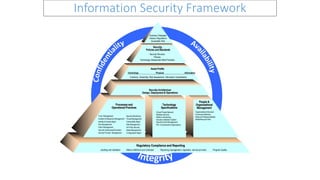
Information Security Framework
- 1. Information Security Framework Regulatory Compliance and Reporting Auditing and Validation Metrics Definition and Collection Reporting (management, regulatory, service provider) Program Quality Security Structure Policies Technology-Independent Best Practices Security, Policies and Standards Technology Physical Information Asset Profile Inventory, Ownership, Risk Assessment, Information Classification Technology Specifications Virtual Private Network Wireless Security Platform Hardening Intrusion Detection System Security Event Management PKI: Components & Applications Business Drivers Business Strategies Industry Regulations Acceptable Risk People & Organizational Management Organizational Structure Functional Definition Roles and Responsibilities Skills/Resource Plan Security Architecture Design, Deployment & Operations Processes and Operational Practices Trust Management Incident & Response Management Identity & Access Mgmt Key Management Patch Management Security Awareness/Education Service Provider Management Security Monitoring Threat Management Vulnerability Mgmt Risk Management 3rd Party Security Asset Management Configuration Mgmt
- 2. Regulatory Compliance and Reporting Auditing and Validation Metrics Definition and Collection Reporting (management, regulatory, service provider) Program Quality Security Structure Policies Technology-Independent Best Practices Security, Policies and Standards Technology Physical Information Asset Profile Inventory, Ownership, Risk Assessment, Information Classification Technology Specifications Virtual Private Network Wireless Security Platform Hardening Intrusion Detection System Security Event Management PKI: Components & Applications Business Drivers Business Strategies Industry Regulations Acceptable Risk People & Organizational Management Organizational Structure Functional Definition Roles and Responsibilities Skills/Resource Plan Security Architecture Design, Deployment & Operations Processes and Operational Practices Trust Management Incident & Response Management Identity & Access Mgmt Key Management Patch Management Security Awareness/Education Service Provider Management Security Monitoring Threat Management Vulnerability Mgmt Risk Management 3rd Party Security Asset Management Configuration Mgmt Information Security Framework Sarbanes Oxley (SOX) Compliance with COSO Governance Rules for SOX Compliance Network and System Architecture and other Tools to Protect SOX data Event Management Practices for Supporting Operations on Systems Hosting SOX related applications Practices for Monitoring the Effectiveness of IT Controls Identification of SOX related data. and Where it Resides Security Impact of Enterprise Network and System Architecture - Vulnerabilities on SOX supported systems Method to Monitor and Maintain SOX Compliance Technology Element of Information and Systems Management
- 3. Regulatory Compliance and Reporting Auditing and Validation Metrics Definition and Collection Reporting (management, regulatory, service provider) Program Quality Security Structure Policies Technology-Independent Best Practices Security, Policies and Standards Technology Physical Information Asset Profile Inventory, Ownership, Risk Assessment, Information Classification Technology Specifications Virtual Private Network Wireless Security Platform Hardening Intrusion Detection System Security Event Management PKI: Components & Applications Business Drivers Business Strategies Industry Regulations Acceptable Risk People & Organizational Management Organizational Structure Functional Definition Roles and Responsibilities Skills/Resource Plan Security Architecture Design, Deployment & Operations Processes and Operational Practices Trust Management Incident & Response Management Identity & Access Mgmt Key Management Patch Management Security Awareness/Education Service Provider Management Security Monitoring Threat Management Vulnerability Mgmt Risk Management 3rd Party Security Asset Management Configuration Mgmt Information Security Framework Gramm-Leach-Bliley Act (GLBA) Compliance Risk Management, Efficiency Enhancement, Business Process Enablement Identification of PII and Where It Resides Rules for Using and Protecting PII Network and System Architecture and other Tools to Protect PII Security Configuration and Management of Systems Hosting PII Practices for Supporting Operations (Tape Backup, Application Execution, Etc.) on Systems Hosting PII Roles, Responsibilities, and Practices for Handling and Using PII Practices for Monitoring the Security and Use of PII Rule for Protection and Use of Enterprise Information Identification of Sensitive Business Information such as Legal, Financial, Strategic, HR, Etc. and Where it Resides Security Impact of Enterprise Network and System Architecture - Vulnerabilities on non-PII systems may Expose PII People Element of Information and Systems Management Process Element of Information and Systems Management Technology Element of Information and Systems Management Method to Monitor and Maintain Architecture Integrity
