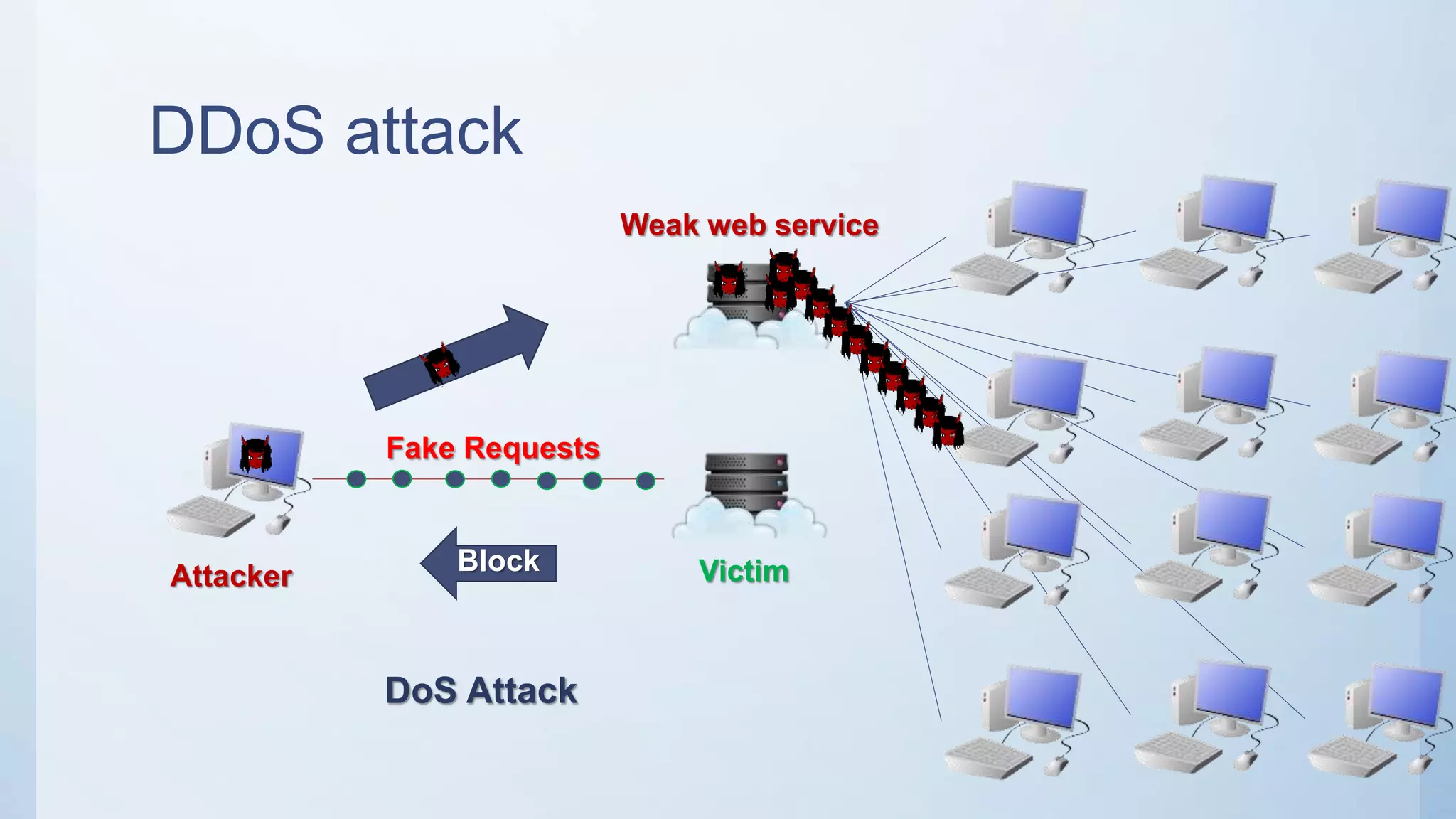
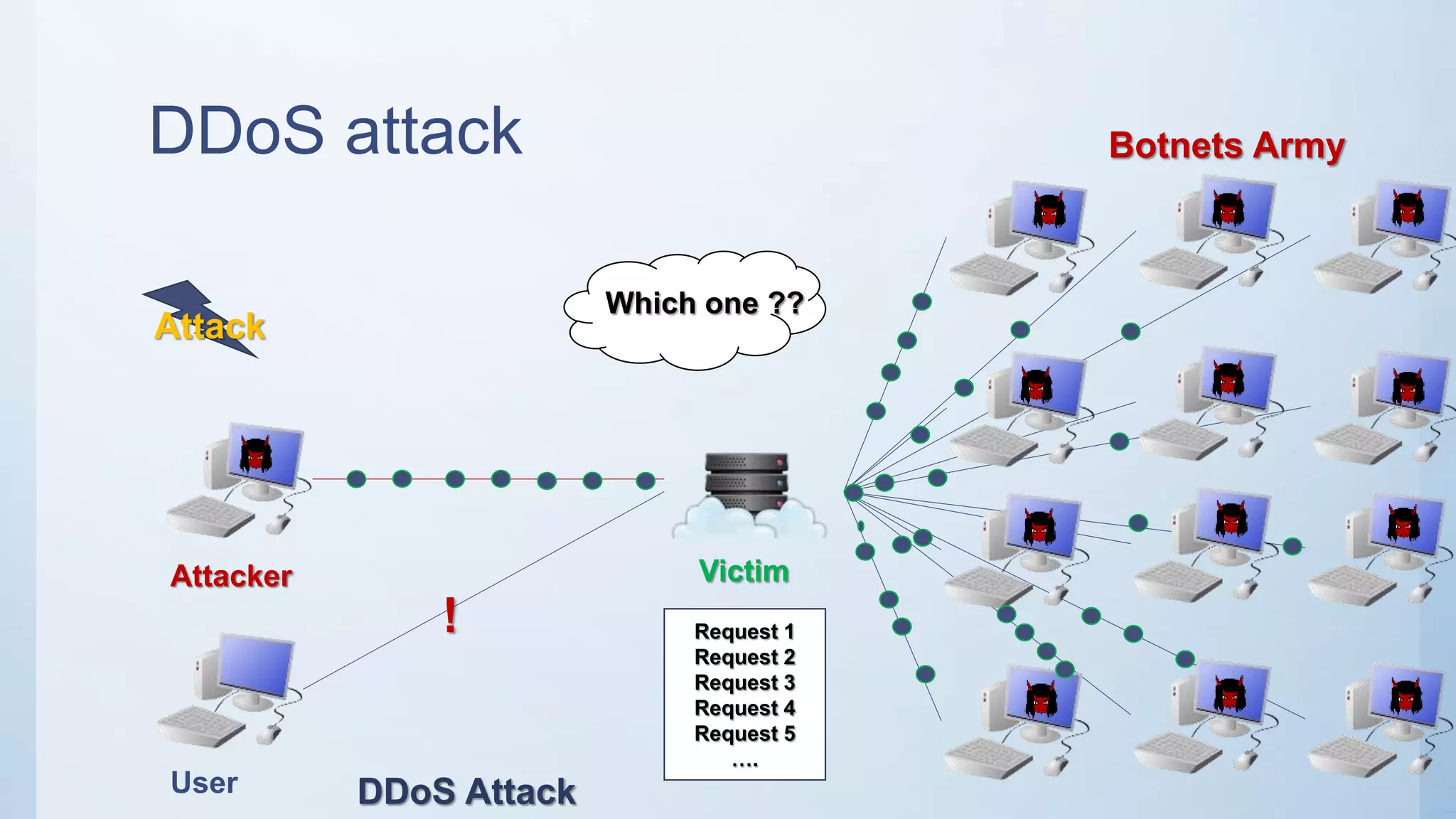
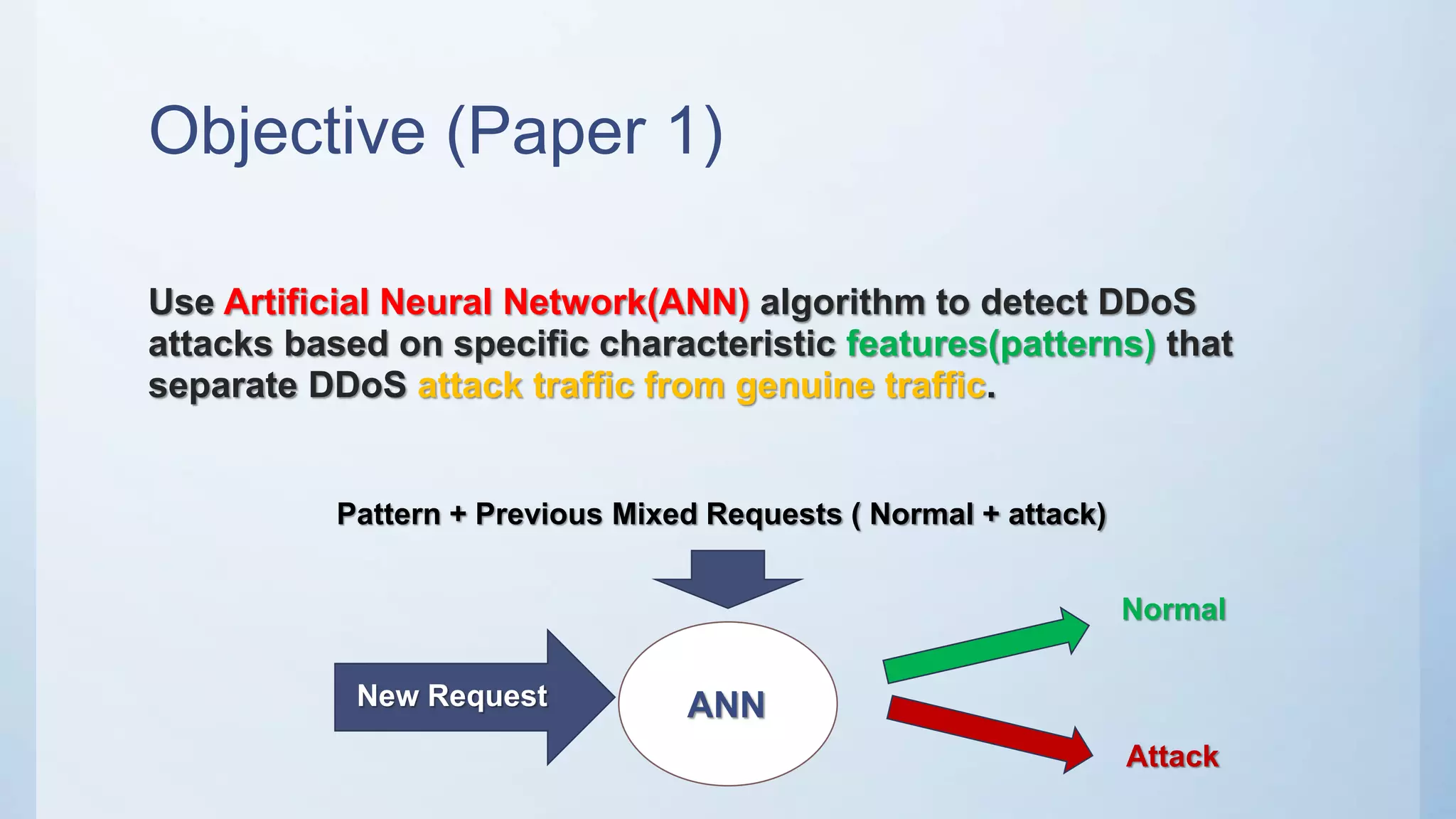
