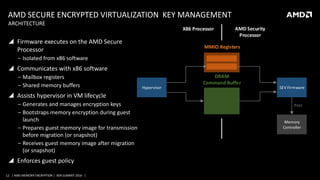
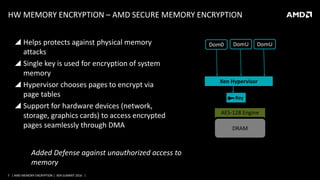
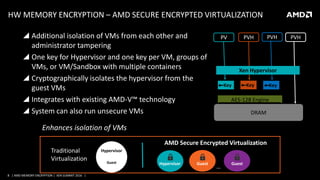
AMD presented on their memory encryption technologies for virtualized environments. Their hardware-based AMD Secure Memory Encryption and AMD Secure Encrypted Virtualization features provide encryption of memory to enhance security and isolation between VMs and the hypervisor. The encryption is performed inline by the memory controller with minimal performance impact. Key management is handled by the AMD Secure Processor to isolate encryption keys. Integration with Xen would involve calling APIs to manage keys and ASIDs for guests to provide encryption using these technologies.





![10 | AMD MEMORY ENCRYPTION | XEN SUMMIT 2016 |
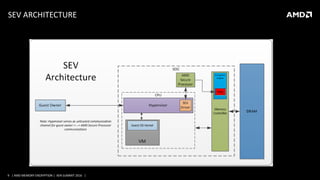
AMD SECURE ENCRYPTED VIRTUALIZATION DETAILS
Address Space ID (ASID) determines VM encryption key
‒ Maximum supported key can be obtained through Fn8000_001F[CX]
‒ ASID is tagged with all data within the SoC
‒ ASID determines encryption key to use when data enters/leaves SoC
HW and Guest page tables determine if a page is “private” or “shared”
‒ Instruction code pages always “private”
‒ Guest page tables always “private”
‒ Data pages can be “private” (C=1) or “shared” (C=0) depending on page tables
‒ Before CR4.PAE=1, all pages are “private”
All DMA must occur to “shared” pages
Example use: all guest pages are “private” except for DMA pages](https://image.slidesharecdn.com/21xensummit2016-brijeshsingh-160902153734/85/XPDS16-AMD-s-virtualization-memory-encryption-technology-Brijesh-Singh-Advanced-Micro-Devices-AMD-10-320.jpg)