Cyberdefense in depth with validy technology
•
0 likes•93 views
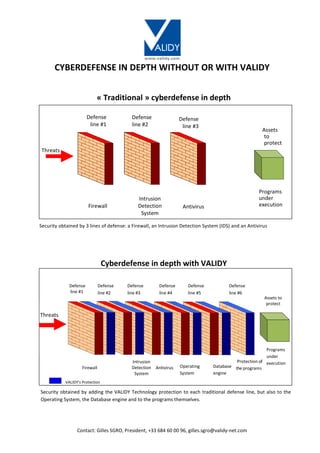
The document describes traditional cyberdefense in depth which uses three lines of defense: a firewall, intrusion detection system, and antivirus programs. It then describes cyberdefense with Validy, which adds Validy's protection technology to each traditional defense line, the operating system, database engine, and programs themselves, providing six total lines of defense. Validy's president Gilles Sgro can be contacted at the provided phone number and email for more information.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
What endpoint protection solutions are available on the market today?

What endpoint protection solutions are available on the market today?
Best Information Security Tips for Better Computing

Best Information Security Tips for Better Computing
Re solution - corona virus cyber security infographic

Re solution - corona virus cyber security infographic
Top 10 Reasons to Learn Cybersecurity | Why Cybersecurity is Important | Edureka

Top 10 Reasons to Learn Cybersecurity | Why Cybersecurity is Important | Edureka
Network Security - Defense Through Layered Information Security

Network Security - Defense Through Layered Information Security
F5 Networks- Why Legacy Security Systems are Failing

F5 Networks- Why Legacy Security Systems are Failing
Viewers also liked
Viewers also liked (11)
Jual implant removal kit 2015~produk juknis dak bkkbn 2015 cv.asaka prima

Jual implant removal kit 2015~produk juknis dak bkkbn 2015 cv.asaka prima
Similar to Cyberdefense in depth with validy technology
Similar to Cyberdefense in depth with validy technology (20)
JS Fest 2019. Анастасия Войтова. "Defense in depth": trench warfare principle...

JS Fest 2019. Анастасия Войтова. "Defense in depth": trench warfare principle...
Fidelis - Live Demonstration of Deception Solution

Fidelis - Live Demonstration of Deception Solution
Cybersecurity Concerns You Should be Thinking About

Cybersecurity Concerns You Should be Thinking About
More from Gilles Sgro
More from Gilles Sgro (20)
Validy lettre-dpsd-colonel-bourguignon-27-dec-2006

Validy lettre-dpsd-colonel-bourguignon-27-dec-2006
Validy lettre-dpsd-colonel-bourguignon-15-fev-2007

Validy lettre-dpsd-colonel-bourguignon-15-fev-2007
Validy 171 signataires lettre au président, aux députés, aux sénateurs et à...

Validy 171 signataires lettre au président, aux députés, aux sénateurs et à...
Courrier du chef de cabinet du président de la république du 8 aout 2012

Courrier du chef de cabinet du président de la république du 8 aout 2012
Lettre recue le 9 nov 2012 du chef de cabinet du président de la république

Lettre recue le 9 nov 2012 du chef de cabinet du président de la république
Lettre recue fleur pellerin 14 sept 2012 - recu le 1 er octobre 2012

Lettre recue fleur pellerin 14 sept 2012 - recu le 1 er octobre 2012
Secrétaire général elyséee macron - lettre - 4 octobre 2012

Secrétaire général elyséee macron - lettre - 4 octobre 2012
Secrétaire général elyséee macron - note -4 octobre 2012

Secrétaire général elyséee macron - note -4 octobre 2012
Rapport senateur bockel surligné cyber defense - 19 juillet 2012

Rapport senateur bockel surligné cyber defense - 19 juillet 2012
Autorité de la concurrence retrait de la plainte - bruno lasserre - 6 mars ...

Autorité de la concurrence retrait de la plainte - bruno lasserre - 6 mars ...
Cyberdefense in depth with validy technology
- 1. www.validy.com Contact: Gilles SGRO, President, +33 684 60 00 96, gilles.sgro@validy-net.com CYBERDEFENSE IN DEPTH WITHOUT OR WITH VALIDY « Traditional » cyberdefense in depth Defense line #1 Defense line #2 Defense line #3 Assets to protect Threats Firewall Intrusion Detection System Antivirus Programs under execution Security obtained by 3 lines of defense: a Firewall, an Intrusion Detection System (IDS) and an Antivirus Cyberdefense in depth with VALIDY Threats Defense line #1 Defense line #2 Defense line #3 Defense line #4 Defense line #5 Defense line #6 Assets to protect Firewall VALIDY’s Protection Intrusion Detection System Antivirus Operating System Database engine Protection of the programs Programs under execution Security obtained by adding the VALIDY Technology protection to each traditional defense line, but also to the Operating System, the Database engine and to the programs themselves.