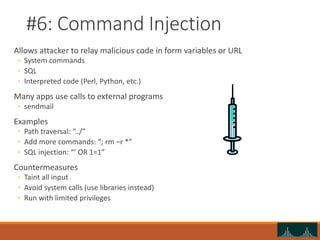
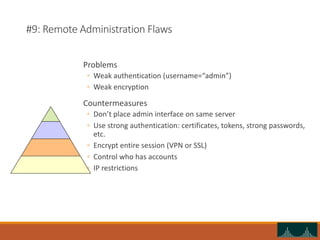
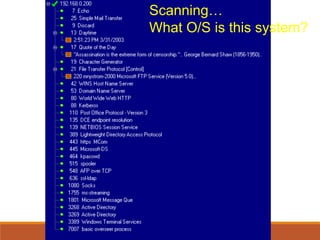
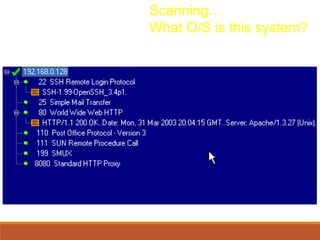
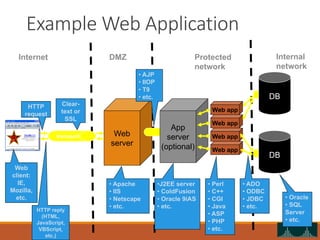
This document discusses web security and common web application vulnerabilities. It begins by outlining common goals of attacks such as stealing data, blackmail, demonstrating vulnerabilities, and damaging reputation. It then warns that security tools can be dangerous and authorities are prosecuting hackers. The document goes on to list commonly attacked services like SMTP, RPC, FTP, and web servers. It provides details on how to scan for vulnerabilities and outlines the OWASP top 10 security risks like unvalidated parameters, broken access control, cross-site scripting, and improper error handling. Throughout it provides examples of exploits and recommendations for mitigations.








![#5: Buffer Overflows
Mostly affects web/app servers
Can affect apps/libraries too
Goal: crash the target app and get a shell
Buffer overflow example
◦ echo “vrfy `perl –e ‘print “a” x 1000’`” |nc
www.targetsystem.com 25
◦ Replace all those “a”s with something like this…
◦ char shellcode[] = “xebxlfx5ex89x76x08…”
Countermeasures
◦ Keep up with bug reports/patches
◦ Code reviews
◦ Run with limited privileges
◦ Use “safer” languages like Java](https://image.slidesharecdn.com/websecurity-230129120544-e0b5cea7/85/Web-Security-14-320.jpg)