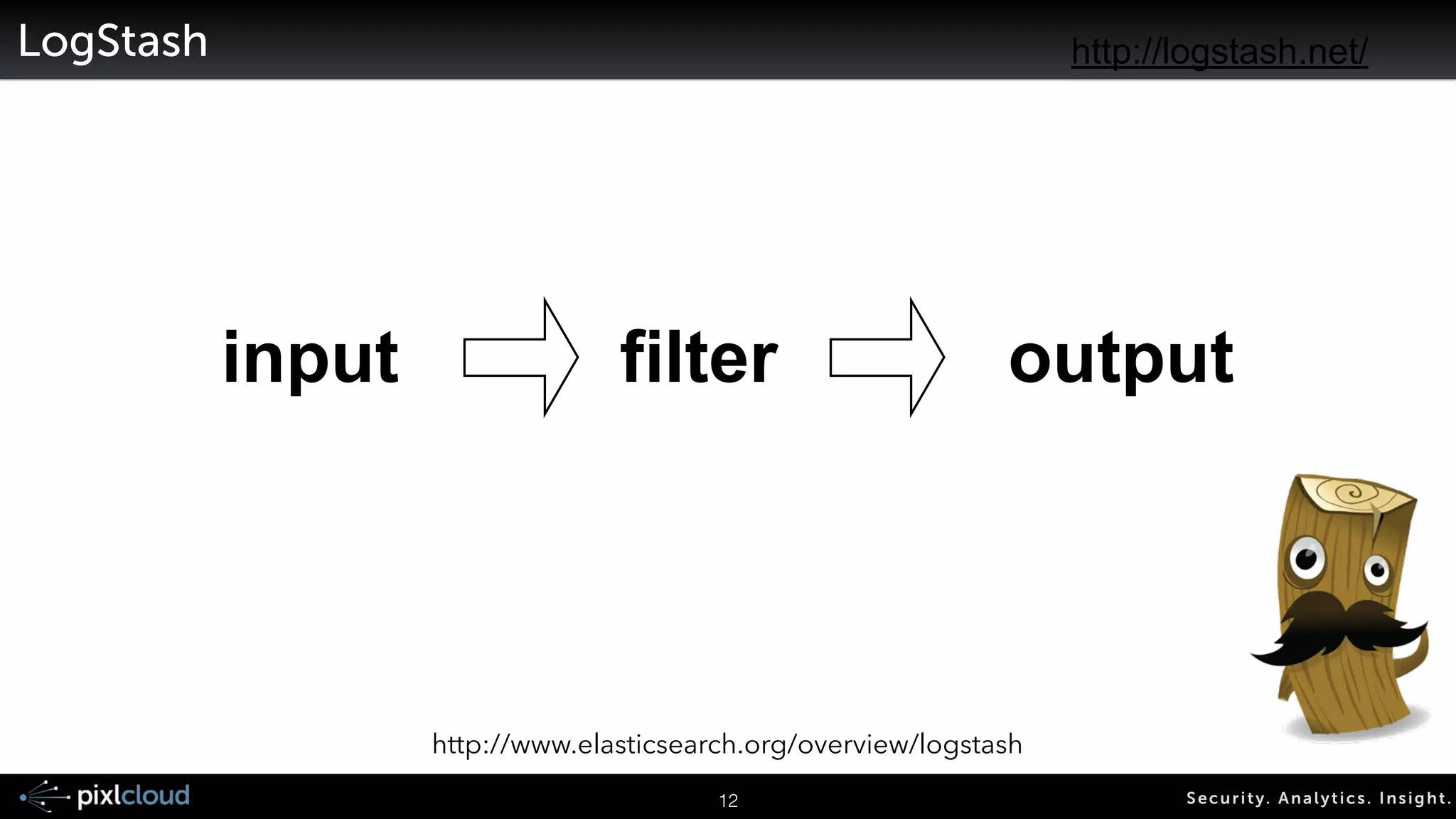
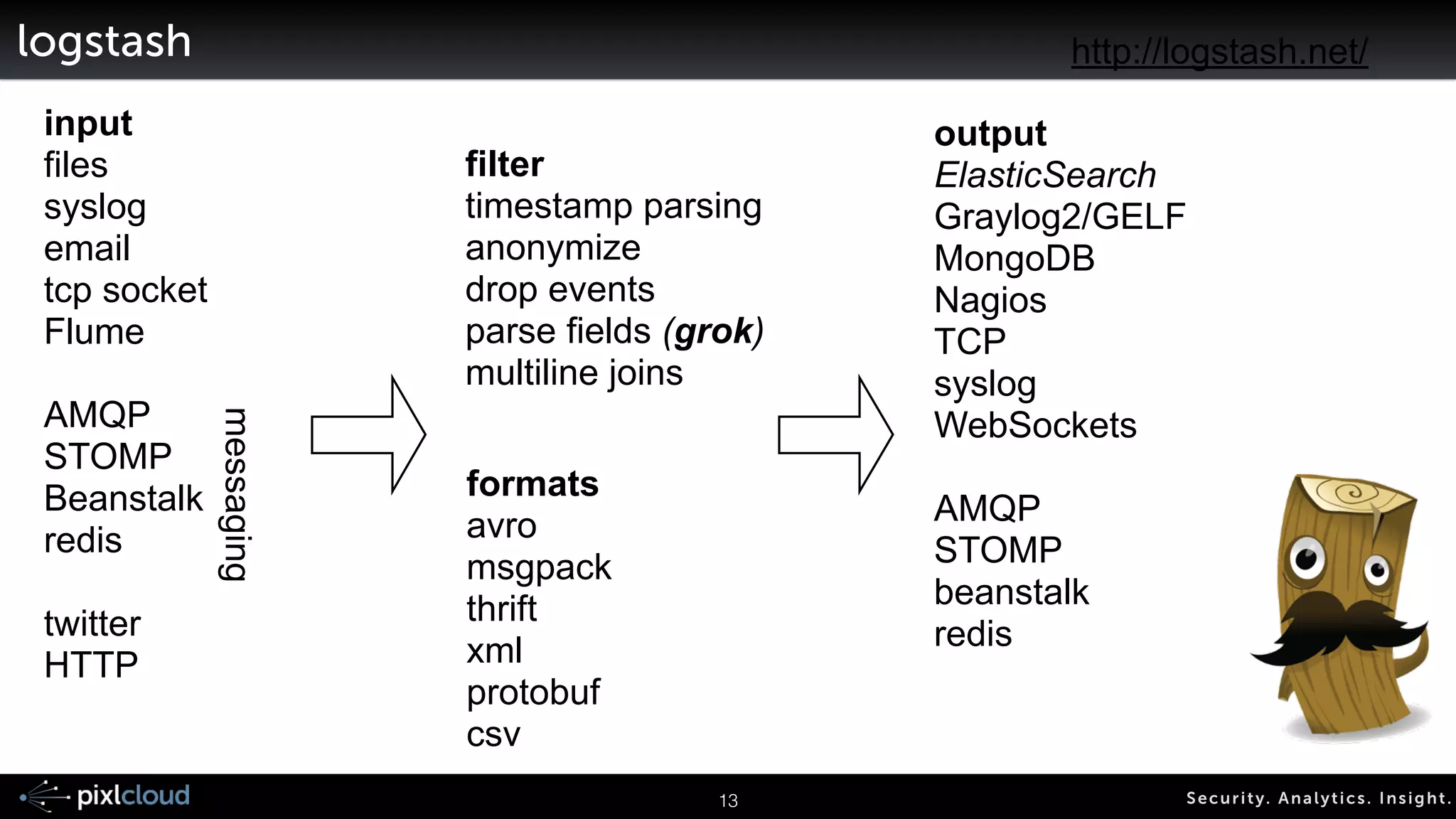
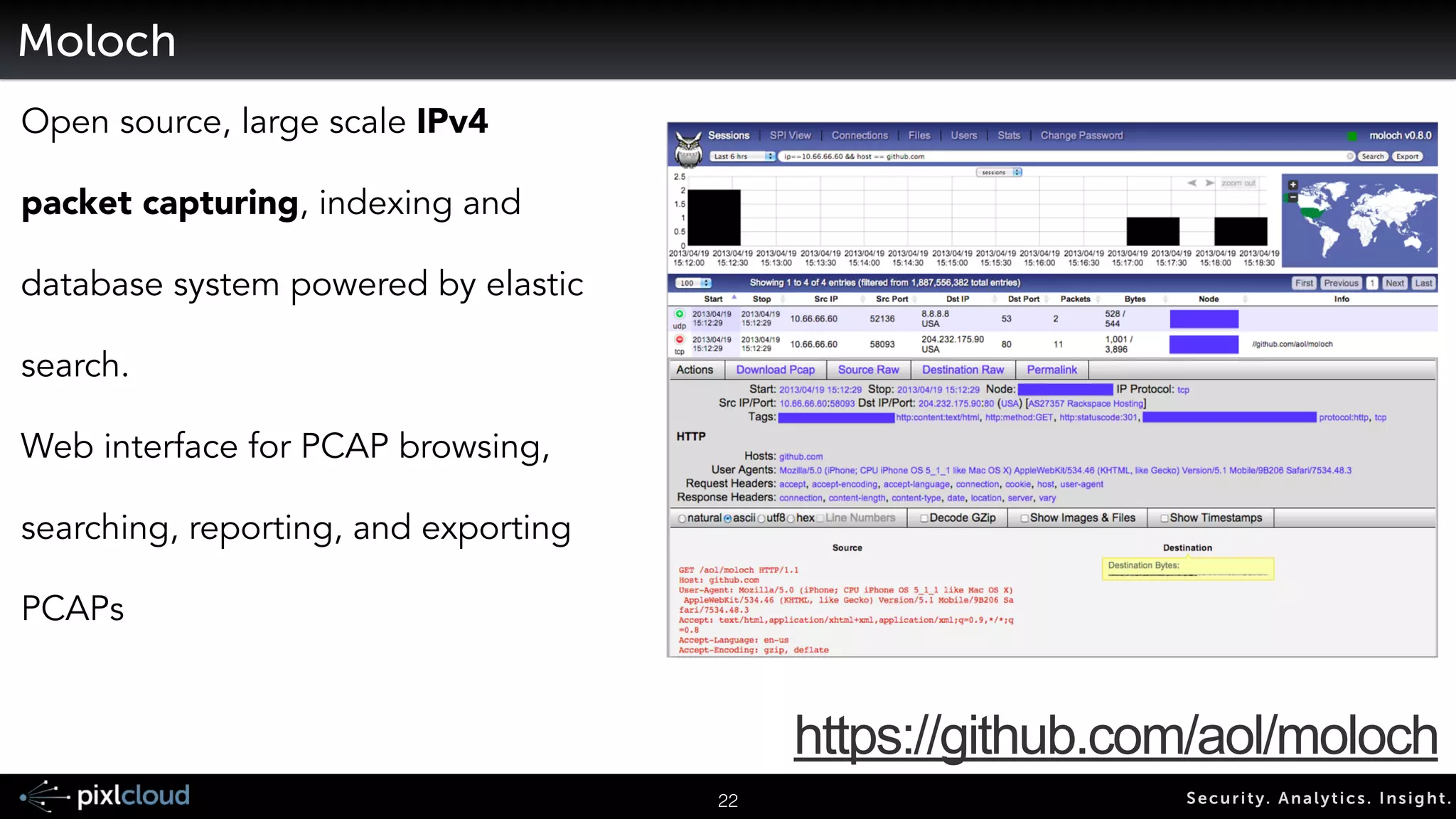
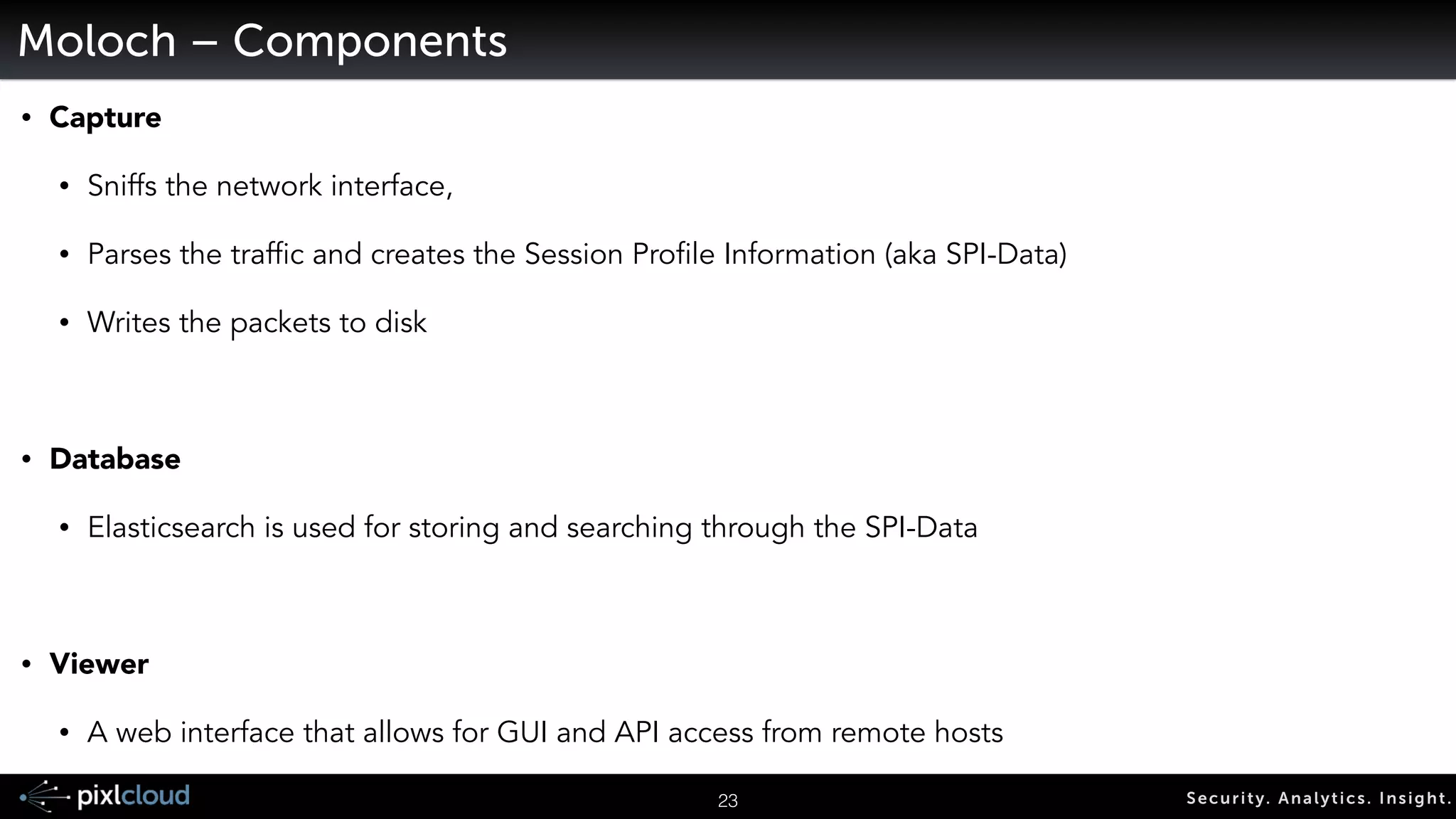
The document discusses big data visualization for security, outlining a comprehensive agenda that covers data sources, processing techniques, and various tools such as Elasticsearch, Logstash, and Kibana. It emphasizes the importance of context in visualization, showcases the capabilities of the ELK stack for managing and visualizing security logs, and highlights the Moloch system for packet capturing. Additionally, it addresses data visualization principles and tools necessary for effectively analyzing and presenting security-related data.



