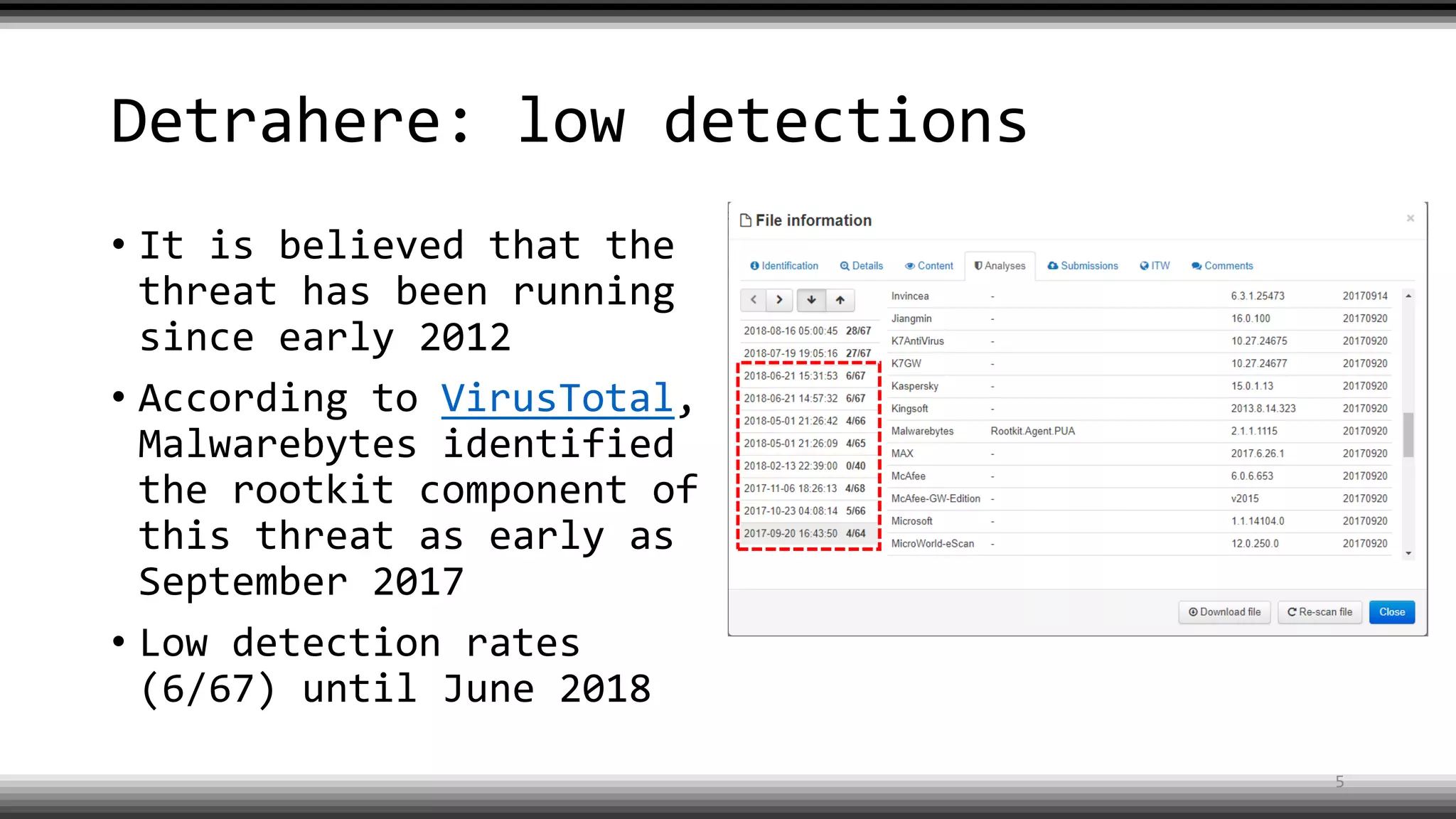
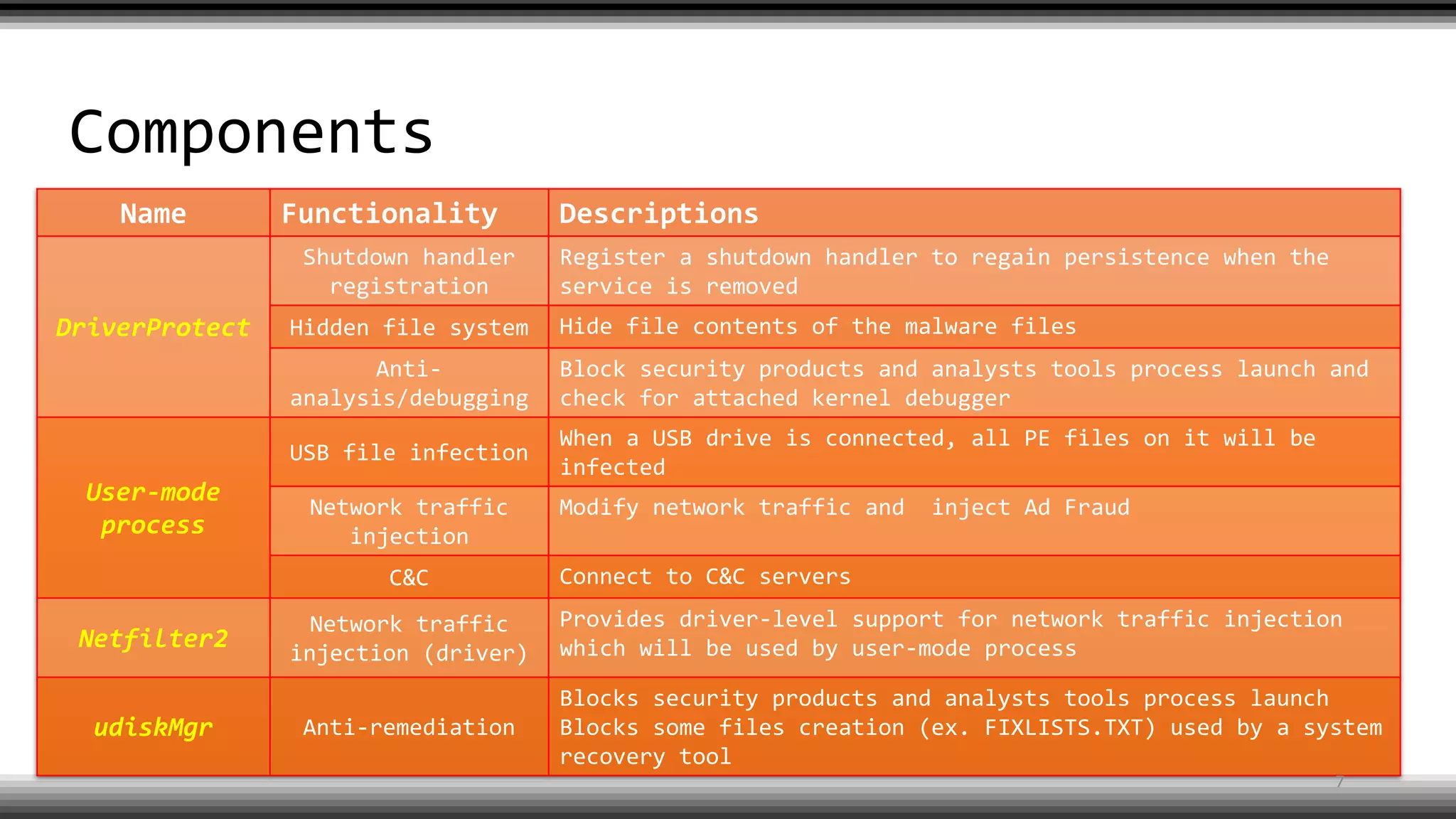
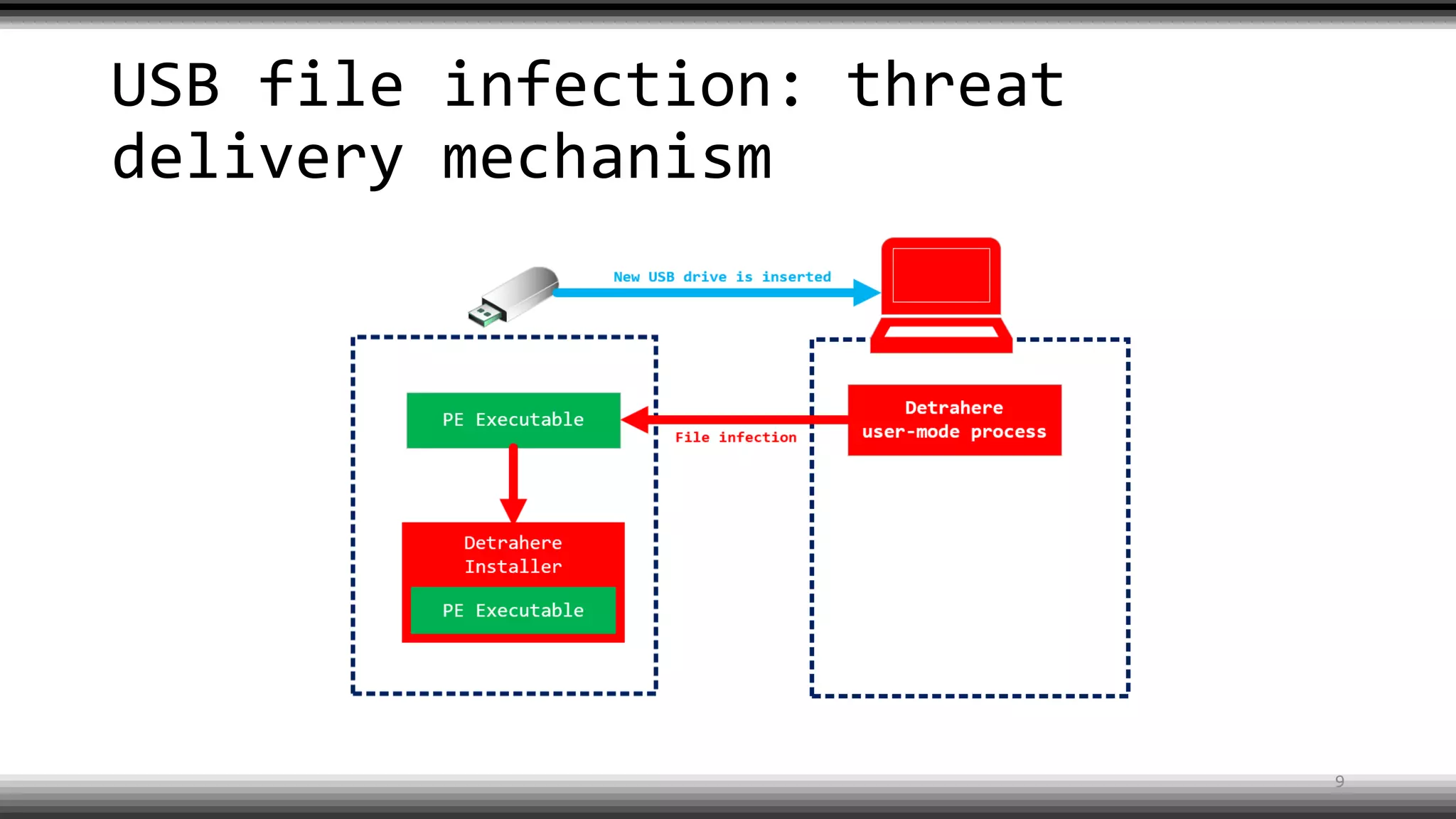
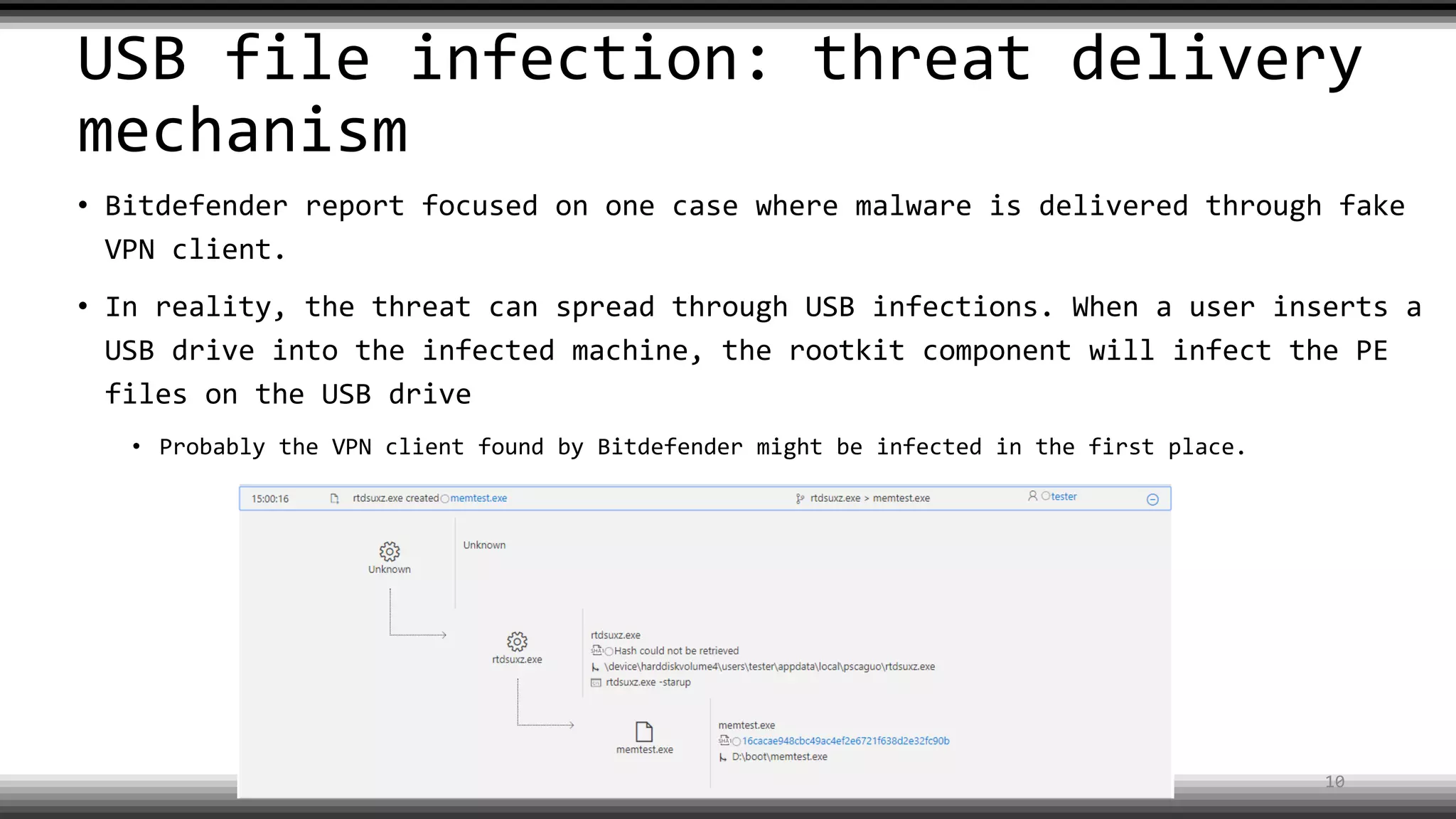
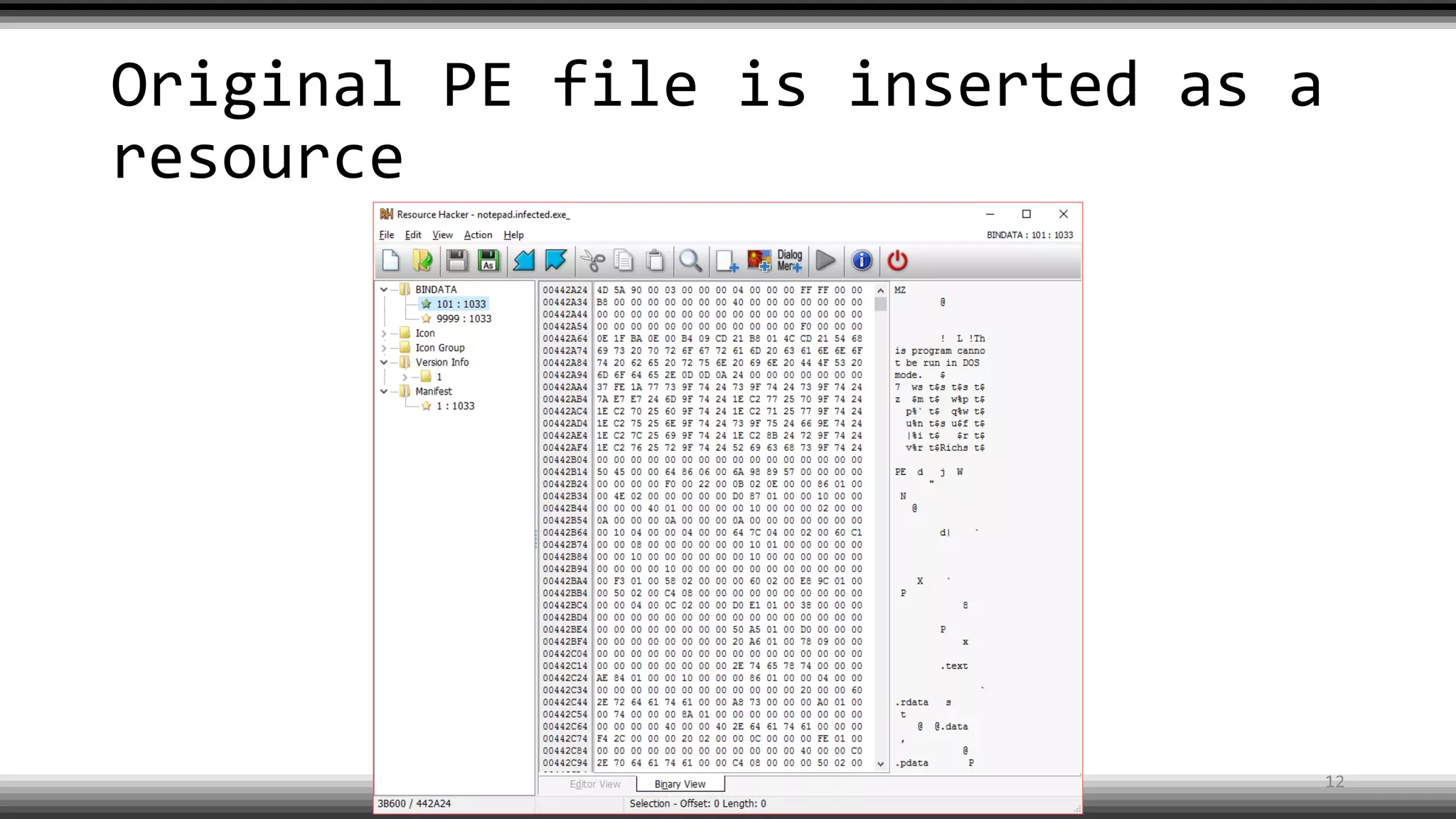
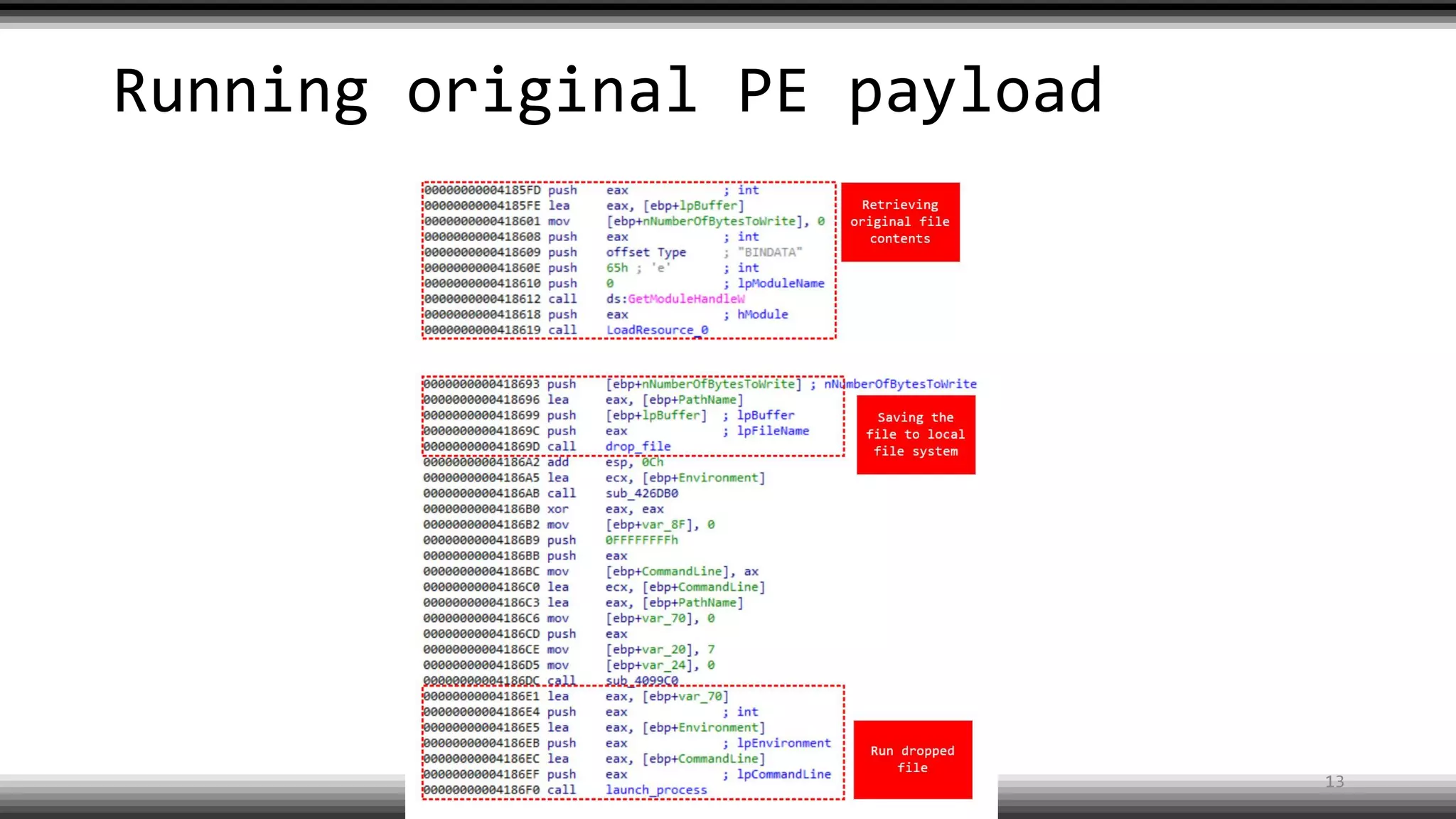