- 4. Regulatory Compliance and Reporting Auditing and Validation Metrics Definition and Collection Reporting (management, regulatory, service provider) Program Quality Security Structure Policies Technology-Independent Best Practices Security, Policies and Standards Technology Physical Information Asset Profile Inventory, Ownership, Risk Assessment, Information Classification Technology Specifications Virtual Private Network Wireless Security Platform Hardening Intrusion Detection System Security Event Management PKI: Components & Applications Business Drivers Business Strategies Industry Regulations Acceptable Risk People & Organizational Management Organizational Structure Functional Definition Roles and Responsibilities Skills/Resource Plan Security Architecture Design, Deployment & Operations Processes and Operational Practices Trust Management Incident & Response Management Identity & Access Mgmt Key Management Patch Management Security Awareness/Education Service Provider Management Security Monitoring Threat Management Vulnerability Mgmt Risk Management 3rd Party Security Asset Management Configuration Mgmt Information Security Framework Supervisor Control and Data Acquisition (SCADA) Best Practice Understand the business risk Best Practice Security Process Control Establish Response Capabilities Practices for Supporting Operations on Systems Hosting SCADA related applications Identification of SCADA related technology. Security Impact of Enterprise Network and System Architecture - Vulnerabilities on SCADA supported systems Manage Third Party Risk Technology Element of Information and Systems Management Implement secure architecture Improve Awareness and Skills
- 5. Regulatory Compliance and Reporting Auditing and Validation Metrics Definition and Collection Reporting (management, regulatory, service provider) Program Quality Security Structure Policies Technology-Independent Best Practices Security, Policies and Standards Technology Physical Information Asset Profile Inventory, Ownership, Risk Assessment, Information Classification Technology Specifications Virtual Private Network Wireless Security Platform Hardening Intrusion Detection System Security Event Management PKI: Components & Applications Business Drivers Business Strategies Industry Regulations Acceptable Risk People & Organizational Management Organizational Structure Functional Definition Roles and Responsibilities Skills/Resource Plan Security Architecture Design, Deployment & Operations Processes and Operational Practices Trust Management Incident & Response Management Identity & Access Mgmt Key Management Patch Management Security Awareness/Education Service Provider Management Security Monitoring Threat Management Vulnerability Mgmt Risk Management 3rd Party Security Asset Management Configuration Mgmt Information Security Framework Payment Card Industry (PCI) Compliance Info Security Policy Identification of PCI and Where It Resides Rules for Using and Protecting PCI Data Network and System Architecture and other Tools to Protect PCI Data Security Configuration and Management of Systems Hosting PCI Data Vulnerability Management Monitoring and Testing Controls Protect Card Holder Data Strong Access Controls Secure Network Method to Monitor and Maintain Architecture Integrity Technology Element of Information and Systems Management Roles, Responsibilities, and Practices for Handling and Using PCI Data
- 6. • Confidentiality – Ensuring that only authorized personnel have access to information • Integrity – Ensuring that information is unchanged and accurate • Availability – Ensuring that information is available to the user when it is needed Confidentiality, Integrity and Availability
- 7. • Demonstrate support for, and commitment to, information security • States policy across the entire enterprise • Broad statement of principle • Long term; changed infrequently • Few in overall number • Provide overall direction for the organization • Mandatory; require formal exception process • Process and technology independent • Require a high level of authority to create, change or eliminate Policies
- 8. • Suitable for complying with policies • Specify a course of action • Mandatory; require formal exception process • Process and technology independent • Mid-level authority required to create, change or eliminate Standards
- 9. • Process and/or technology dependent • Require a low level of authority to create, change or eliminate • May have a high level of complexity • Generally apply enterprise-wide, with some exceptions locally • May be situation-specific • May require formal exception process • They are detailed steps to be followed by users, system operations personnel, or others to accomplish a particular task (e.g., preparing new user accounts and assigning the appropriate privileges). Procedures / Guidelines
- 10. Policy, Standard, Procedure Framework
- 11. Policy, Standard, Procedure Framework
- 12. • Development: Planning and creation of the policy • Review: Assessment of the policy by an independent party • Approval: Authorizing implementation of the policy • Communication: Dissemination of policy to enterprise • Implementation: Initial execution of the policy • Compliance Monitoring: Tracking and reporting on the effectiveness • Exception Approval: Evaluation, documentation and tracking of exceptions • Maintenance: Ensuring currency Policy Management / Administration
