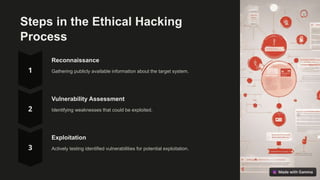
This document discusses ethical hacking and provides an overview of the key concepts and steps involved. It defines ethical hacking as authorized testing of computer systems to identify potential vulnerabilities in order to strengthen cybersecurity defenses. The document outlines the different types of hackers (black hat, white hat, grey hat), legal and ethical considerations, the main steps in the ethical hacking process (reconnaissance, vulnerability assessment, exploitation), and best practices for ethical hacking.