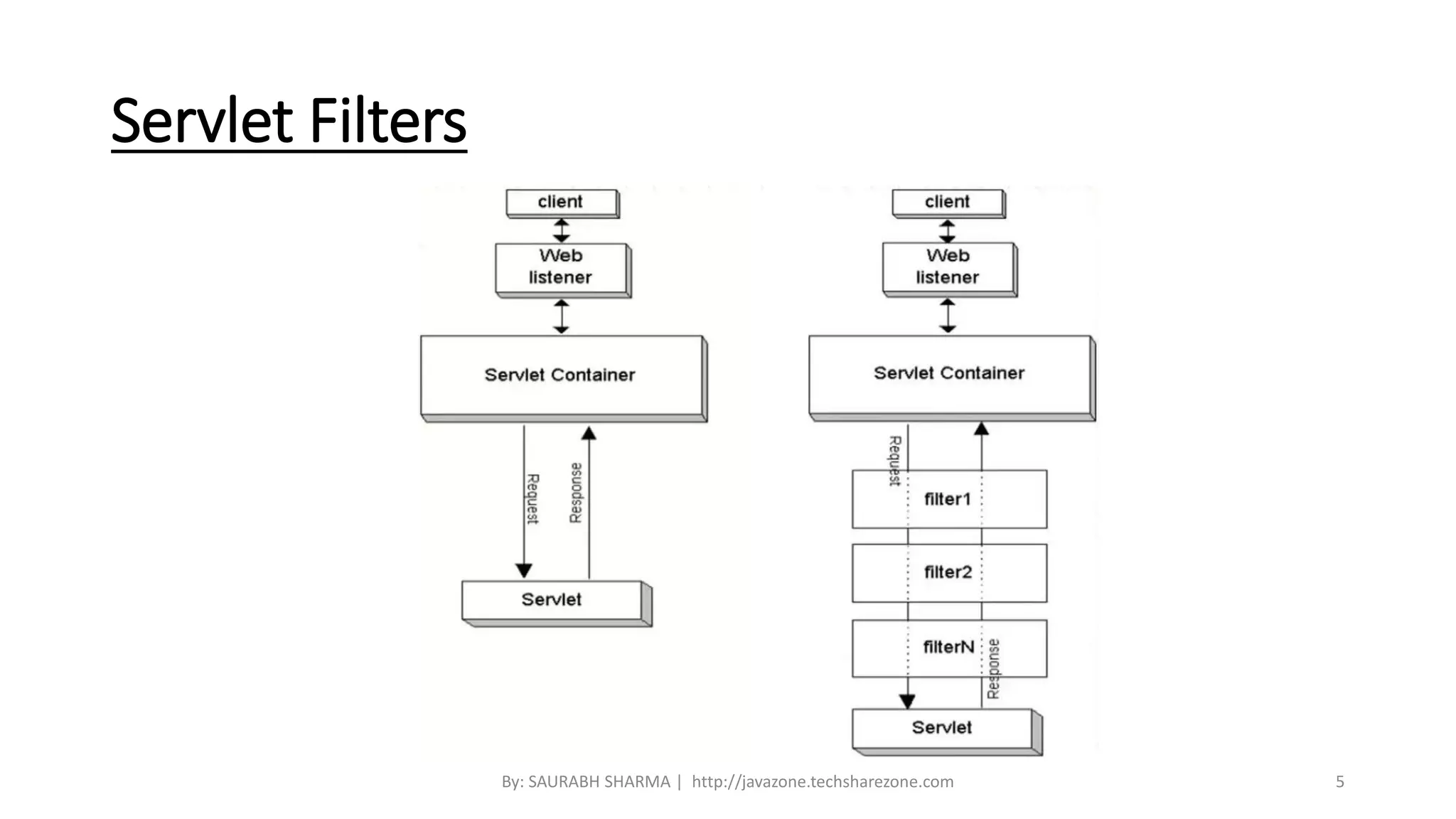