![18 Secur i ty. Analyt ics . Ins ight .
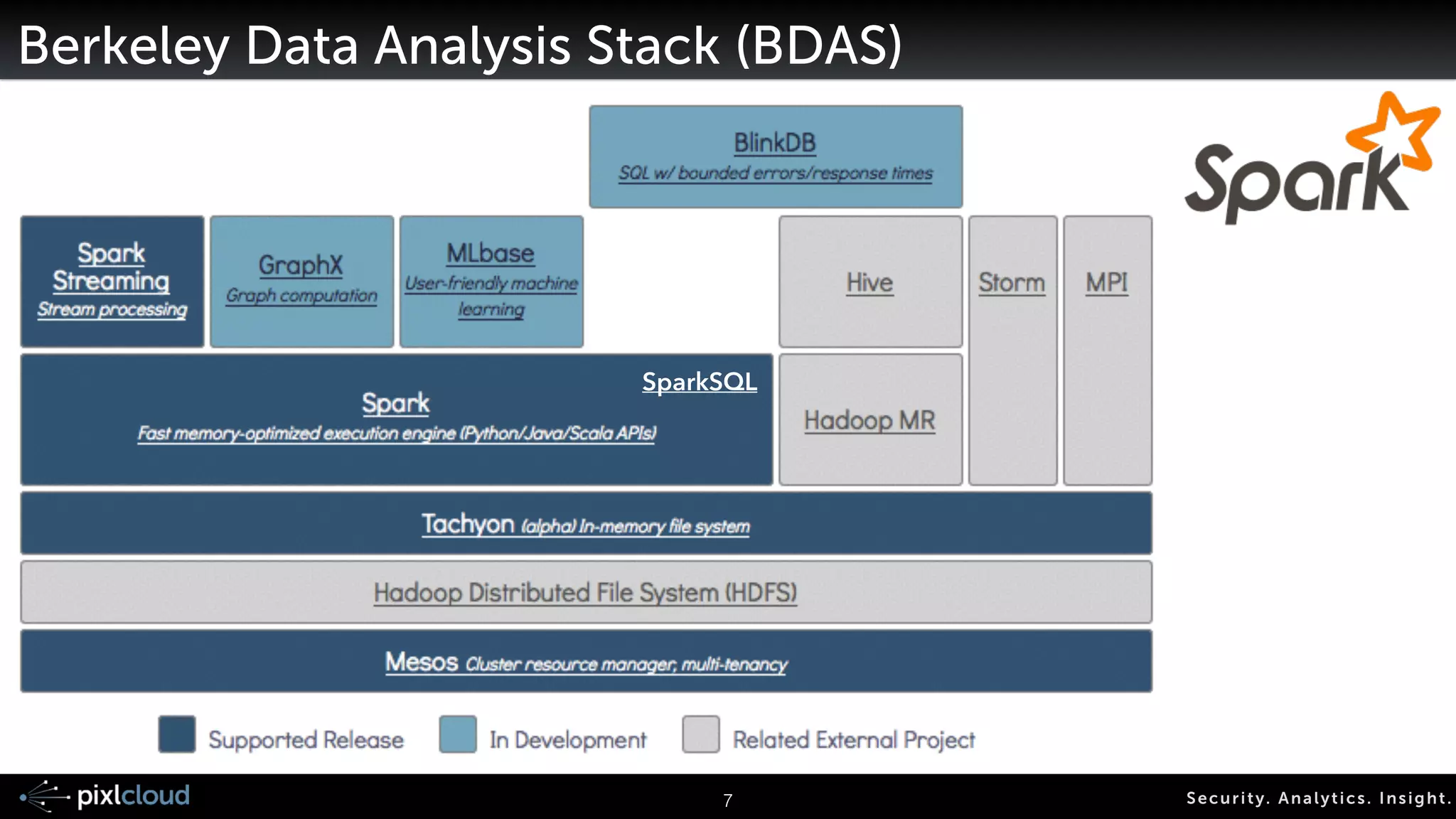
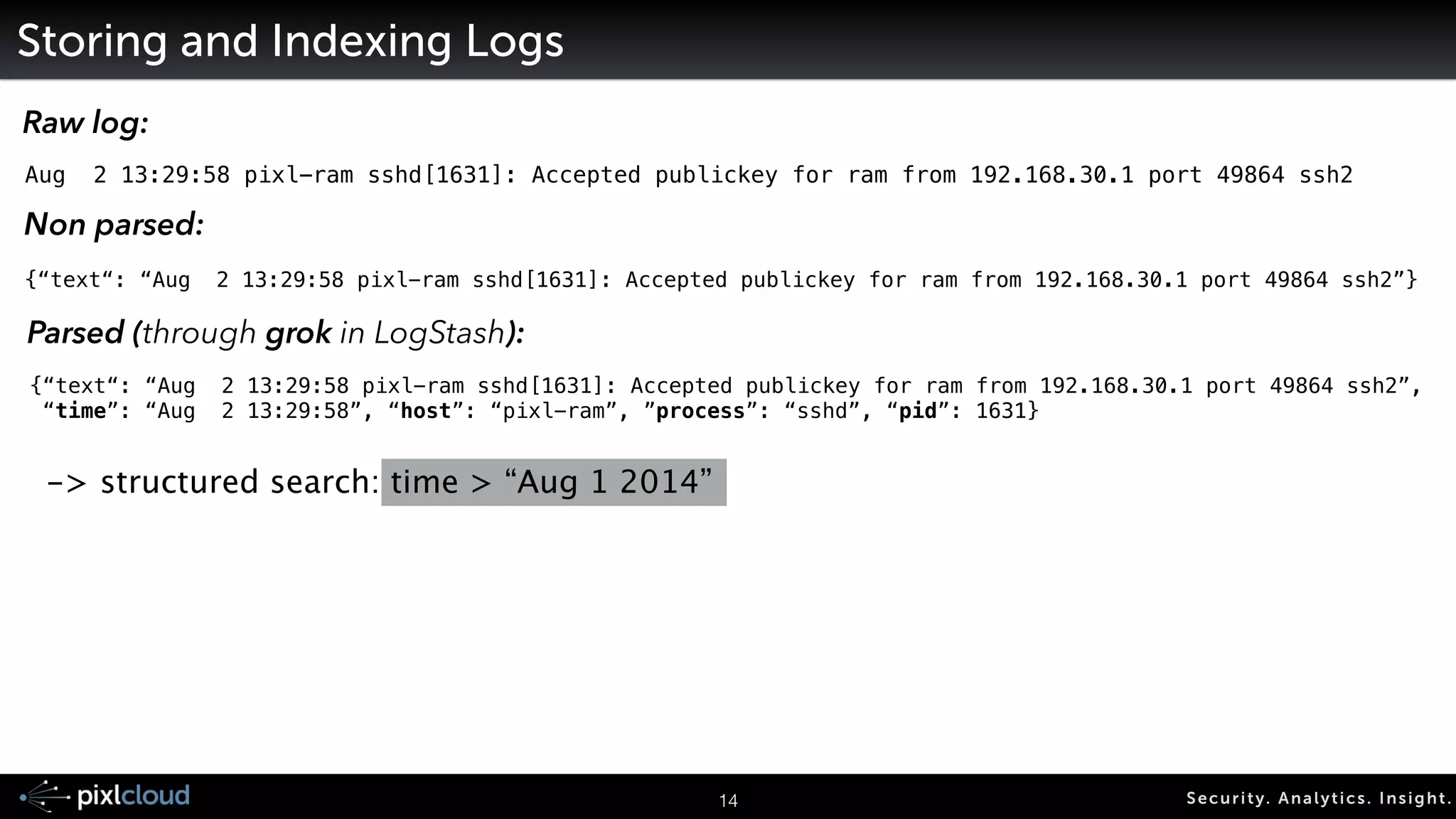
Storing and Indexing Logs
Raw log:
Aug 2 13:29:58 pixl-ram sshd[1631]: Accepted publickey for ram from 192.168.30.1 port 49864 ssh2
Non parsed:
{“text“: “Aug 2 13:29:58 pixl-ram sshd[1631]: Accepted publickey for ram from 192.168.30.1 port 49864 ssh2”}
Parsed (through grok in LogStash):
{“text“: “Aug 2 13:29:58 pixl-ram sshd[1631]: Accepted publickey for ram from 192.168.30.1 port 49864 ssh2”,
“time”: “Aug 2 13:29:58”, “host”: “pixl-ram”, ”process”: “sshd”, “pid”: 1631}
-> structured search: time > “Aug 1 2014”](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-15-2048.jpg)
![19 Secur i ty. Analyt ics . Ins ight .
Grok
• Instead of re-writing regexes
• Ships with about 100 patterns
