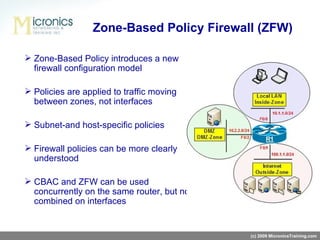
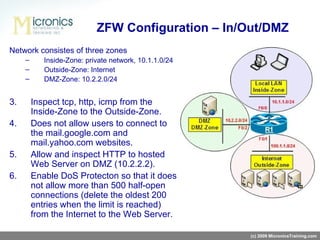
- Zone-Based Policy Firewall (ZFW) introduces a new firewall configuration model where policies are applied between zones (like inside and outside networks) rather than interfaces. This provides more granular control over traffic.
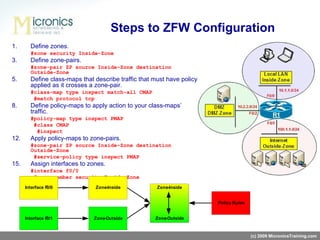
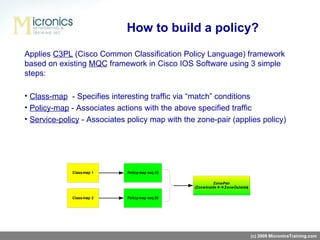
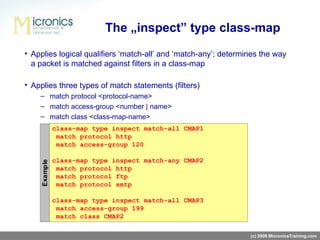
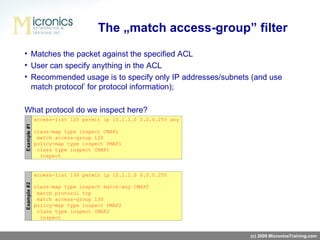
- ZFW defines zones for networks, zone-pairs to identify traffic flowing between zones, class-maps to classify traffic, policy-maps to apply actions to traffic classes, and service-policies to attach policies to zone-pairs.
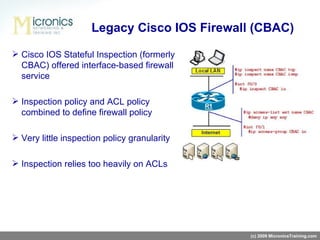
- Key benefits of ZFW include subnet-level policies, ability to define separate policies for different zone-pairs, and running ZFW concurrently with legacy Cisco firewall (CBAC).











![(c) 2009 MicronicsTraining.com Thank you! www.MicronicsTraining.com [email_address]](https://image.slidesharecdn.com/zonebasedpolicyfirewall-12636381721209-phpapp02/85/Zone-Based-Policy-Firewall-19-320.jpg)