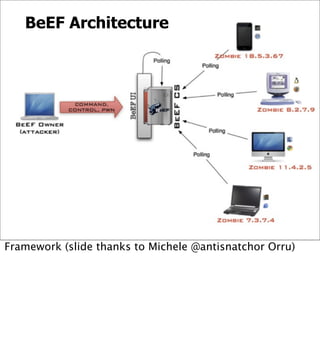
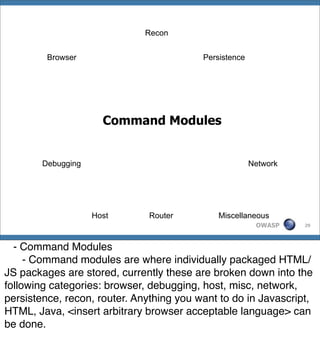
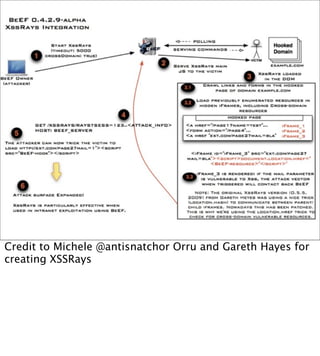
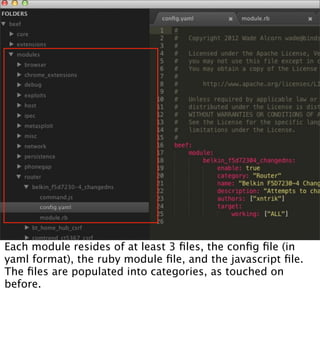
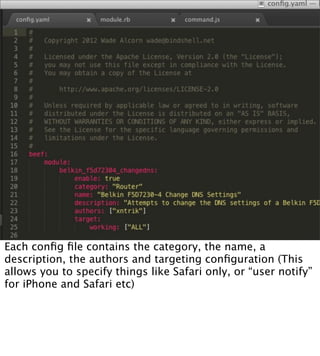
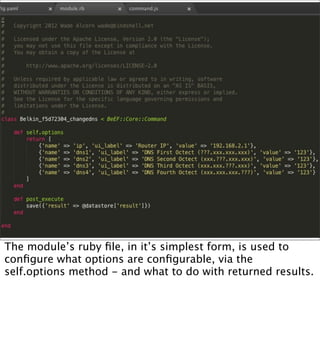
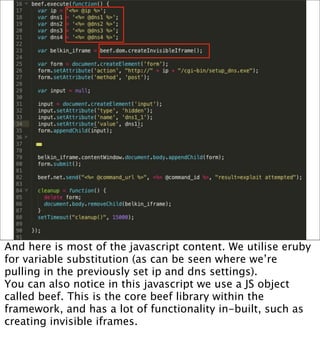
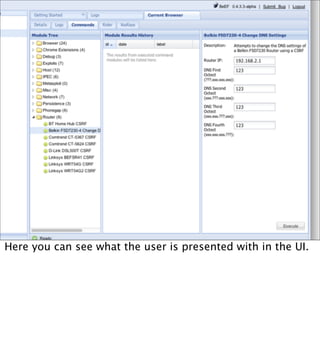
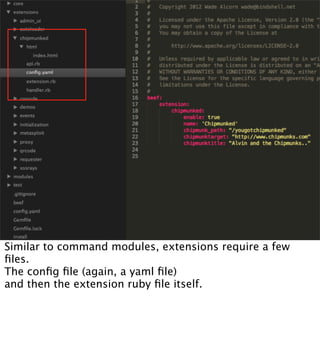
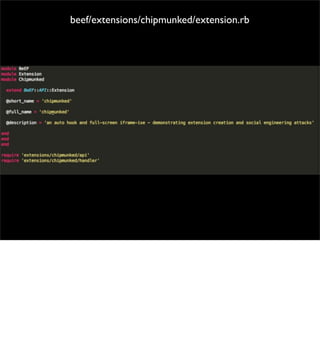
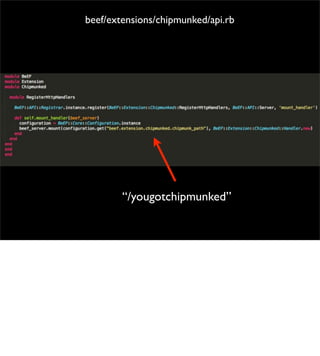
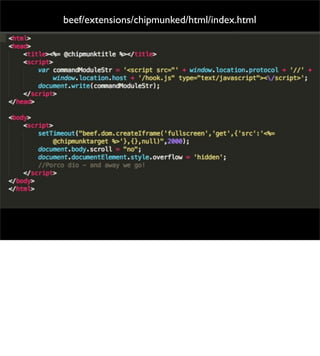
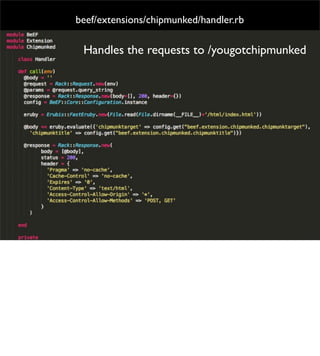
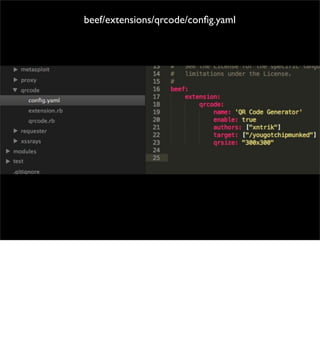
The document introduces the Browser Exploitation Framework (BeEF), which allows penetration testers to target client-side applications from within the context of the browser. BeEF can pivot through client systems to internal networks that are not directly exposed. It discusses how BeEF hooks browsers, its architecture including core components and extensions, and example command modules and use cases. It also provides instructions for customizing BeEF by developing new command modules and extensions.