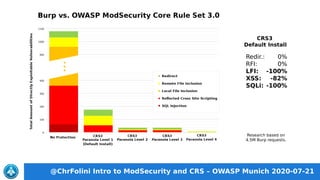
This document discusses ModSecurity and the OWASP Core Rule Set (CRS). ModSecurity is an open source web application firewall that can be embedded into servers. It uses rules to provide granular control over requests and responses. The CRS is a set of generic rules that can block 80% of common web attacks in its default configuration with minimal false positives. It is organized into different rule groups and has different paranoia levels to control security and false positives. The presentation demonstrates how to install and configure ModSecurity and CRS to provide a first line of defense against web application attacks.