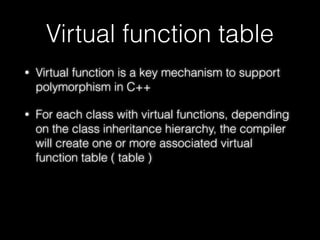
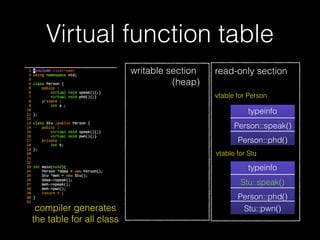
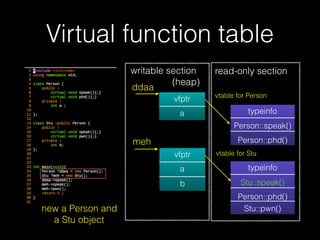
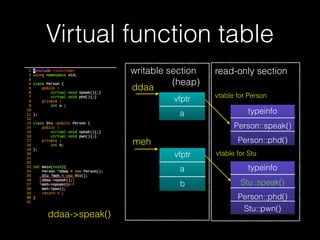
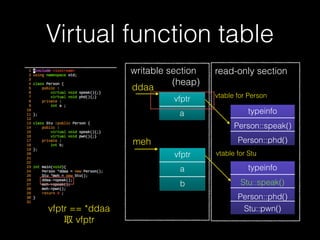
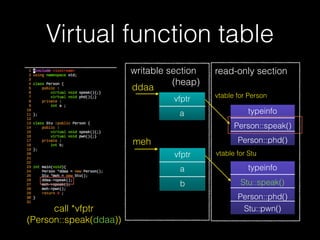
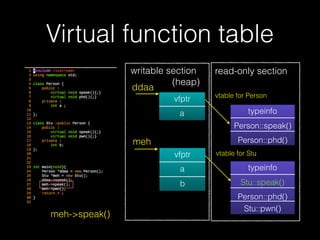
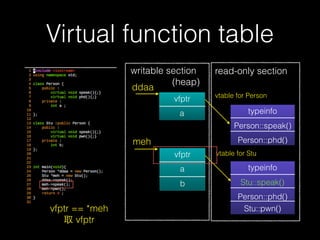
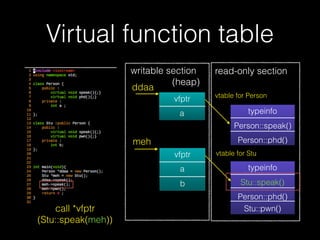
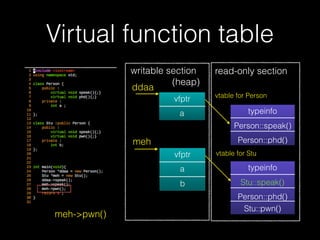
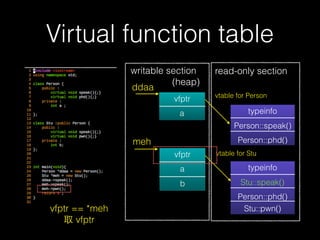
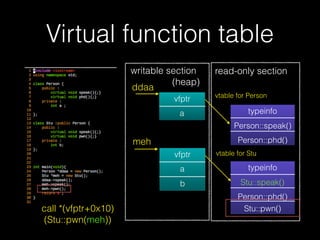
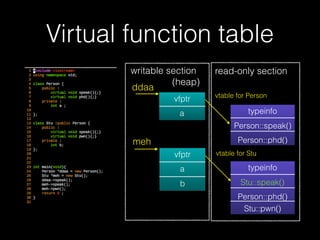
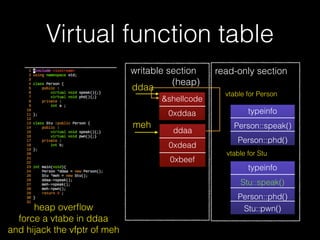
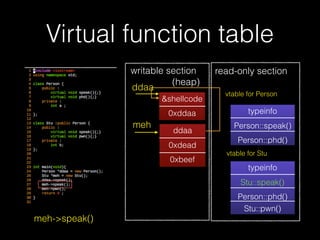
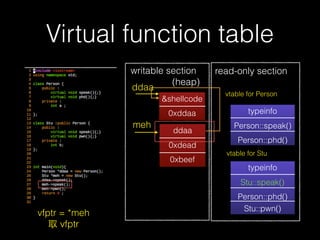
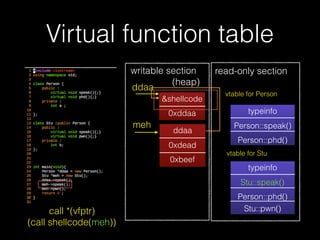
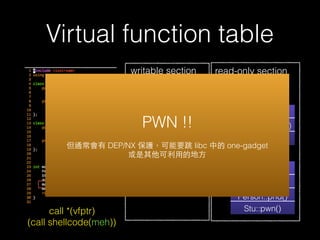
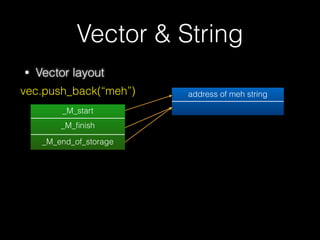
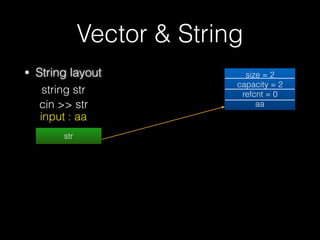
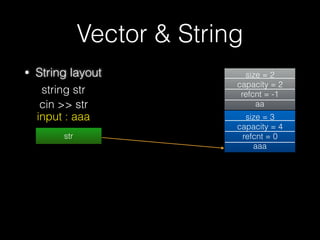
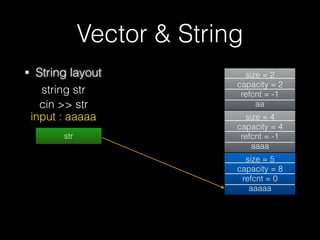
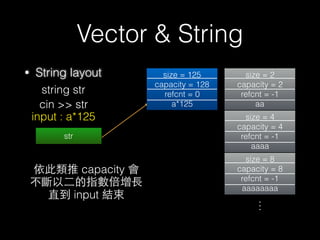
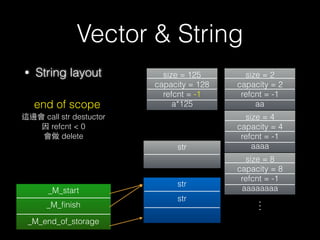
