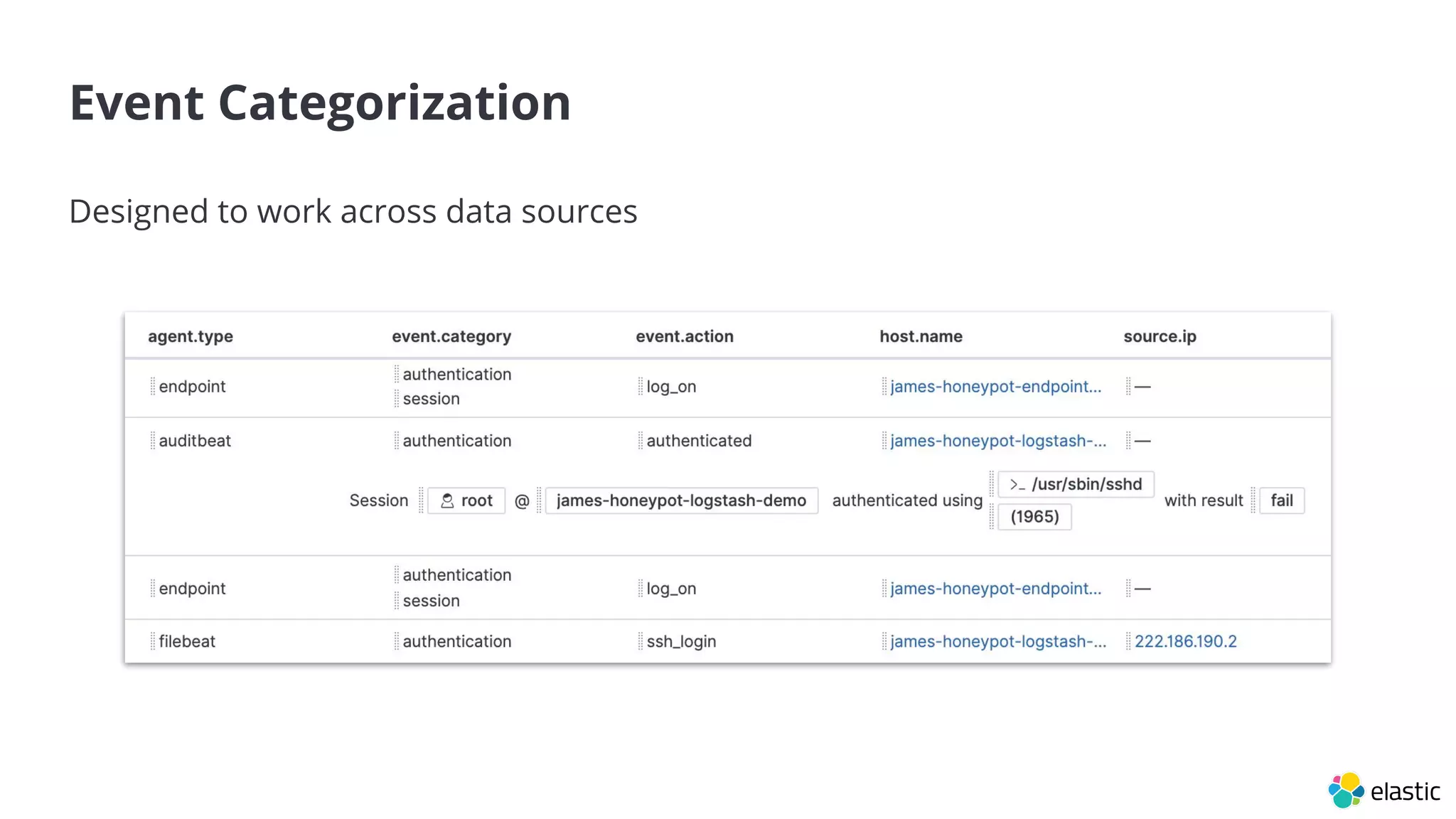
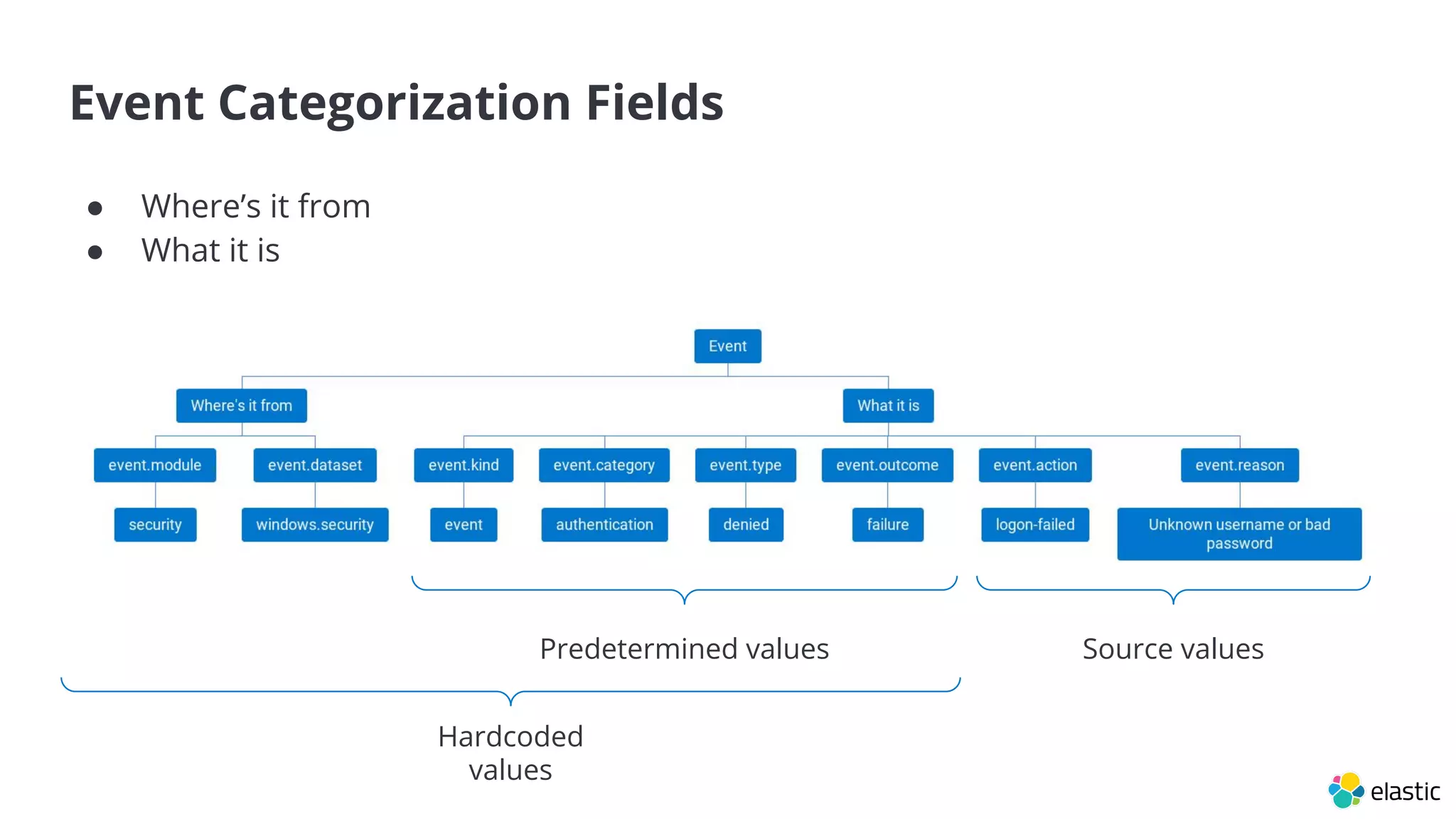
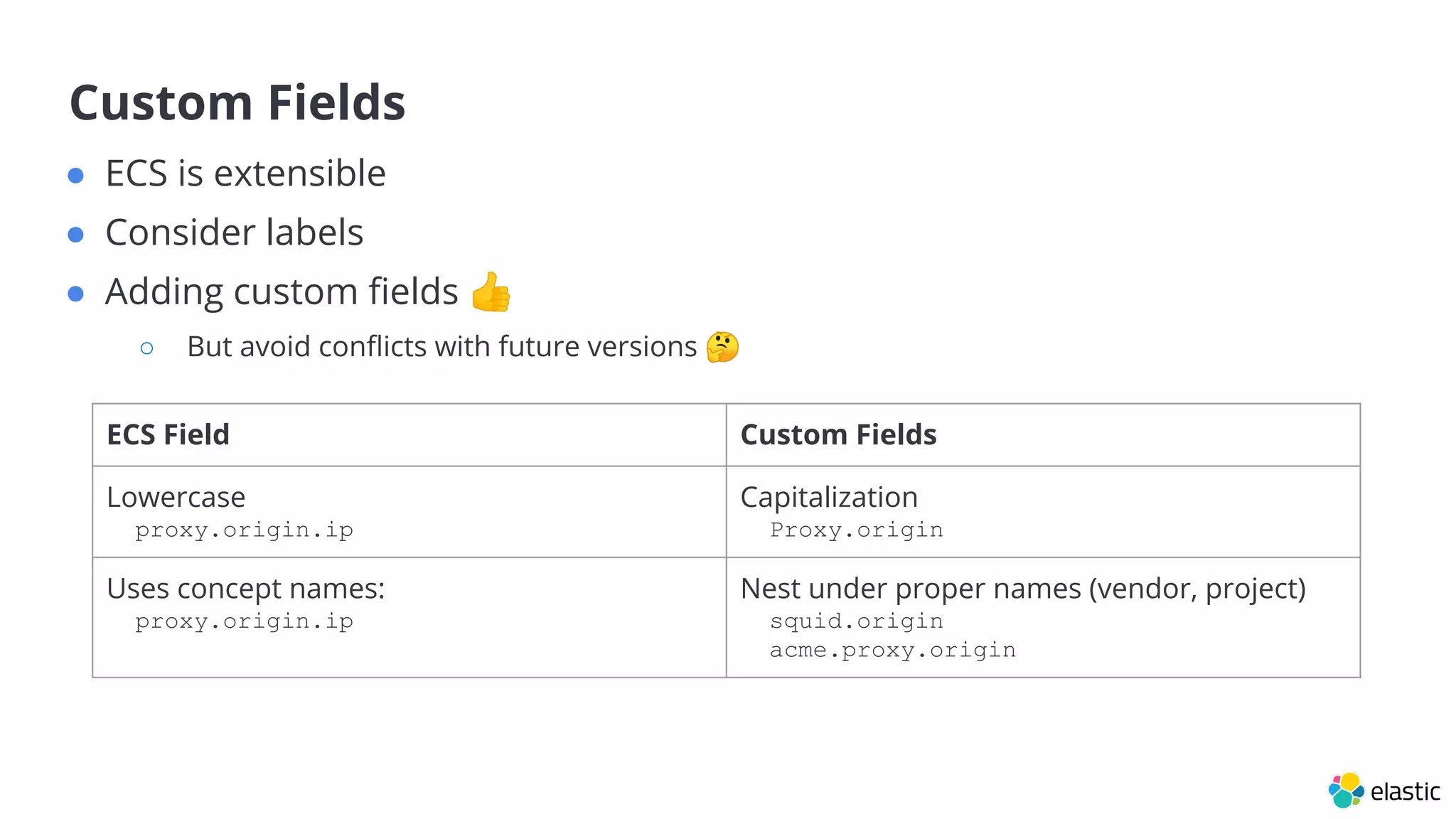
