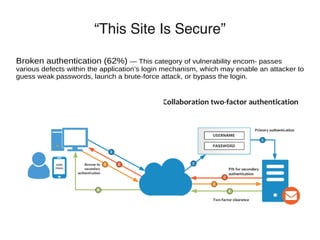
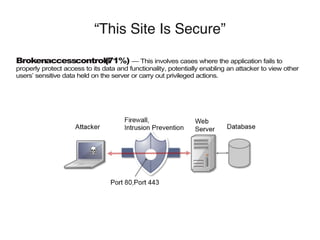
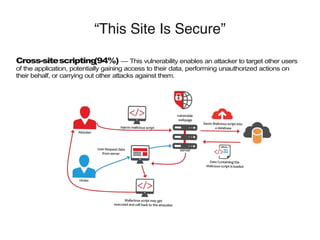
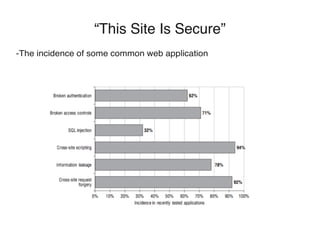
Common web applications include shopping, social networking, banking, web search, auctions, gambling, blogs, web mail, and wikis. These applications often contain highly sensitive data and functionality for HR, administration, collaboration, business software, email, and office applications. While many sites claim to be secure using SSL and PCI compliance, vulnerabilities are still common, including broken authentication, access controls, SQL injection, cross-site scripting, information leakage, and cross-site request forgery. The OWASP organization provides free resources to help address security issues in web applications.