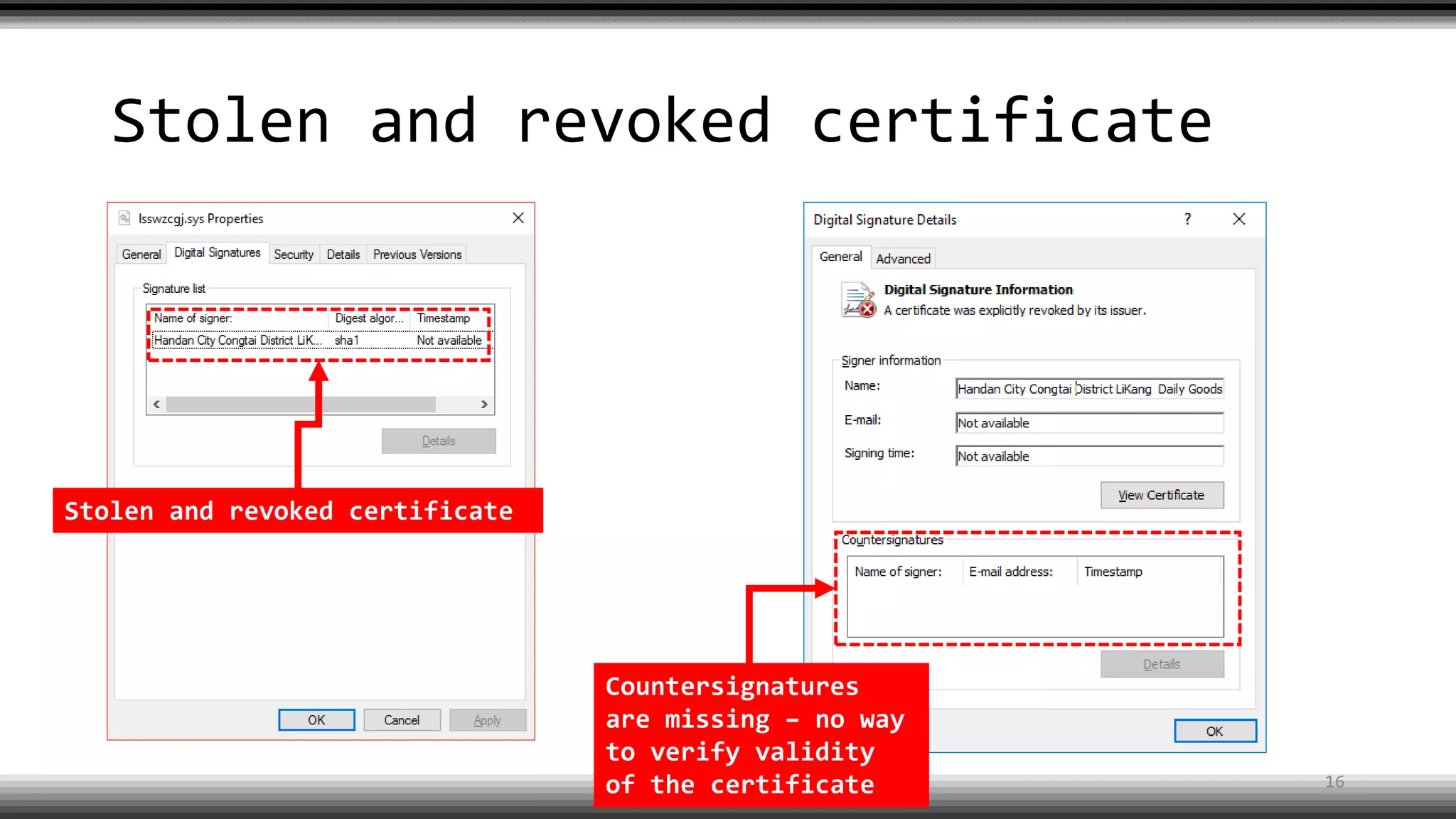
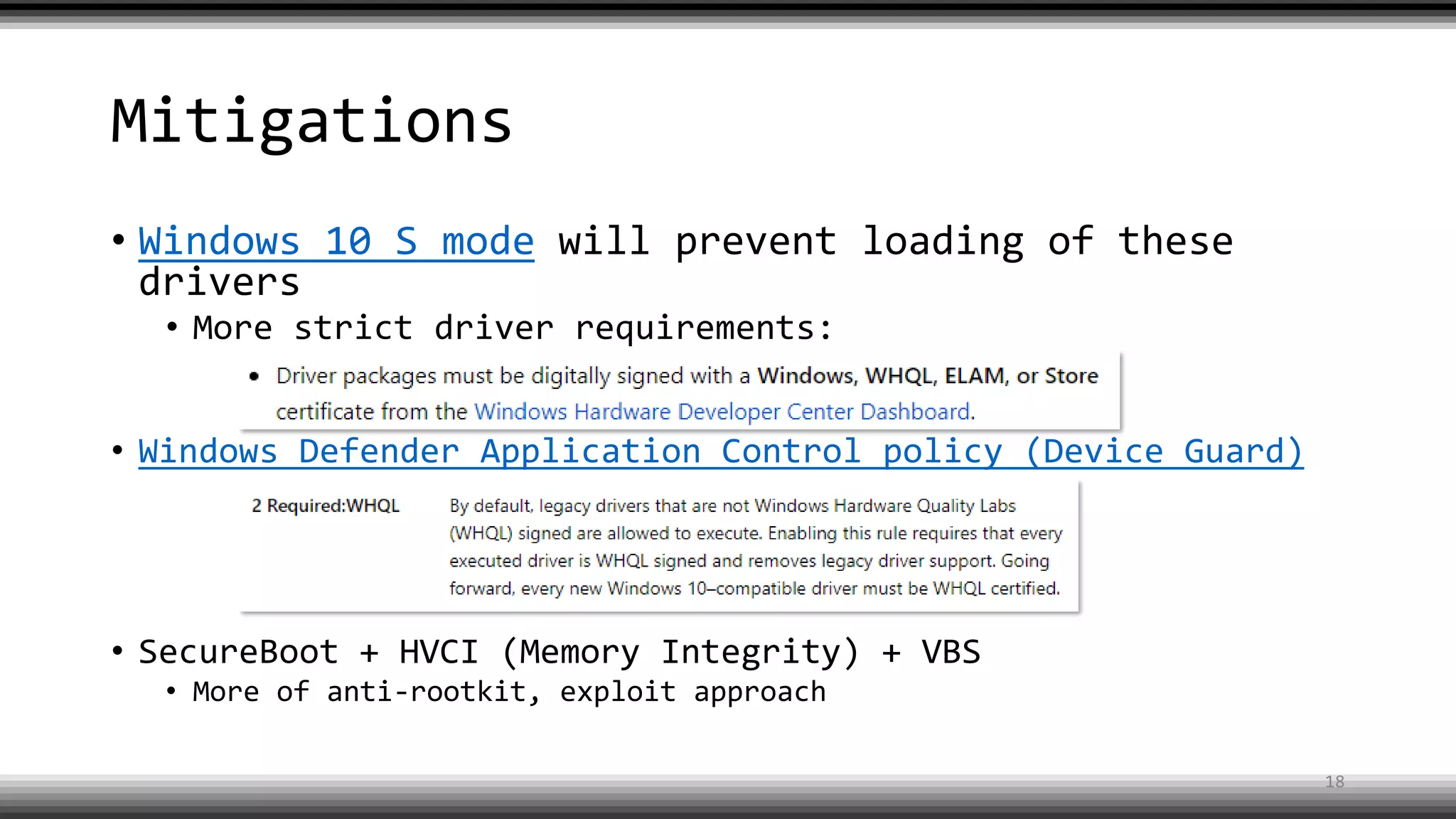
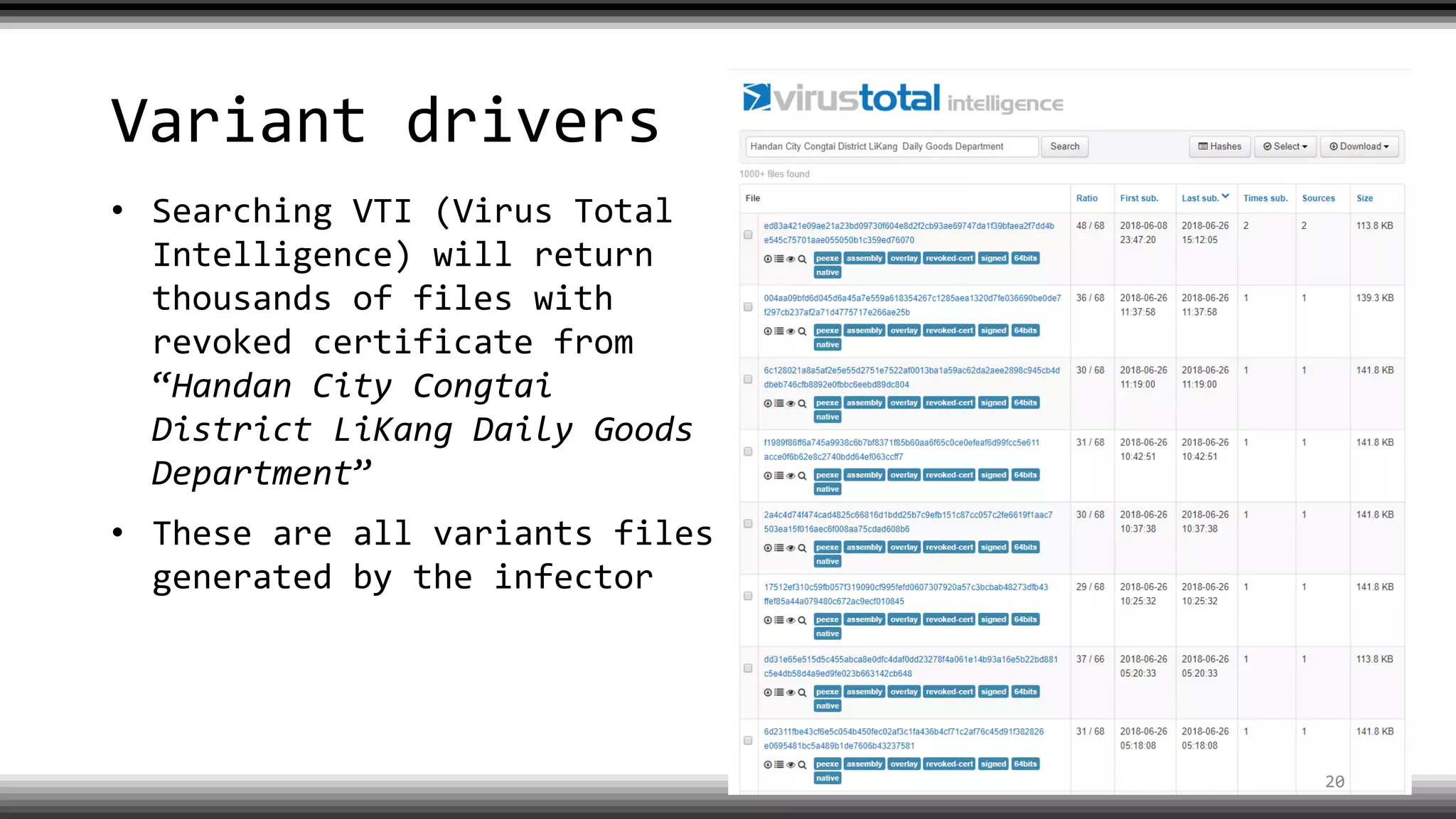
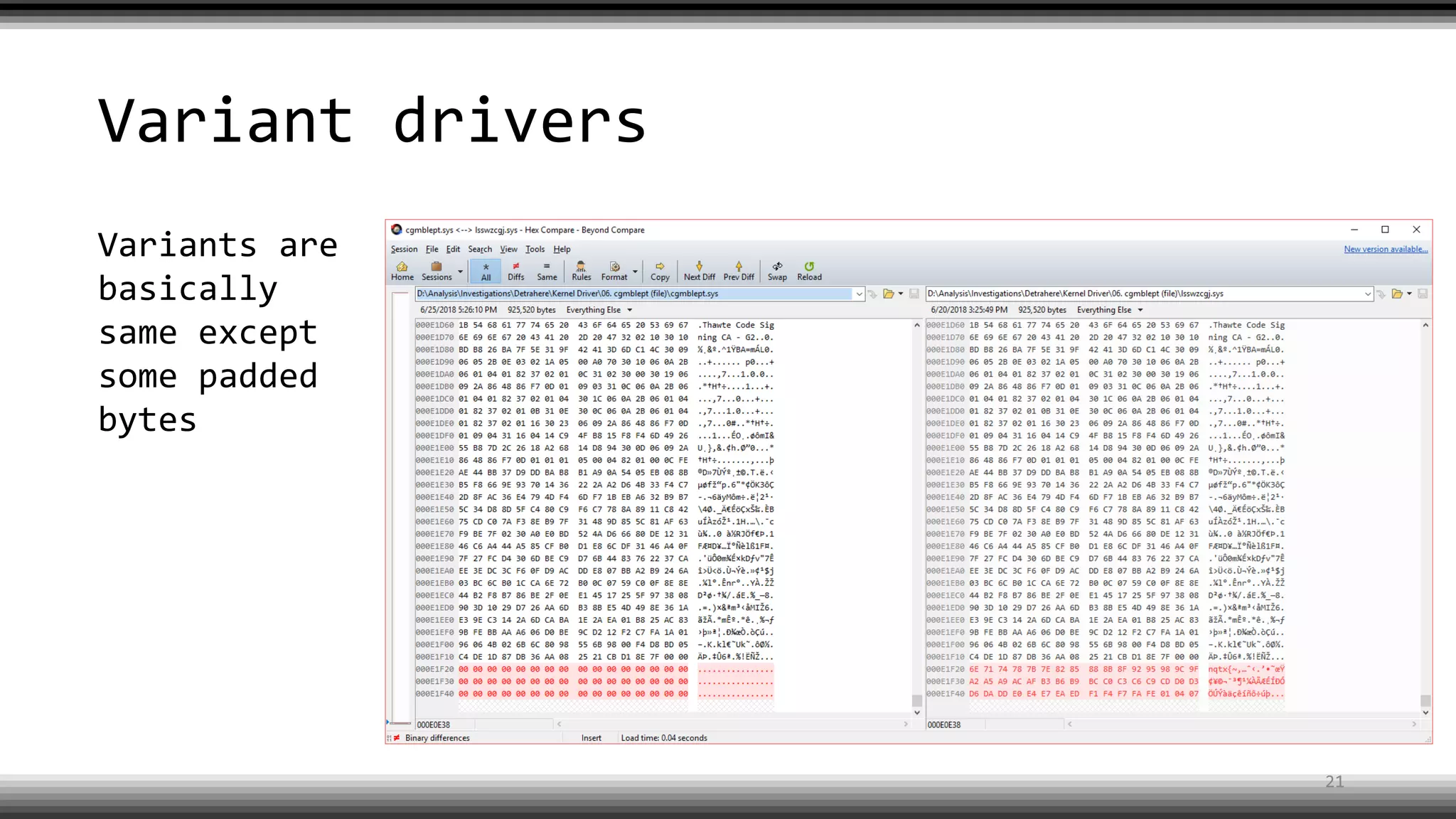
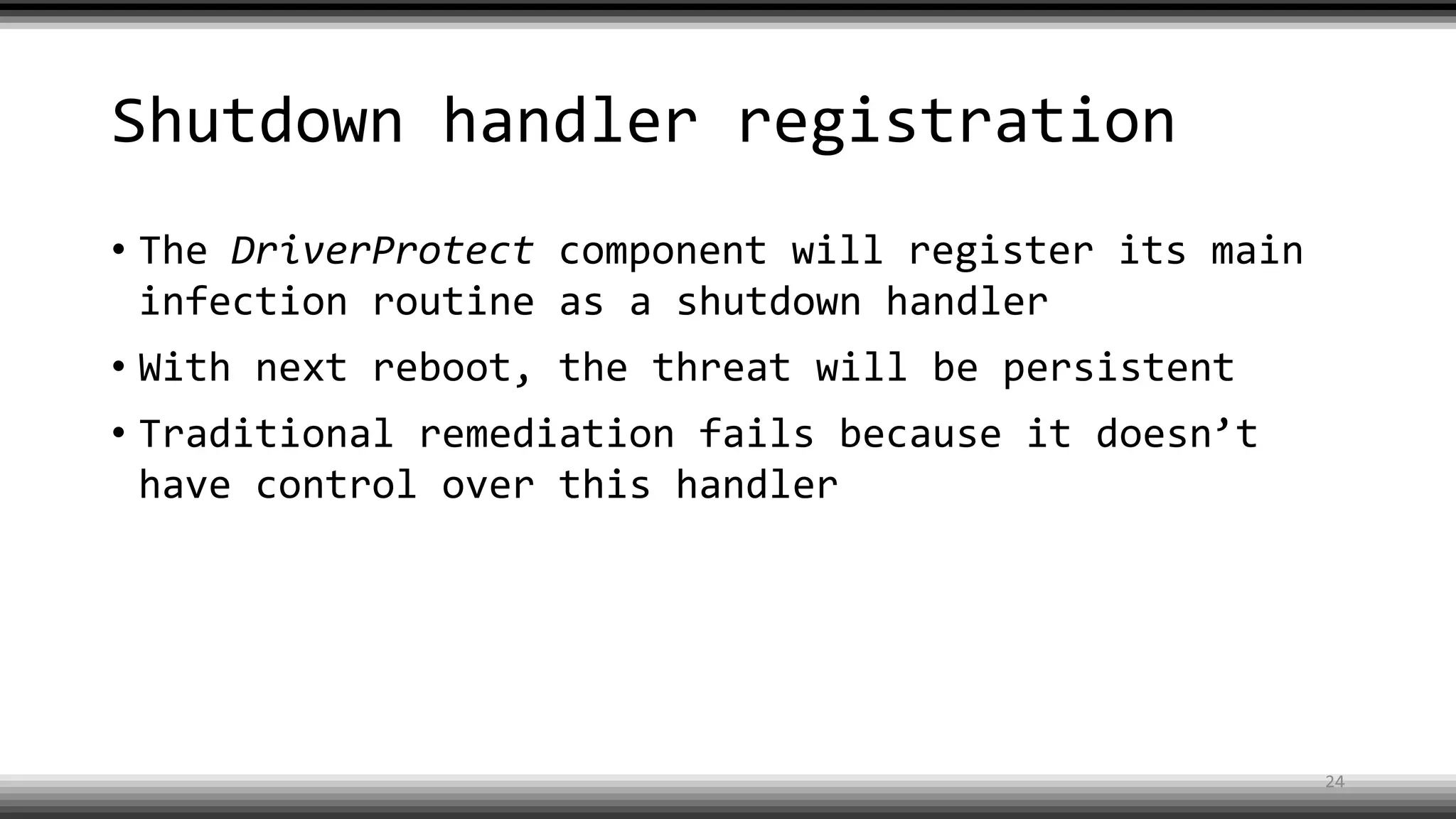
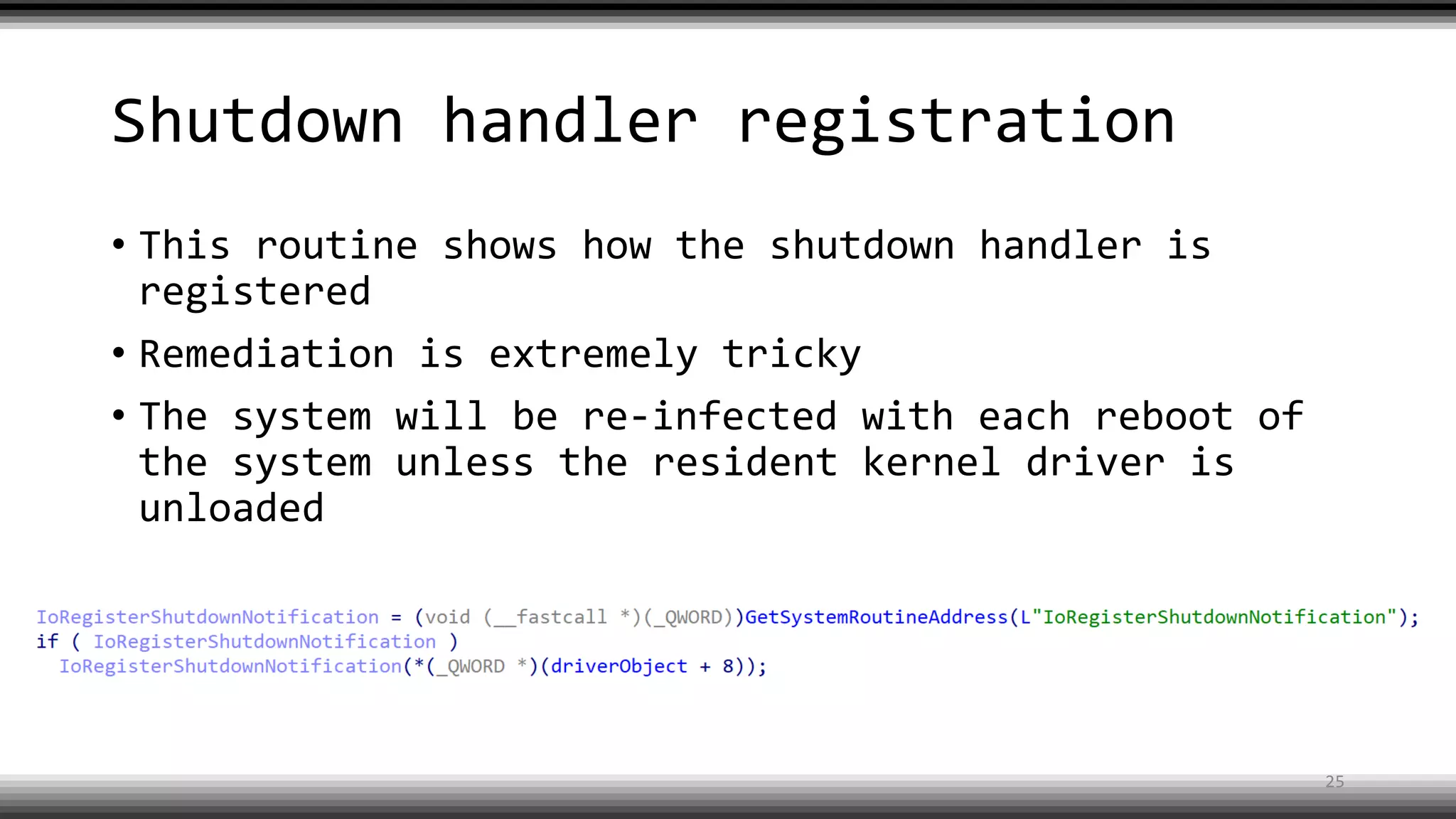
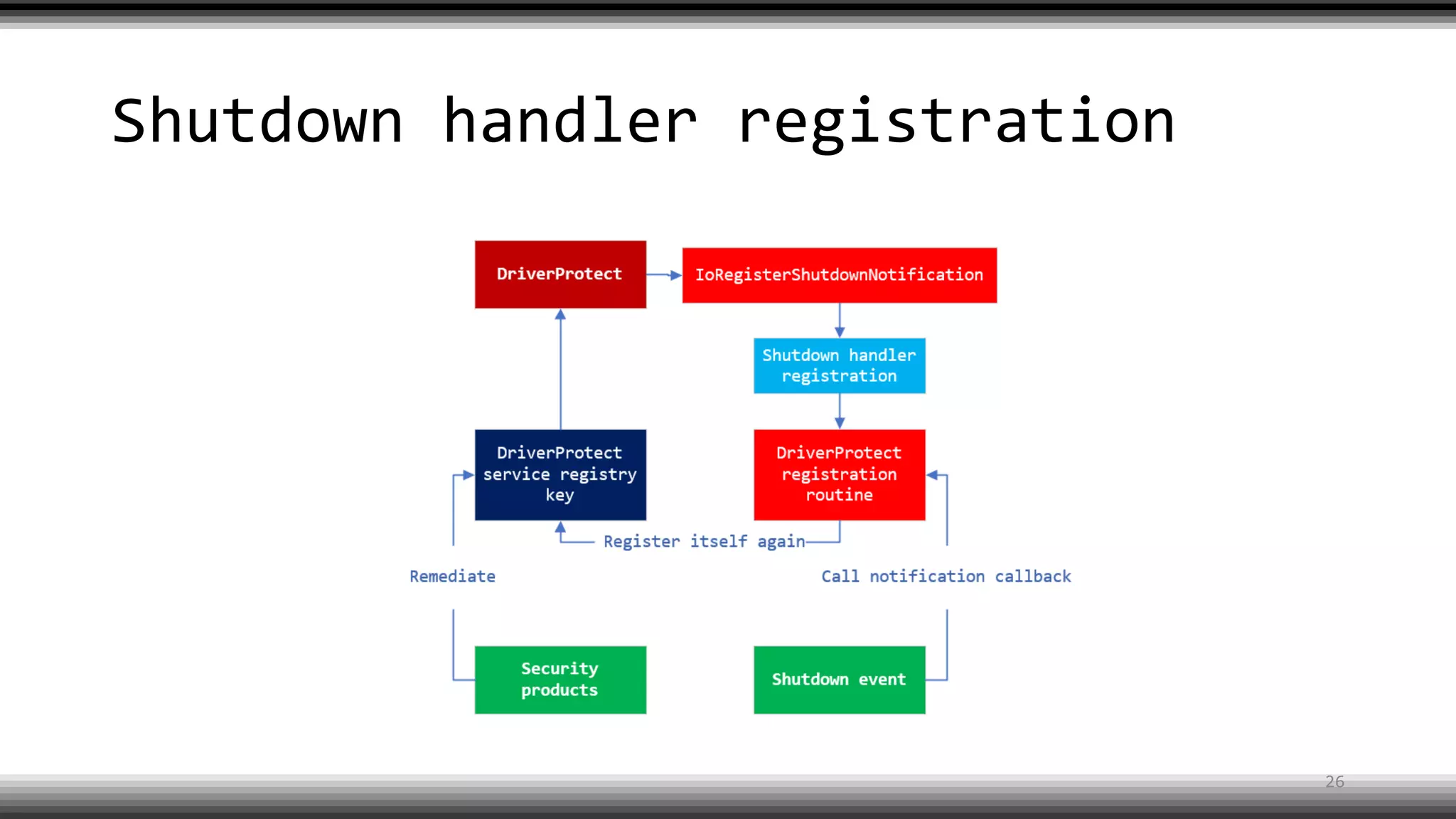
