR www.intertek.com 28 Risk Management www.intertek.com28Issue 2 © Intertek QATAR www.intertek.com 28 PROPOSED CONTROLS IN RISK ASSESSMENT AFTER INCIDENT DOES THIS NEWDOES THIS NEW CONTROL(S)CONTROL(S) GENERATES ANYGENERATES ANY CASCADINGCASCADING IMPACTSIMPACTS YESYES NONO Update Risk Assessment and implement New Controls to Mitigate the Risk of Incident Repetition The BIG Qs. Is AWHAT ARE THE STEPS TO UPDATE THE RISK ASSESSMENT ?
- 29. www.intertek.com29Issue 2 © Intertek QATAR www.intertek.com 29 Risk Management Answer> RISK VALIDATION SYSTEMSYSTEM • Governance; • Strategy; • Policies; • Industry sector specific Statutory & Regulatory Requirement Strategy & Policies Controls (mitigations) Incorporated In the Process Documents & Implemented Incident New controls and / or and / or Existing controls New Threats/ New Vulnerabilities and / or Take away >>> `RISK ASSESSMENT, SOA AND INCIDENTS have to be Synchronized PLAN DO CHECK ACT Risk Validation– Converting VISION RA to FACTUAL RA Residual risks 1st Step to Validate > RESIDUAL RISKS MIGHT HAVE CAUSED THE INCIDENT ?2nd Step to Validate (If 1st is Failure) > WEAK MITIGATIONS / WEAK IMPLEMENTAION MIGHT HAVE CAUSED THE INCIDENT ?3rd Step to Validate (If 1st & 2nd are Failure) > NEW THREAT / VULNERABILITY MIGHT HAVE CAUSED THE INCIDENT KNOWLEDGE BASE RCA Root Cause Analysis KEDB Known Error Data Base CMDB Configuration Management Data Base
- 30. www.intertek.com30Issue 2 © Intertek QATAR www.intertek.com 30 Risk Management www.intertek.com30Issue 2 © Intertek QATAR www.intertek.com 30 COST IMPACT DUE TO PERFECTION / NON-CONFORMANCE
- 31. www.intertek.com31Issue 2 © Intertek QATAR www.intertek.com 31 Risk Management www.intertek.com31Issue 2 © Intertek QATAR www.intertek.com 31 COST IMPACT DUE TO PERFECTION / NON-CONFORMANCE
- 32. www.intertek.com32Issue 2 © Intertek QATAR www.intertek.com 32 Risk Management www.intertek.com32Issue 2 © Intertek QATAR www.intertek.com 32 Thanks for your valuable time !