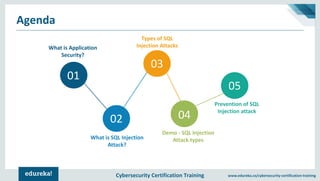
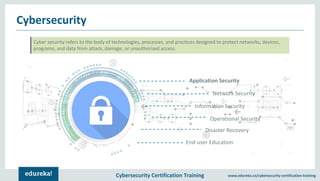
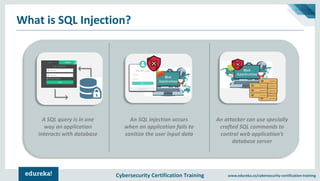
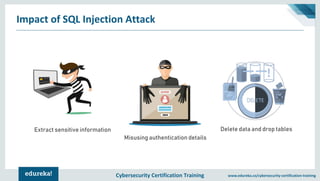
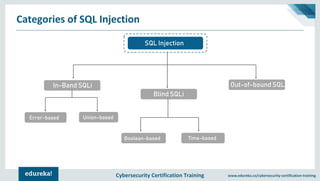
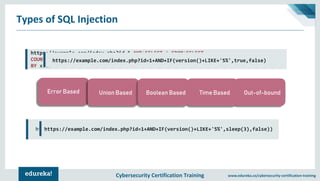
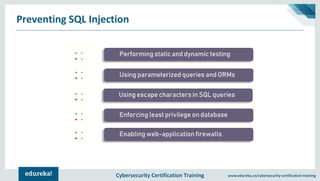
The document outlines cybersecurity certification training focused on application security, particularly targeting SQL injection attacks. It explains what SQL injection is, its types, and the potential impacts, including extracting sensitive information and deleting data. It also provides prevention strategies such as static and dynamic testing, using parameterized queries, and implementing web-application firewalls.