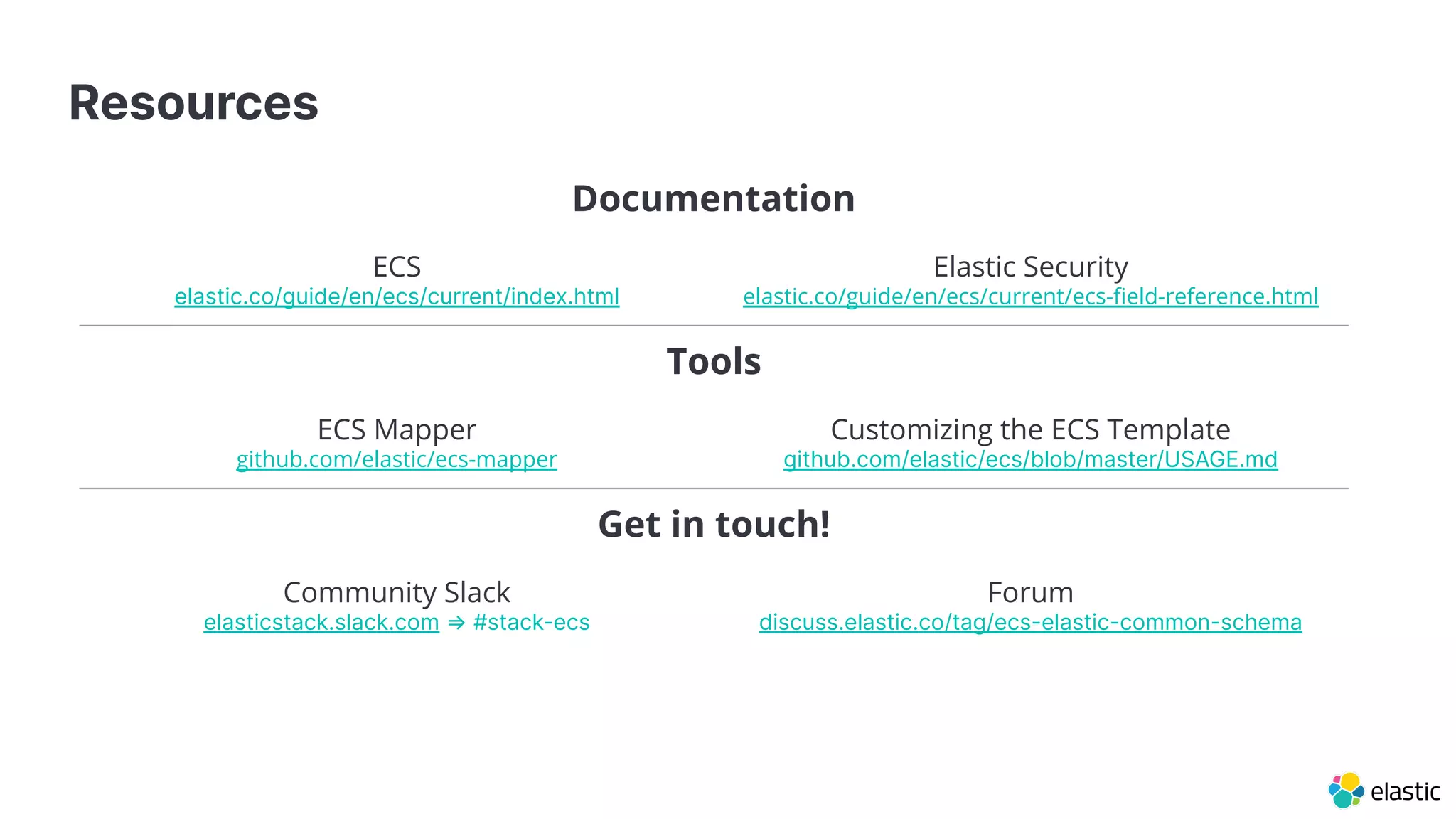
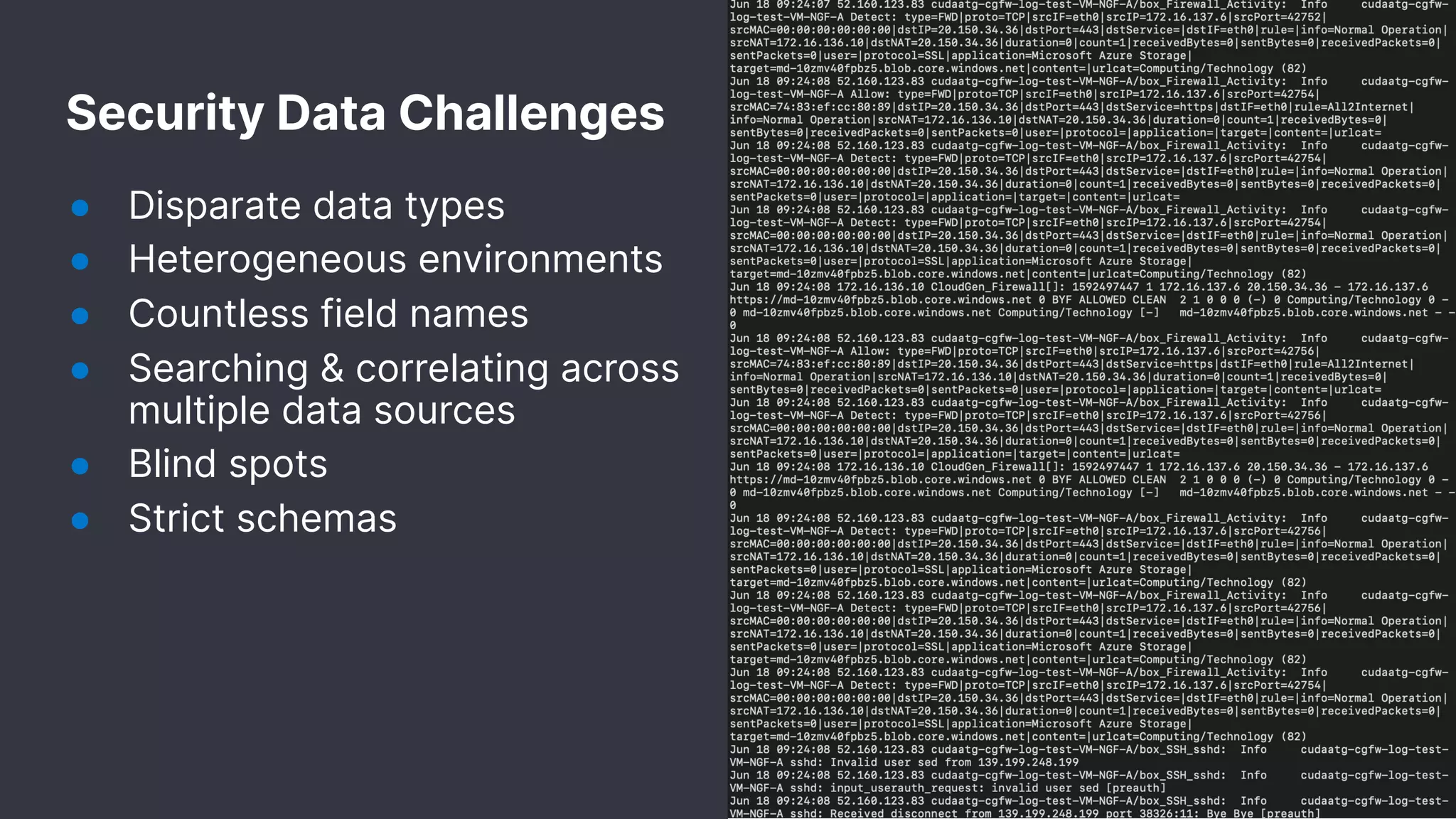
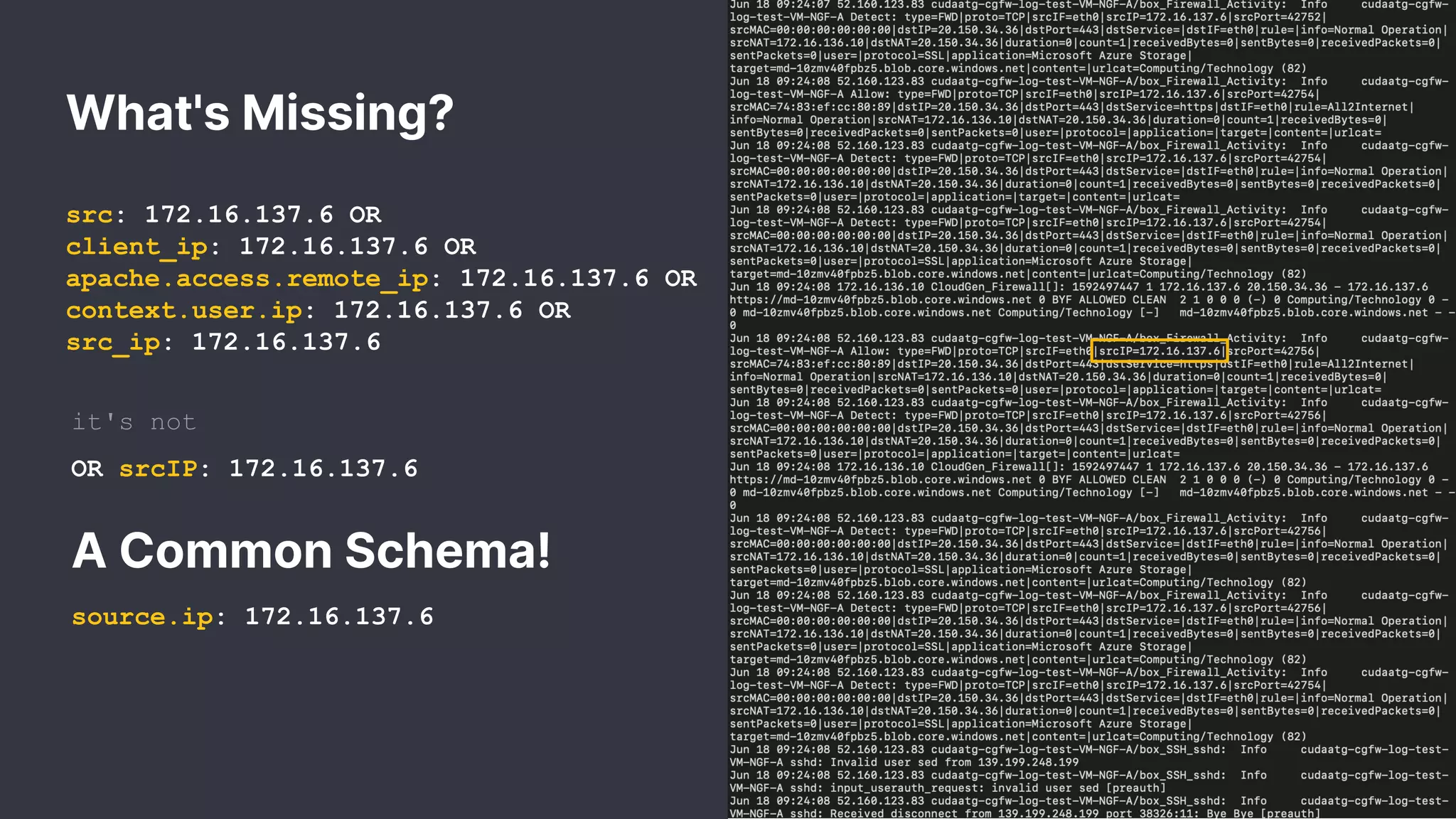
