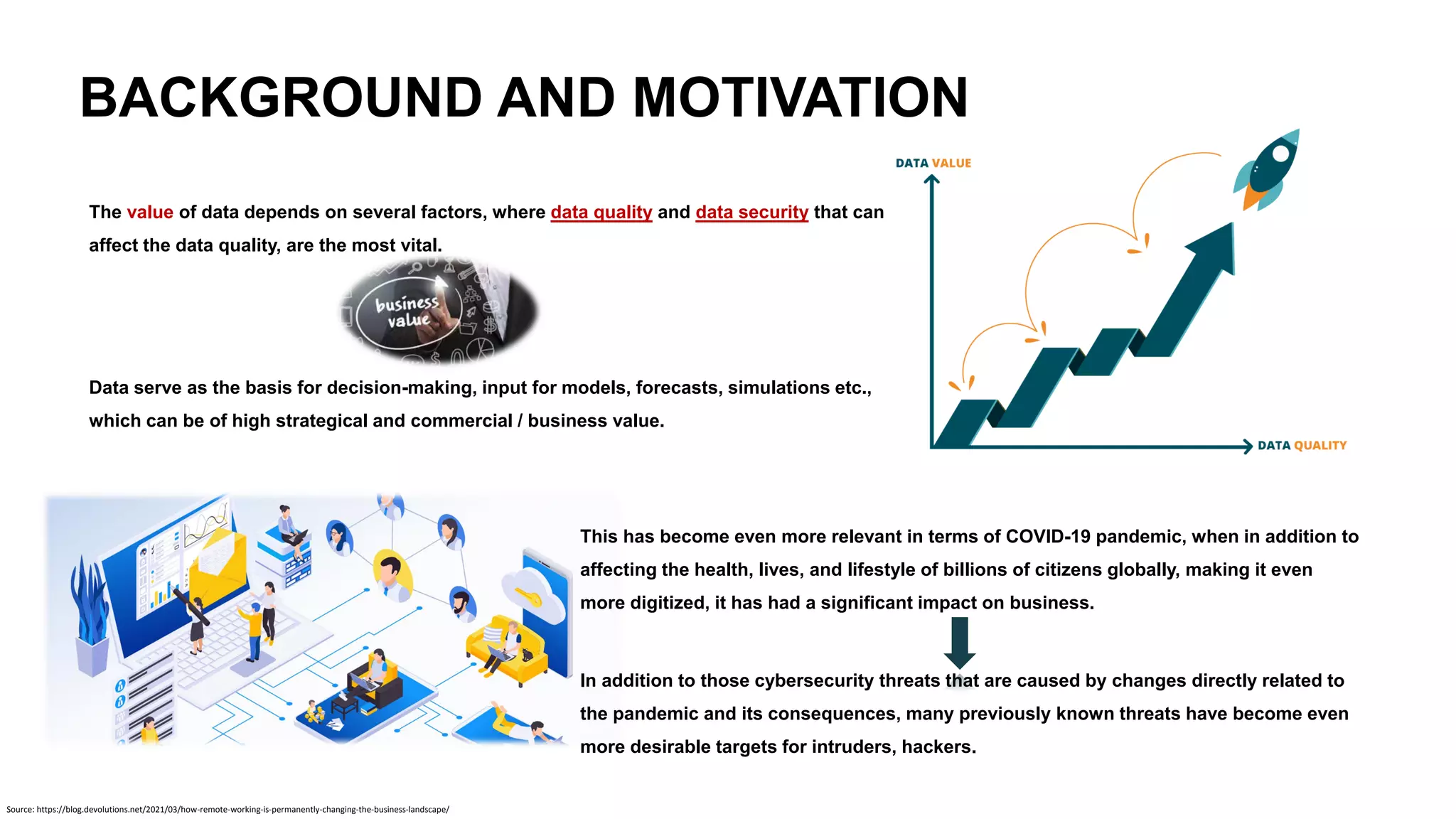
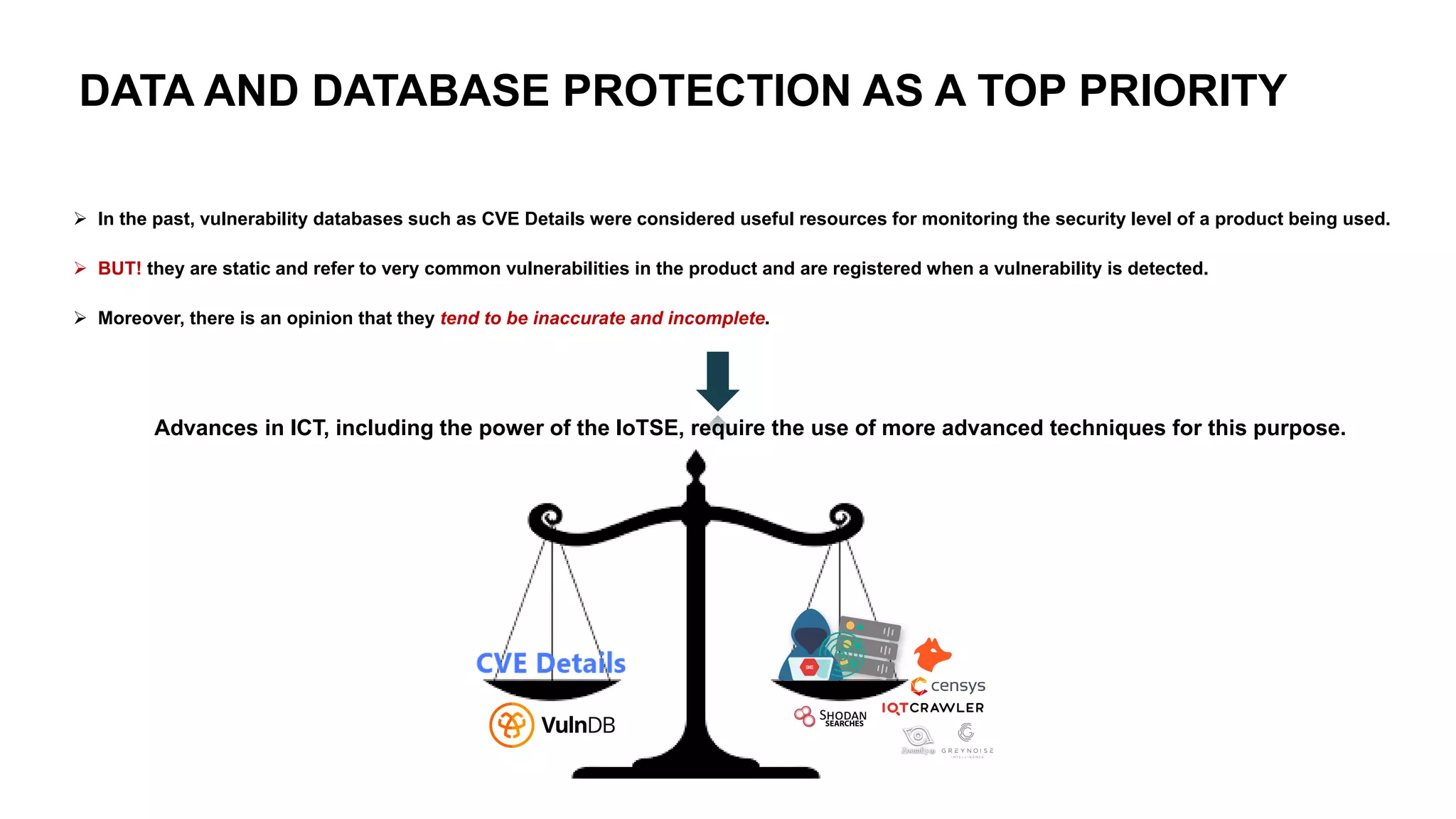
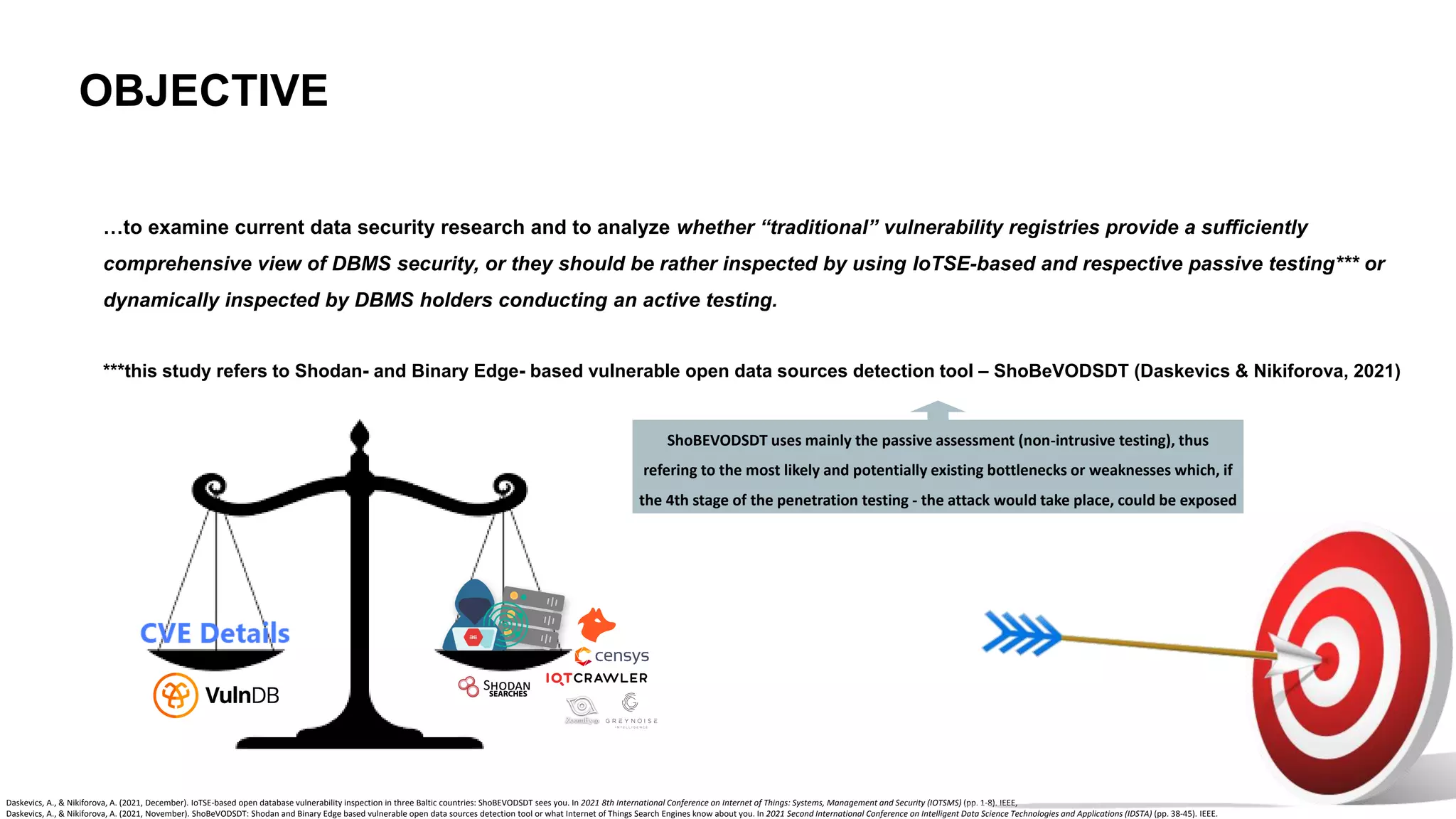
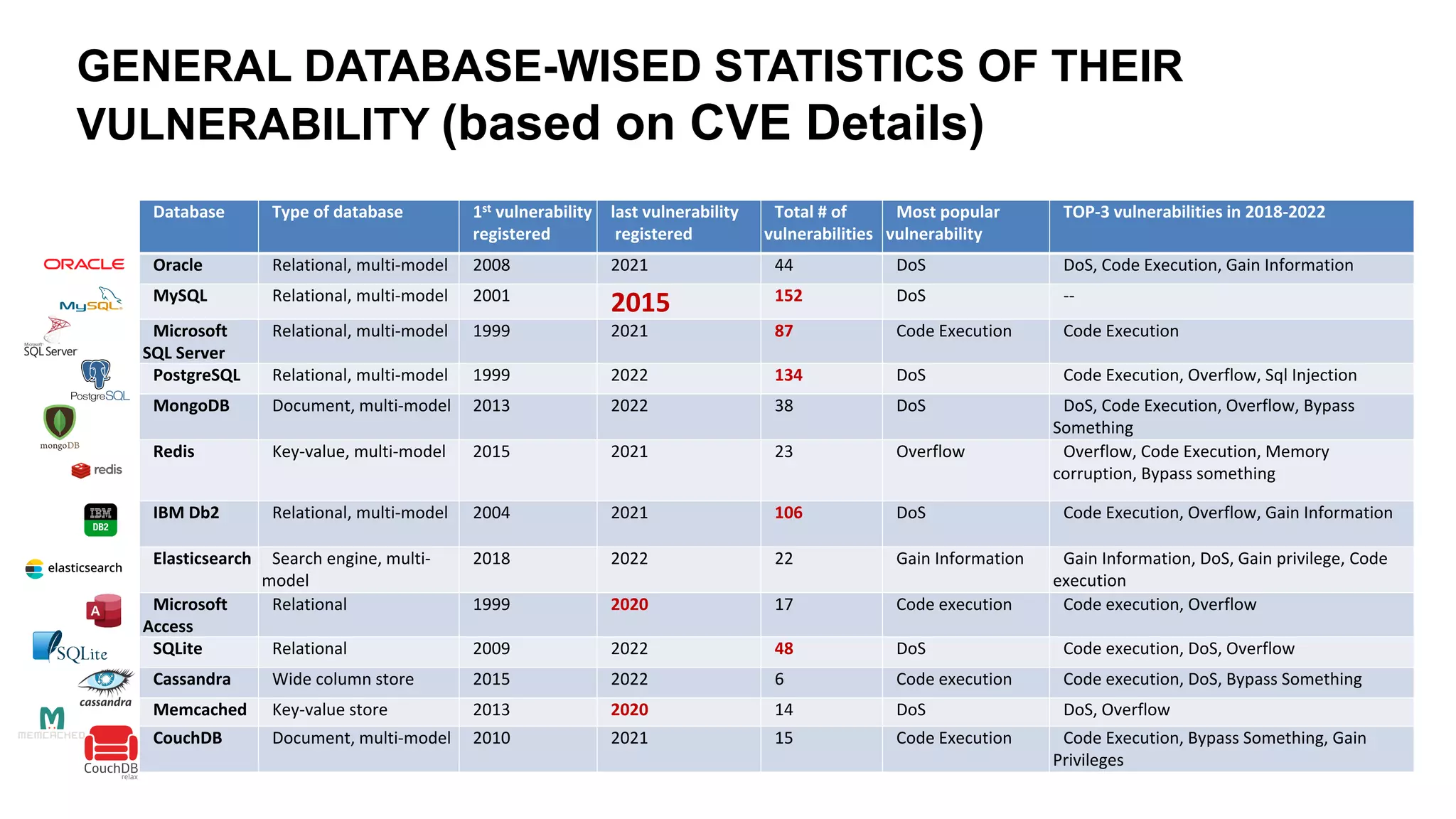
