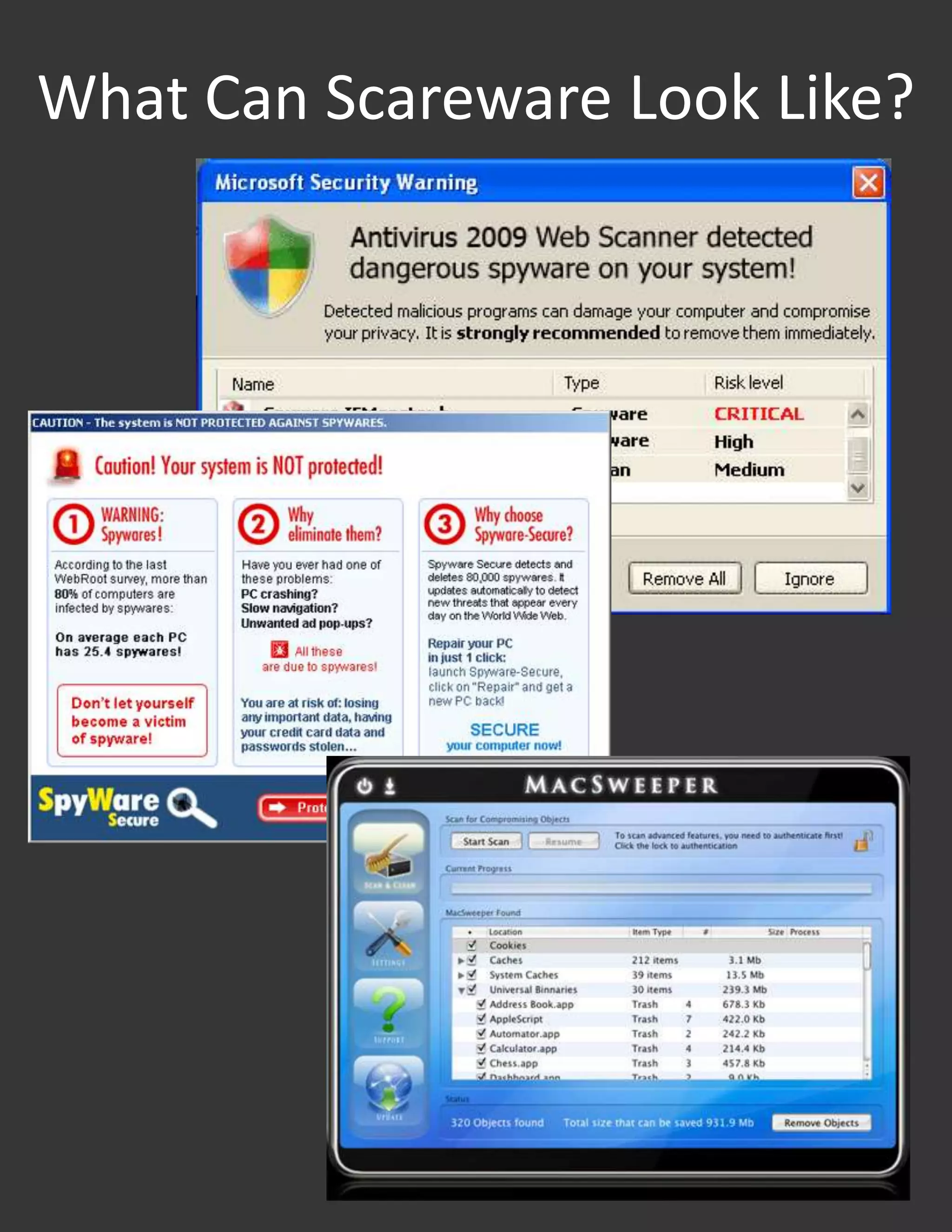
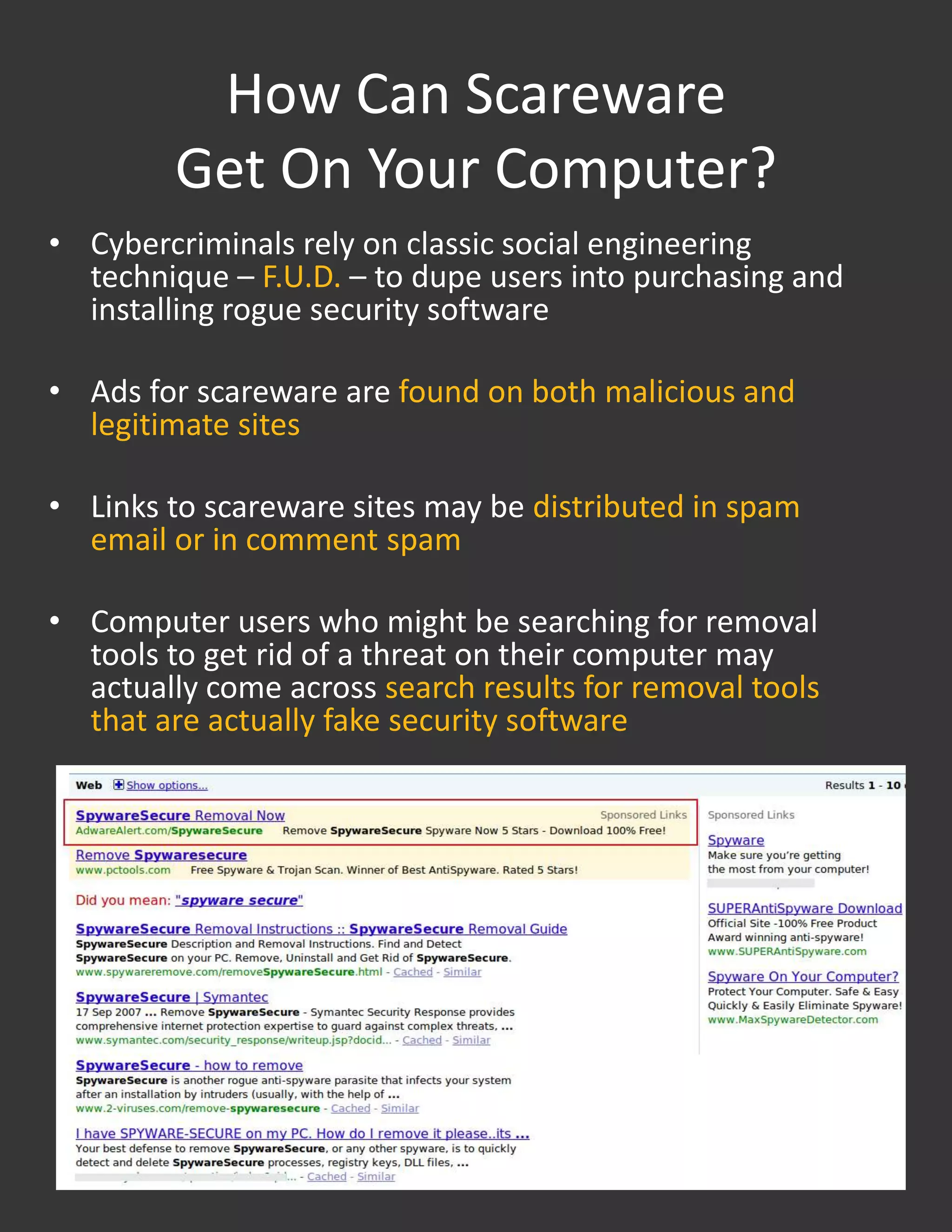
The Symantec report details the rise of scareware, a form of rogue security software that tricks users into purchasing fake security solutions through fear tactics and social engineering. Scammers earn substantial profits using an affiliate model, often leading to identity theft and weakening of actual security on users' computers. The report highlights the widespread nature of this issue, with 43 million installation attempts reported and various prevention strategies suggested for consumers.