• Patterns you don't have to write yourself
• It is easy to add new patterns
HOSTNAME b(?:[0-9A-Za-z].......!
IP (?<![0-9])(?:(?:25[0-5]|2[0-4][0-9]…!
IPORHOST (?:%{HOSTNAME}|%{IP})!](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-16-2048.jpg)
![• Automatic schema inference
• Assigns analyzers (prefix indexing, etc.)
• Field properties:
• “store” [field and document level]
• “index”:
• “analyzed”: tokenized, analyzed
• “not_analyzed”: indexed as is
• “no”: no indexing
20 Secur i ty. Analyt ics . Ins ight .
ElasticSearch on Grokked Data](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-17-2048.jpg)
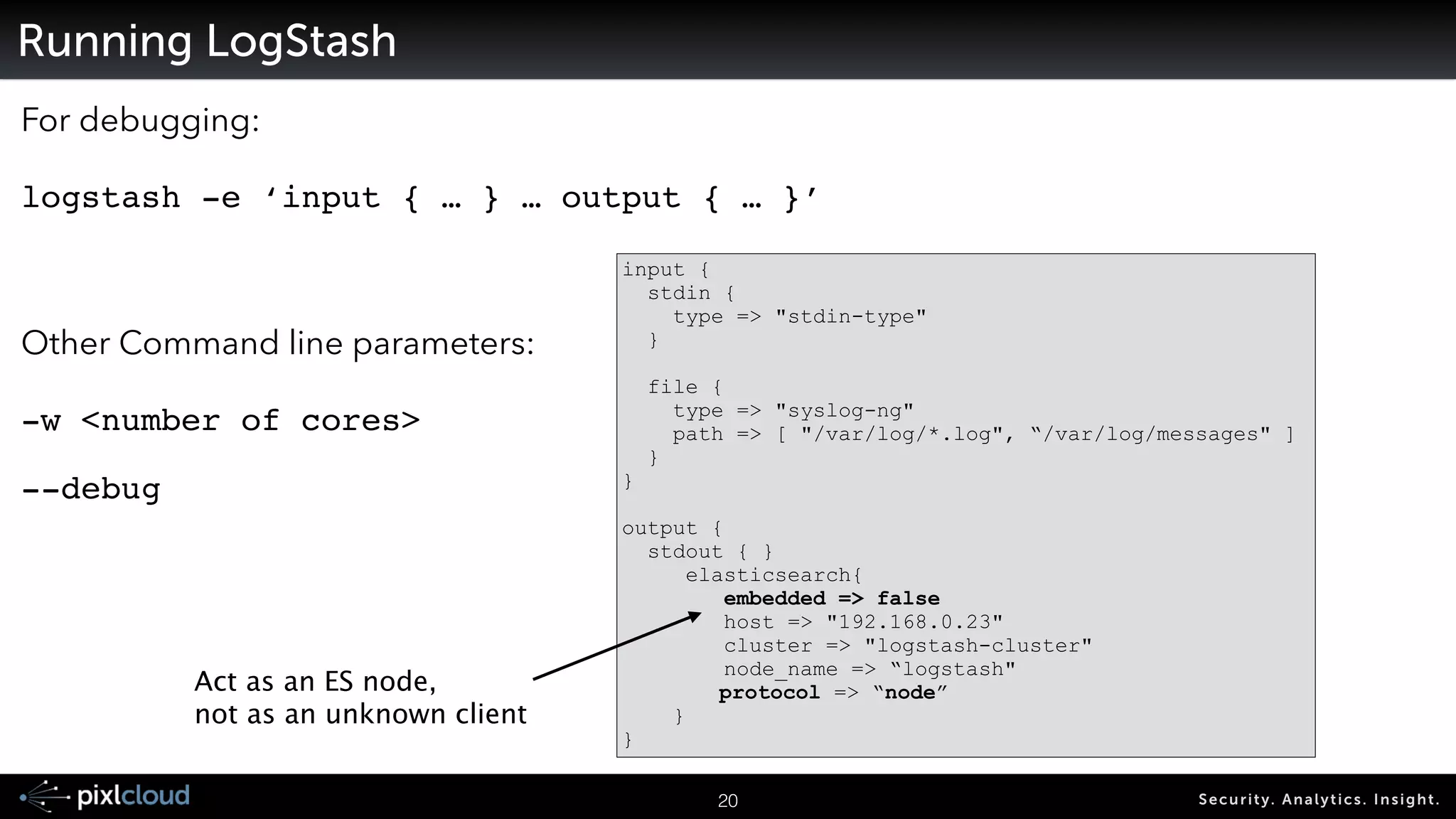
![Running LogStash
For debugging:
logstash -e ‘input { … } … output { … }’ !
24 Secur i ty. Analyt ics . Ins ight .
!
Other Command line parameters:
-w <number of cores>!
--debug!
!