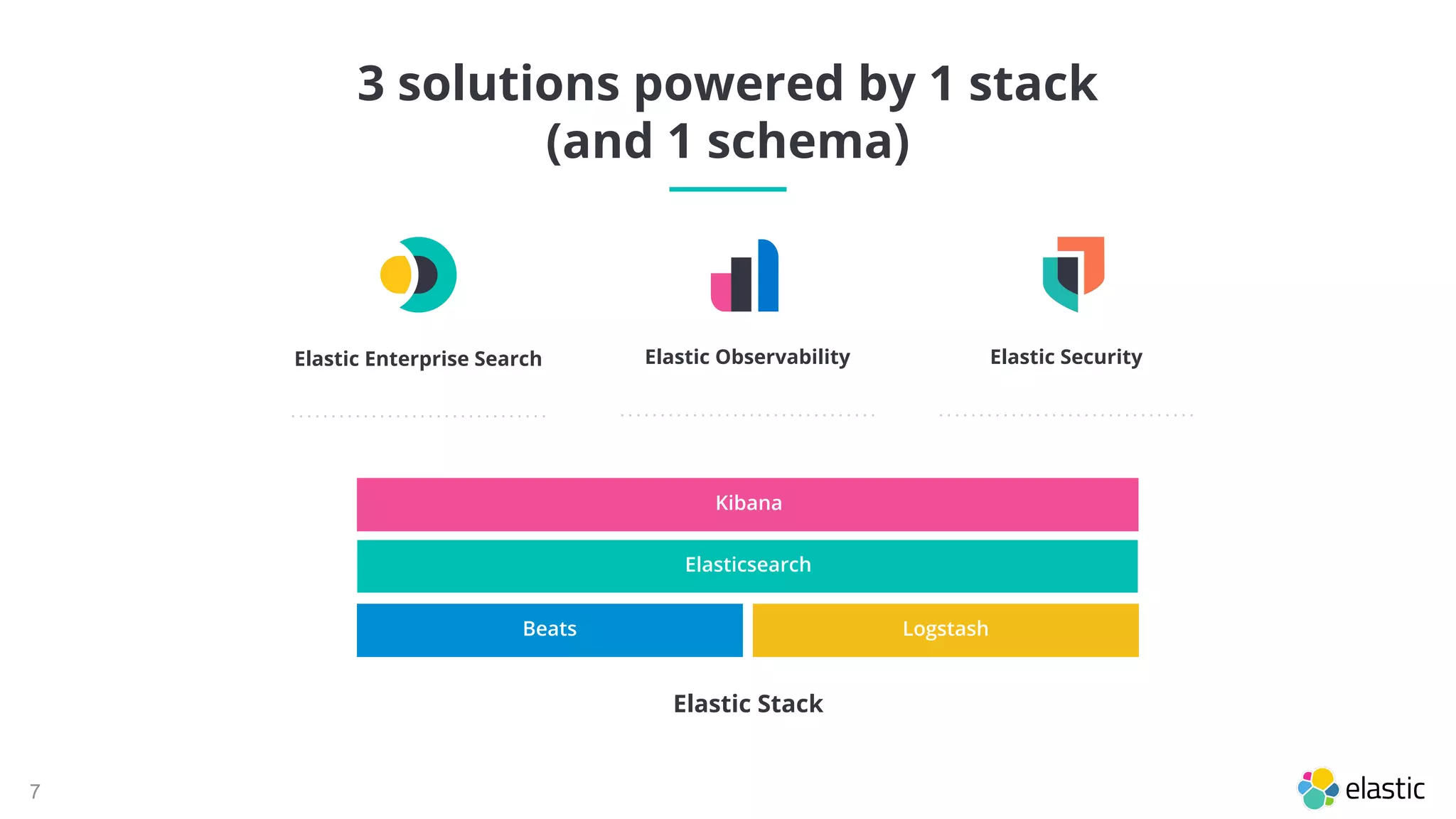
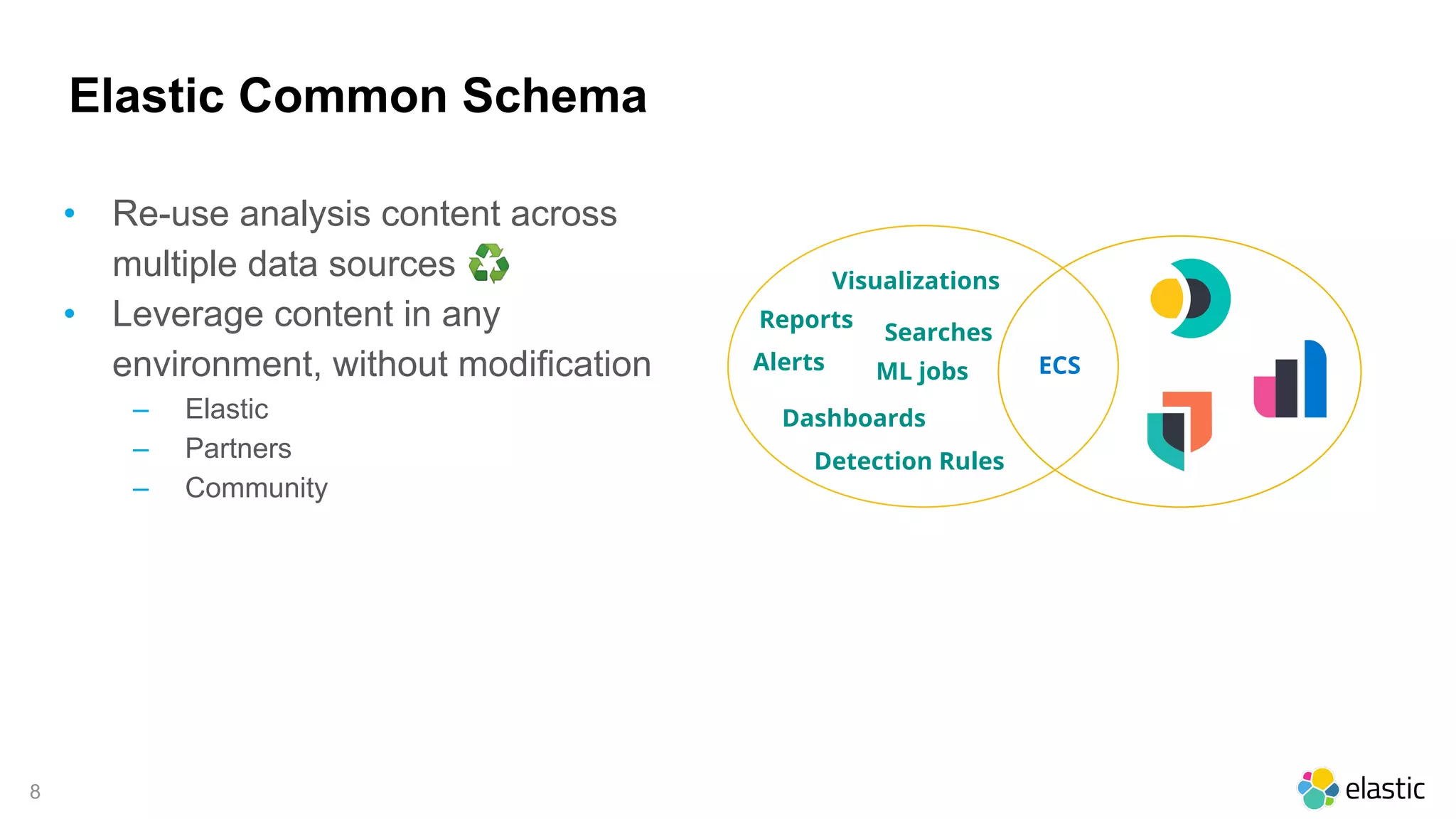
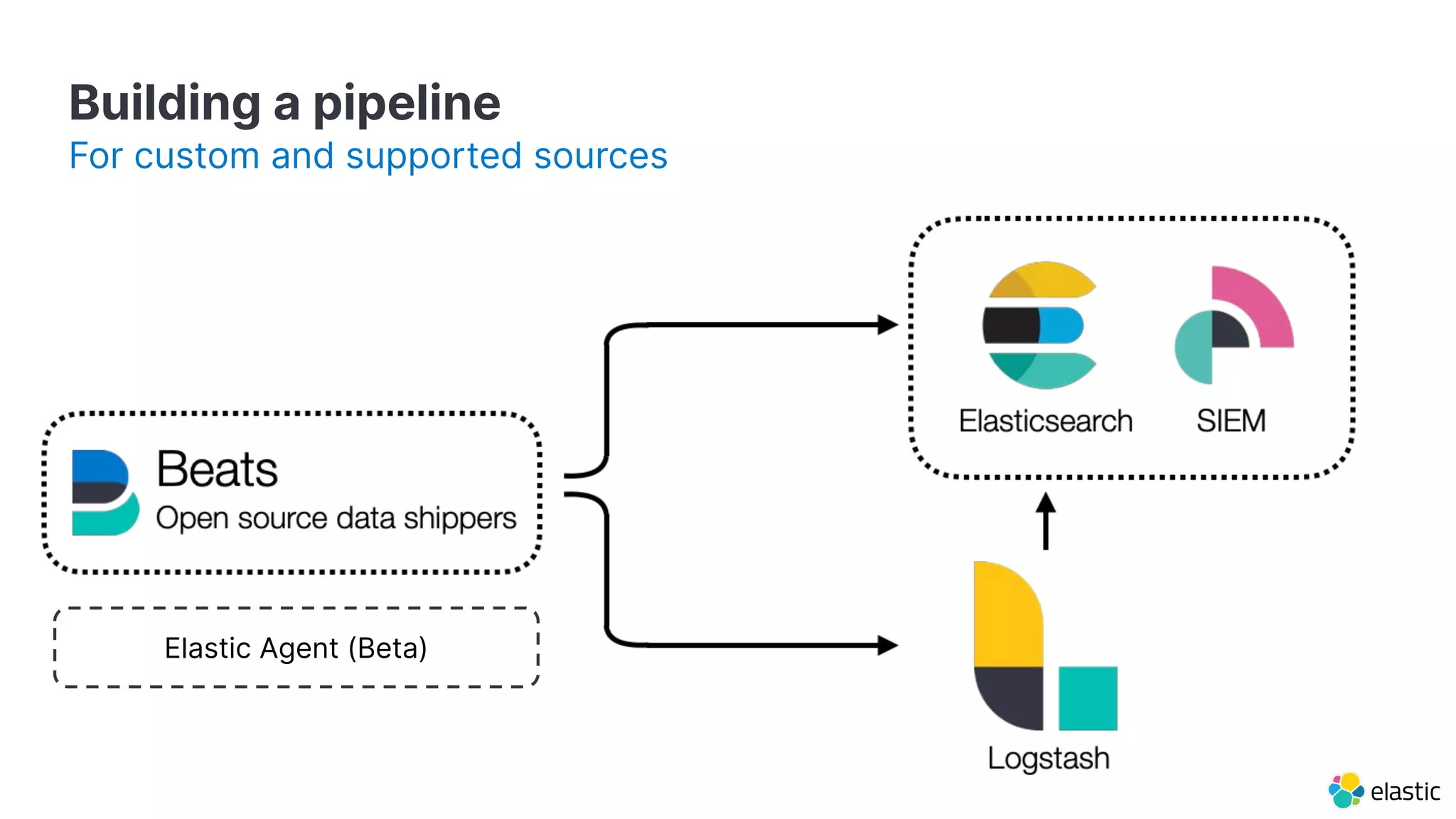
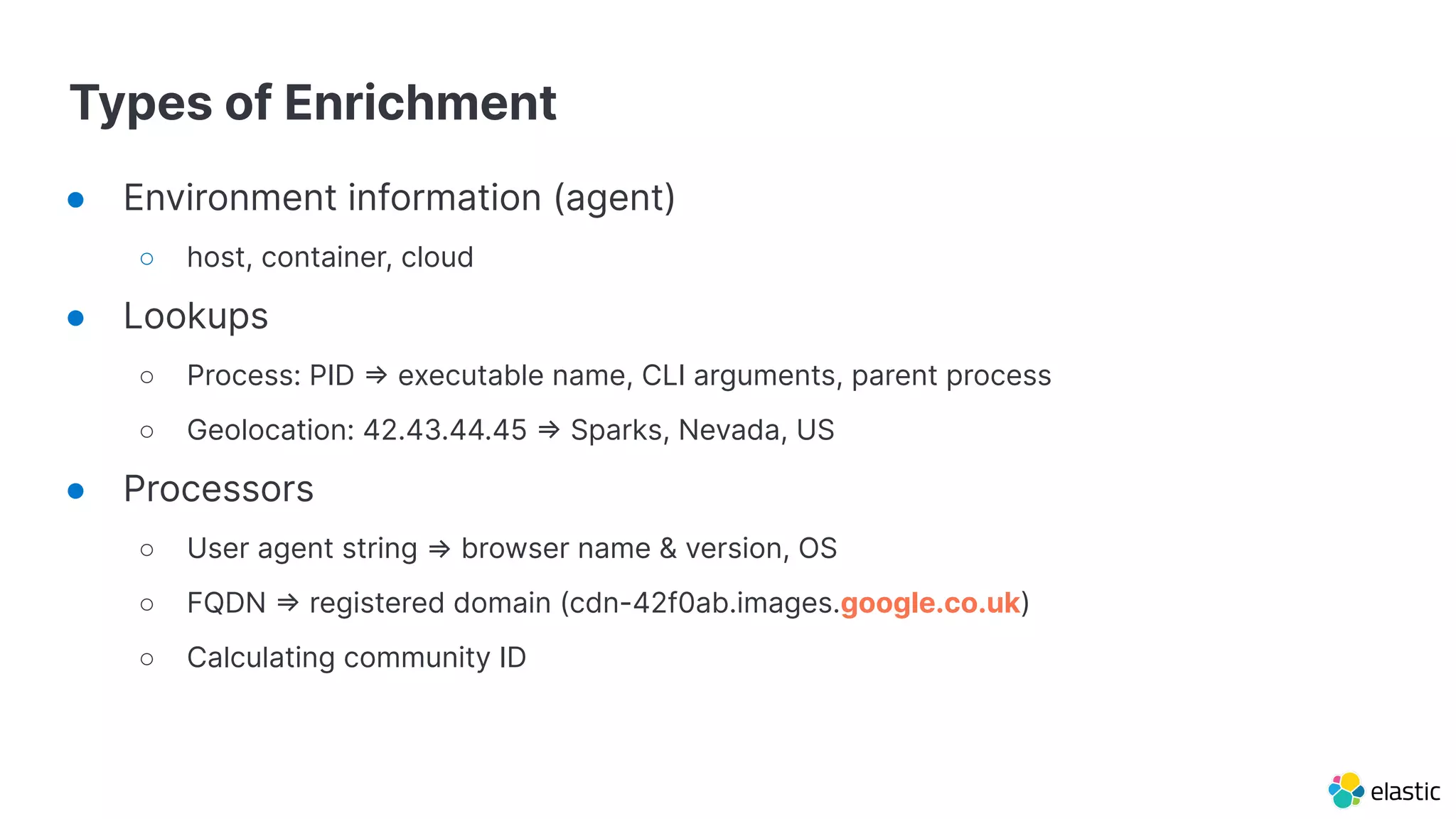
The document discusses the importance of normalizing security data using the Elastic Common Schema (ECS), which addresses challenges such as disparate data types and blind spots. It outlines ECS's role in providing a consistent data format for integrated security across various Elastic products and services, alongside available documentation and tools for mapping data to ECS. Key points include the significance of custom fields, integration capabilities, and resources for further community engagement.