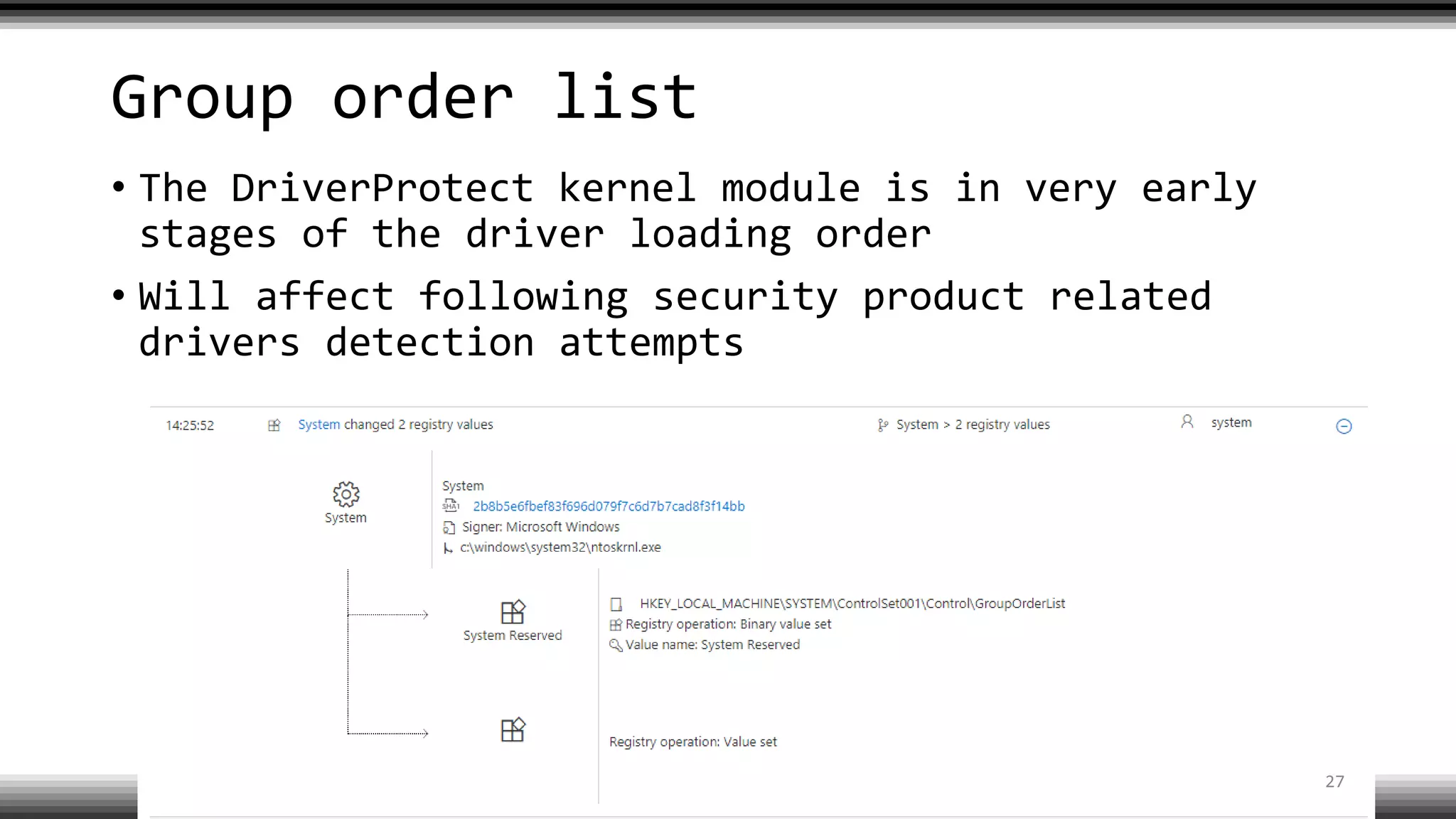
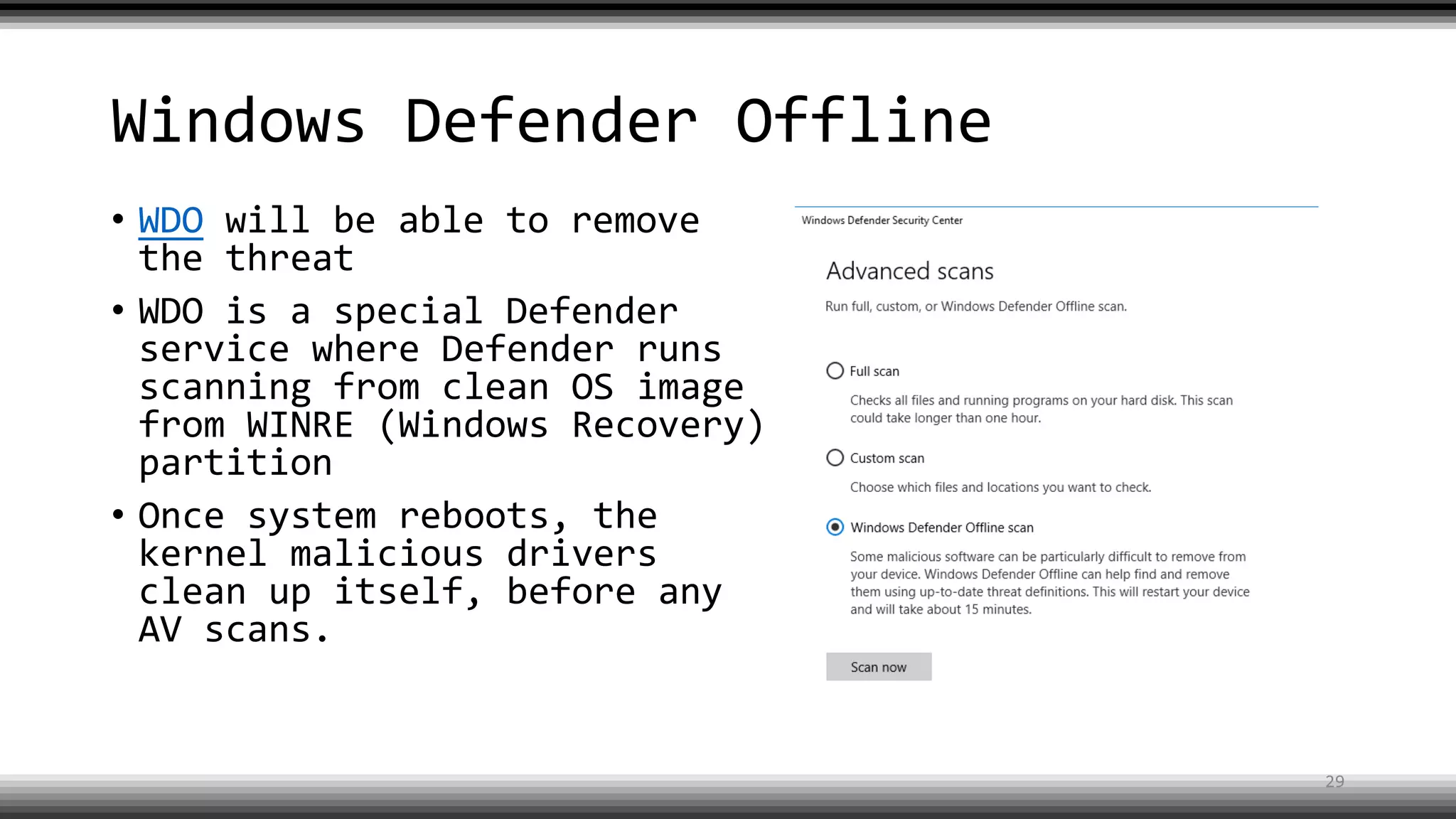
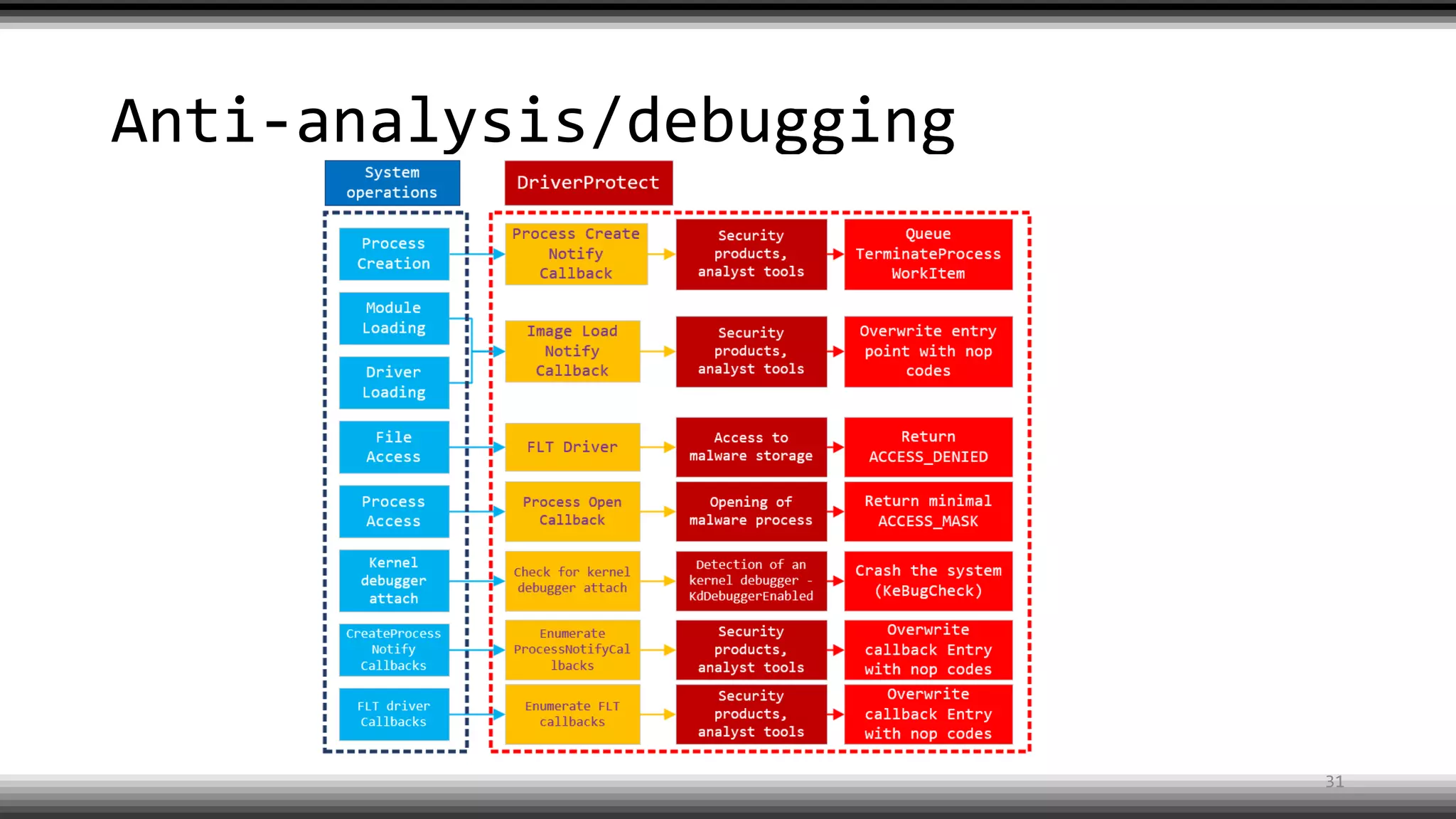
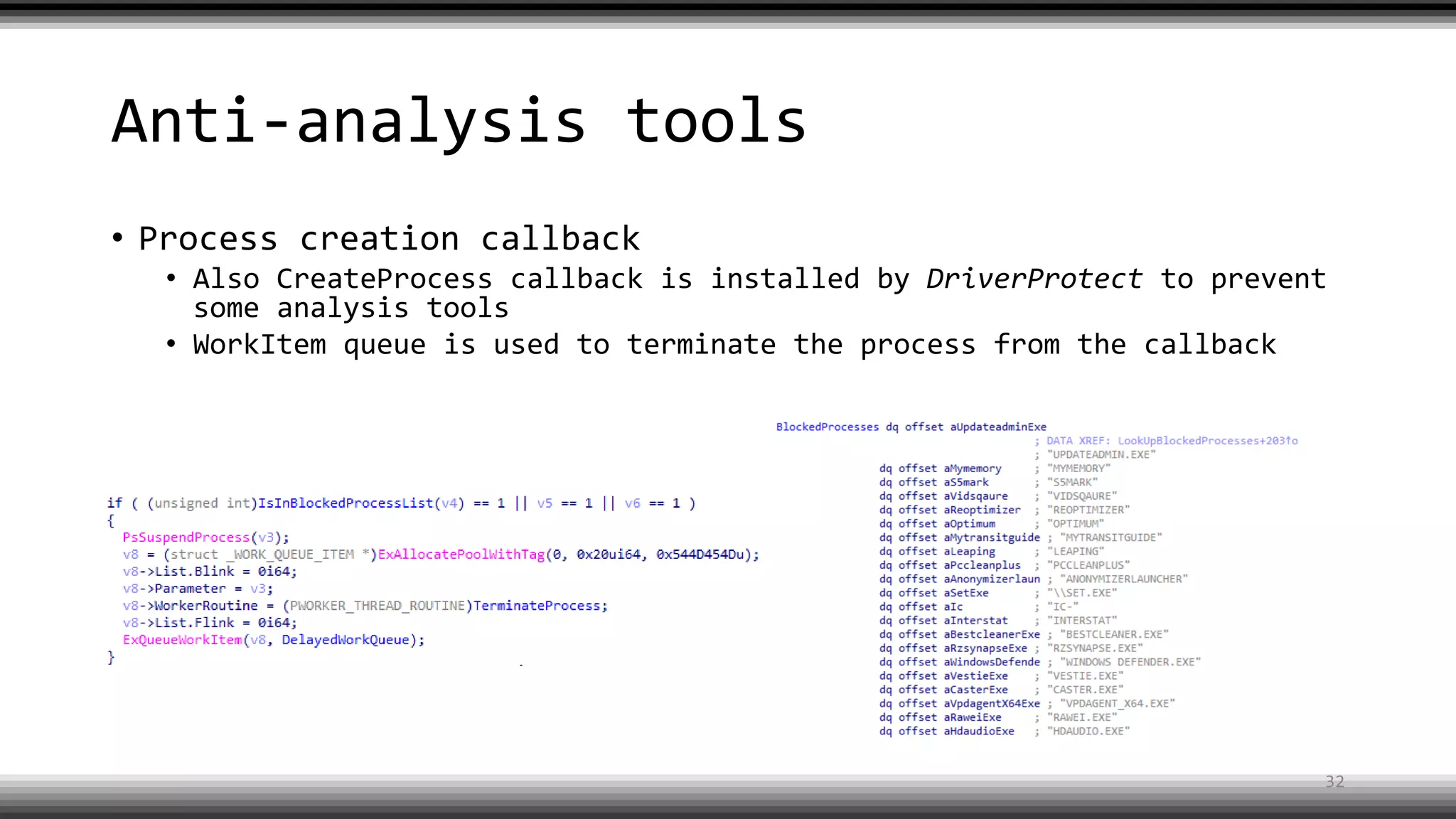
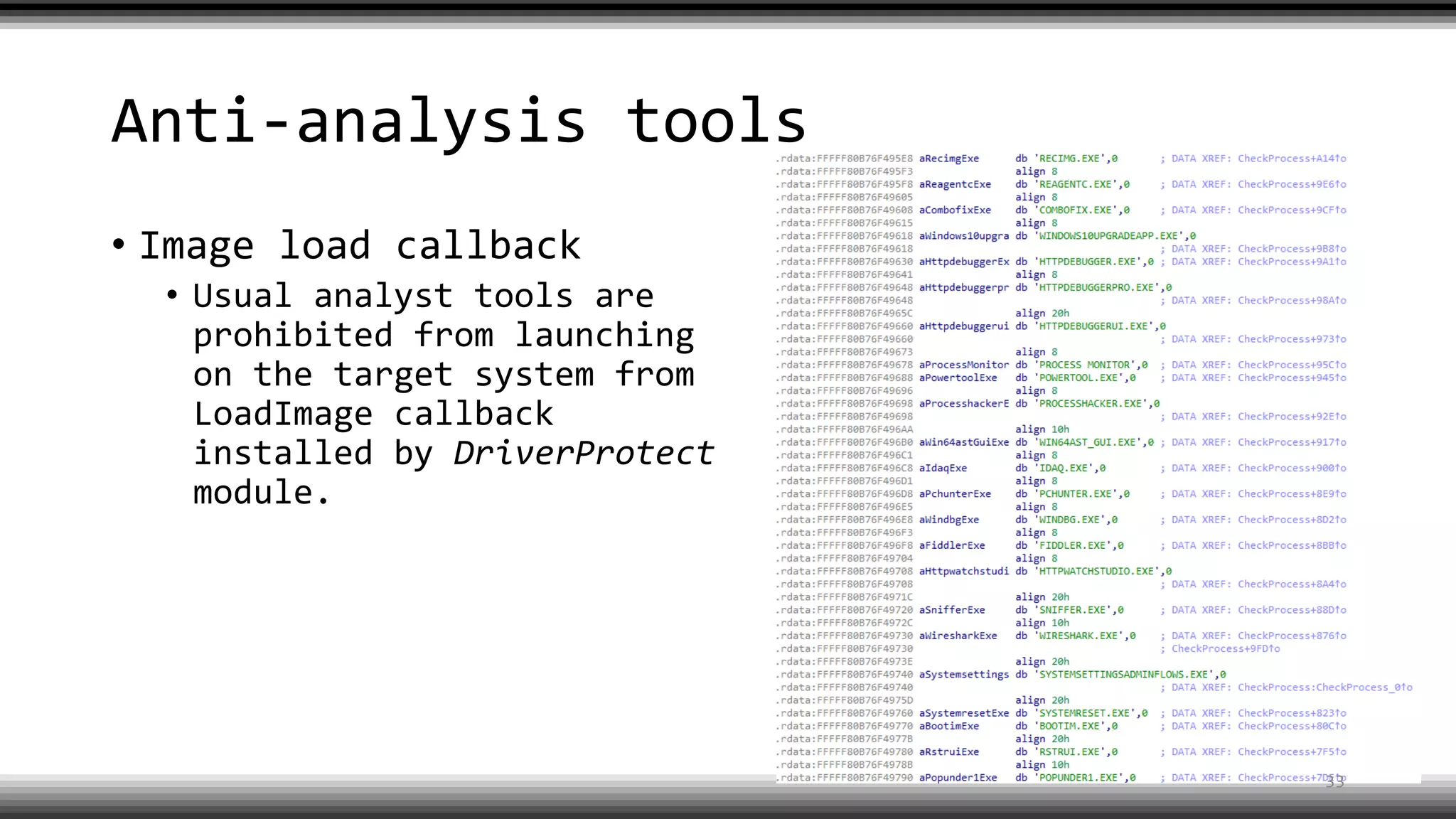
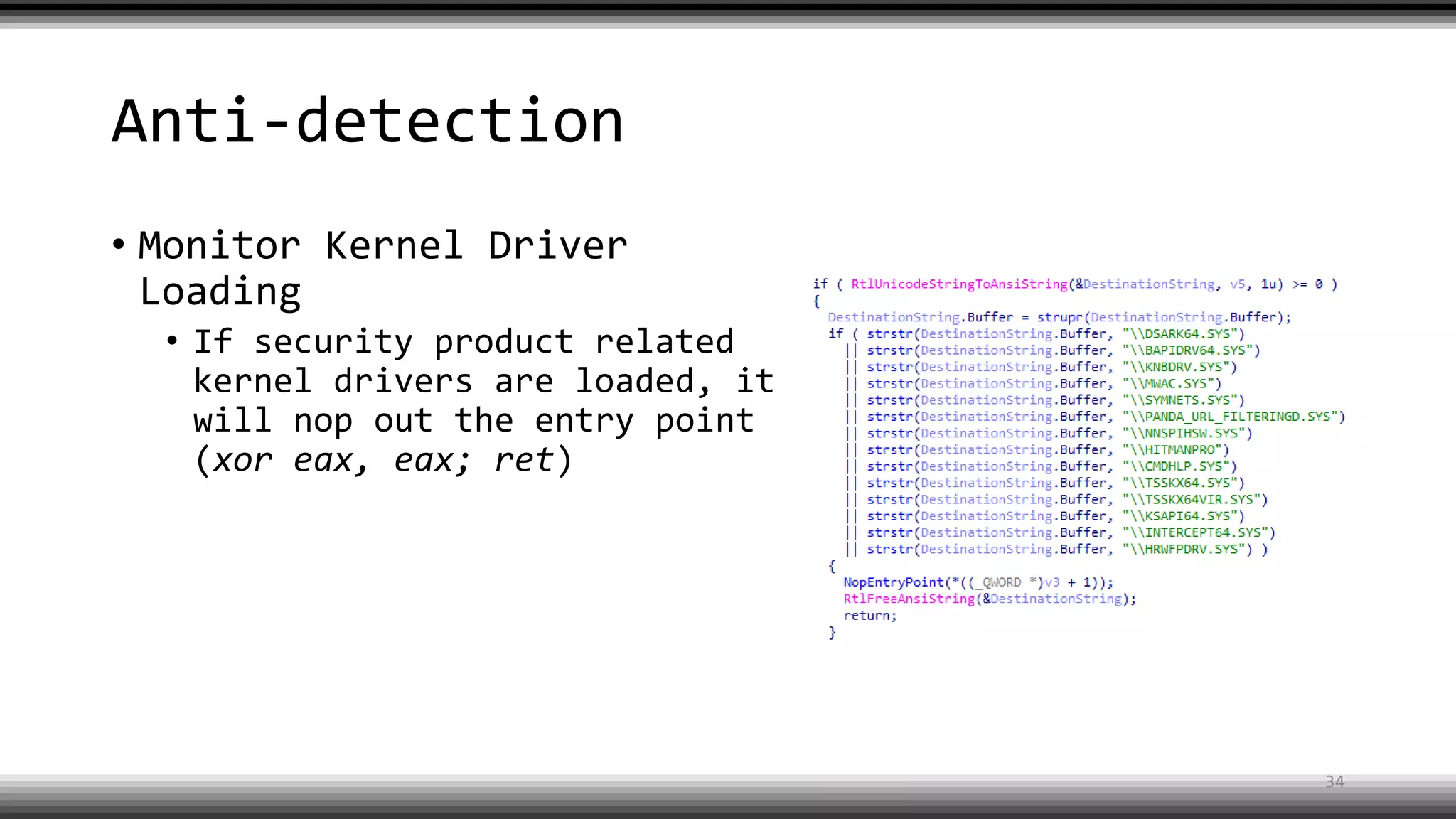
