The Overview of Hyper-V Virtual Switch
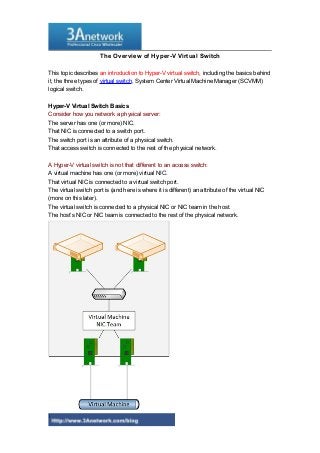
- 1. The Overview of Hyper-V Virtual Switch This topic describes an introduction to Hyper-V virtual switch, including the basics behind it, the three types of virtual switch, System Center Virtual Machine Manager (SCVMM) logical switch. Hyper-V Virtual Switch Basics Consider how you network a physical server: The server has one (or more) NIC. That NIC is connected to a switch port. The switch port is an attribute of a physical switch. That access switch is connected to the rest of the physical network. A Hyper-V virtual switch is not that different to an access switch: A virtual machine has one (or more) virtual NIC. That virtual NIC is connected to a virtual switch port. The virtual switch port is (and here is where it is different) an attribute of the virtual NIC (more on this later). The virtual switch is connected to a physical NIC or NIC team in the host. The host’s NIC or NIC team is connected to the rest of the physical network. 1
- 2. The virtual switch connects virtual machines to the rest of the physical network. Let’s get back to the switch port being an attribute of the virtual NIC. When we do network configurations on a physical switch, such VLAN tagging, we implement those configurations on a switch port. The same happens (under the covers) with a Hyper-V switch port. A physical server rarely moves, but when it does, we have to reconfigure the new switch port. A virtual machine can move very frequently. By making the switch port an attribute of the virtual NIC, any assigned network policy moves with the virtual machine, so there is no need to re-implement network policy for the VM. The Hyper-V virtual switch implements functionality such as QoS, VLAN tagging, bandwidth limits, and so on, even though those settings are revealed by the virtual NIC. The virtual switch also implements other advanced features such as Port ACLs. Important functionality 1 ARP/ND Poisoning (spoofing) protection: Provides protection against a malicious VM using Address Resolution Protocol (ARP) spoofing to steal IP addresses from other VMs. Provides protection against attacks that can be launched for IPv6 using Neighbor Discovery (ND) spoofing. 2 DHCP Guard protection: Protects against a malicious VM representing itself as a Dynamic Host Configuration Protocol (DHCP) server for man-in-the-middle attacks. 3 Port ACLs: Provides traffic filtering based on Media Access Control (MAC) or Internet Protocol (IP) addresses/ranges, which enables you to set up virtual network isolation. 4 Trunk mode to a VM: Enables administrators to set up a specific VM as a virtual appliance, and then direct traffic from various VLANs to that VM. 5 Network traffic monitoring: Enables administrators to review traffic that is traversing the network switch. 6 Isolated (private) VLAN: Enables administrators to segregate traffic on multiple vlans, to more easily establish isolated tenant communities. Following is a list of capabilities that enhance Hyper-V Virtual Switch usability: 1 Bandwidth limit and burst support: Bandwidth minimum guarantees amount of bandwidth reserved. Bandwidth maximum caps the amount of bandwidth a VM can consume. 2
- 3. 2 ENC marking support: Explicit Congestion Notification (ECN) marking—also known as Data CenterTCP (DCTCP)—enables the physical switch and operating system to regulate traffic flow such that the buffer resources of the switch are not flooded, which results in increased traffic throughput. 3 Diagnostics: Diagnostics allow easy tracing and monitoring of events and packets through the virtual switch. 3 Types of Virtual Switch There are three types of virtual switch that you can create in Hyper-V. External: This is the most common kind of virtual switch. VMs connected to this switch can communicate with other VMs on the physical network, the host, and other networked physical entities. Internal: VMs on an internal network can talk to other VMs on that same internal network that are running on that host, and the host. Rarely do you see internal virtual switches used outside of a lab. Private: When connected to a private virtual switch, VMs are limited to communications with VMs on the same private network that are running on that host. This approach is sometimes used for network isolation but communications are constrained within a host. In production, you are better off deploying a firewall protected VLAN or using Hyper-V Network Virtualization (Software-Defined Networking). Note that any communications to and from a VM are subject to security rules that are applied, such as physical firewall (gateway) rules, Port ACLs, and so on. More related: New SDN product Cisco 40G switch Juniper QFX5100 switch Hot topic of Interop 2013 exhibition in New York: infrastructure construction More Cisco products and Reviews you can visit: http://www.3anetwork.com/blog It is referred from www.petri.co.il/hyper-v-virtual-switch-overview.htm 3Anetwork.com is a world leading Cisco networking products wholesaler, we wholesale original new Cisco networking equipments, including Cisco Catalyst switches, Cisco routers, Cisco firewalls, Cisco wireless products, Cisco modules and interface cards products at competitive price and ship to worldwide. Our website: http://www.3anetwork.com Telephone: +852-3069-7733 Email: info@3Anetwork.com Address: 23/F Lucky Plaza, 315-321 Lockhart Road, Wanchai, Hongkong 3
