Classification of data handling
•
0 likes•333 views
A brief description of the origin and the attributes of data handling and the classification there of.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
The third session from a two day course for potential first responders I ran for a large financial services client.First Responders Course - Session 3 - Monitoring and Controlling Incident Costs

First Responders Course - Session 3 - Monitoring and Controlling Incident CostsPhil Huggins FBCS CITP
More Related Content
Viewers also liked
Viewers also liked (6)
Sinergi Lintas Sektor dan Politik Anggaran dalam Mendukung Pembangunan Sumber...

Sinergi Lintas Sektor dan Politik Anggaran dalam Mendukung Pembangunan Sumber...
Clarissa usando un collar de Guau re miau by maria trapos

Clarissa usando un collar de Guau re miau by maria trapos
Jean Fares Couture on the Most Popular US Entertainment Shows!-Newsletter May...

Jean Fares Couture on the Most Popular US Entertainment Shows!-Newsletter May...
Similar to Classification of data handling
The third session from a two day course for potential first responders I ran for a large financial services client.First Responders Course - Session 3 - Monitoring and Controlling Incident Costs

First Responders Course - Session 3 - Monitoring and Controlling Incident CostsPhil Huggins FBCS CITP
Similar to Classification of data handling (20)
First Responders Course - Session 3 - Monitoring and Controlling Incident Costs

First Responders Course - Session 3 - Monitoring and Controlling Incident Costs
Risk Factory: How to Implement an Effective Incident Response Programme

Risk Factory: How to Implement an Effective Incident Response Programme
01-introductiontosecurity-111122004432-phpapp02.pdf

01-introductiontosecurity-111122004432-phpapp02.pdf
Events Management or How to Survive Security Incidents

Events Management or How to Survive Security Incidents
Classification of data handling
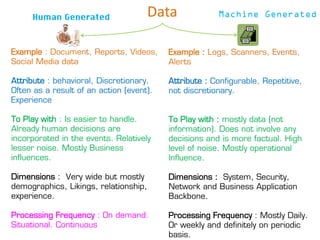
- 1. Data Human Generated Example : Document, Reports, Videos, Social Media data Attribute : behavioral, Discretionary. Often as a result of an action (event). Experience To Play with : Is easier to handle. Already human decisions are incorporated in the events. Relatively lesser noise. Mostly Business influences. Dimensions : Very wide but mostly demographics, Likings, relationship, experience. Processing Frequency : On demand. Situational. Continuous Example : Logs, Scanners, Events, Alerts Attribute : Configurable, Repetitive, not discretionary. To Play with : mostly data (not information). Does not involve any decisions and is more factual. High level of noise. Mostly operational Influence. Dimensions : System, Security, Network and Business Application Backbone. Processing Frequency : Mostly Daily. Or weekly and definitely on periodic basis.