The document discusses C++ exploitation techniques including name mangling, virtual function tables, vtable hijacking, vectors, strings, and memory allocation/deallocation functions like new and delete. It provides details on how virtual function tables are used to implement polymorphism in C++ and how vtable hijacking can be used to exploit vulnerabilities by forcing a vtable and hijacking the virtual function pointer to call shellcode. It also explains how vectors and strings are implemented dynamically in memory and their memory layout.







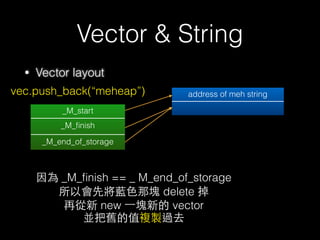
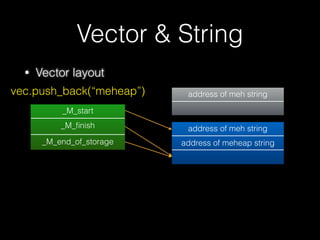
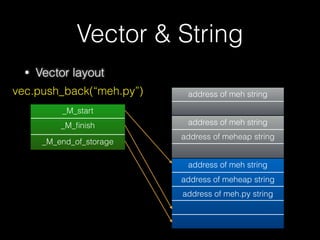
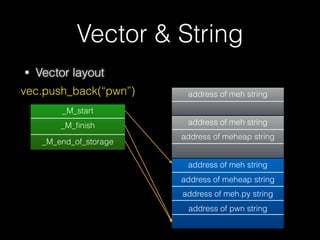


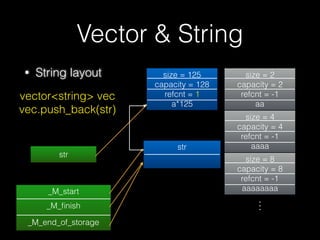
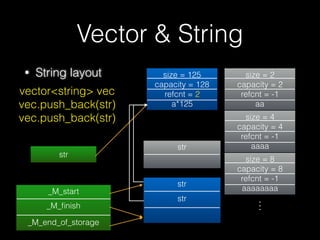
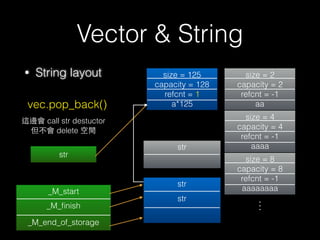
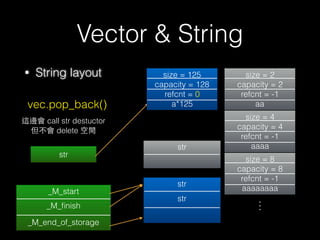






![New & Delete
• 因此 new/delete 及 operator new / operator