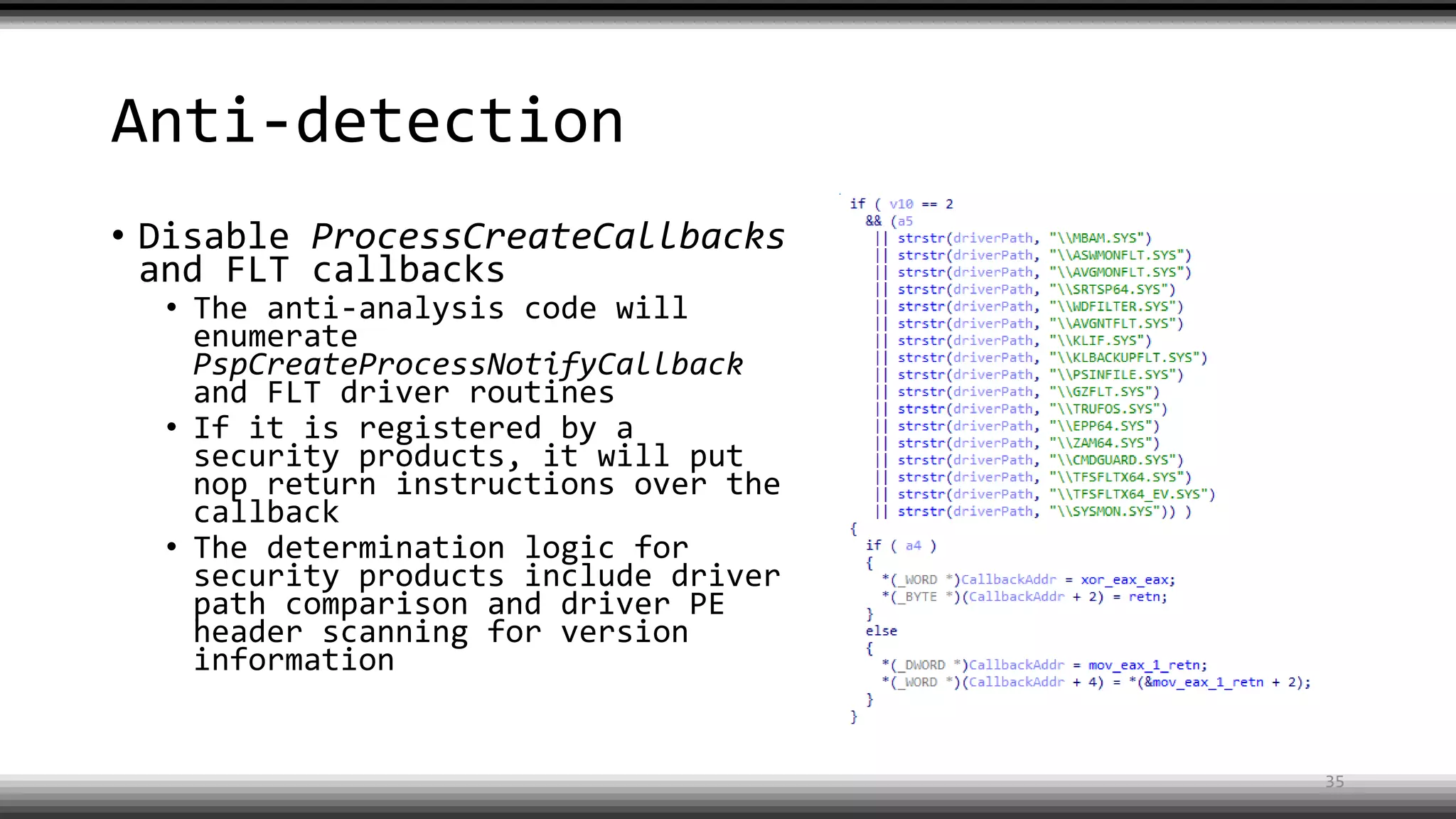
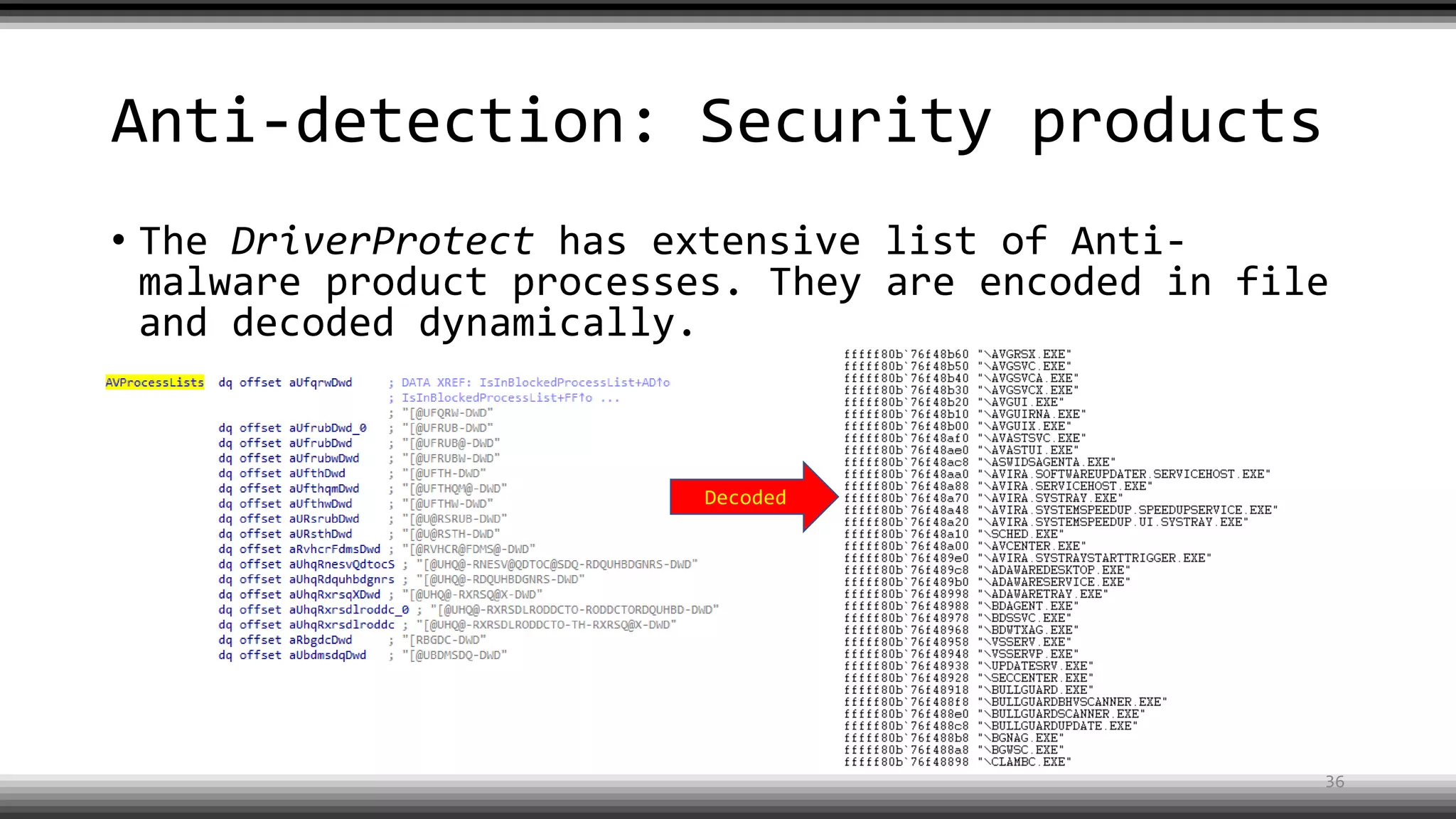
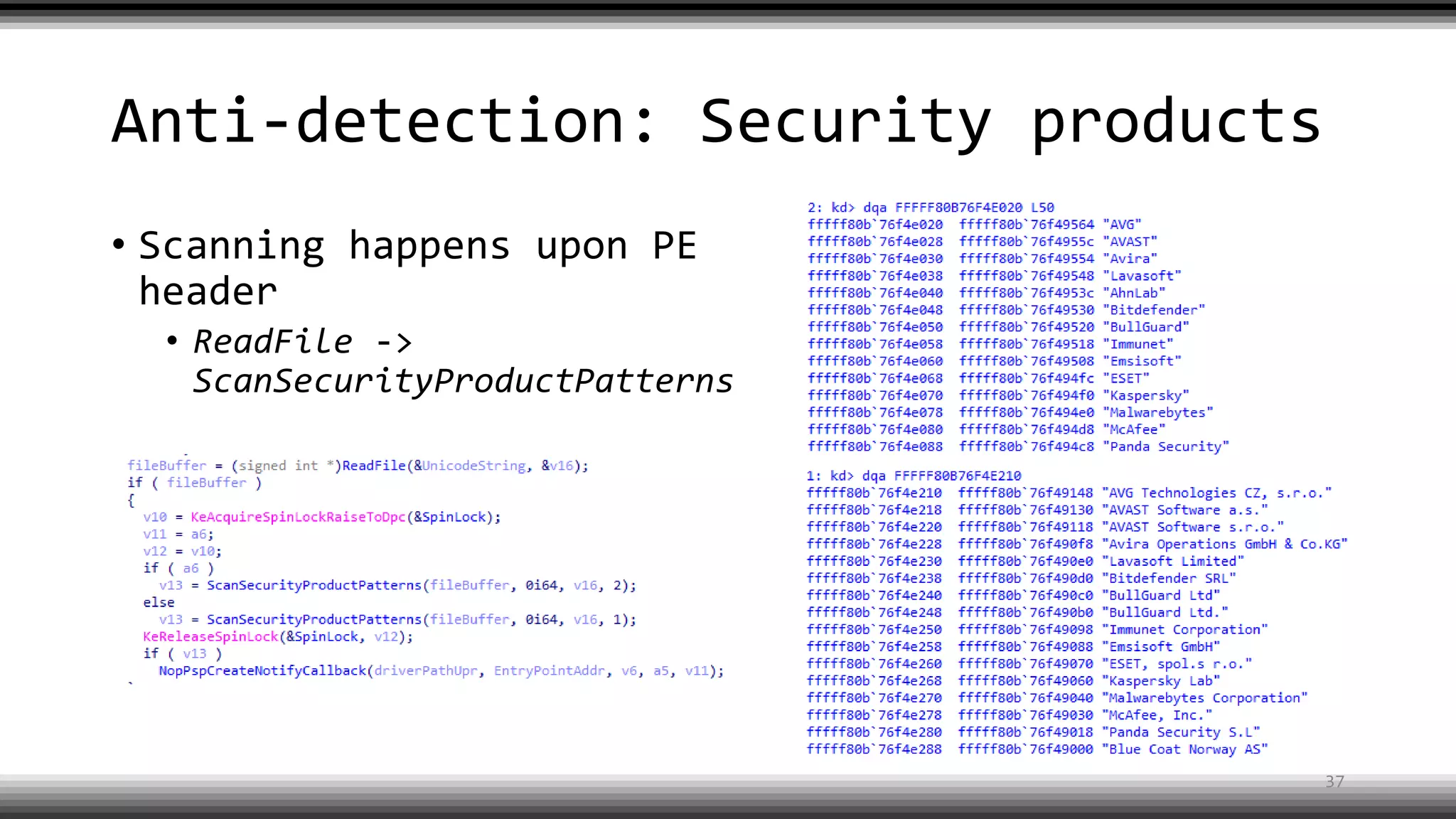
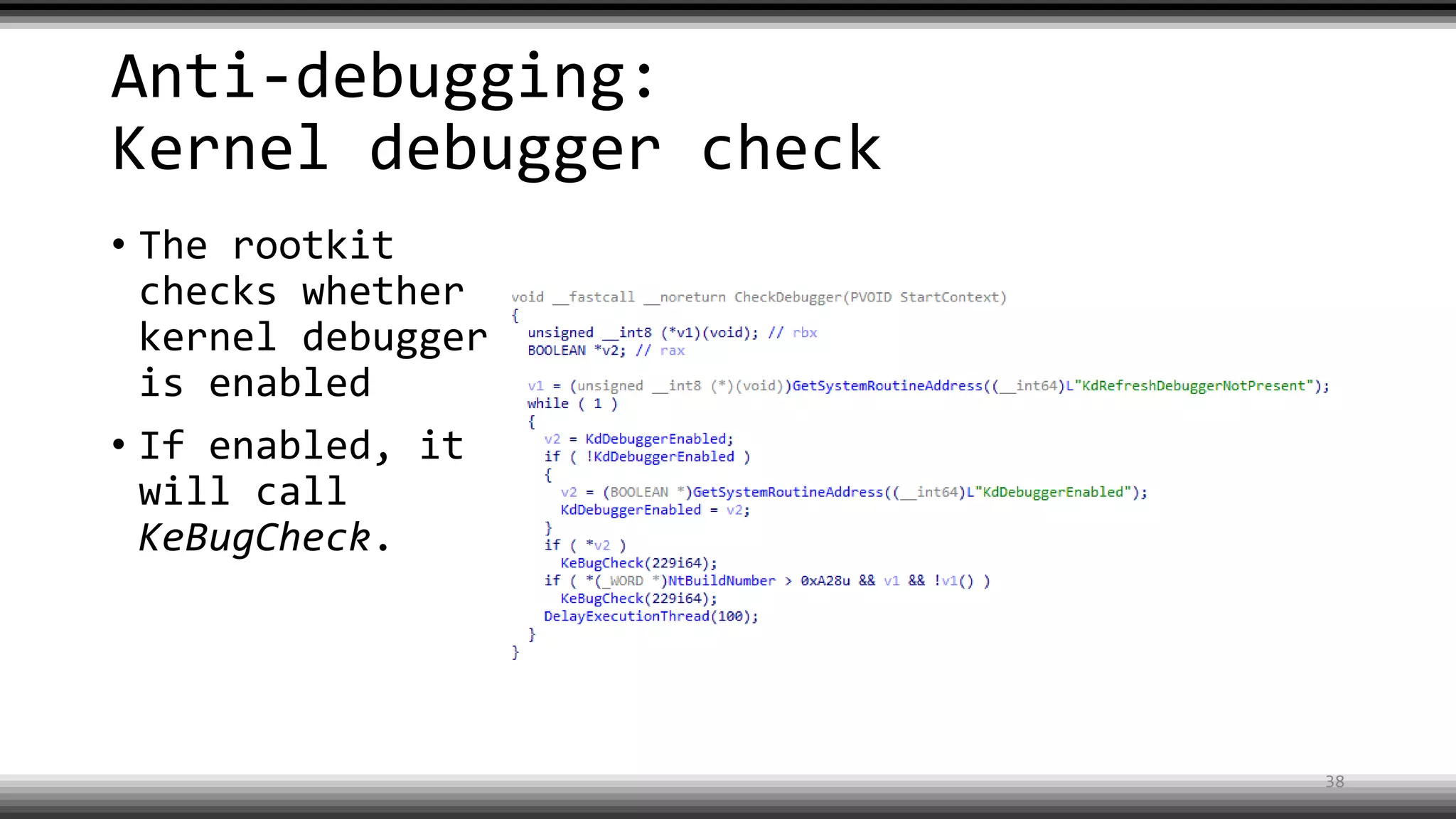
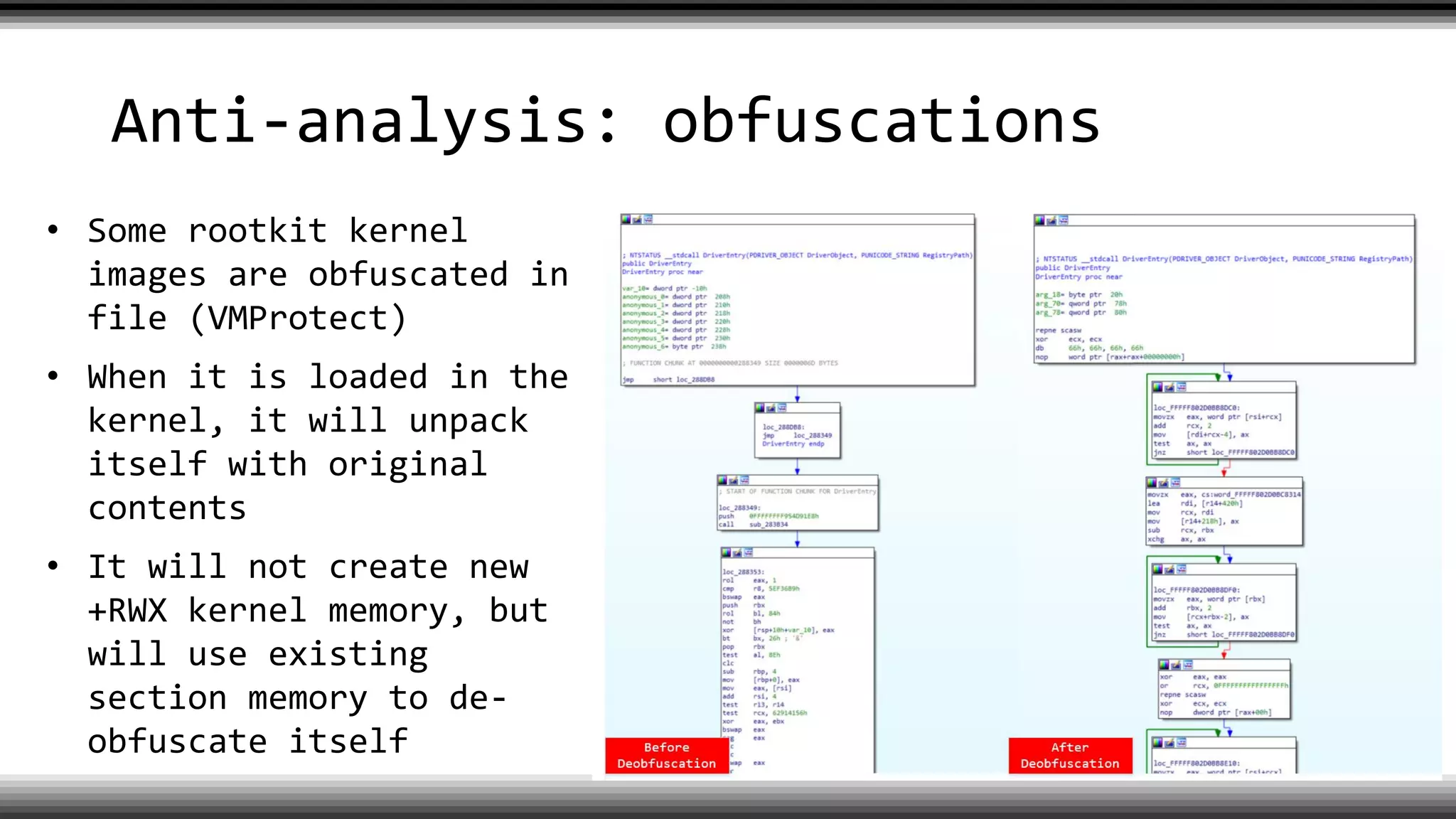
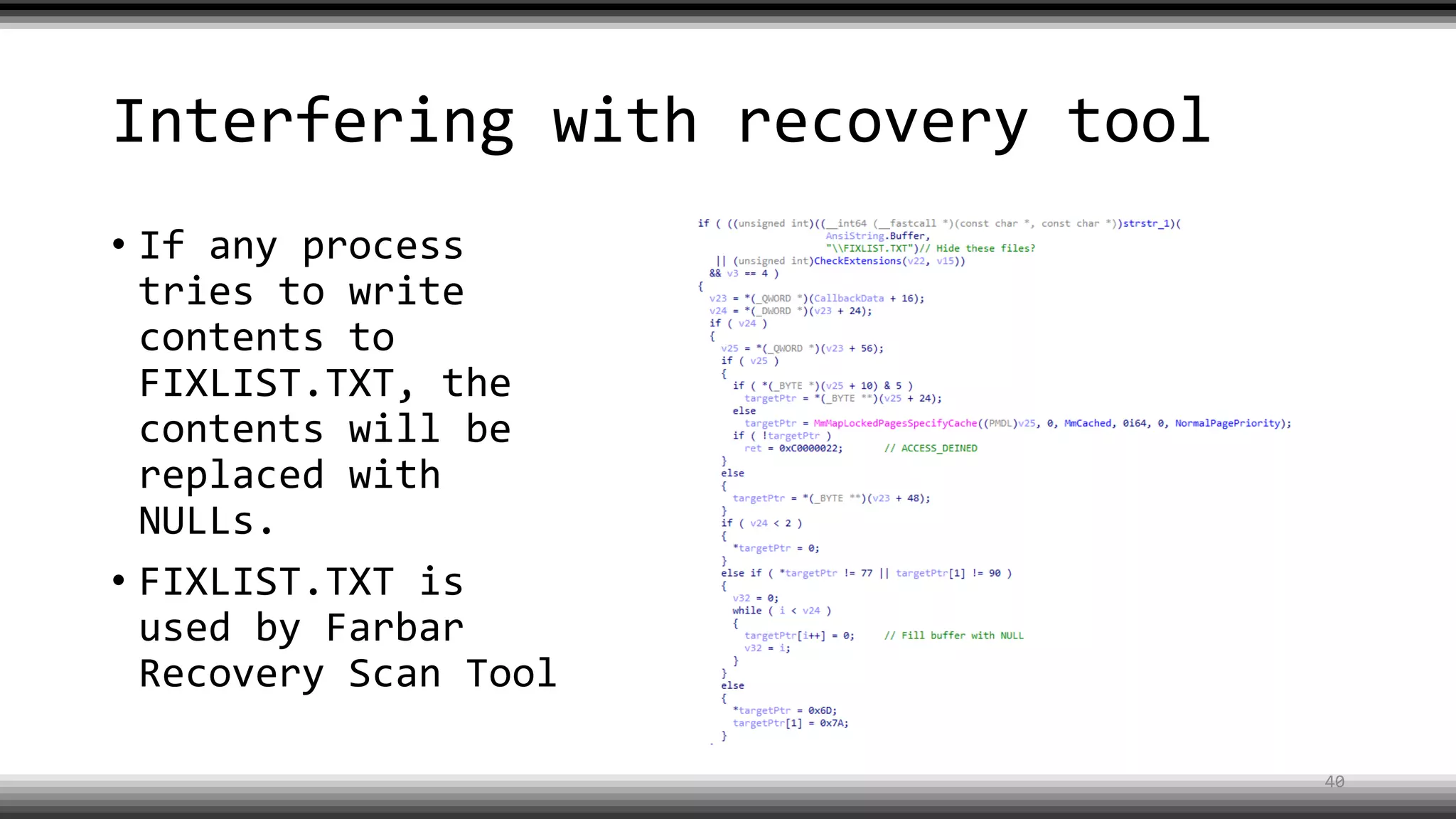
