Cybersecurity's Impact on Innovation
•
2 likes•800 views
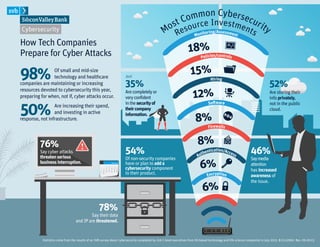
Most small and mid-sized tech and healthcare companies are maintaining or increasing their cybersecurity resources this year in preparation for inevitable cyber attacks. While half are increasing spending, most are investing in active response capabilities rather than infrastructure. Only a small minority of companies express high confidence in the security of their information, and many see serious business disruption risks from cyber attacks.
Report
Share
Report
Share
Download to read offline
Recommended
Security policy orchestration and automation (SPOA) is the area of technology that facilitates managing and standardizing network firewall security policies.
These slides based on the webinar from leading IT analyst firm Enterprise Management Associates (EMA) delve into the difference between organizations using an SPOA solution to manage their firewall environments versus those not using one of these solutions. The Value of Using Security Policy Orchestration and Automation for Improving...

The Value of Using Security Policy Orchestration and Automation for Improving...Enterprise Management Associates
More Related Content
What's hot
Security policy orchestration and automation (SPOA) is the area of technology that facilitates managing and standardizing network firewall security policies.
These slides based on the webinar from leading IT analyst firm Enterprise Management Associates (EMA) delve into the difference between organizations using an SPOA solution to manage their firewall environments versus those not using one of these solutions. The Value of Using Security Policy Orchestration and Automation for Improving...

The Value of Using Security Policy Orchestration and Automation for Improving...Enterprise Management Associates
What's hot (20)
2018 Trends in Cybersecurity: Building Effective Security Teams 

2018 Trends in Cybersecurity: Building Effective Security Teams
The Cyber Security Readiness of Canadian Organizations

The Cyber Security Readiness of Canadian Organizations
Understanding the Security-Specific Purchase Process [Infographic]![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Security-Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Understanding the Security-Specific Purchase Process [Infographic]
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Radical Innovation In Security (New Techniques Applied To Tomorrow’s Risk)

Radical Innovation In Security (New Techniques Applied To Tomorrow’s Risk)
2015 Energy Industry Cybersecurity Research Update

2015 Energy Industry Cybersecurity Research Update
Managing Security Policies Across Hybrid Cloud Environments

Managing Security Policies Across Hybrid Cloud Environments
The Value of Using Security Policy Orchestration and Automation for Improving...

The Value of Using Security Policy Orchestration and Automation for Improving...
Viewers also liked
Beyond ISO 27034 - Intel's Product Security Maturity Model (PSMM)NTXISSACSC3 - Beyond ISO 27034 - Intel's Product Security Maturity Model (PSM...

NTXISSACSC3 - Beyond ISO 27034 - Intel's Product Security Maturity Model (PSM...North Texas Chapter of the ISSA
Viewers also liked (17)
NTXISSACSC3 - Beyond ISO 27034 - Intel's Product Security Maturity Model (PSM...

NTXISSACSC3 - Beyond ISO 27034 - Intel's Product Security Maturity Model (PSM...
Extending the 20 critical security controls to gap assessments and security m...

Extending the 20 critical security controls to gap assessments and security m...
Estimating Development Security Maturity in About an Hour

Estimating Development Security Maturity in About an Hour
NISTs Cybersecurity Framework -- Comparison with Best Practice

NISTs Cybersecurity Framework -- Comparison with Best Practice
Global Cyber Security Outlook - Deloitte (Hotel_Digital_Security_Seminar_Sept...

Global Cyber Security Outlook - Deloitte (Hotel_Digital_Security_Seminar_Sept...
Cybersecurity Risk Assessment - 'All Done' with WISER

Cybersecurity Risk Assessment - 'All Done' with WISER
The Security Vulnerability Assessment Process & Best Practices

The Security Vulnerability Assessment Process & Best Practices
Similar to Cybersecurity's Impact on Innovation
Incident Response Management: How European Enterprises are Planning to Prepare for a Cyber Security BreachBreaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...Hewlett Packard Enterprise Business Value Exchange
Similar to Cybersecurity's Impact on Innovation (20)
Ponemon report : 'Critical Infrastructure: Security Preparedness and Maturity -

Ponemon report : 'Critical Infrastructure: Security Preparedness and Maturity -
CompTIA - IT Security Sales Practices in the Channel 

CompTIA - IT Security Sales Practices in the Channel
Securing the C-Suite: Cybersecurity Perspectives from the Boardroom

Securing the C-Suite: Cybersecurity Perspectives from the Boardroom
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study
Global Megatrends in Cybersecurity – A Survey of 1,000 CxOs

Global Megatrends in Cybersecurity – A Survey of 1,000 CxOs
International Technology Adoption & Workforce Issues Study - Brazilian Summary

International Technology Adoption & Workforce Issues Study - Brazilian Summary
“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...

“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...
Cybersecurity in the Cognitive Era: Priming Your Digital Immune System

Cybersecurity in the Cognitive Era: Priming Your Digital Immune System
15 Years of Web Security: The Rebellious Teenage Years

15 Years of Web Security: The Rebellious Teenage Years
More from Silicon Valley Bank
More from Silicon Valley Bank (20)
Trends in Healthcare Investments and Exits 2018 - Mid-Year Report

Trends in Healthcare Investments and Exits 2018 - Mid-Year Report
How Paperless Payables Can Streamline Ops and Improve Cash Flow

How Paperless Payables Can Streamline Ops and Improve Cash Flow
Trends in Healthcare Investments and Exits: Mid-Year 2017

Trends in Healthcare Investments and Exits: Mid-Year 2017
3 ways to sell your suppliers on credit card payments

3 ways to sell your suppliers on credit card payments
Silicon Valley Bank 2017 State of the Wine Industry Report

Silicon Valley Bank 2017 State of the Wine Industry Report
Recently uploaded
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Cybersecurity's Impact on Innovation
- 1. C ommonnvybersecu st C ource I estmen rity Mo Res Monitoring/Assessment ts Cybersecurity How Tech Companies Prepare for Cyber Attacks 98% Of small and mid-size technology and healthcare companies are maintaining or increasing resources devoted to cybersecurity this year, preparing for when, not if, cyber attacks occur. 50% Are increasing their spend, and investing in active response, not infrastructure. 18% Policies/controls Just 35% Are completely or very confident in the security of their company information. 15% Hiring 12% Software 8% 52% Are storing their info privately, not in the public cloud. Firewalls 76% 54% Say cyber attacks threaten serious business interruption. Of non-security companies have or plan to add a cybersecurity component to their product. 8% entication/Acces uth s A 6% Encryption 6% 46% Say media attention has increased awareness of the issue. 78% Say their data and IP are threatened. Statistics come from the results of an SVB survey about cybersecurity completed by 216 C-level executives from US-based technology and life science companies in July 2013. B-13-12992. Rev. 09-20-13