delete 也應該成對配對
• 記憶體函式配對
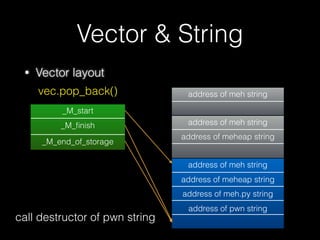
59
配置函式 解除函式
new delete
new [] delete []
operator new operator delete
operator new[] operator delete[]
malloc free](https://image.slidesharecdn.com/pwnincplusplus-160217120850/85/Pwning-in-c-basic-59-320.jpg)


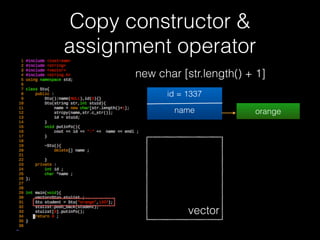
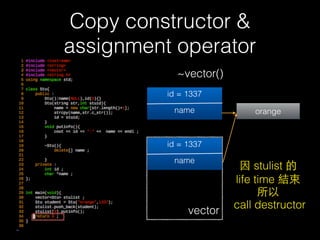


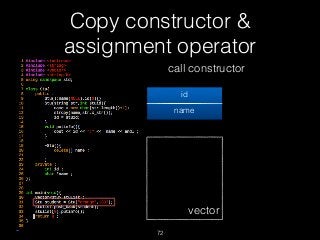
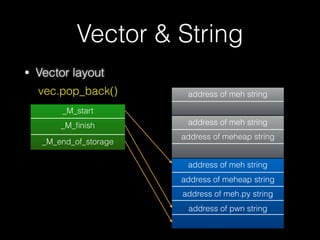
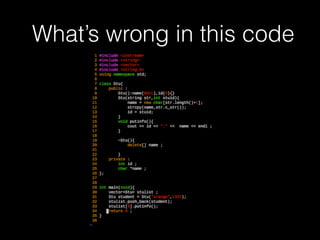
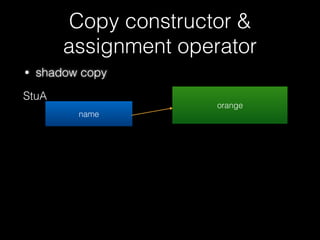
![Copy constructor &
assignment operator
73
new char [str.length() + 1]
id = 1337
name orange
vector](https://image.slidesharecdn.com/pwnincplusplus-160217120850/85/Pwning-in-c-basic-73-320.jpg)
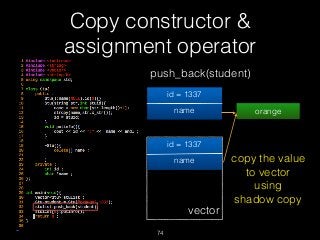
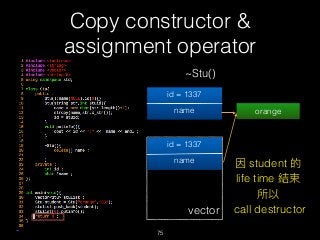
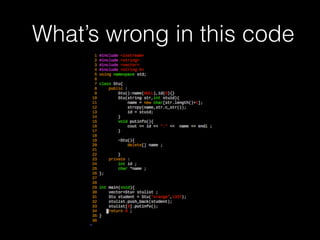
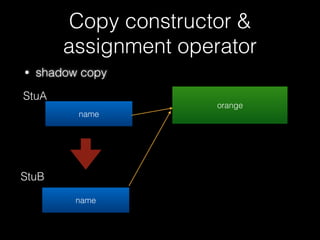
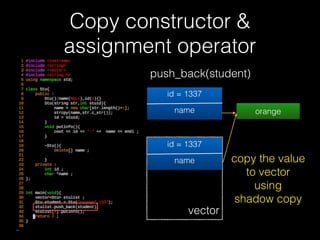
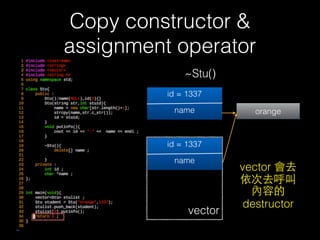
