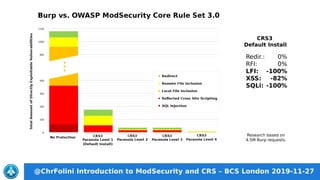
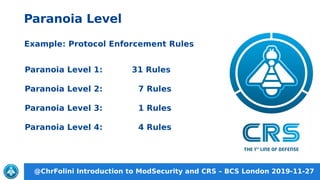
This document provides an introduction to ModSecurity and the OWASP Core Rule Set (CRS) presented by Christian Folini. The presentation covers what a web application firewall (WAF) and ModSecurity are, an overview of the CRS including rule groups and paranoia levels, how to install and configure ModSecurity with the CRS, and handling false positives. The goal of ModSecurity and CRS is to provide a first line of defense against web application attacks and block around 80% of attacks with minimal false positives in the default installation.