!
input {
stdin {
type => "stdin-type"
}
!
file {
type => "syslog-ng"
path => [ "/var/log/*.log", “/var/log/messages" ]
}
}
!
output {
stdout { }
elasticsearch{
embedded => false
host => "192.168.0.23"
cluster => "logstash-cluster"
node_name => “logstash"
protocol => “node”
}
}
Act as an ES node,
not as an unknown client](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-21-2048.jpg)
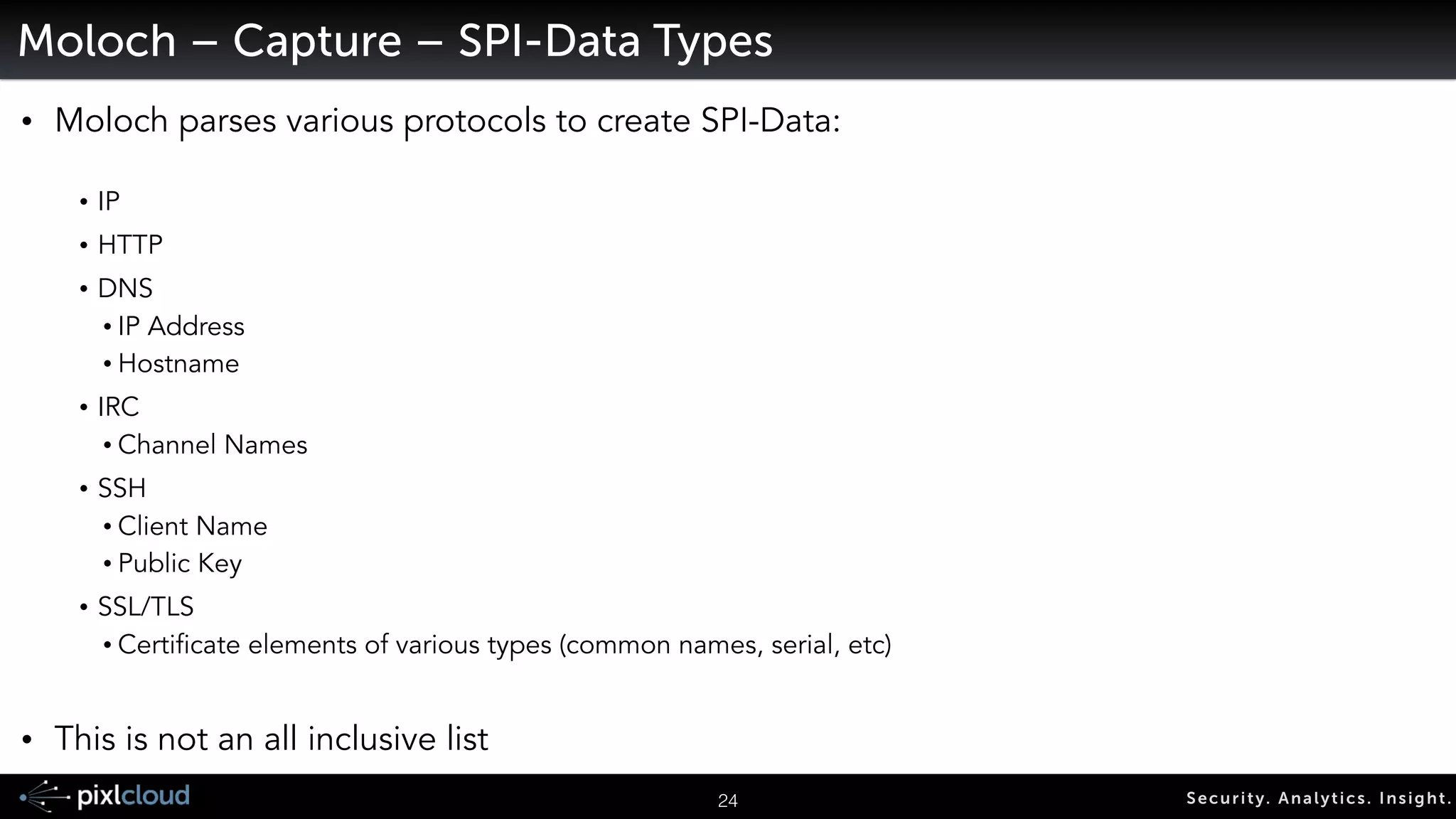
![34 Secur i ty. Analyt ics . Ins ight .
Moloch - Couple Additions
• Web API’s
• Access meta information
• Grab PCAPs
!
• Indexing PCAP files:
! ${moloch_dir}/bin/moloch-capture -c [config_file] -r [pcap_file]](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-26-2048.jpg)


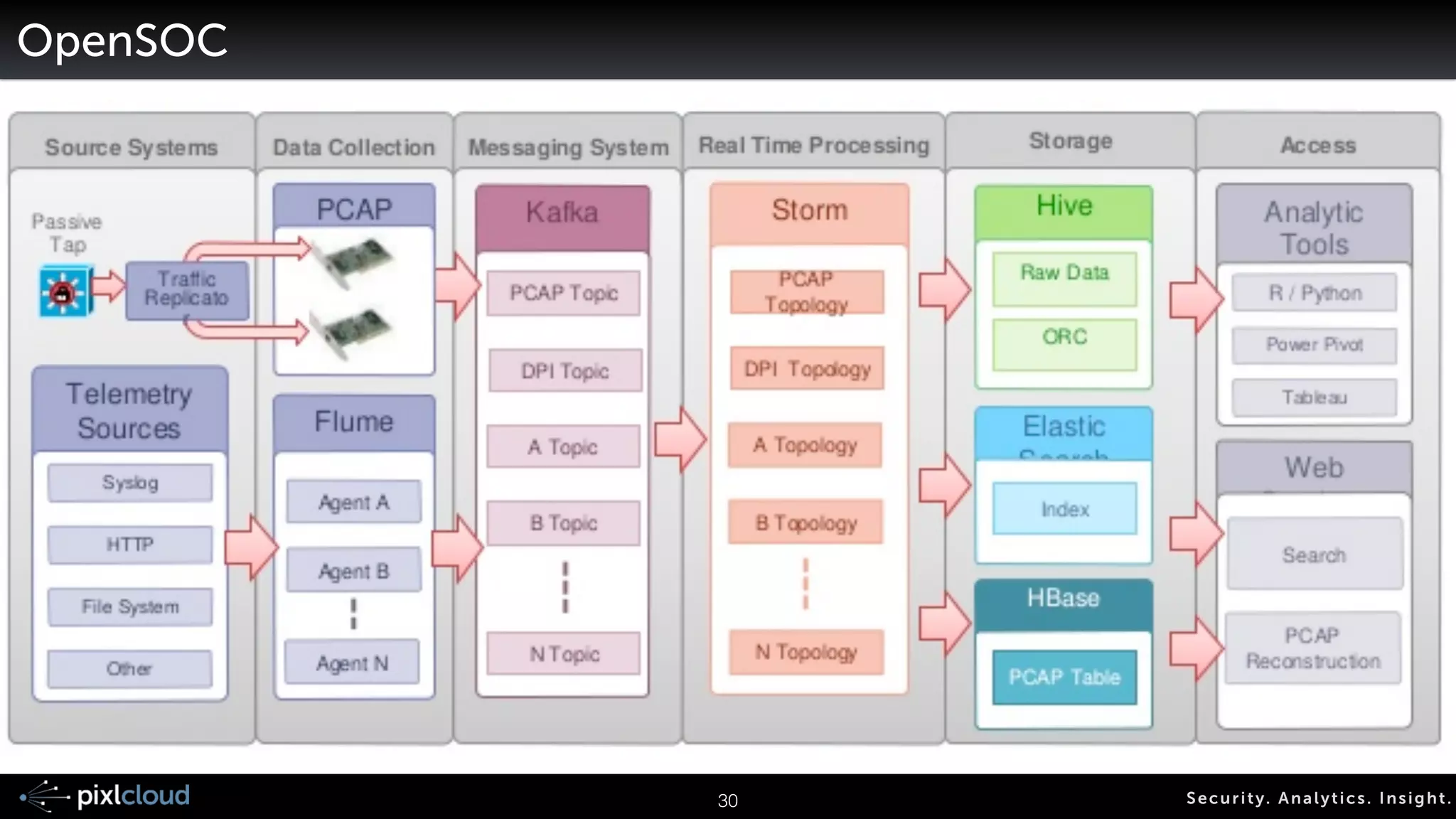



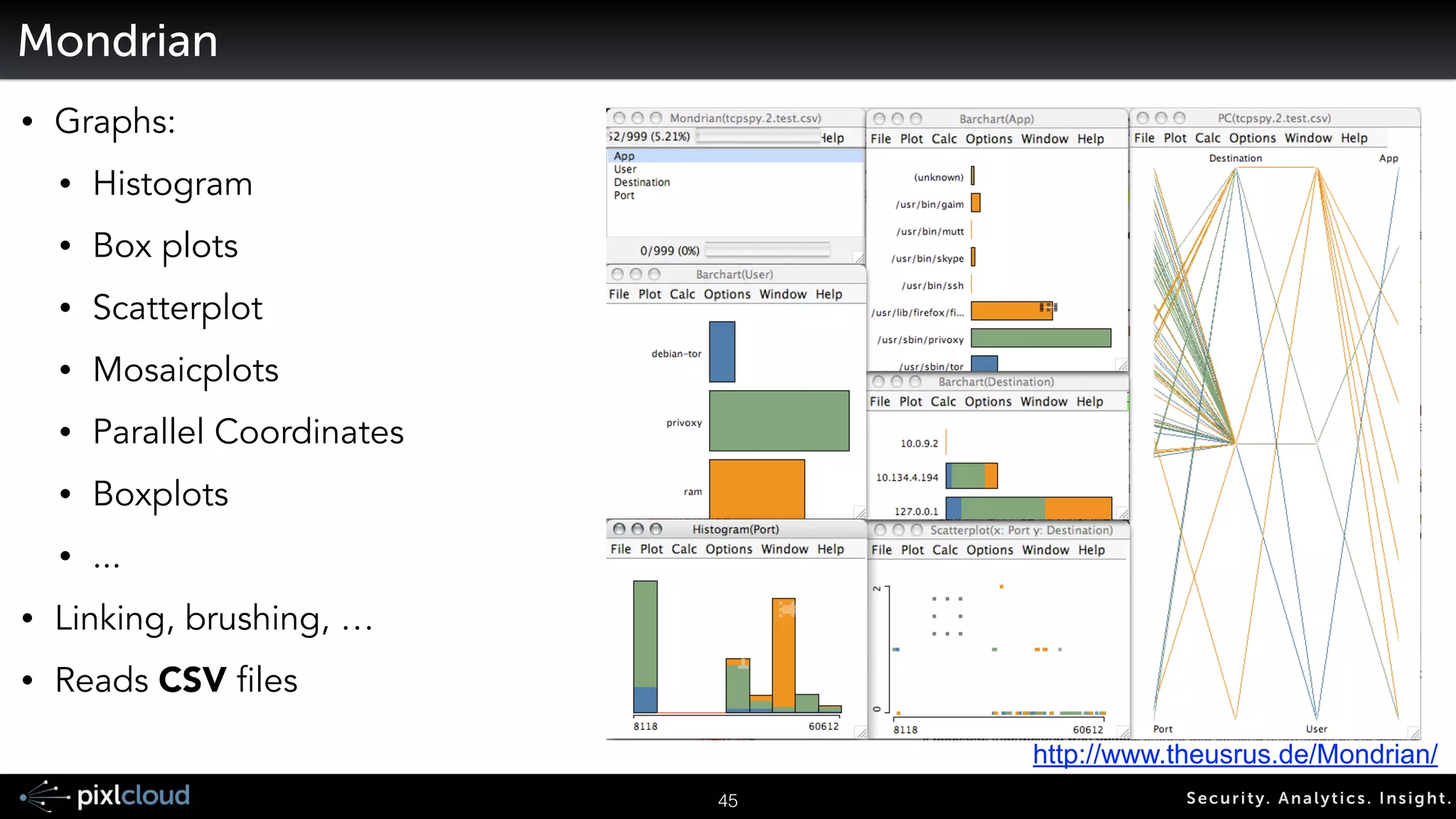