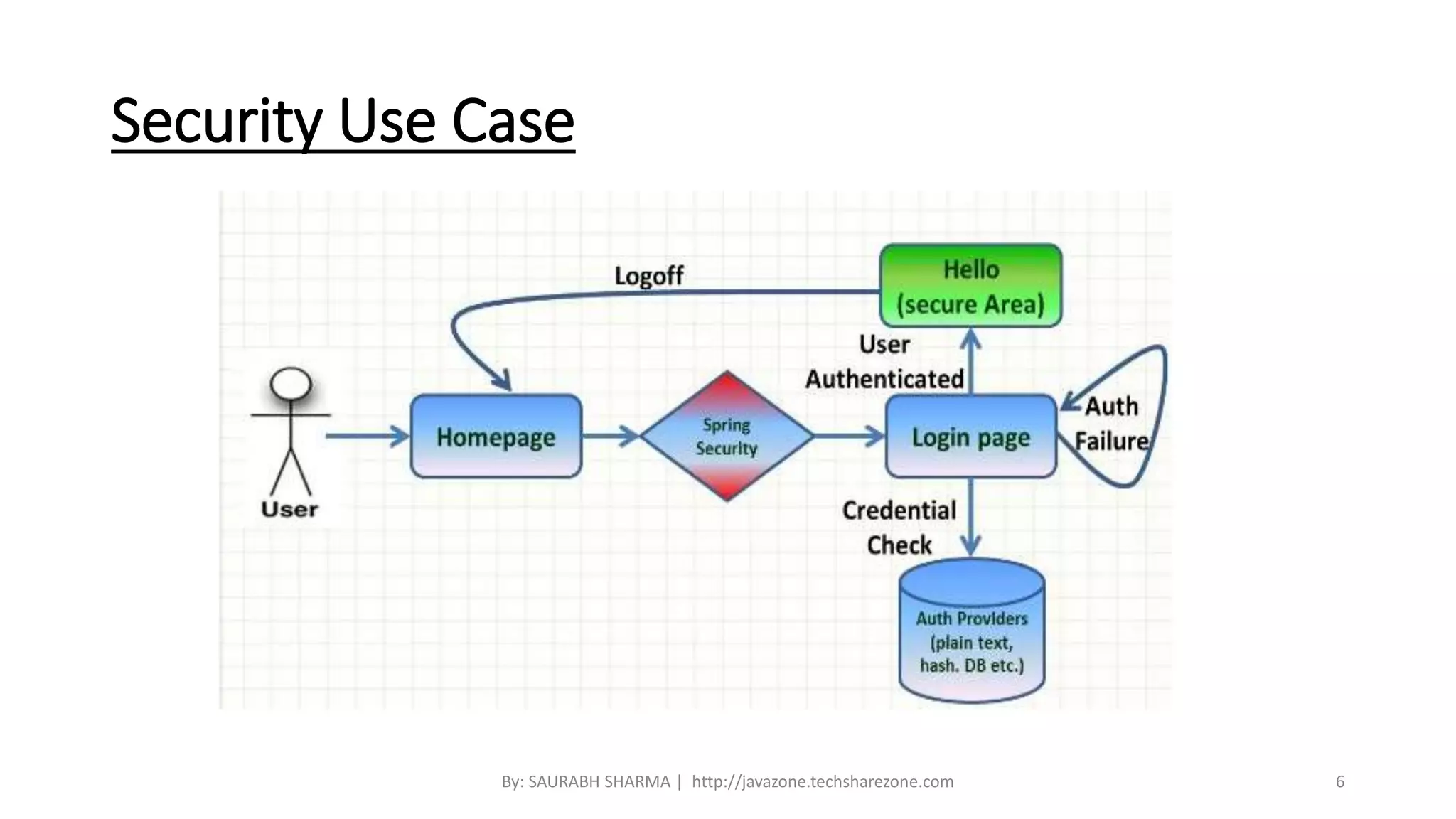