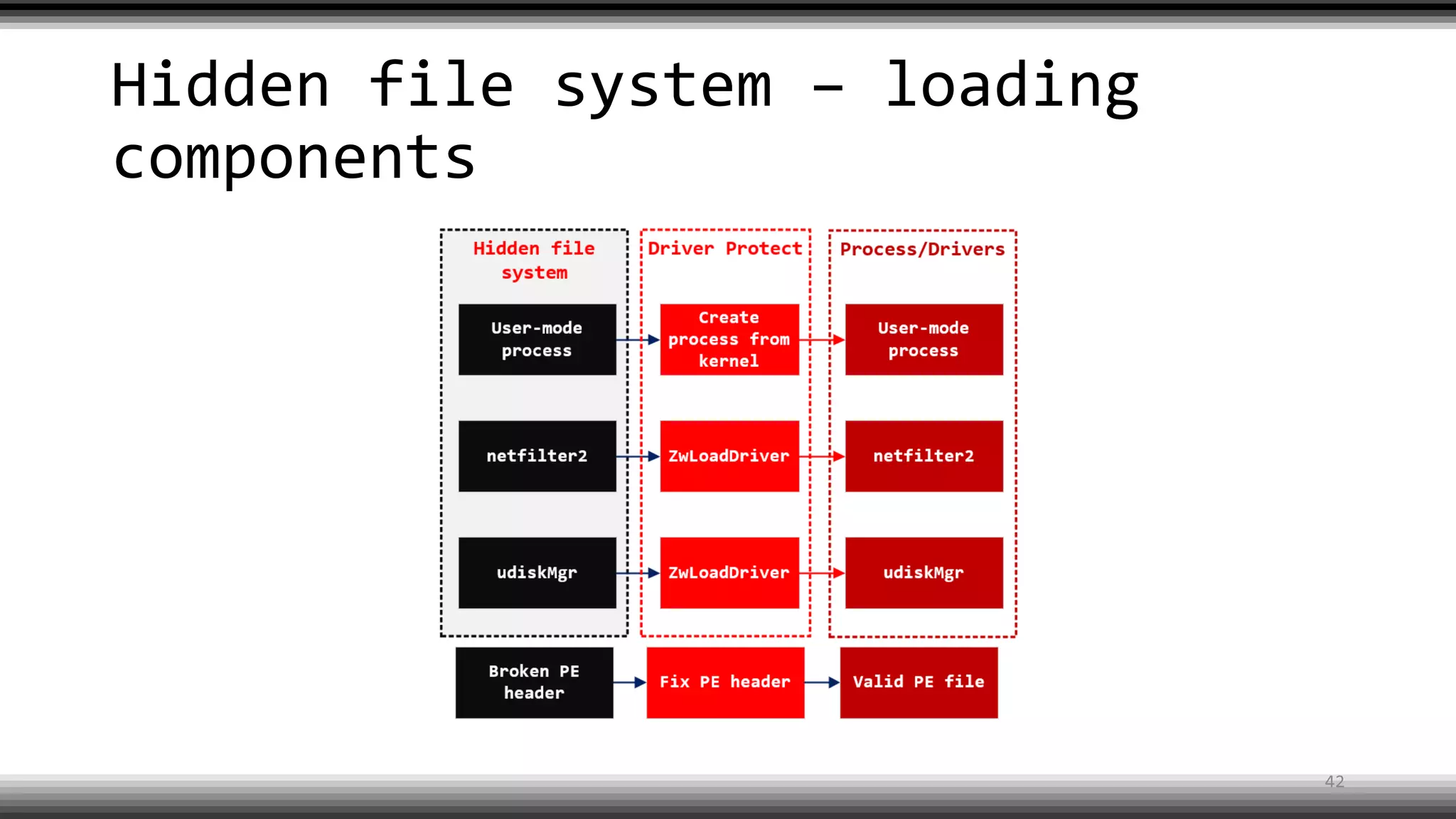
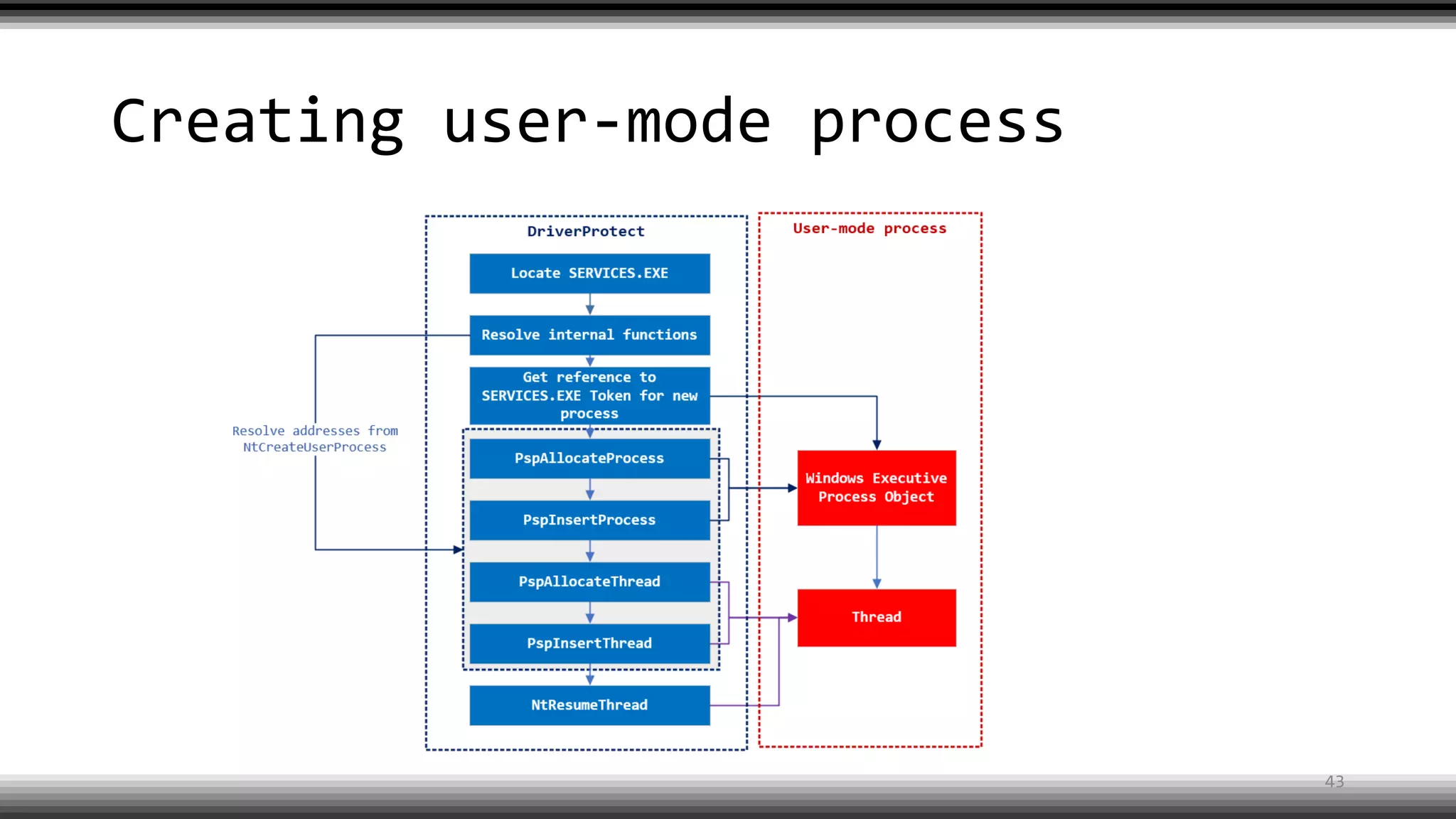
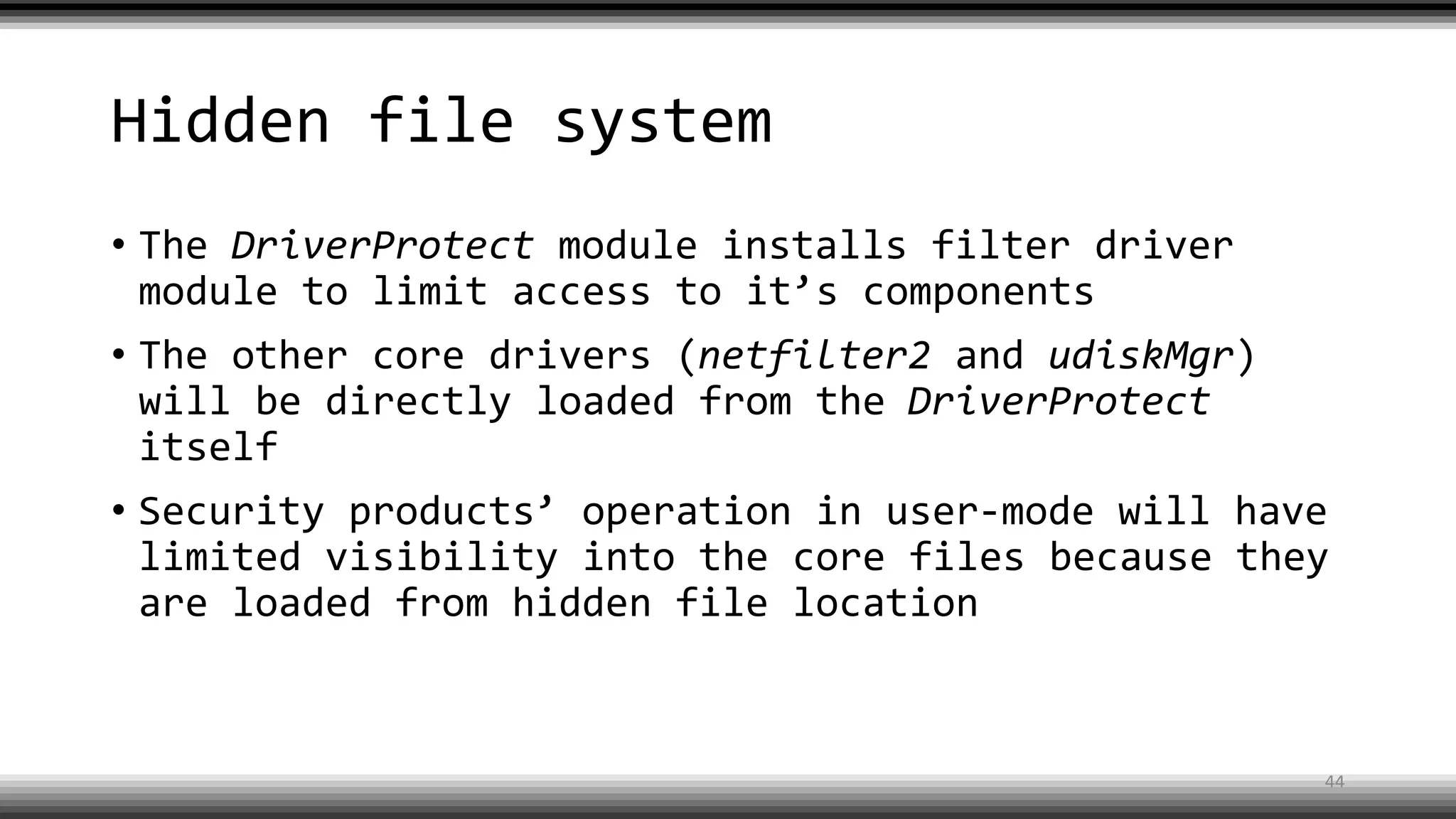
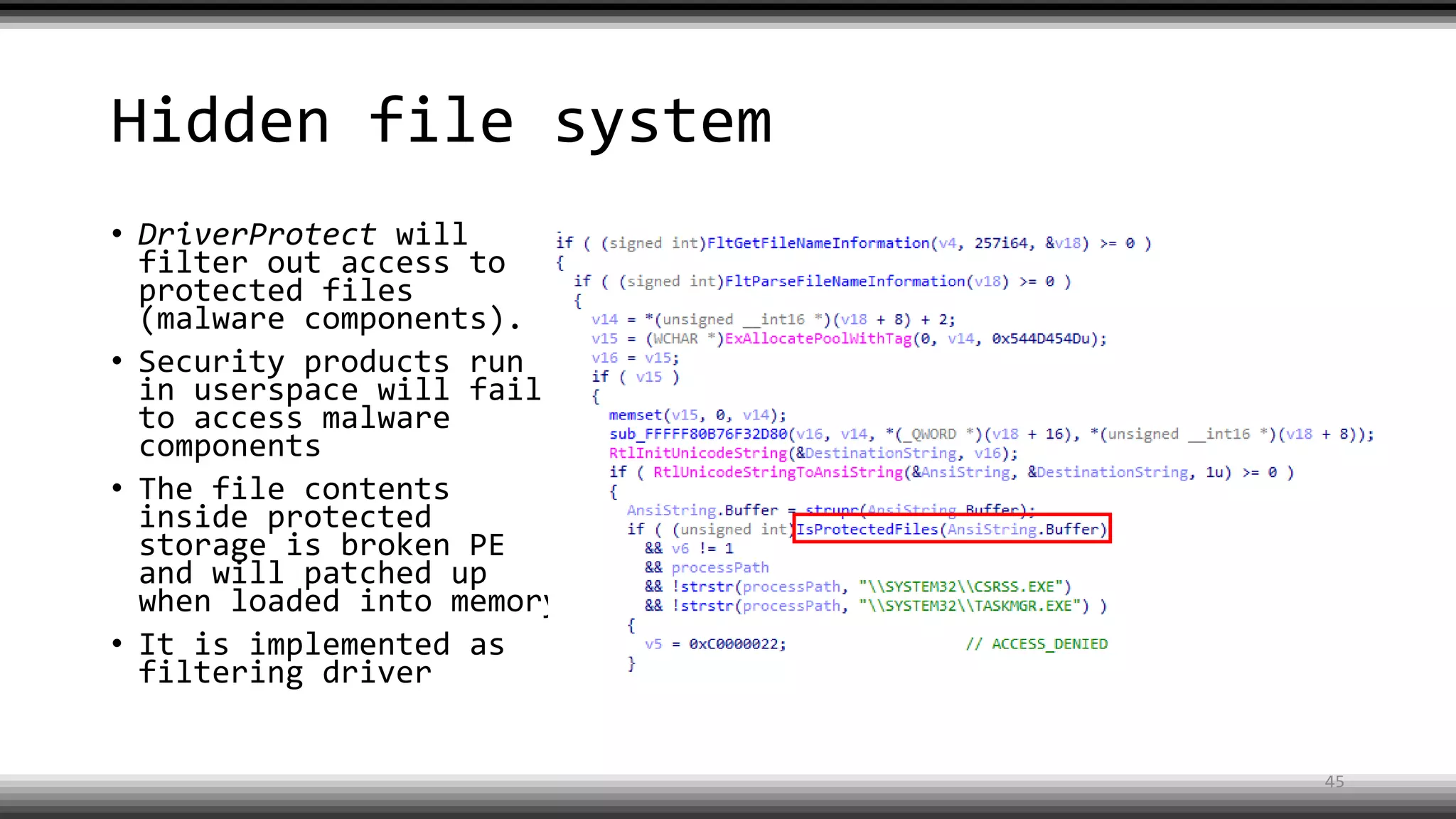
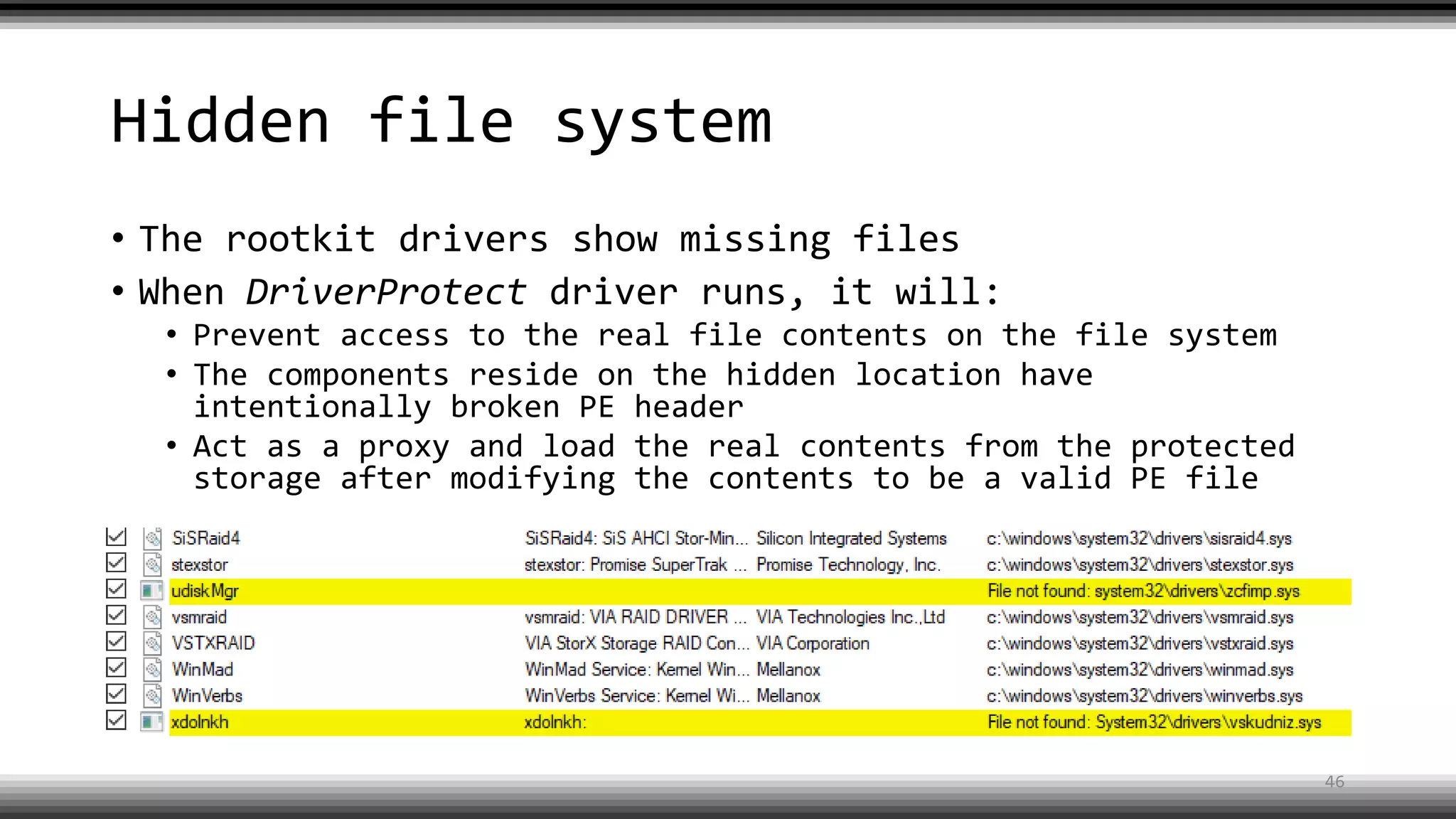
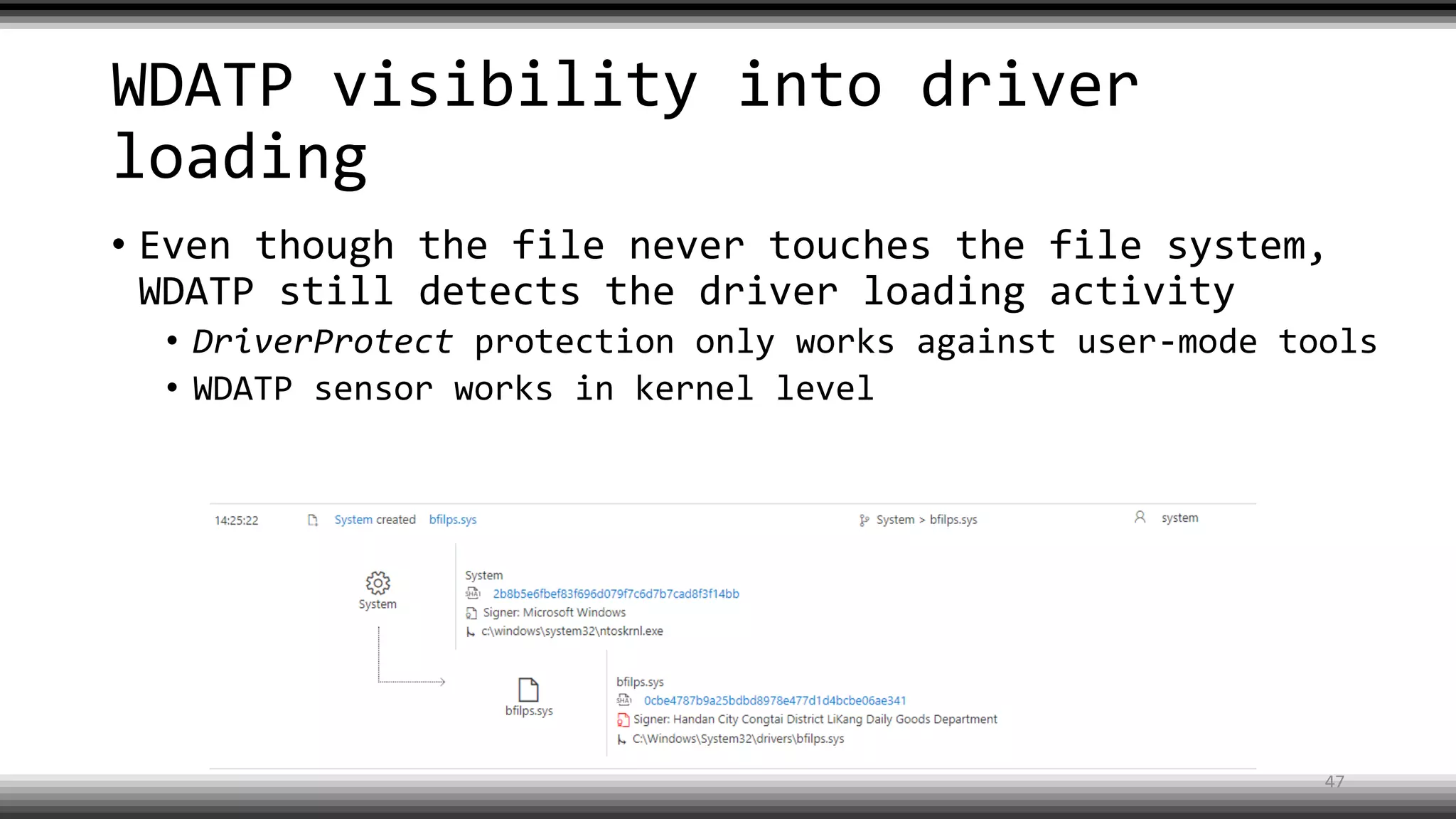
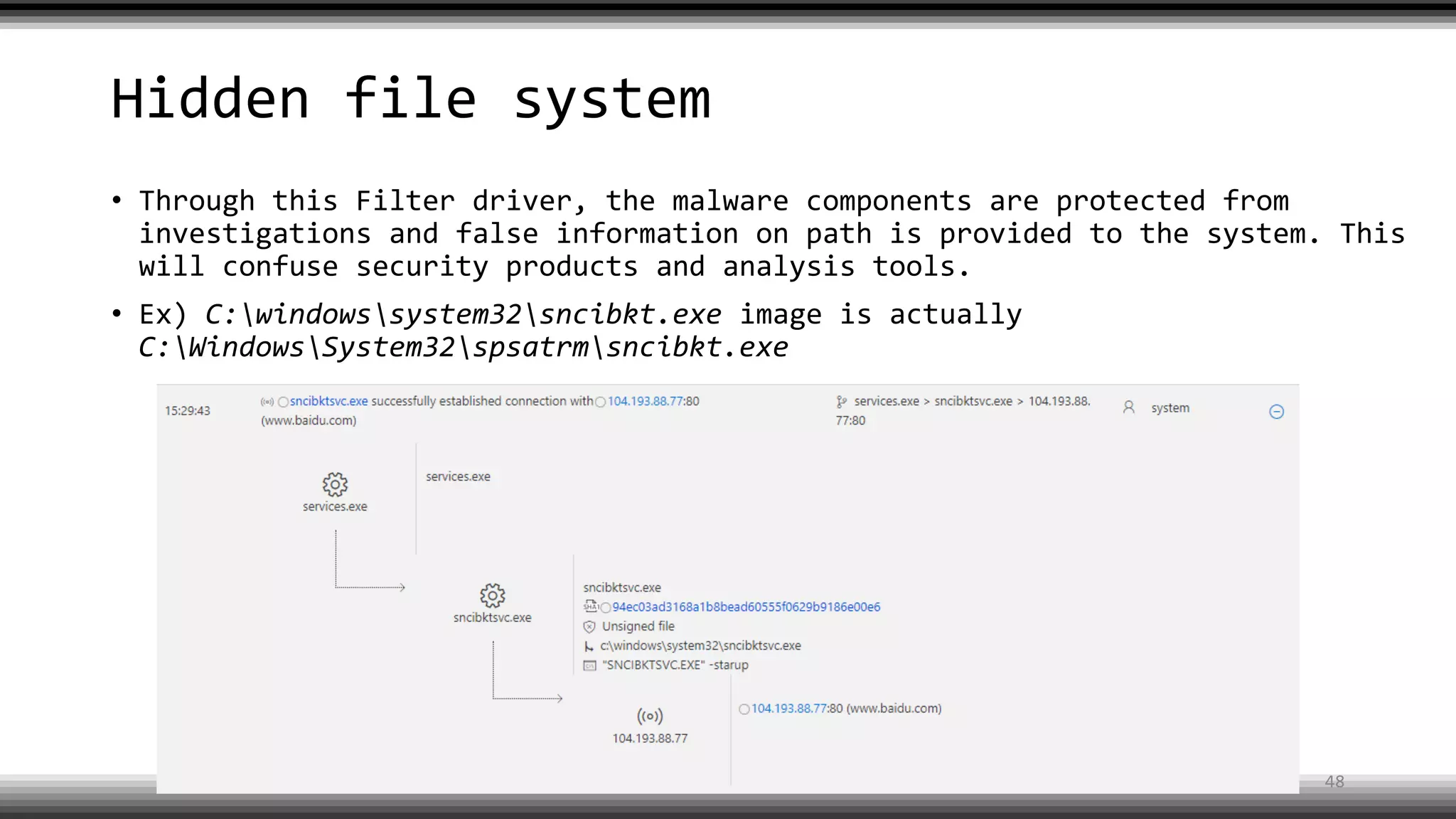