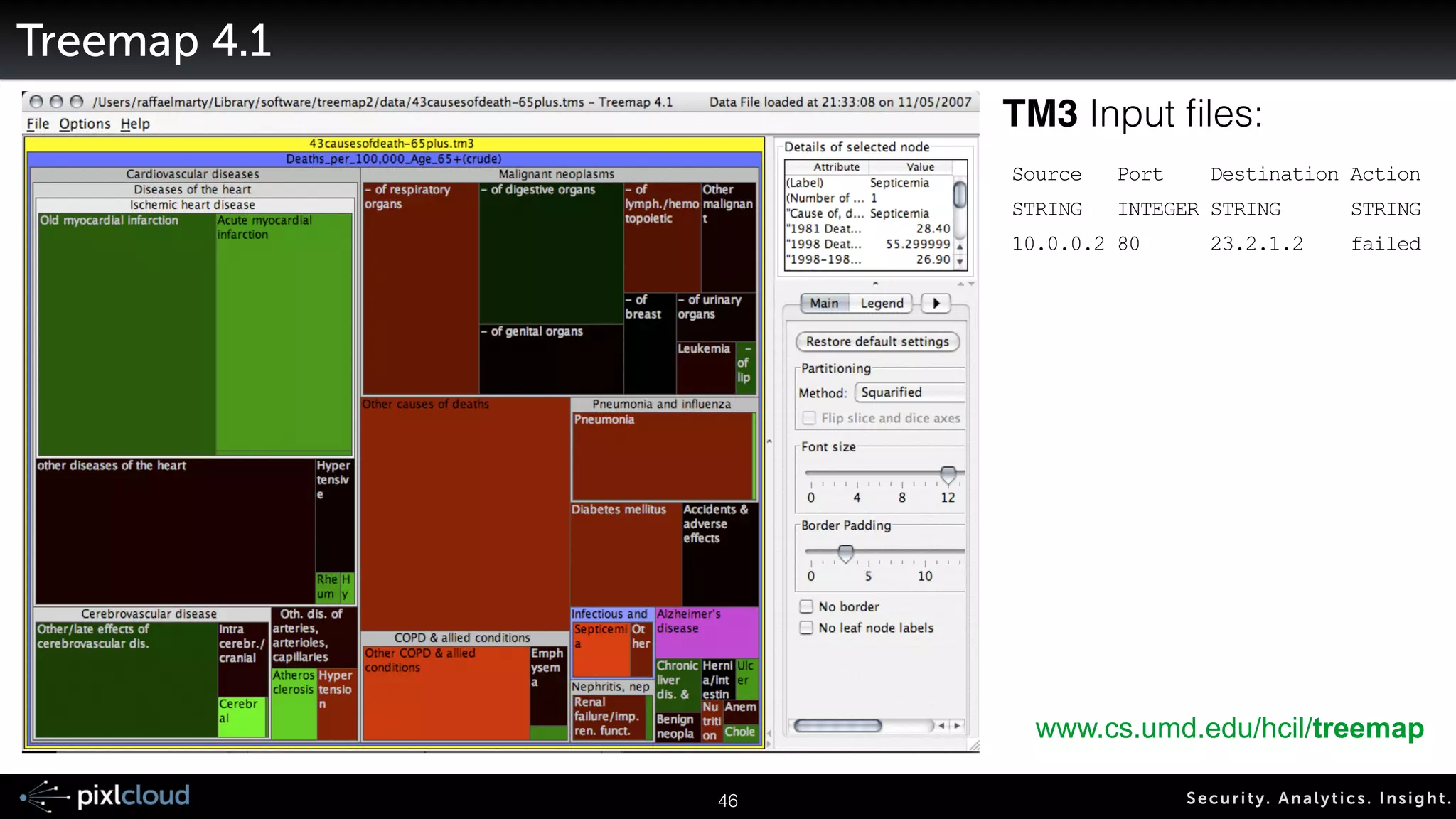
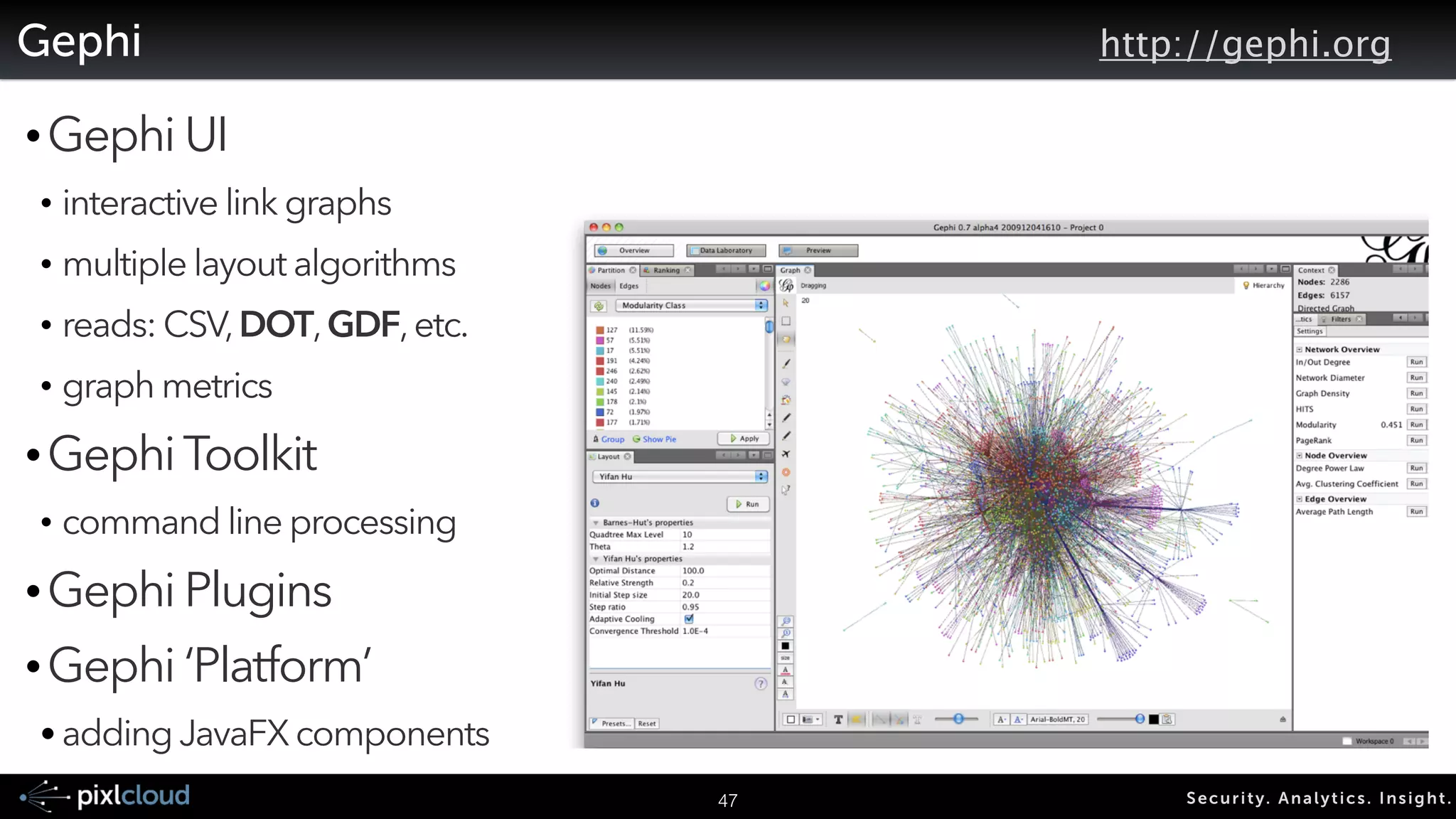
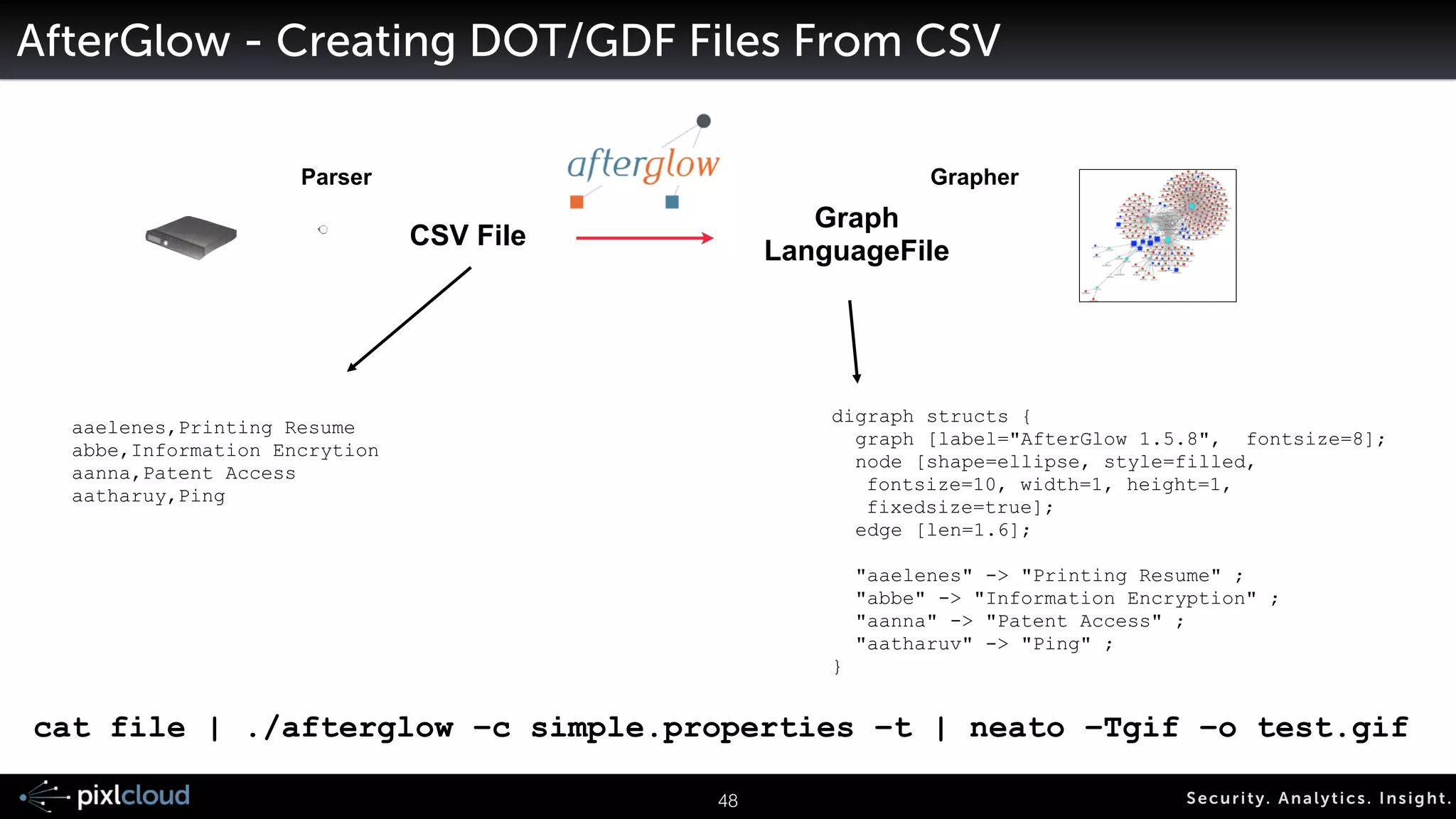


![AfterGlow - Creating DOT/GDF Files From CSV
Parser Grapher
CSV File Graph
LanguageFile
digraph structs {
graph [label="AfterGlow 1.5.8", fontsize=8];
node [shape=ellipse, style=filled,
fontsize=10, width=1, height=1,
fixedsize=true];
edge [len=1.6];
!