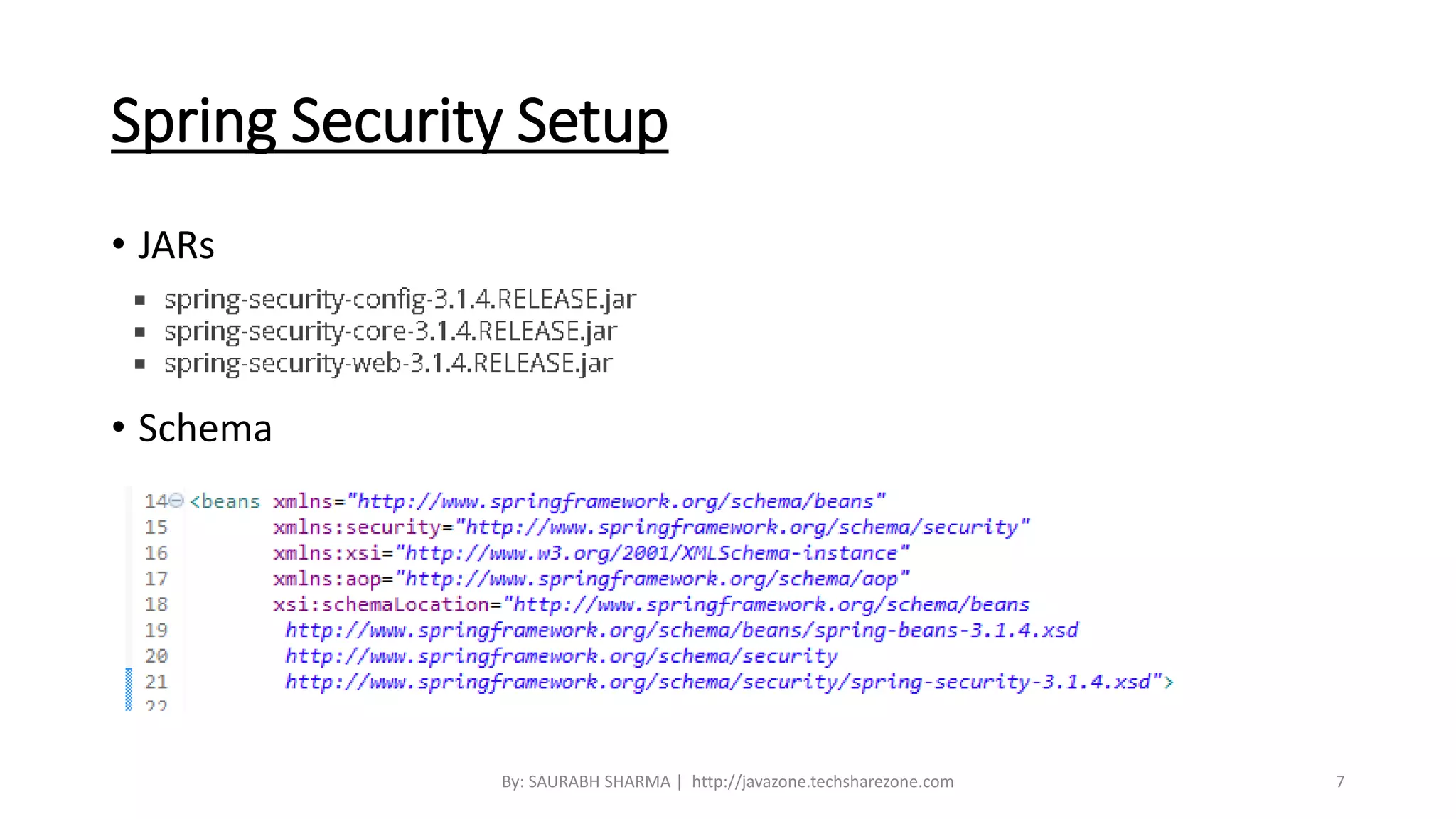
