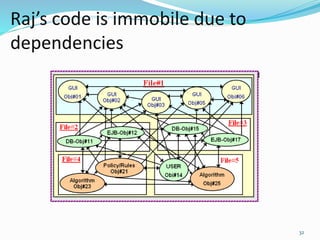
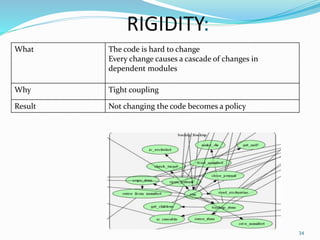
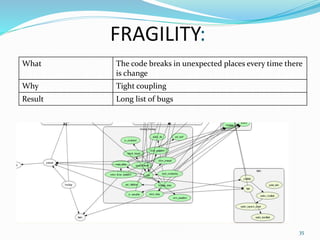
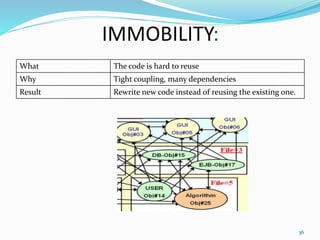
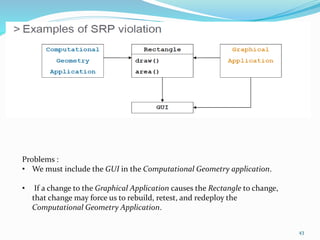
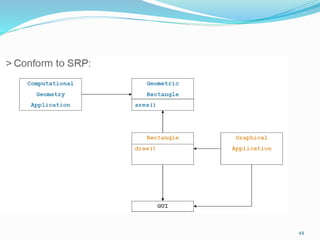
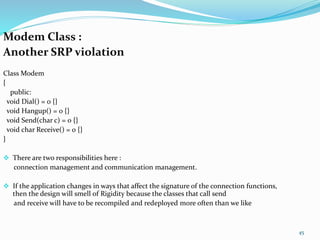
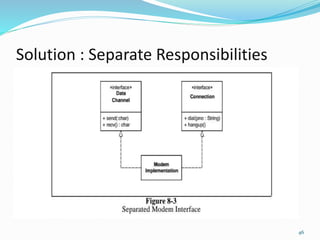
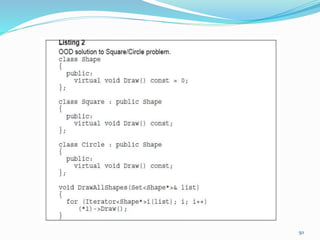
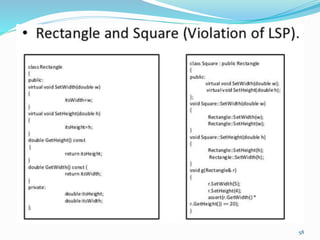
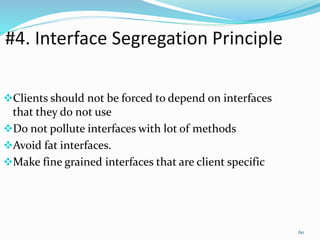
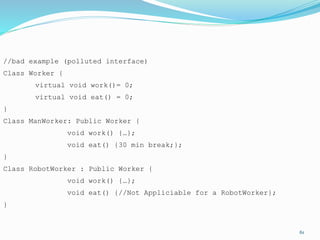
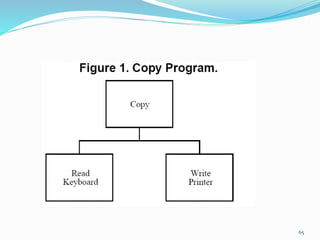
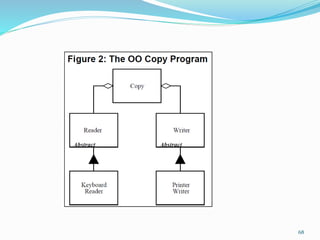
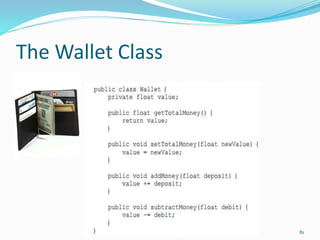
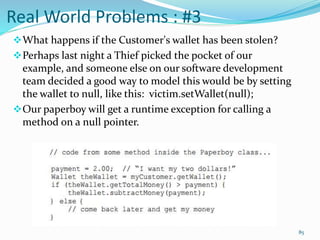
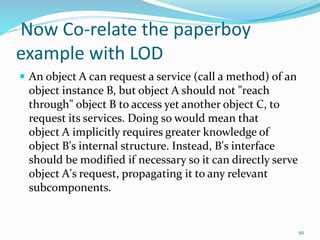
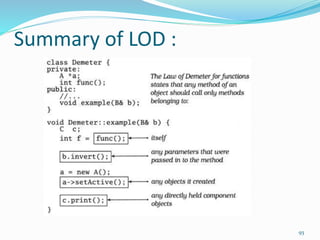
The document discusses key principles of software design, emphasizing object-oriented programming origins and practices. It introduces the Pimpl Idiom to reduce recompilation dependencies and outlines SOLID principles to avoid poor design and maintainability issues, using real-world examples and a fictional character, Rahul, to illustrate bad coding practices. Moreover, it highlights the Law of Demeter to promote information hiding and reduce tight coupling between objects.