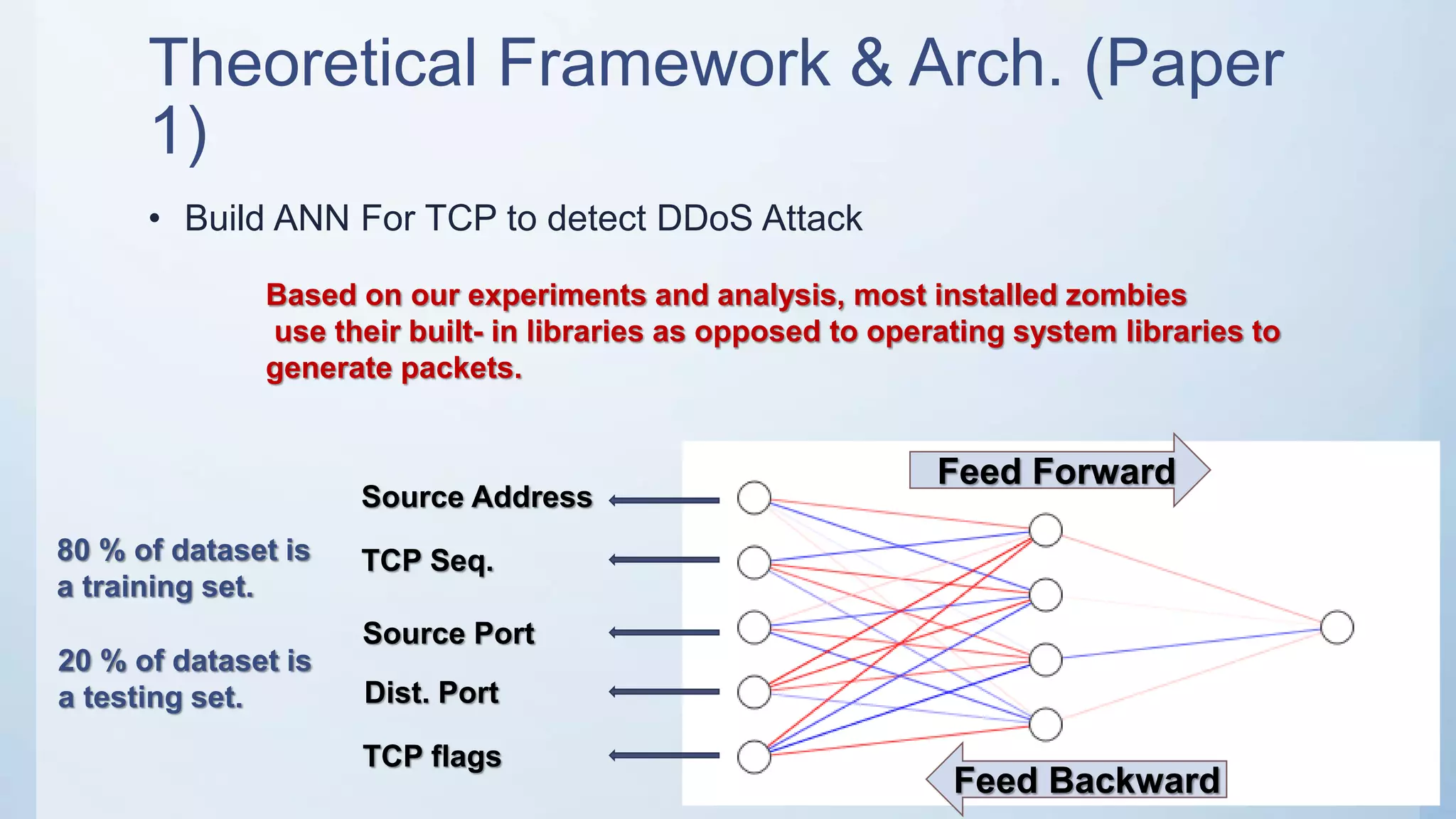
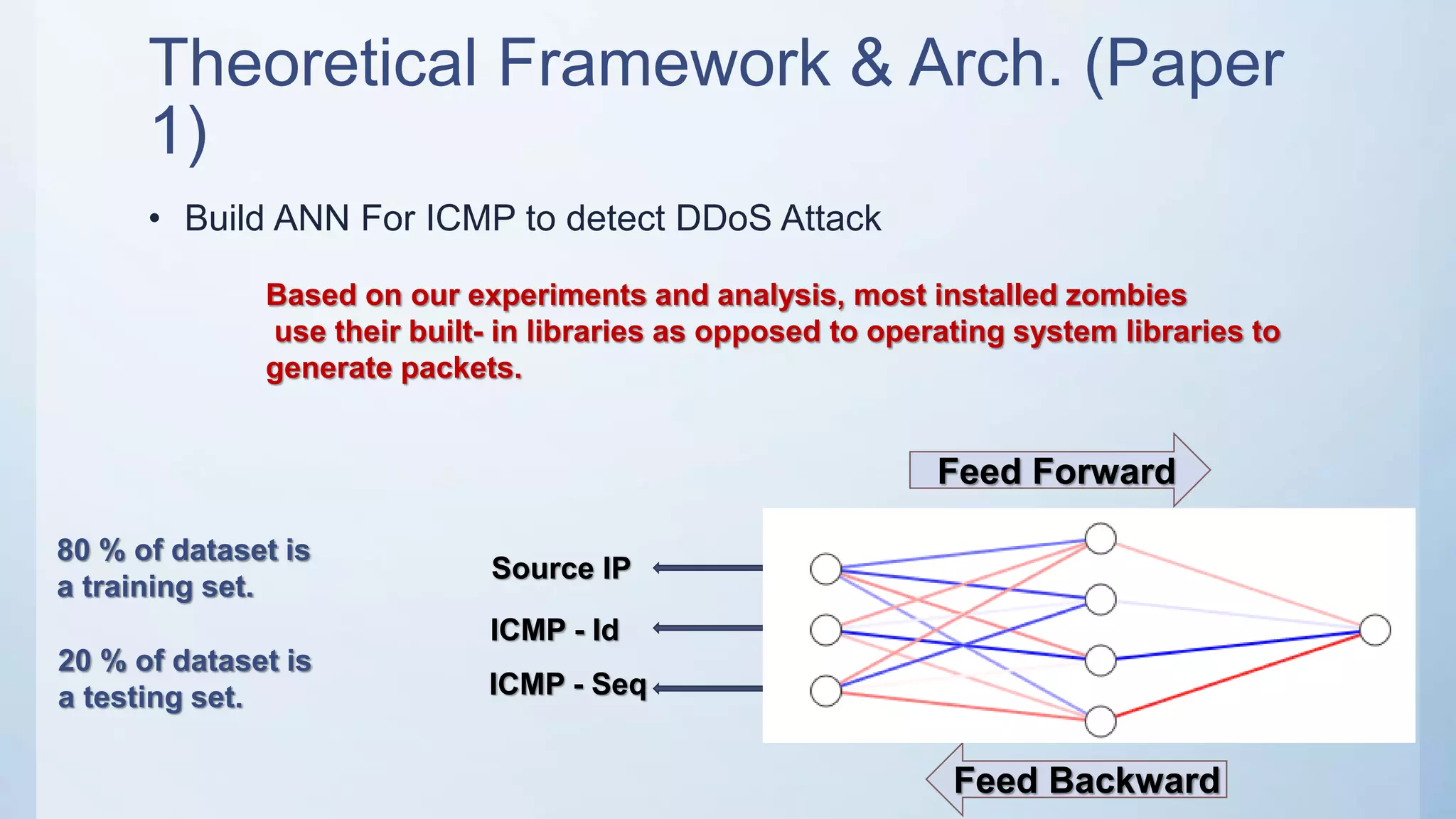
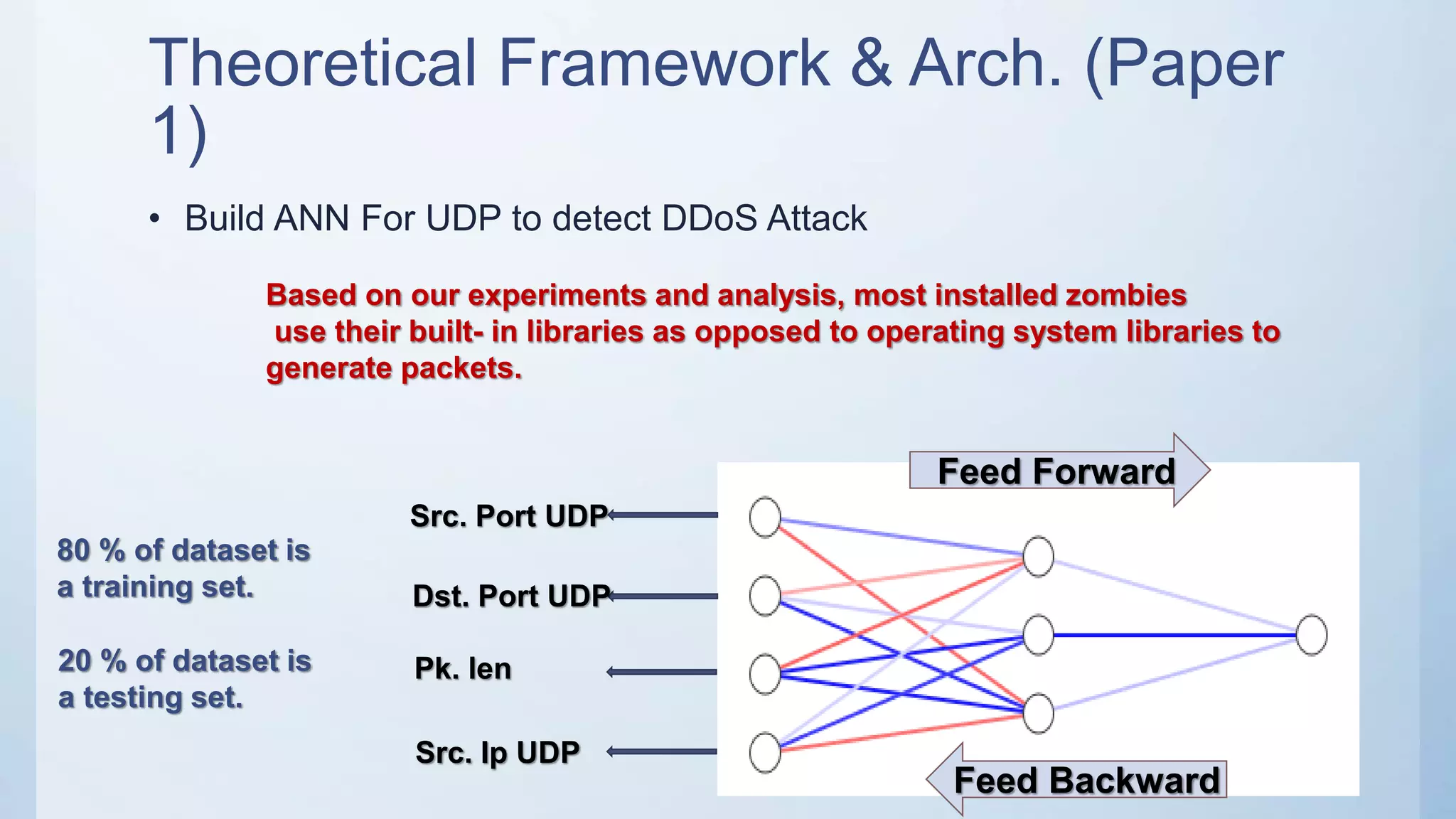
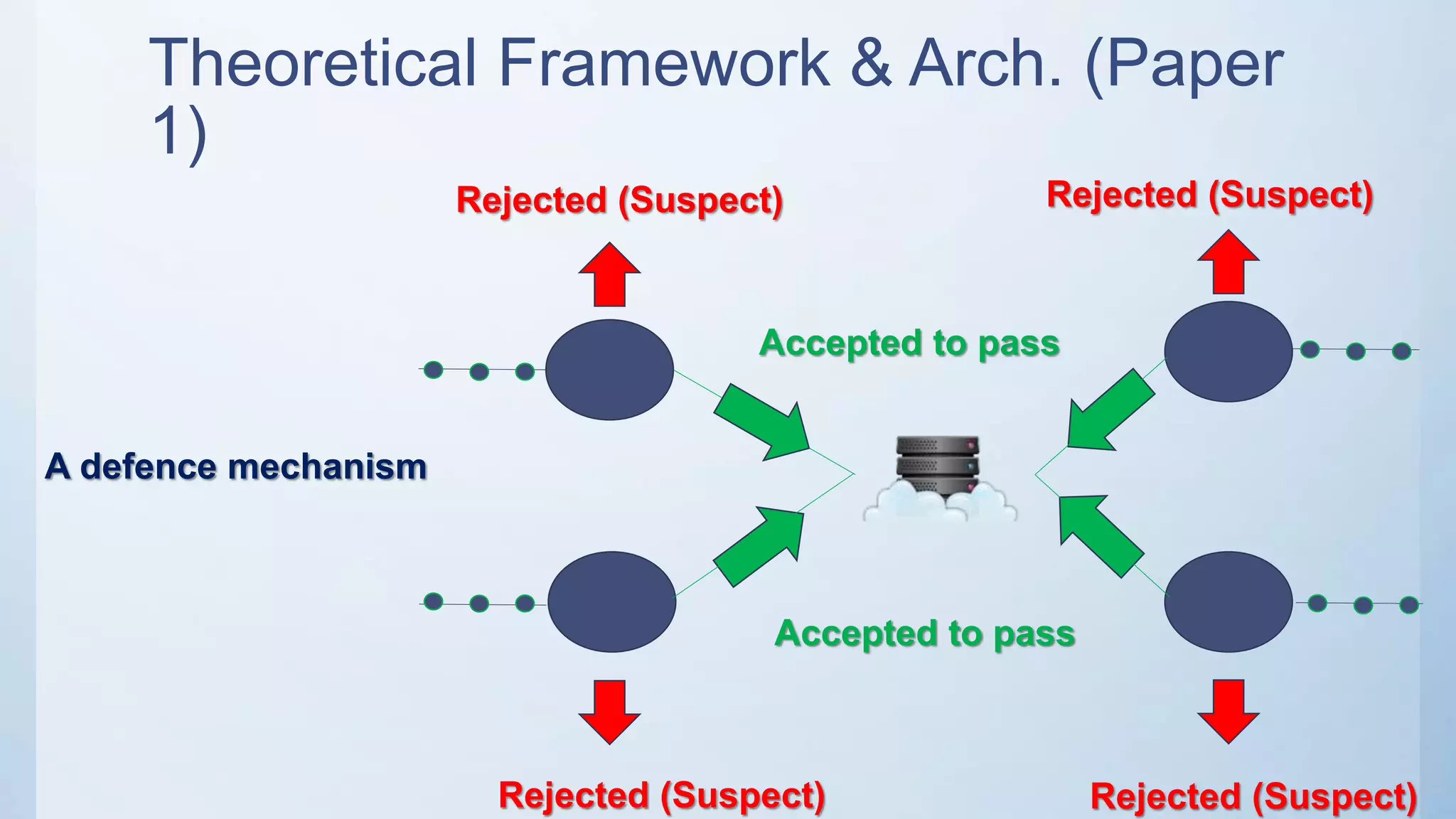