"aaelenes" -> "Printing Resume" ;
"abbe" -> "Information Encryption" ;
"aanna" -> "Patent Access" ;
"aatharuv" -> "Ping" ;
}
65 Secur i ty. Analyt ics . Ins ight .
aaelenes,Printing Resume
abbe,Information Encrytion
aanna,Patent Access
aatharuy,Ping
cat file | ./afterglow –c simple.properties –t | neato –Tgif –o test.gif](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-53-2048.jpg)


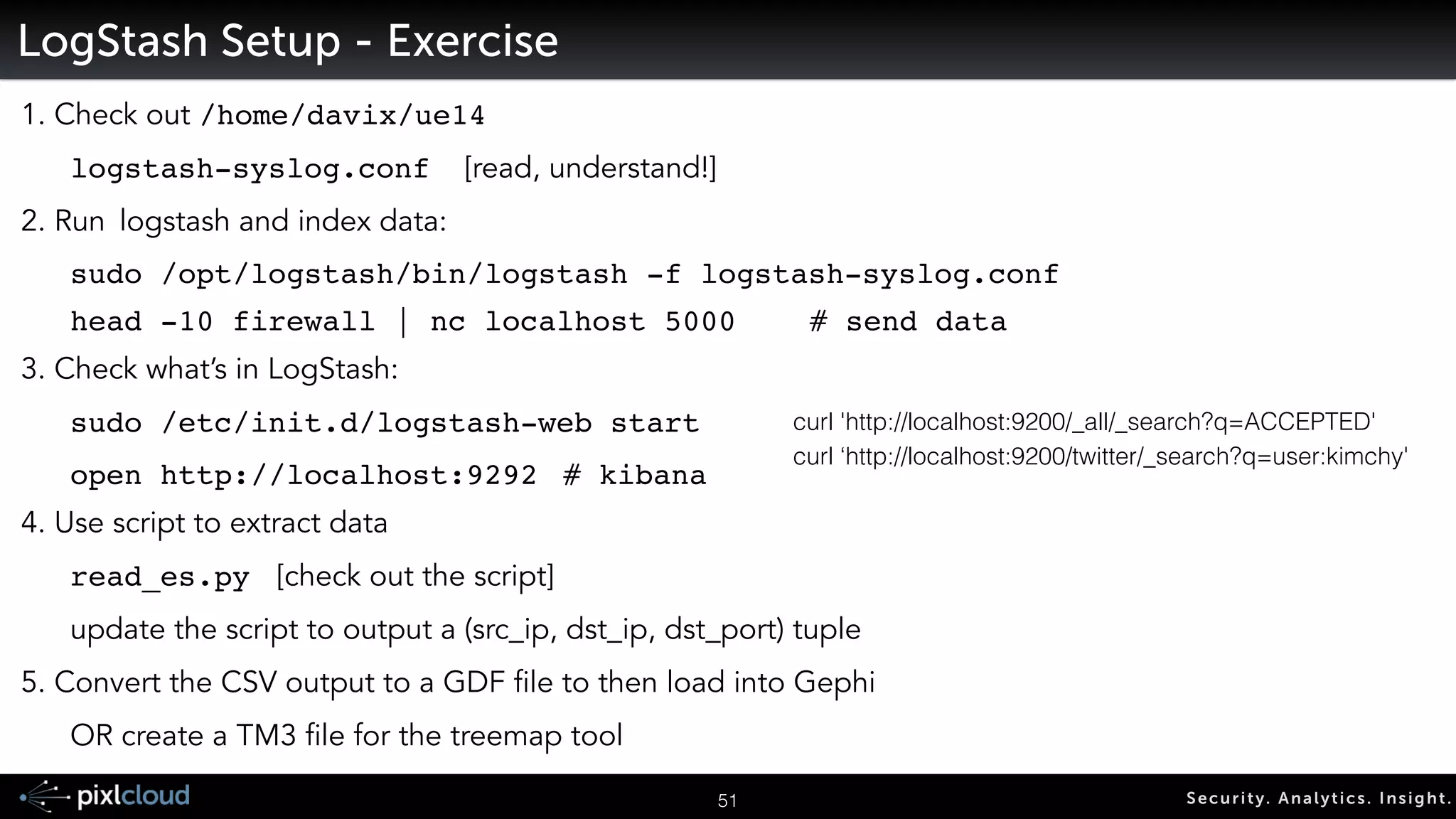
![68 Secur i ty. Analyt ics . Ins ight .
LogStash Setup - Exercise
1. Check out /home/davix/ue14
logstash-syslog.conf [read, understand!]
2. Run logstash and index data:
! sudo /opt/logstash/bin/logstash -f logstash-syslog.conf!
! head -10 firewall | nc localhost 5000!! # send data
3. Check what’s in LogStash:
sudo /etc/init.d/logstash-web start!
! open http://localhost:9292 !# kibana
4. Use script to extract data
read_es.py [check out the script]
update the script to output a (src_ip, dst_ip, dst_port) tuple
5. Convert the CSV output to a GDF file to then load into Gephi
OR create a TM3 file for the treemap tool
curl 'http://localhost:9200/_all/_search?q=ACCEPTED'
curl ‘http://localhost:9200/twitter/_search?q=user:kimchy'](https://image.slidesharecdn.com/ue14bigdatasecviz-140915022839-phpapp01/75/Workshop-Big-Data-Visualization-for-Security-56-2048.jpg)


