HIPAA Topology
•
2 likes•251 views
Created by Jason P. Rusch
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
Similar to HIPAA Topology
Similar to HIPAA Topology (7)
Altis Webinar: Pragmatic Data Governance with Azure Data Catalogue

Altis Webinar: Pragmatic Data Governance with Azure Data Catalogue
Pma salehuddin technology and innovation management

Pma salehuddin technology and innovation management
CIP IT Governance 5.0 Solution Guide for ArcSight Logger

CIP IT Governance 5.0 Solution Guide for ArcSight Logger
More from Jason Rusch - CISSP CGEIT CISM CISA GNSA
More from Jason Rusch - CISSP CGEIT CISM CISA GNSA (20)
Information_Governance_Risk_Compliance_Frameworks (v5)

Information_Governance_Risk_Compliance_Frameworks (v5)
Recently uploaded
❤️Chandigarh Escort Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ C...

❤️Chandigarh Escort Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ C...Rashmi Entertainment
❤️Chandigarh Escorts Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ ...

❤️Chandigarh Escorts Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ ...Rashmi Entertainment
Recently uploaded (20)
Delhi Call Girl Service 📞8650700400📞Just Call Divya📲 Call Girl In Delhi No💰Ad...

Delhi Call Girl Service 📞8650700400📞Just Call Divya📲 Call Girl In Delhi No💰Ad...
Independent Call Girls Service Chandigarh | 8868886958 | Call Girl Service Nu...

Independent Call Girls Service Chandigarh | 8868886958 | Call Girl Service Nu...
❤️Chandigarh Escorts☎️9814379184☎️ Call Girl service in Chandigarh☎️ Chandiga...

❤️Chandigarh Escorts☎️9814379184☎️ Call Girl service in Chandigarh☎️ Chandiga...
Call Girls In Indore 📞9235973566📞Just Call Inaaya📲 Call Girls Service In Indo...

Call Girls In Indore 📞9235973566📞Just Call Inaaya📲 Call Girls Service In Indo...
💞 Safe And Secure Call Girls Coimbatore 🧿 9332606886 🧿 High Class Call Girl S...

💞 Safe And Secure Call Girls Coimbatore 🧿 9332606886 🧿 High Class Call Girl S...
❤️Chandigarh Escort Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ C...

❤️Chandigarh Escort Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ C...
💚Chandigarh Call Girls Service 💯Jiya 📲🔝8868886958🔝Call Girls In Chandigarh No...

💚Chandigarh Call Girls Service 💯Jiya 📲🔝8868886958🔝Call Girls In Chandigarh No...
💞 Safe And Secure Call Girls chhindwara 🧿 9332606886 🧿 High Class Call Girl S...

💞 Safe And Secure Call Girls chhindwara 🧿 9332606886 🧿 High Class Call Girl S...
💞 Safe And Secure Call Girls gaya 🧿 9332606886 🧿 High Class Call Girl Service...

💞 Safe And Secure Call Girls gaya 🧿 9332606886 🧿 High Class Call Girl Service...
Call Girls Goa Just Call 9xx000xx09 Top Class Call Girl Service Available

Call Girls Goa Just Call 9xx000xx09 Top Class Call Girl Service Available
Call Girls Service 11 Phase Mohali {7435815124} ❤️ MONA Call Girl in Mohali P...

Call Girls Service 11 Phase Mohali {7435815124} ❤️ MONA Call Girl in Mohali P...
Independent Call Girls Service Chandigarh Sector 17 | 8868886958 | Call Girl ...

Independent Call Girls Service Chandigarh Sector 17 | 8868886958 | Call Girl ...
Call Girls Service Amritsar Just Call 9352988975 Top Class Call Girl Service ...

Call Girls Service Amritsar Just Call 9352988975 Top Class Call Girl Service ...
❤️Chandigarh Escorts Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ ...

❤️Chandigarh Escorts Service☎️9815457724☎️ Call Girl service in Chandigarh☎️ ...
❤️ Zirakpur Call Girl Service ☎️9878799926☎️ Call Girl service in Zirakpur ☎...

❤️ Zirakpur Call Girl Service ☎️9878799926☎️ Call Girl service in Zirakpur ☎...
Low Rate Call Girls Udaipur {9xx000xx09} ❤️VVIP NISHA CCall Girls in Udaipur ...

Low Rate Call Girls Udaipur {9xx000xx09} ❤️VVIP NISHA CCall Girls in Udaipur ...
HIPAA Topology
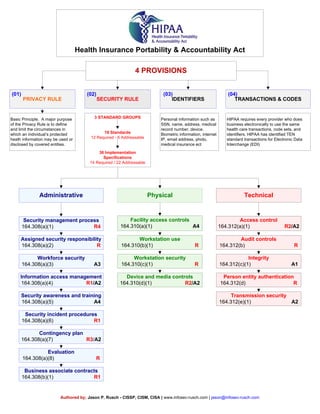
- 1. Health Insurance Portability & Accountability Act 4 PROVISIONS TRANSACTIONS & CODES Administrative Physical Technical PRIVACY RULE SECURITY RULE IDENTIFIERS (04)(03)(02)(01) Basic Principle. A major purpose of the Privacy Rule is to define and limit the circumstances in which an individual’s protected heath information may be used or disclosed by covered entities. Business associate contracts 164.308(b)(1) R1 Evaluation 164.308(a)(8) R Security awareness and training 164.308(a)(5) A4 Workforce security 164.308(a)(3) A3 Assigned security responsibility 164.308(a)(2) R Contingency plan 164.308(a)(7) R3/A2 Security management process 164.308(a)(1) R4 Information access management 164.308(a)(4) R1/A2 Security incident procedures 164.308(a)(6) R1 Transmission security 164.312(e)(1) A2 Person entity authentication 164.312(d) R Access control 164.312(a)(1) R2/A2 Workstation security 164.310(c)(1) R Workstation use 164.310(b)(1) R Integrity 164.312(c)(1) A1 Facility access controls 164.310(a)(1) A4 Device and media controls 164.310(d)(1) R2/A2 Audit controls 164.312(b) R Personal information such as SSN, name, address, medical record number, device. Biometric information, internet IP, email address, photo, medical insurance ect HIPAA requires every provider who does business electronically to use the same health care transactions, code sets, and identifiers. HIPAA has identified TEN standard transactions for Electronic Data Interchange (EDI) Authored by; Jason P. Rusch - CISSP, CISM, CISA | www.infosec-rusch.com | jason@infosec-rusch.com 3 STANDARD GROUPS 18 Standards 12 Required - 6 Addressable 36 Implementation Specifications 14 Required / 22 Addressable