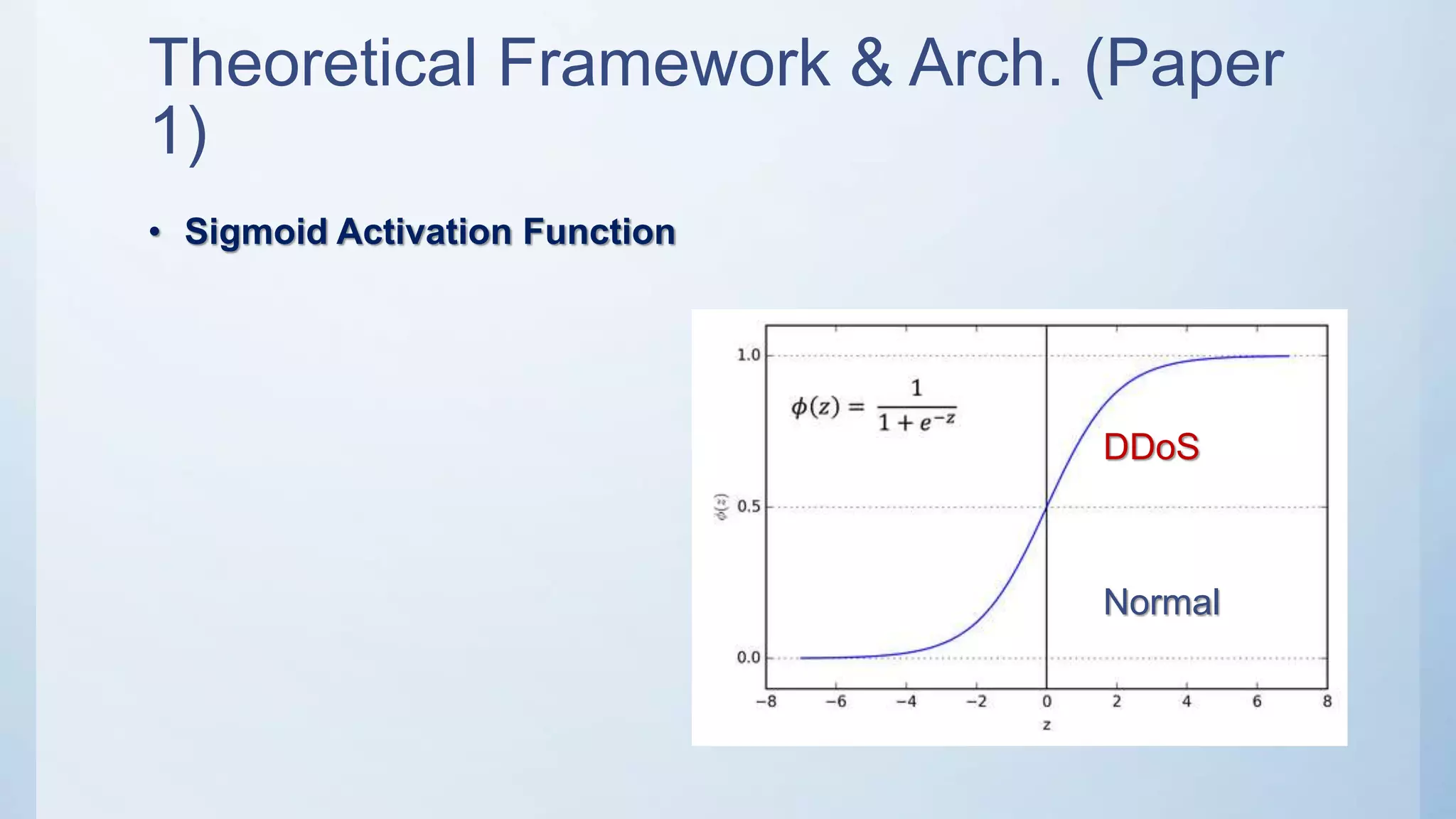
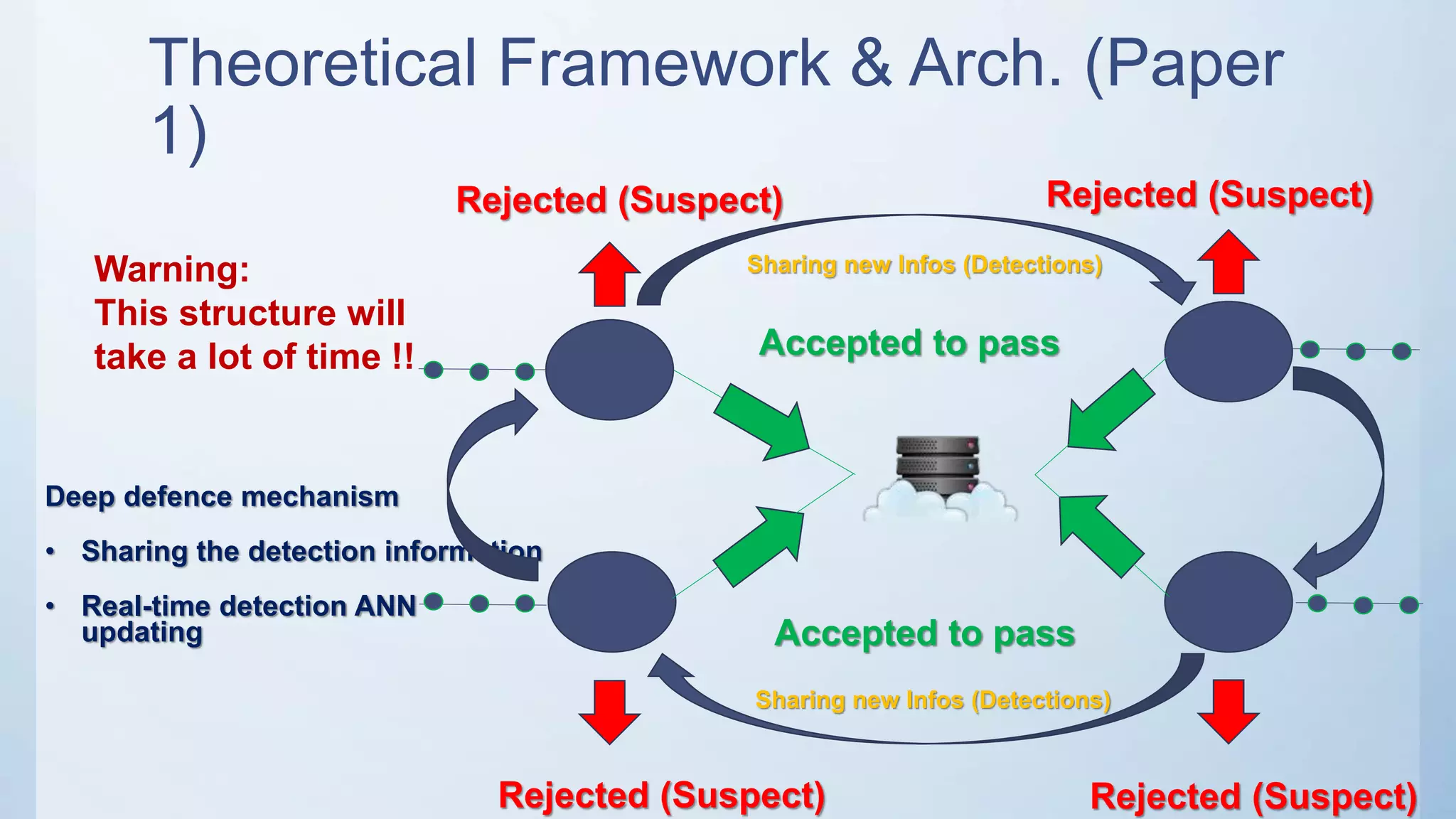
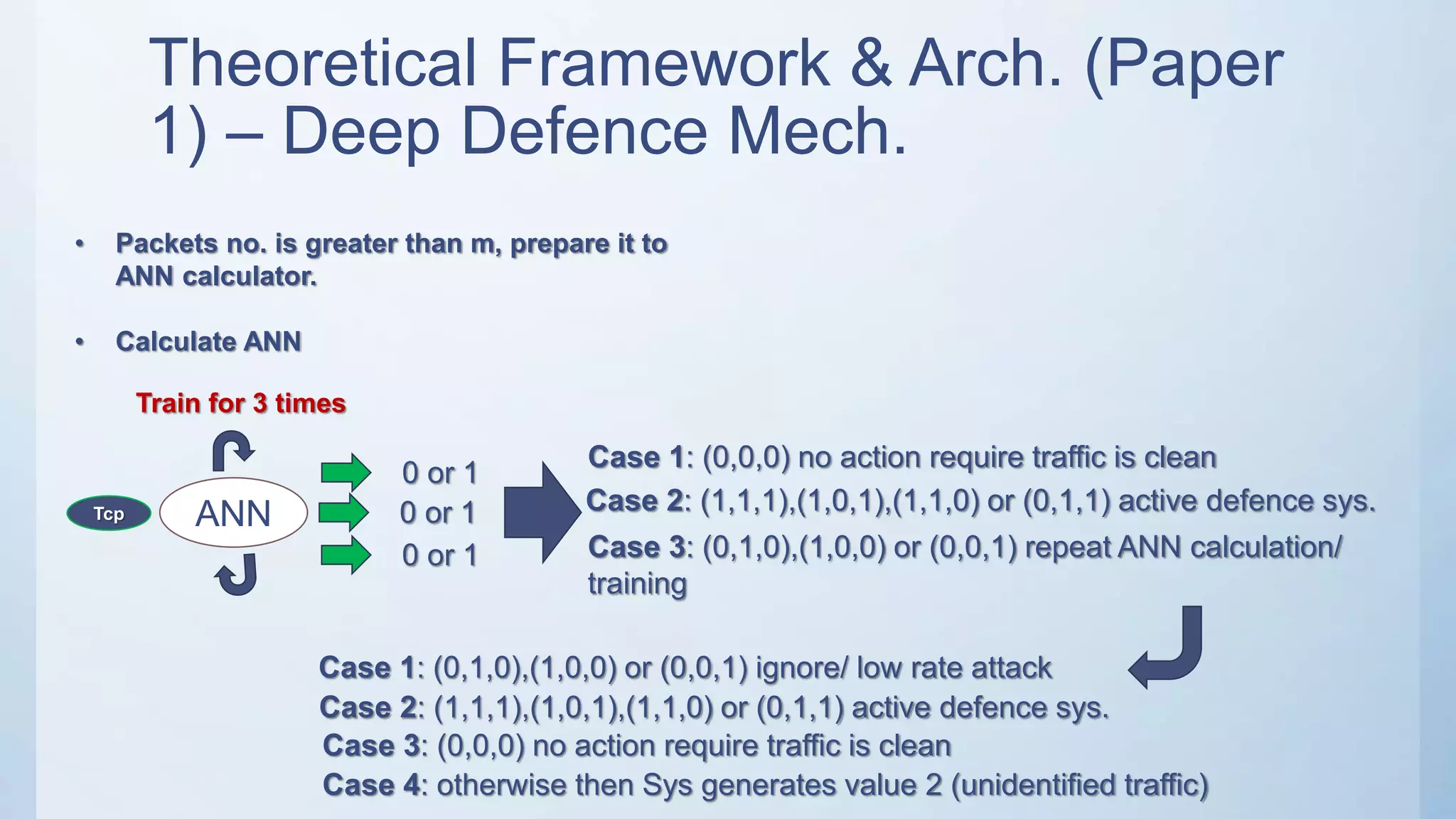
