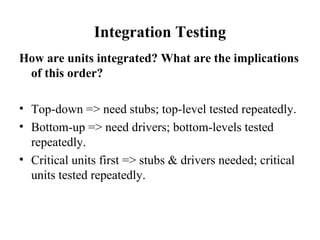
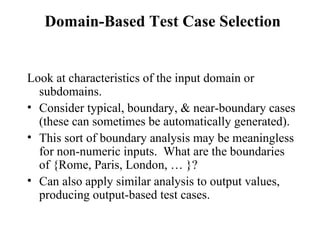
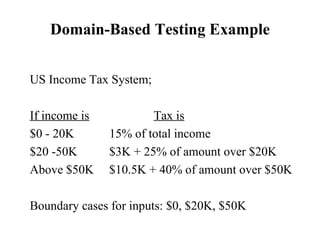
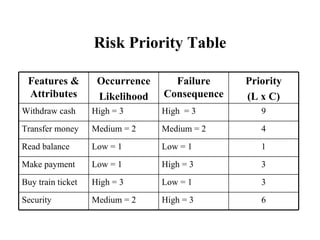
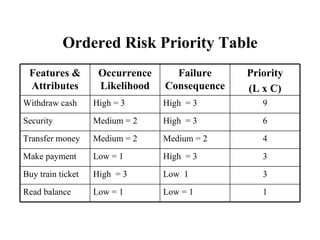
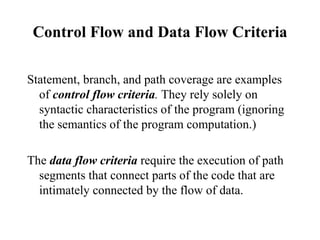
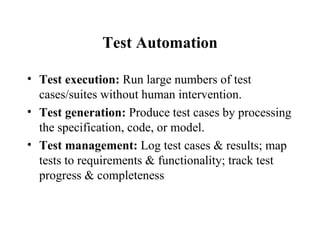
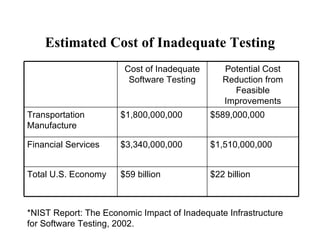
The document discusses various techniques for software testing including unit testing, integration testing, system testing, and regression testing. It describes challenges in software testing like determining correctness of outputs and selecting test cases. Different strategies for test case selection are covered such as code-based, specification-based, operational distribution-based, domain-based, random testing, and risk-based testing.