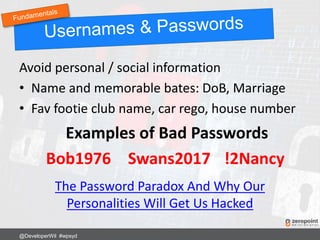
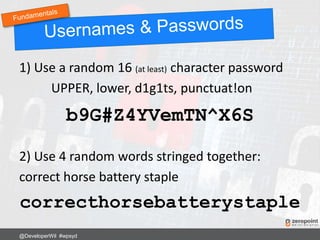
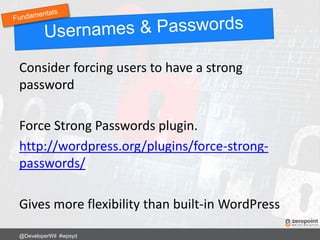
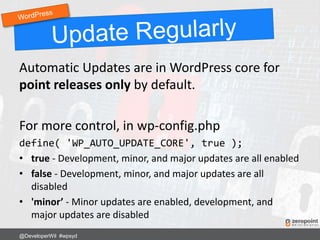
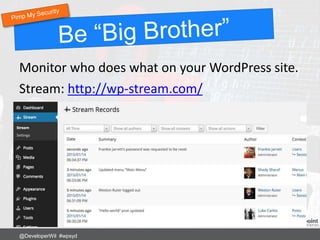
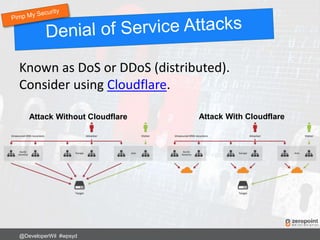
This document provides numerous tips and best practices for hardening WordPress website security, including using strong and unique passwords, keeping software updated, properly configuring file permissions, installing security plugins, implementing two-factor authentication, and regularly backing up the site. It emphasizes that security is an ongoing process rather than a single fix, as threats constantly evolve over time.










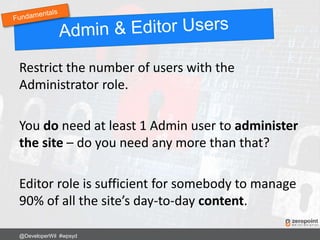
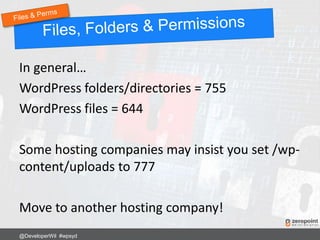