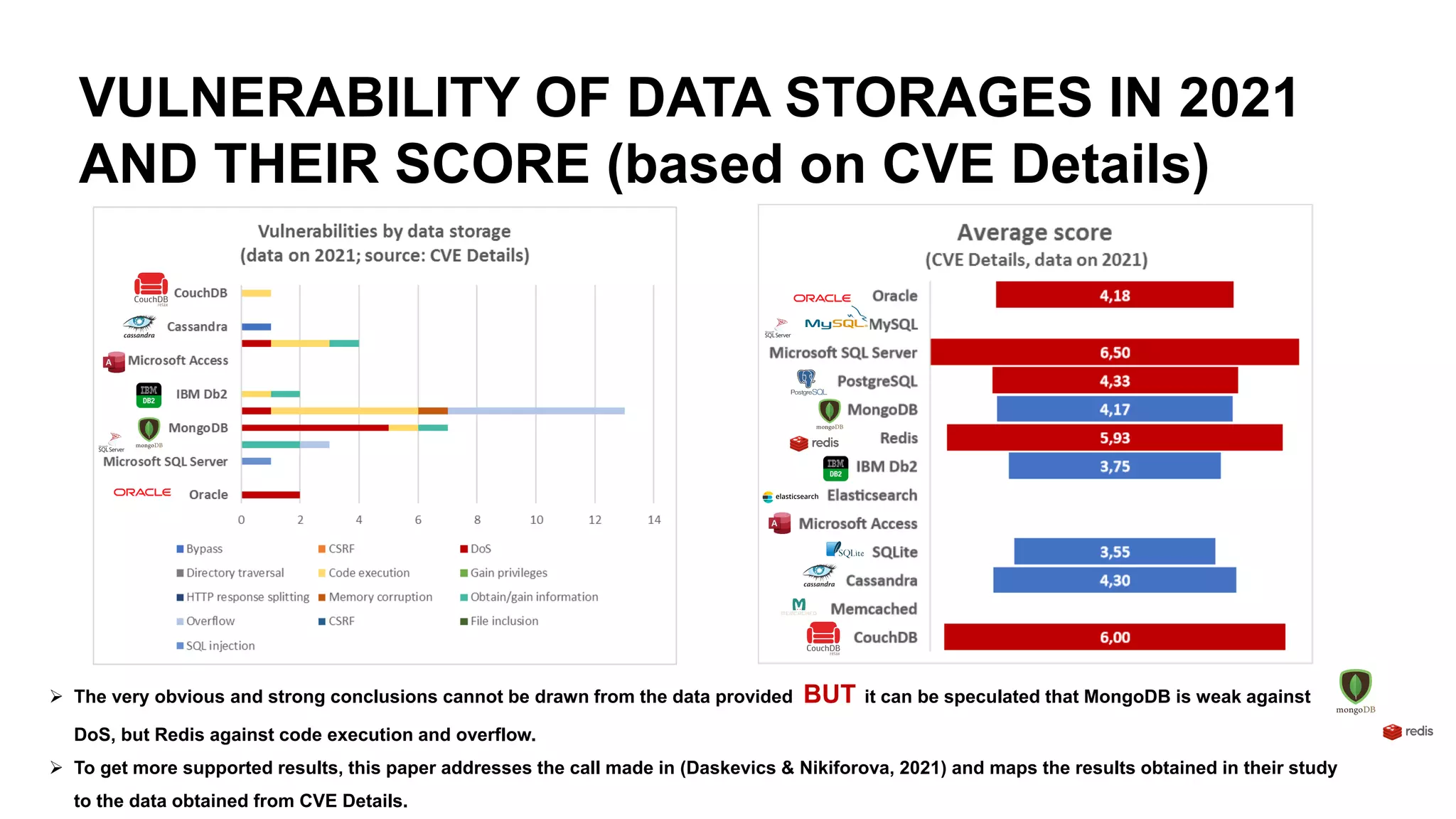
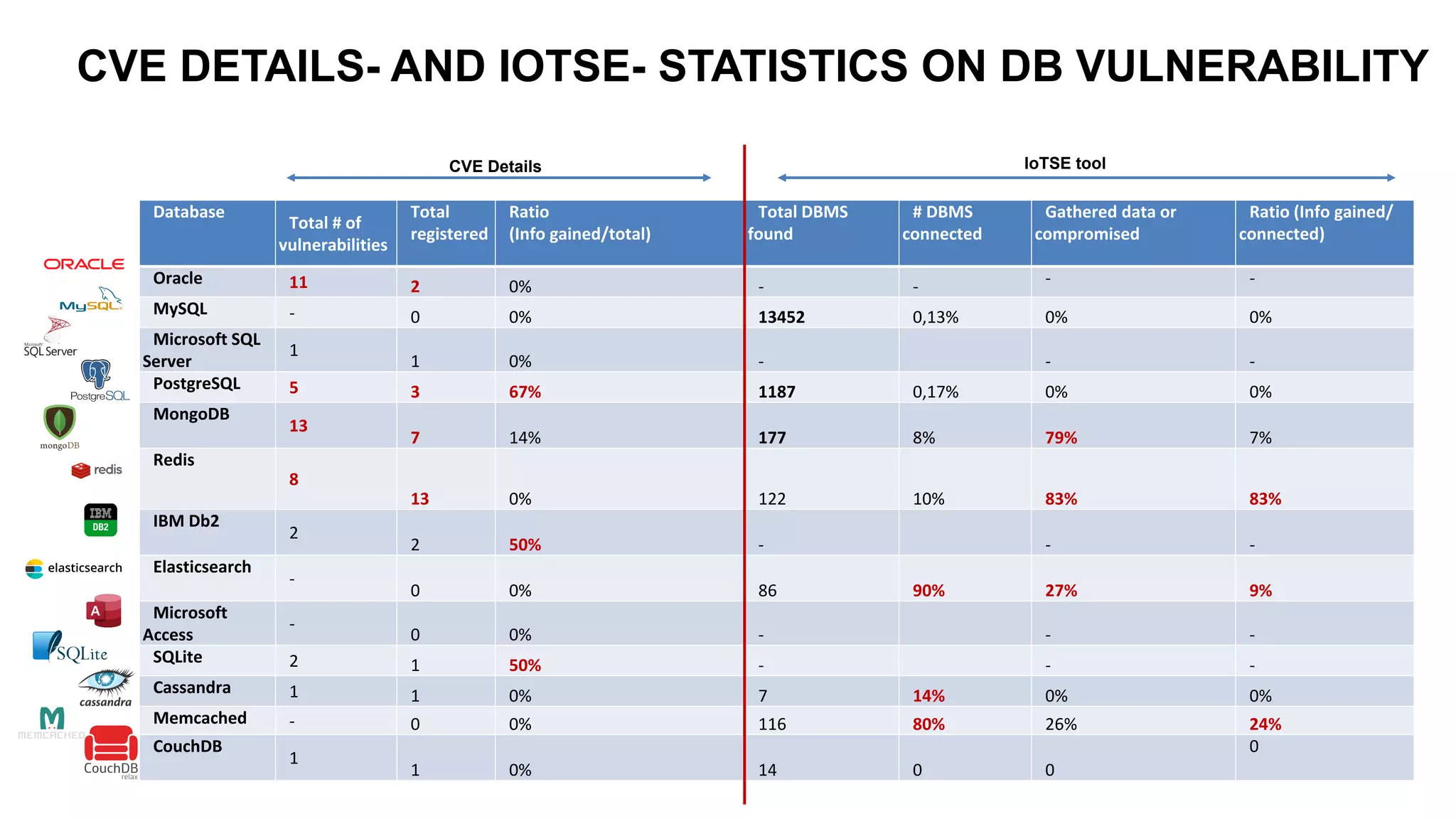
The document emphasizes the critical importance of data security in the context of increasing cyber threats, particularly exacerbated by the COVID-19 pandemic, which has shifted many activities into the digital realm. It highlights the rising numbers of cybersecurity issues, including significant increases in phishing attacks and data breaches, and critiques current vulnerability registries for their inadequacy in reflecting the true security status of databases. The findings suggest that comprehensive and dynamic security measures, including better education on digital hygiene, are essential for protecting data and mitigating risks.