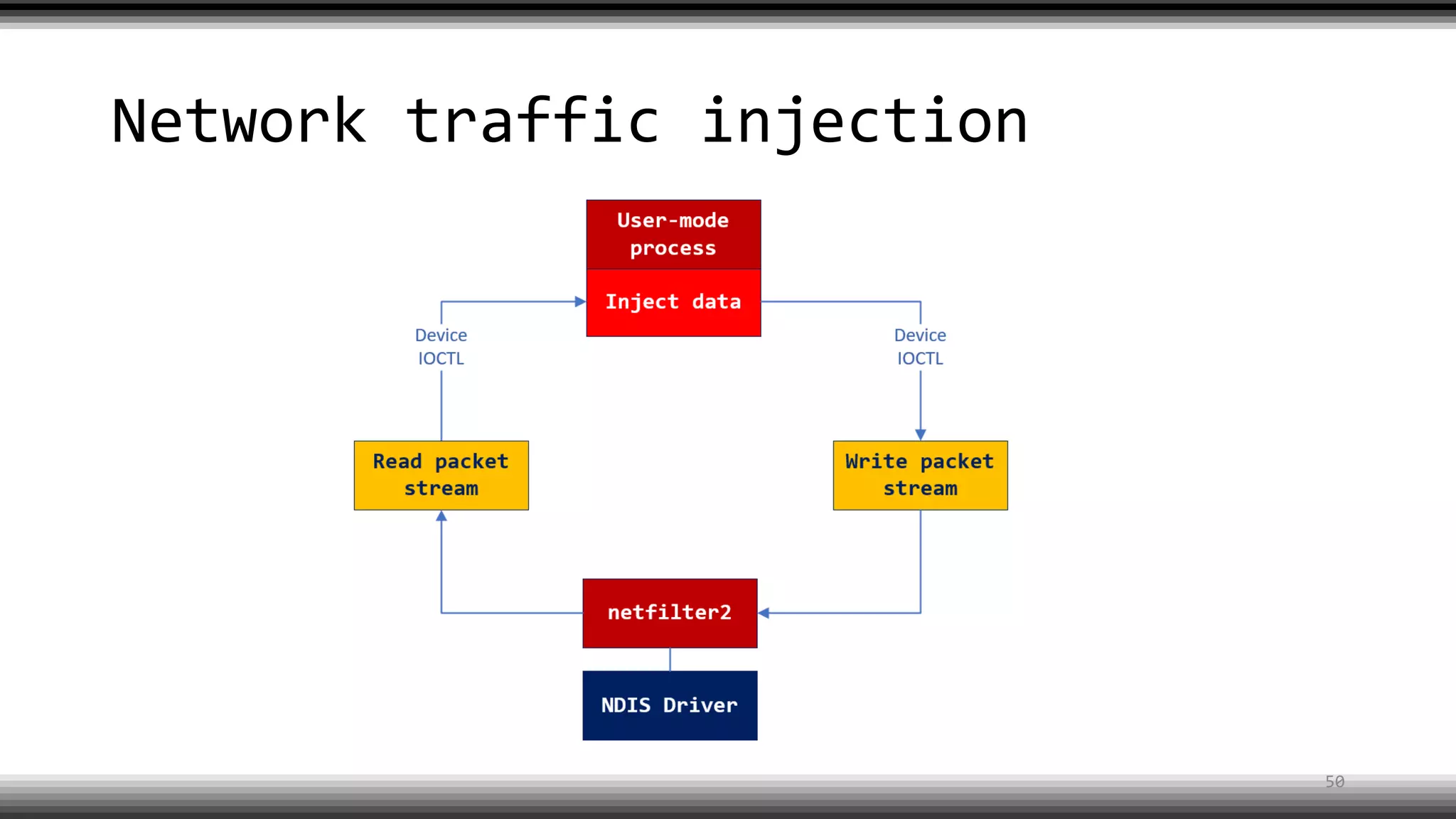
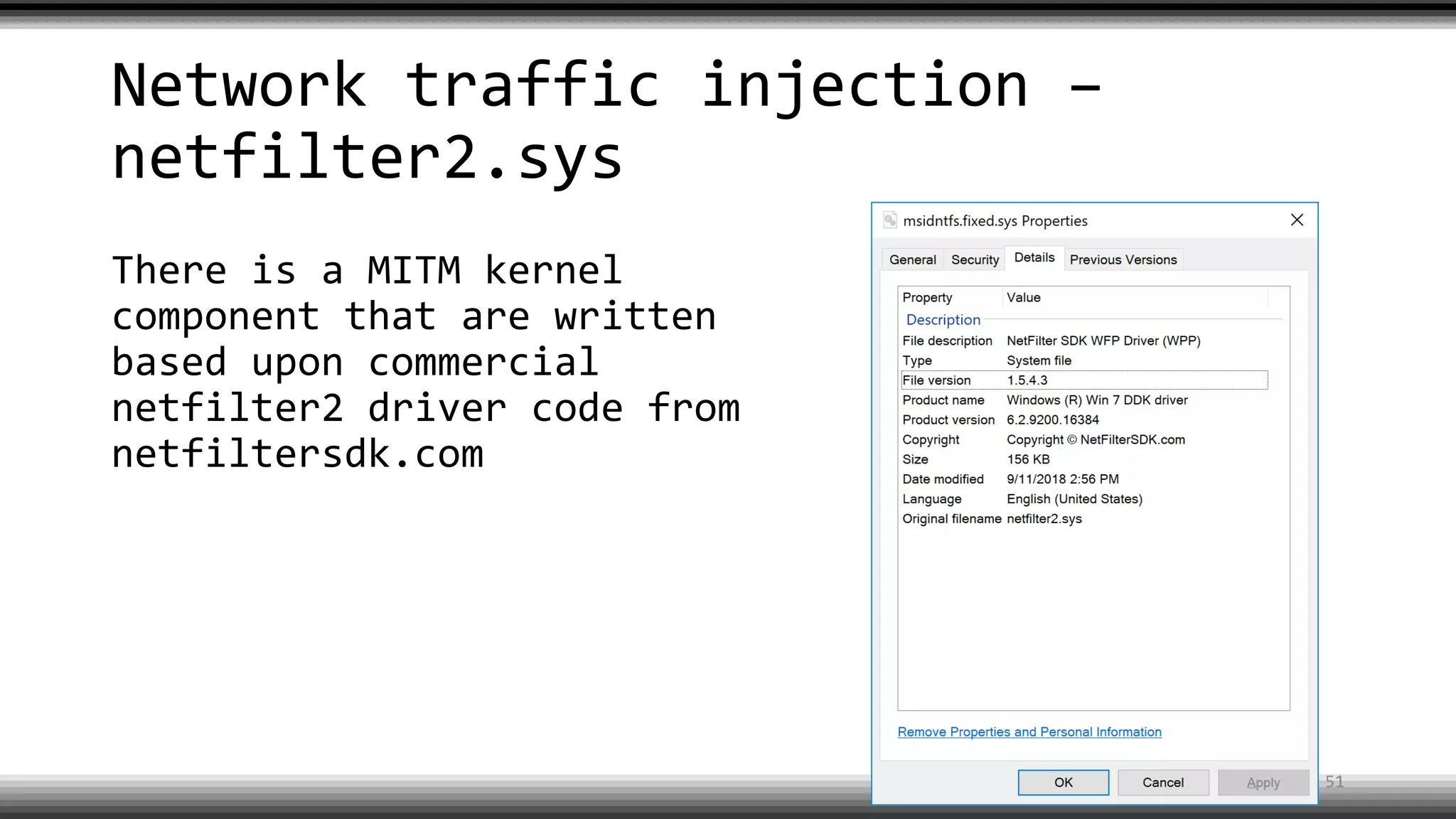
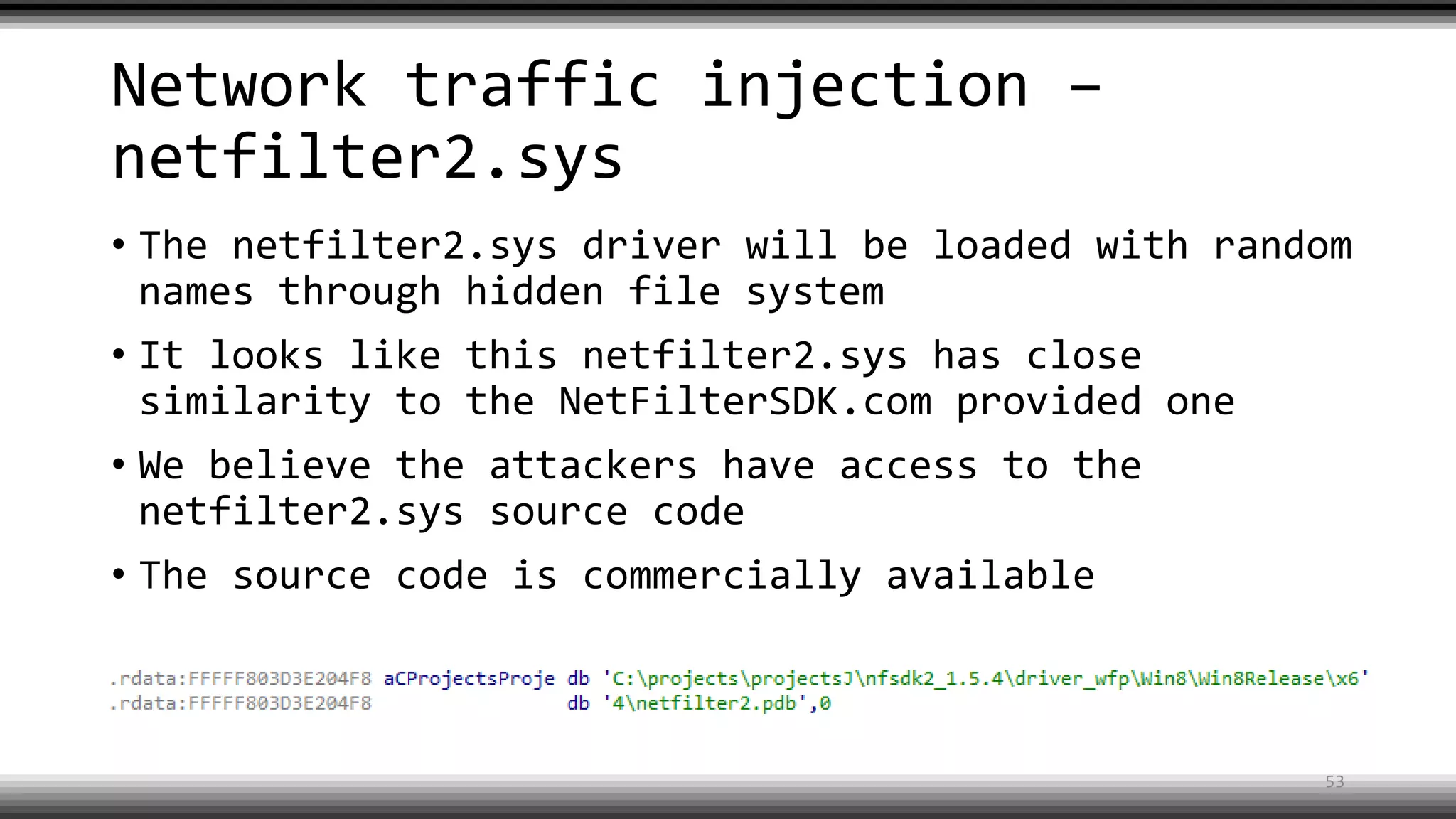
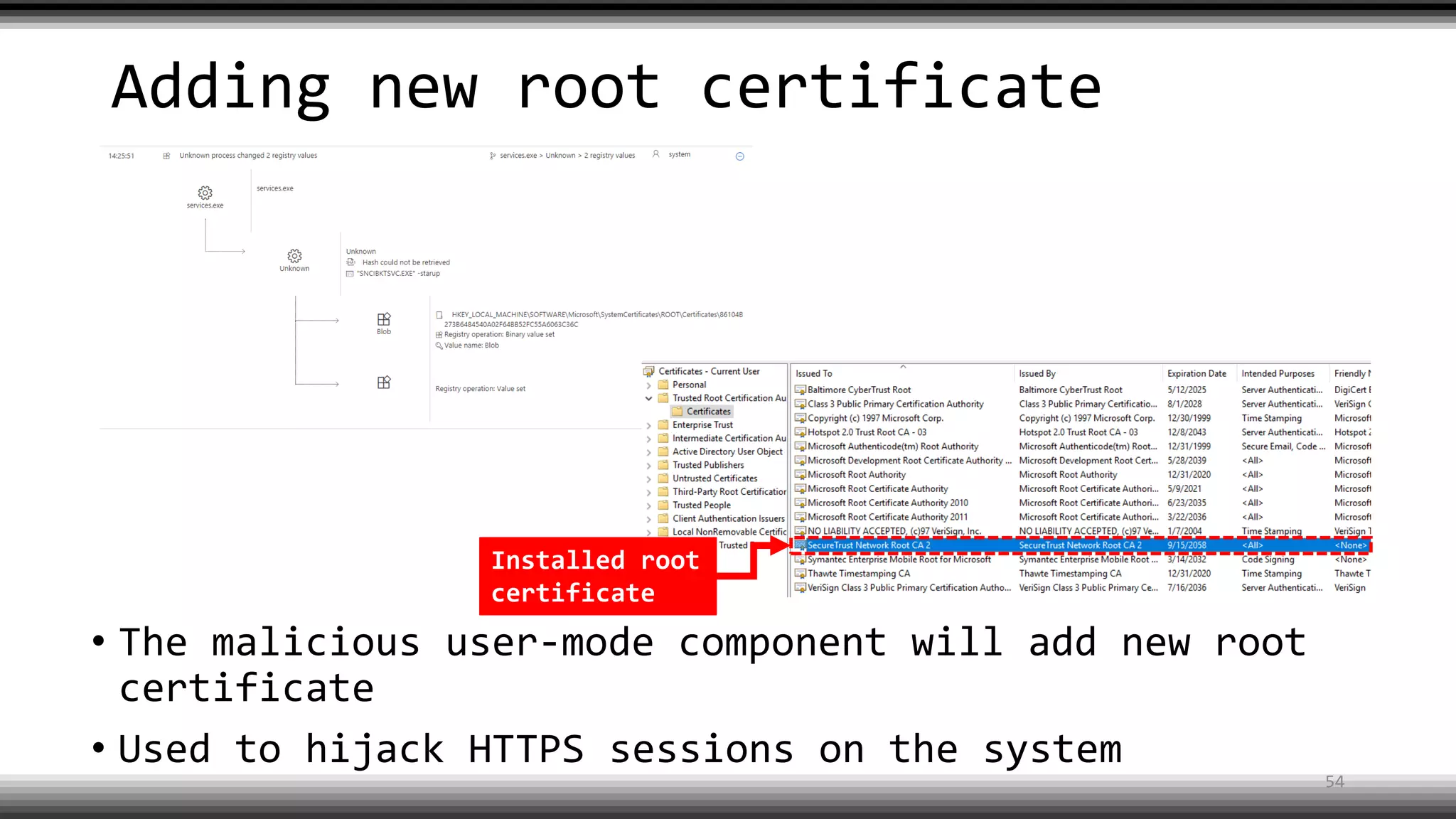
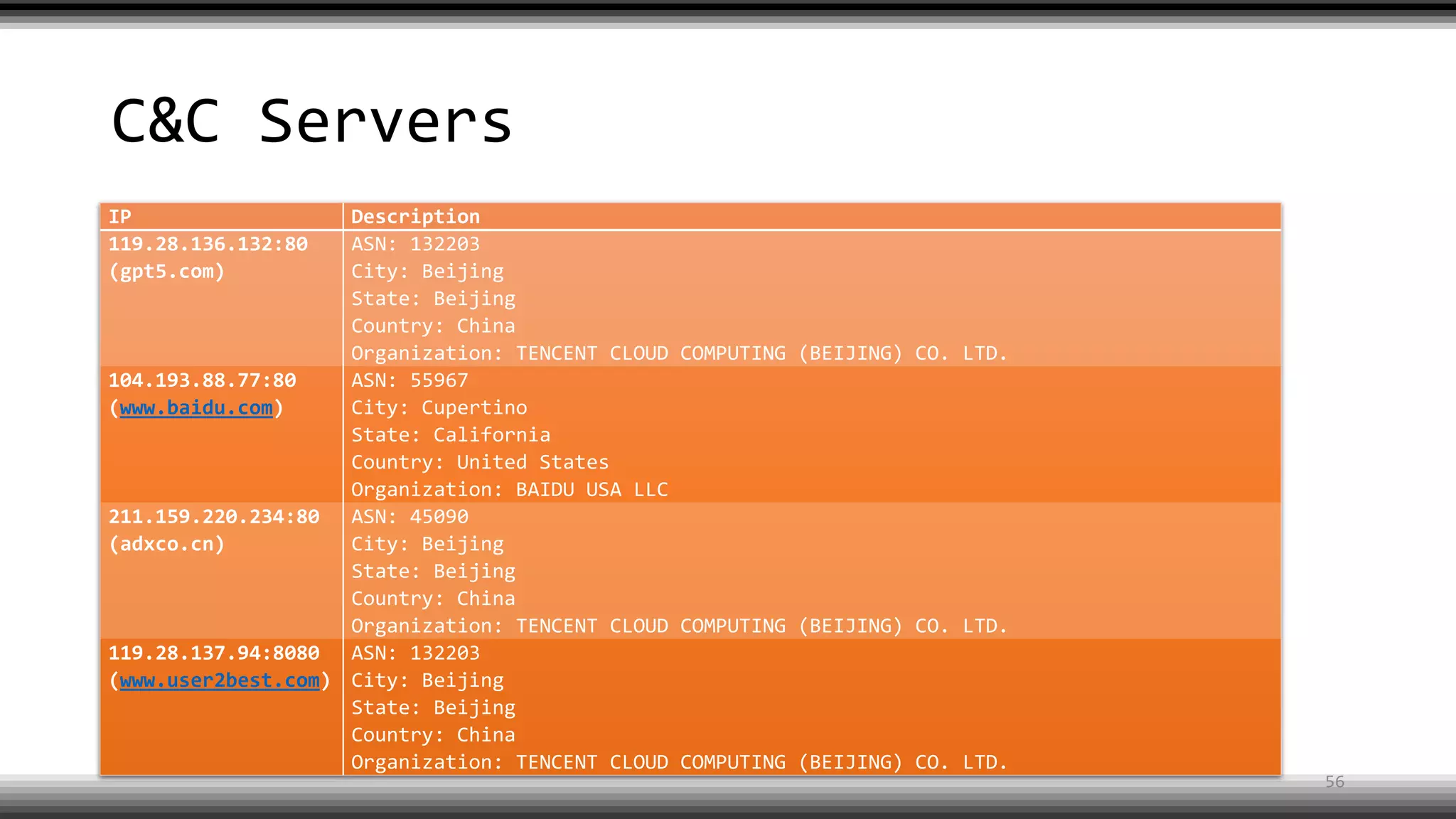
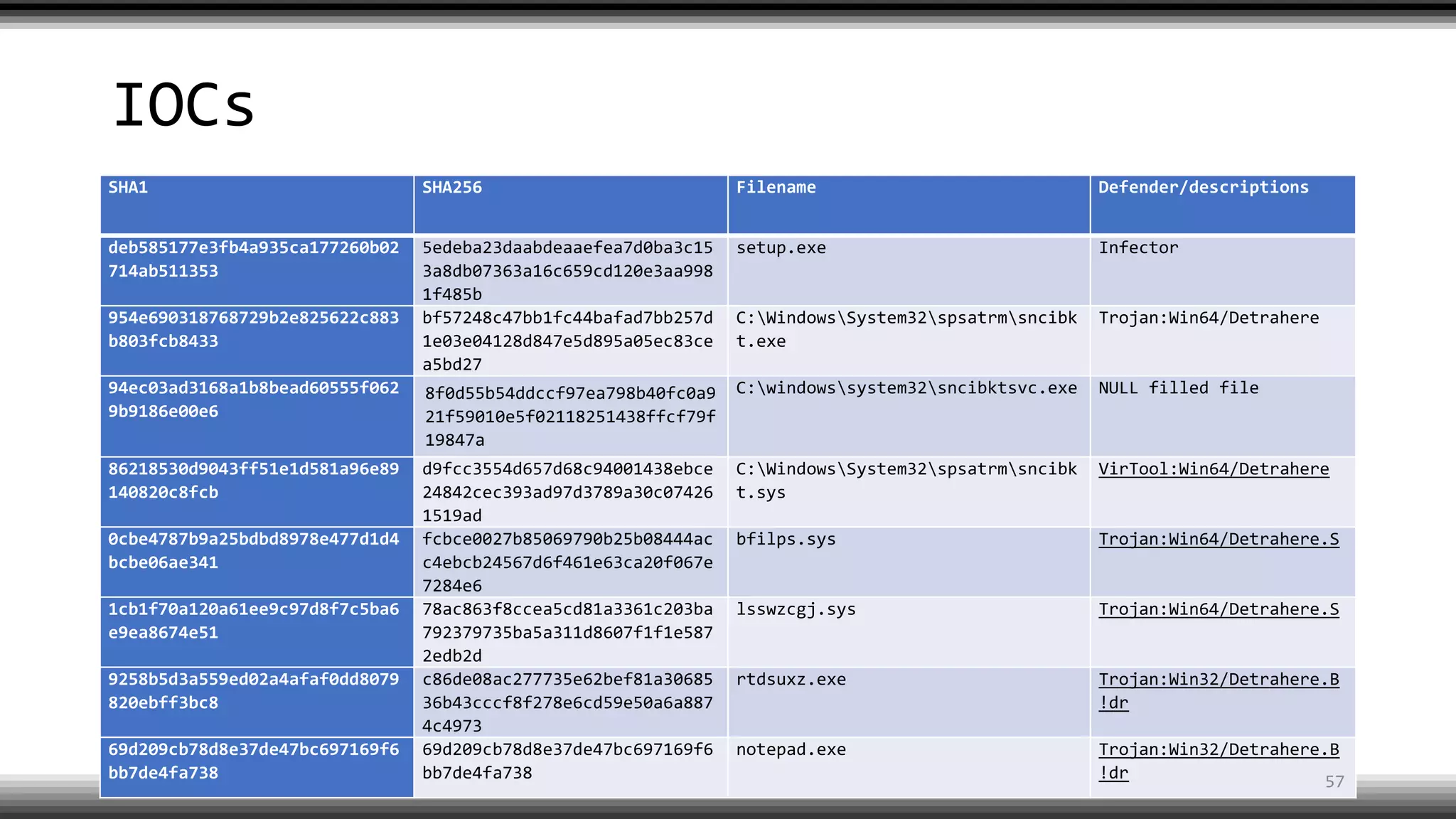
The document discusses the return of kernel rootkit malware, specifically focusing on the Detrahere variant associated with the Zacinlo ad fraud operation. It outlines the malware's stealth mechanisms, propagation methods, and self-protection traits, including the use of a hidden file system and revoked certificates for driver loading. Additionally, it emphasizes the challenges of remediation and detection presented by this advanced threat, while suggesting that Windows Defender can help in mitigating the risks involved.