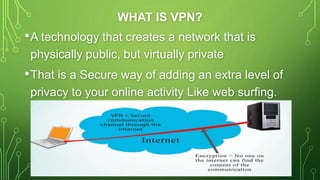
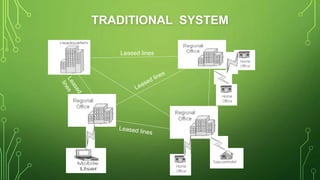
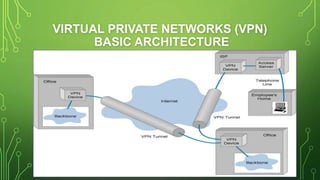
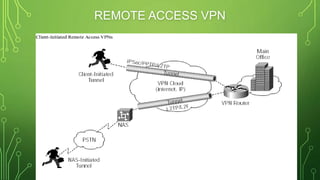
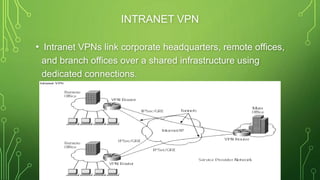
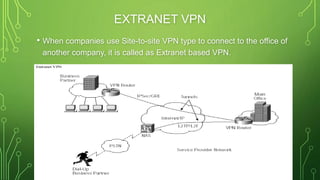
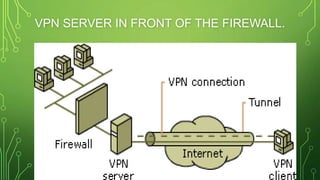
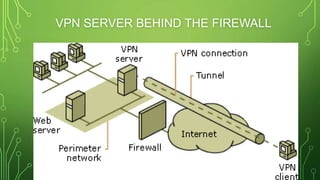
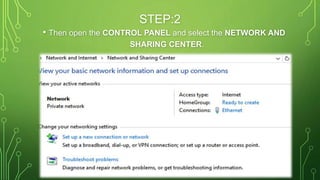
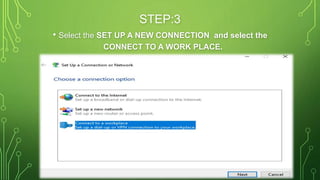
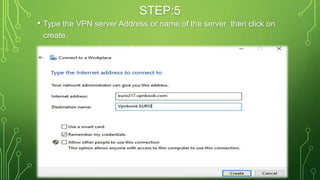
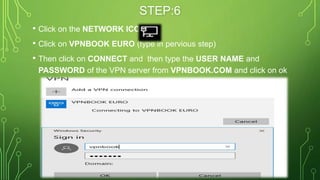
The document provides an overview of Virtual Private Networks (VPNs), including their types such as remote access and site-to-site VPNs, as well as specific protocols like IPSec and SSL/TLS. It explains the benefits of using VPNs, including bypassing regional restrictions, enhancing online security, and enabling secure connections to remote networks. Additionally, it discusses the configuration of firewalls with VPN servers and the disadvantages of VPN usage.