Infographic Mtrends EMEA 2016
•
0 likes•280 views
In 2015, FireEye responded to some of the most high profile breaches in Europe, Middle East and Africa (EMEA). During these investigations consultants from Mandiant, a FireEye company, collected data and details on leading cyber trends and threat actor tactics used to compromise businesses and steal data. View the infographic for a quick snapshot of the statistics, trends and lessons learned from these data breach investigations. For more information on Mandiant consulting services, visit www.fireeye.com/services.html.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
Viewers also liked
Viewers also liked (12)
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
Keynote Session : Internet Of Things (IOT) Security Taskforce

Keynote Session : Internet Of Things (IOT) Security Taskforce
How to Replace Your Legacy Antivirus Solution with CrowdStrike

How to Replace Your Legacy Antivirus Solution with CrowdStrike
More from FireEye, Inc.
More from FireEye, Inc. (12)
[Infographic] Healthcare Cyber Security: Threat Prognosis![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Healthcare Cyber Security: Threat Prognosis
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
FireEye Advanced Threat Protection - What You Need to Know

FireEye Advanced Threat Protection - What You Need to Know
Recently uploaded
Recently uploaded (20)
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Infographic Mtrends EMEA 2016
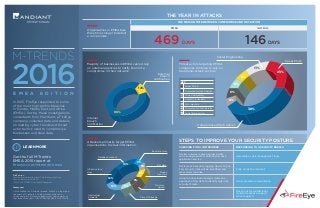
- 1. SPECIAL REPORT / M-TRENDS EMEA EDITION 2016 1 CHECKING FOR A COMPROMISE RESPONDING TO A SECURITY BREACH Review network ingress/egress points and use appropriate monitoring on each application service. Assemble a crisis management team. Review each security logging device to see how security risks will be identified and what alerts look like. Fully scope the incident. Adopt a behavioural analysis detection approach of log data to identify high-risk security threats. Avoid premature remediation. Reach out for professional incident response support when required. STEPS TO IMPROVE YOUR SECURITY POSTURE THE YEAR IN ATTACKS Organisations in EMEA take three times longer to detect a compromise. THE MEDIAN TIME BETWEEN COMPROMISE AND DETECTION EMEA GLOBAL 469 DAYS 146 DAYS In 2015, FireEye responded to some of the most high profile breaches in Europe, Middle East and Africa (EMEA). During these investigations consultants from Mandiant, a FireEye company, collected data and details on leading cyber trends and threat actor tactics used to compromise businesses and steal data. M-TRENDS 2016E M E A E D I T I O N Threat actors targeting EMEA companies continue to rely on traditional attack vectors. KEY Spear Phish Compromised Web Server Citrix Vulnerability Default Credentials SQL Injection Compromised Mail Server Social Engineering LEARN MORE Get the full M-Trends EMEA 2016 report at fireeye.com/mtrends-emea 38% 25% 13% 6% 6% 6% 6% Spear Phish Social Engineering Compromised Web Server Majority of businesses in EMEA cannot rely on external agencies to notify them of a compromise in their network. Internal breach notification External breach notification 12% 88% Attackers primarily target EMEA organisations to steal information. 19% 18% 18% Database content Infrastructure docs Intellectual property 9% 9% 9% 9% Sensitive docs PCI data Money transfers Memory dump Cisco IOS image 9% FireEye, Inc. Reading International Business Park, Basingstoke Road Reading, Berkshire, RG2 6DA +44(0) 203 747 5600 / europe@fireeye.com fireeye.com © 2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.MTRENDSEMEA.EN-UK.072016