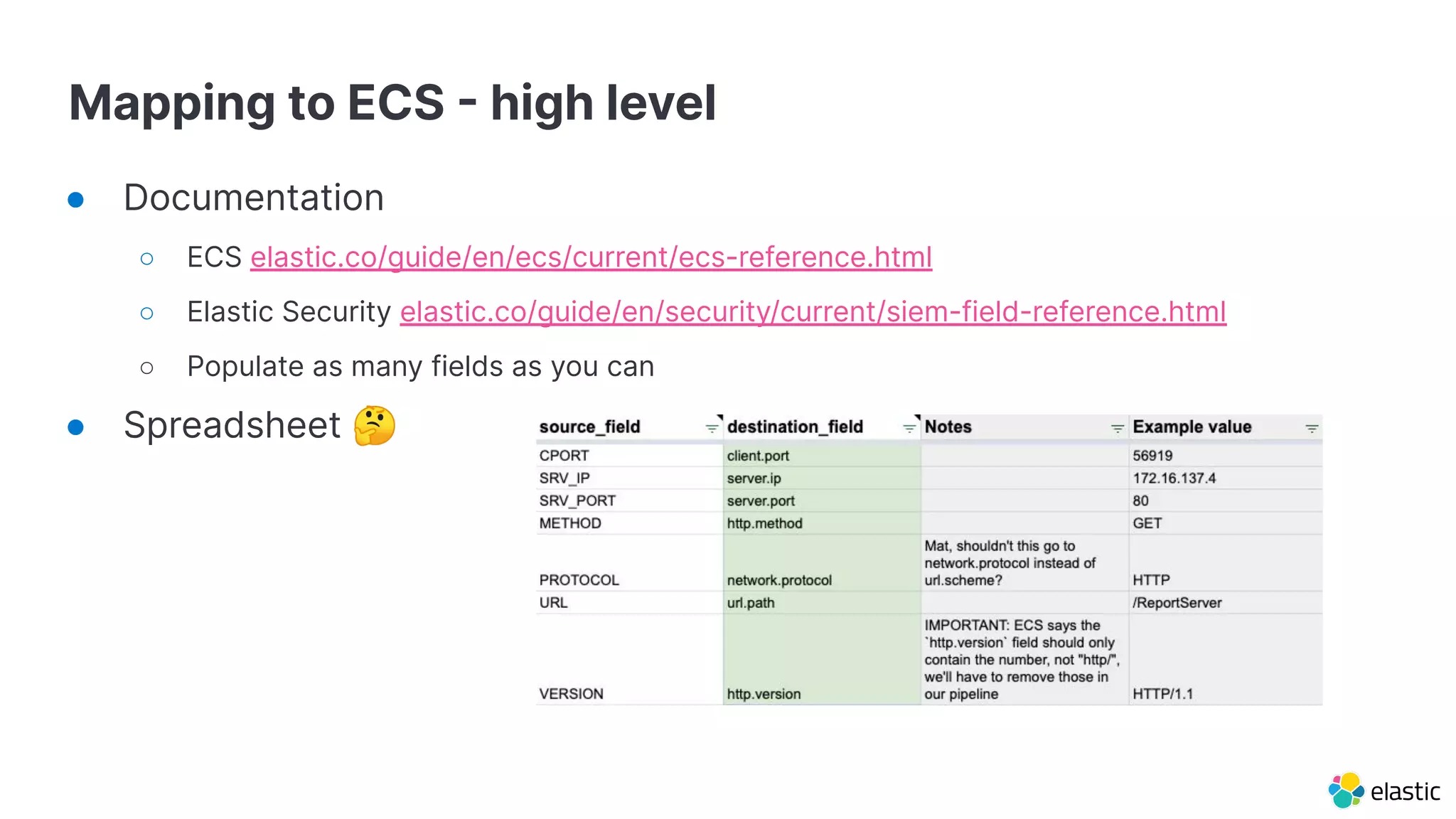
![Mapping to ECS field names
● Plaintext logs
○ Use ECS field names in your grok or dissect
● Structured events
○ Multiple field renames
○ ecs-mapper: mapping spreadsheet ⇒ 3 starter pipelines
useradd[12507]: new user: name=bob, UID=1002, GID=1003
%{DATA:process.name}[%{POSINT:process.pid}]: new user: name=%{DATA:user.name},
UID=%{NUMBER:user.id}, GID=%{NUMBER:group.id}](https://image.slidesharecdn.com/theimportanceofnormalizingyoursecuritydata-martinhynds-201030050530/75/The-importance-of-normalizing-your-security-data-to-ECS-12-2048.jpg)
![Building on your logs
{
"message": "pam_unix(su:session)...",
"agent": {
"type": "filebeat",
"version": "7.9.1"
},
"host": {
"name": "bob-laptop",
"id": "7fa34c7914aa4e4...",
"os": {
"name": "Ubuntu",
"version": "18.04.4 LTS"
},
"ip": [ "10.0.2.15" ]
},
su[9000]: pam_unix(su:session): session opened for user root by vagrant(uid=0)
"process": {
"start": "2020-08-26T17:20:38.430Z",
"pid": 9000,
"name": "su",
"executable": "/bin/su",
"parent": {
"pid": 8999,
"name": "sudo",
"executable": "/usr/bin/sudo"
}
}
}](https://image.slidesharecdn.com/theimportanceofnormalizingyoursecuritydata-martinhynds-201030050530/75/The-importance-of-normalizing-your-security-data-to-ECS-14-2048.jpg)