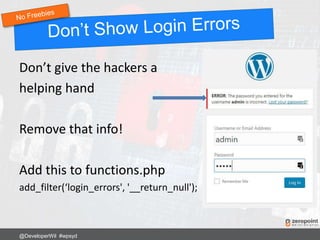



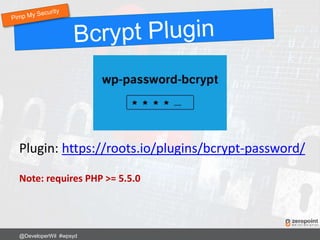



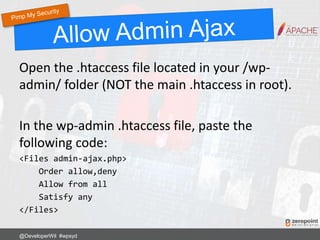
![Use .htaccess to stop SQL injection attacks on
form fields and URLs.
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (<|%3C).*script.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|[|%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|[|%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
Any requests or changes to global variables
containing <script> gets blocked.
@DeveloperWil #wpsyd](https://image.slidesharecdn.com/wordpress-security-best-practices-2017-update-171128013605/85/WordPress-Security-Best-Practices-57-320.jpg)
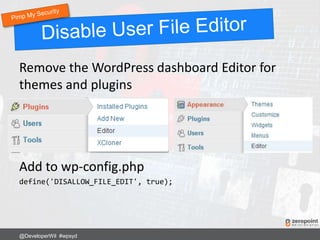
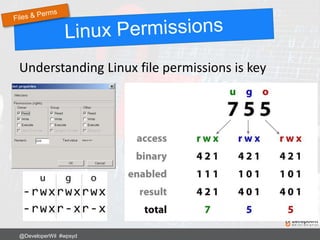
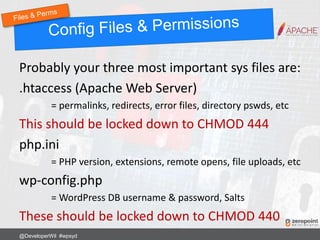
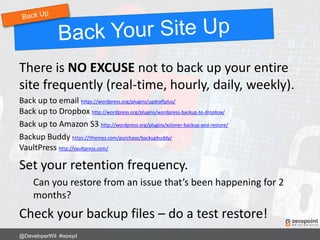
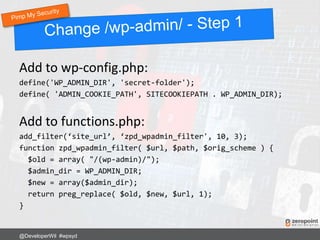
![Using .htaccess
RewriteRule ^login$ http://www.mywebsite.com/wp-login.php [NC,L]
Now login to your site using:
http://www.mywebsite.com/login
@DeveloperWil #wpsyd](https://image.slidesharecdn.com/wordpress-security-best-practices-2017-update-171128013605/85/WordPress-Security-Best-Practices-65-320.jpg)
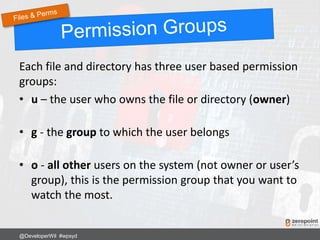
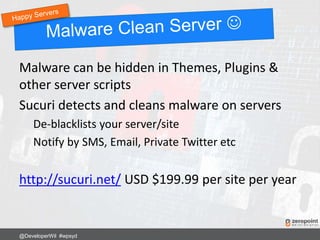
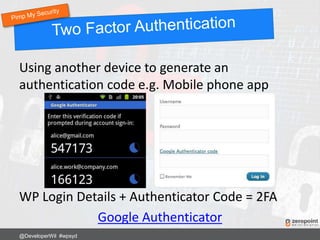
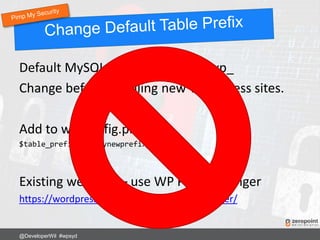
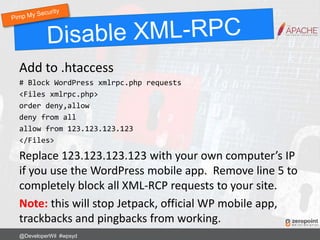
![Add to .htaccess:
RewriteRule ^secret-folder/(.*) wp-admin/$1?%{QUERY_STRING} [L]
Now login to your site using:
http://www.mysite.com/secret-folder/
@DeveloperWil #wpsyd](https://image.slidesharecdn.com/wordpress-security-best-practices-2017-update-171128013605/85/WordPress-Security-Best-Practices-67-320.jpg)



![[Cover] zeropointdevelopment.com
[3] jamesclear.com/sun-tzu-habits
[9] activerain.com
[10] mybroadband.co.za
[11] amazon.com
[18] lastpass.com
[23] zeropointdevelopment.com
[29] managewp.com
[33] wordpress.org
[35] wordpress.org
[39] promptwebhosting.com.au
[45] zeropointdevelopment.com
[47] zeropointdevelopment.com
[48] mobyware.ru
[52] roots.io
[53] ibmsystemsmag.com
[54] wordpress.org
[55] wordpress.org
[58] gobalakrishnan.com
[59] trickytechs.com/wpbeginner.com
[61] zeropointdevelopment.com
[63] wp-stream.com
[69] cloudflare.com
[72] zeropointdevelopment.com
[Back Cover] zeropointdevelopment.com
Note: This presentation may contain affiliate
links.
@DeveloperWil #wpsyd](https://image.slidesharecdn.com/wordpress-security-best-practices-2017-update-171128013605/85/WordPress-Security-Best-Practices-73-320.jpg)