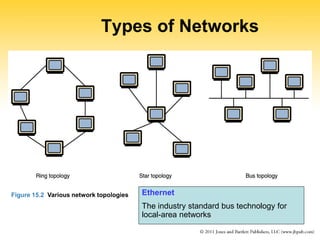
This document provides an overview of computer networks and networking concepts. It discusses network topologies including local area networks, wide area networks, and the internet. It describes addressing using IP addresses and domain names. It explains how messages are delivered over networks using packet switching and protocols like TCP and UDP. The document also discusses network security issues and solutions like firewalls.