- 13. Provide simple, consistent and timely classification and authorization processes Balance between protection of and access to an organization’s business information Provide clear guidelines for employees and contractors for the classification and handling of information Policy Management / Administration
- 14. Maintain an inventory of assets, link those assets to owners, and identify technologies supporting key applications or groups of applications Enable organizations to track security controls implemented to protect assets Monitor support of ongoing threats that may be introduced to the asset environment Asset Management – Asset Inventory
- 15. • Multi-tiered centrally managed approach to Internet access • All access to the Internet is controlled via password protected proxy devices that filter inappropriate content • Third party connectivity is controlled via connections to distinct network segments • Connections to the enterprise network are only made after a review of controls at connecting organization Security Architecture Design, Deployment, Operations
- 16. • Network-based intrusion detection in place for all external network connections • Host-based intrusion detection in place for all business critical servers • Production data is strictly segmented from development data Security Architecture Design, Deployment, Operations
- 17. • Multiple tiers of virus protection exist • All email is filtered through a virus scanner • All file servers and workstations are protected via a managed (push-technology) virus protection solution • Encryption Standards are employed consistently across enterprise • Only Standards Based Encryption is used • Centralized Directory (LDAP) in use Security Architecture Design, Deployment, Operations
- 18. • Business Continuity Management • Critical Business Process are identified and linked to Applications • Business Applications are linked to IT Disaster Recovery Plans • Incident Response • Documented Incident Response Plans define roles and actions • Ensure proper control of information released to public • Identity and Access Management • Users are centrally managed • Tools may assist in user provisioning Processes and Operational Practices
- 19. • Trust Management • Incident Reporting & Response Management • Identity & Access Mgmt • Key Management • Patch Management • Security Awareness/Education • Service Provider Management Processes and Operational Practices
- 20. • Security Monitoring • Threat Management • Vulnerability Mgmt • Risk Management • Service Party Security (i.e., Verizon, HP, CSC) • Asset Management • Configuration Mgmt Processes and Operational Practices
- 21. • All Major Platforms are identified • Minimum Security Baselines for Specific platforms in use • Technical Specifications for technologies created before implementation Technical Specifications
- 22. • Virtual Private Network • Wireless Security • Platform Hardening • Intrusion Detection System • Security Event Management • PKI: Components & Applications • Security and Privacy in Cloud Management Technical Specifications
- 23. Technical Security Standard for Unix (Solaris, Linux, AIX, HPUX) Technical Security Standards for AS400 Technical Security Standard for Firewalls Technical Security Standard for Routers Technical Security Standards for Oracle, SQL Technical Security Standards for Web Security Technical Security Standards for Citrix Technical Security Standards for Cryptography Technical Security Standards for System or Application Development and Maintenance Technical Security Standards for Windows 2000, 2003, XP, Vista Technical Security Standards for Wireless Technical Specifications
- 24. • Security concerns are issues of corporate governance • Identify and communicate high-level executive sponsorship to manage information security risks • Recognize information security as a business issue that requires people, technology, policy, and process to implement Security Organization
- 25. • Structure is clearly defined and communicated in leading organizations • Reporting levels are appropriately aligned and have appropriate authority • Blends of both centralized and de-centralized security structure • De-centralized business unit or functional security units are aligned with centralized corporate security function Security Organization - Structure
- 26. • Measures effectiveness of security program • Gramm-Leach-Bliley Act (GLBA) Compliance • Sarbanes Oxley (SOX) Compliance with COSO • Payment Card Industry (PCI) Compliance • Supervisor or Control and Data Acquisition (SCADA) Best Practice • Conducts compliance reviews across all domains of influence • Reports across the enterprise • Security audits performed on risk basis • Goals have been defined for projects Security Program Compliance and Reporting
- 27. Determine the effectiveness and maturity of a various business supporting practices, processes, and management Demonstrates where you are in the security lifecycle Organization will be able to visualize – Exceeding expectations – Meeting requirements – Gaps in business needs Information Security Lifecycle