![Copy constructor &
assignment operator
76
delete [] name
id = 1337
name orange
vector
id = 1337
name](https://image.slidesharecdn.com/pwnincplusplus-160217120850/85/Pwning-in-c-basic-76-320.jpg)
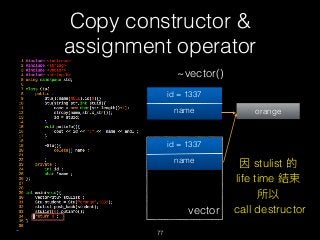
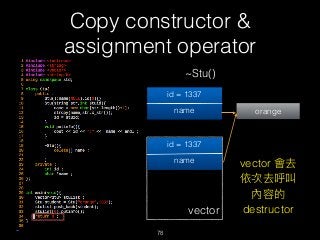
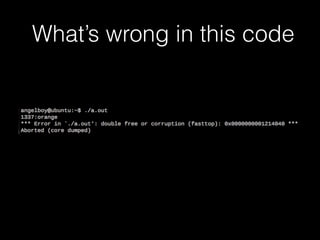
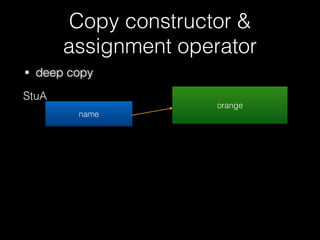
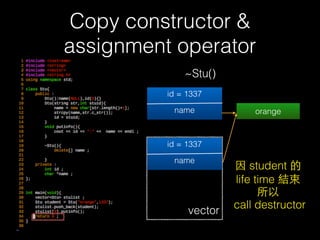
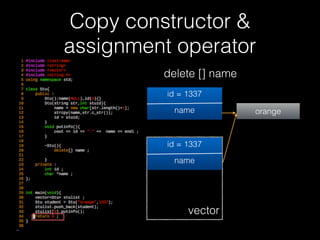
![Copy constructor &
assignment operator
79
delete [] name
id = 1337
name orange
vector
id = 1337
name](https://image.slidesharecdn.com/pwnincplusplus-160217120850/85/Pwning-in-c-basic-79-320.jpg)
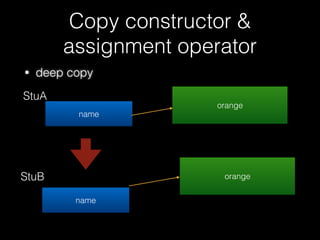
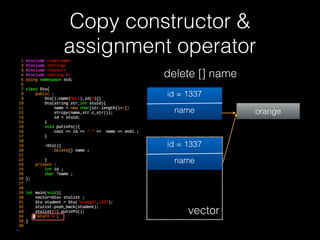
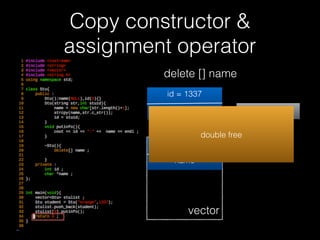
![Copy constructor &
assignment operator
80
delete [] name
id = 1337
name orange
vector
id = 1337
name
double free](https://image.slidesharecdn.com/pwnincplusplus-160217120850/85/Pwning-in-c-basic-80-320.jpg)