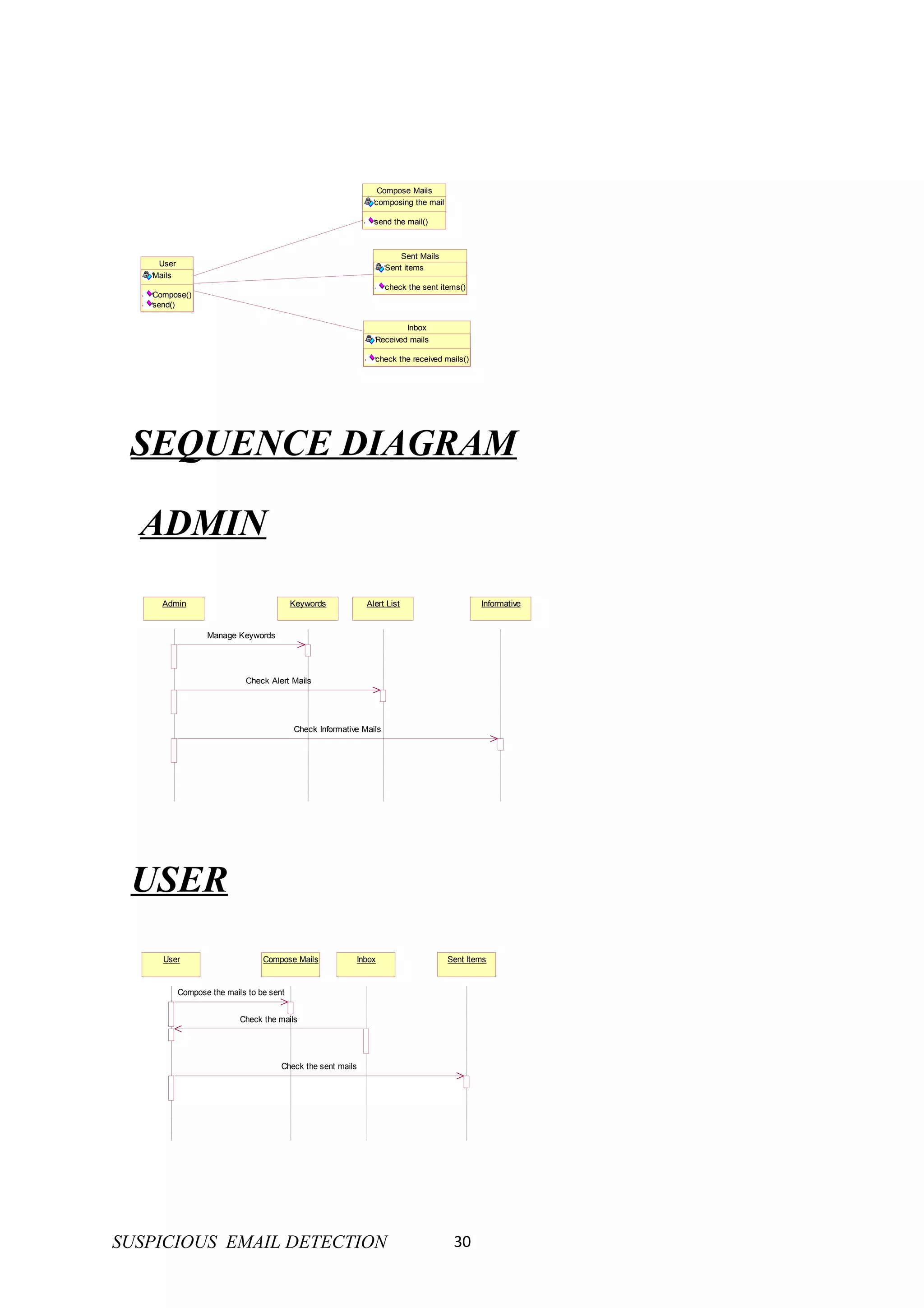
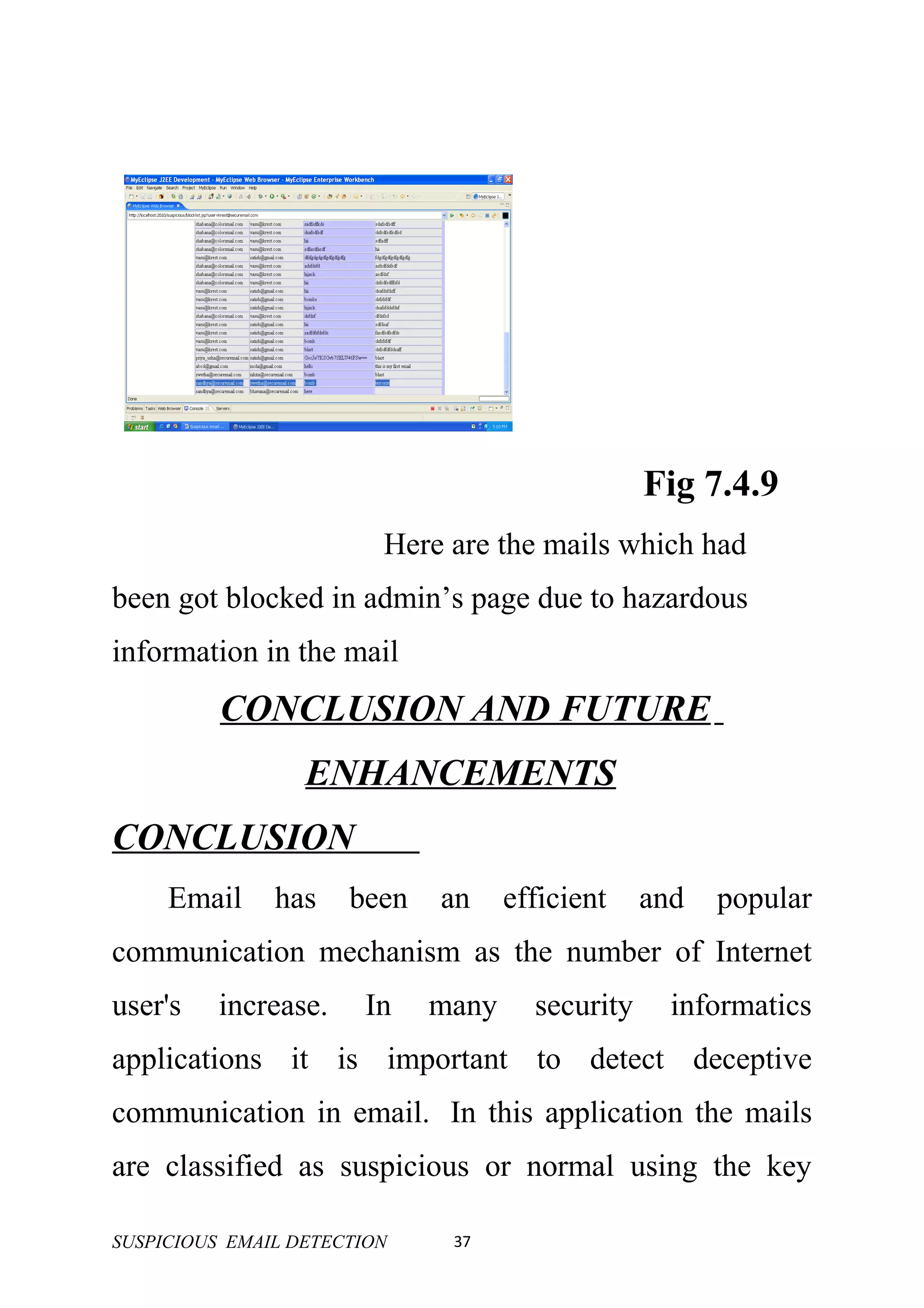
This document provides an overview and outline for a project on detecting suspicious emails. It discusses the scope, purpose, and architecture of the project. It also includes sections on technologies involved like Java, servlets, JSP, JDBC, HTML, and JavaScript. The document outlines components like the login module, registration module, administration module, encryption module, user module, and mailing module. It concludes with future plans like screens, conclusion, and enhancements.