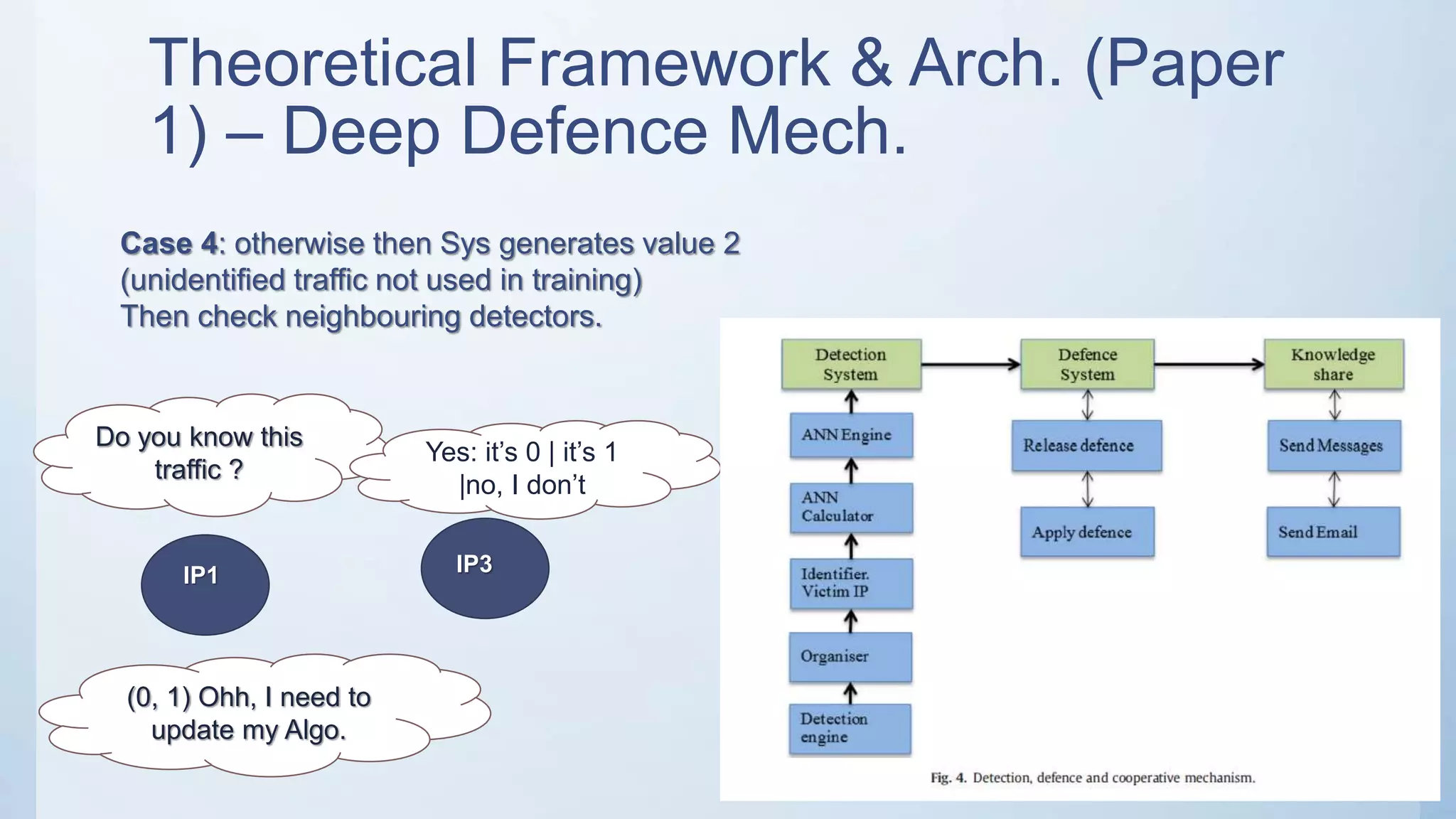
The document discusses using machine learning techniques like artificial neural networks to detect DDoS attacks. Specifically, it proposes building separate ANN models for TCP, ICMP, and UDP to classify requests as normal traffic or attacks based on protocol header attributes. The models would be trained on labeled historical data and tested on a separate dataset. If an incoming request is classified as suspicious by one of the ANN detectors, neighboring detection systems would be queried to share information before taking action. The proposed approach aims to detect both known and unknown DDoS attacks in real-time but has limitations around handling encrypted traffic.