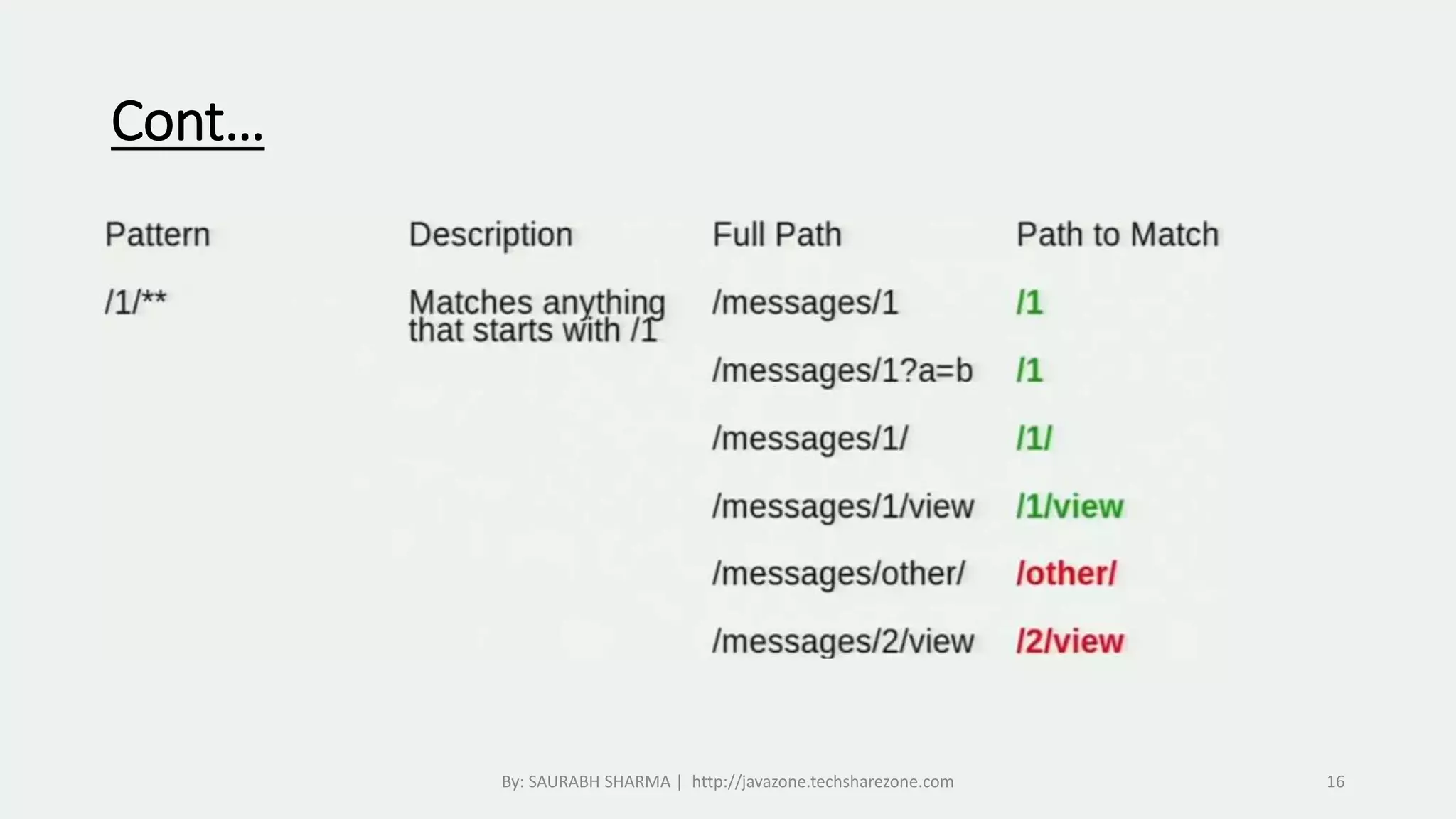
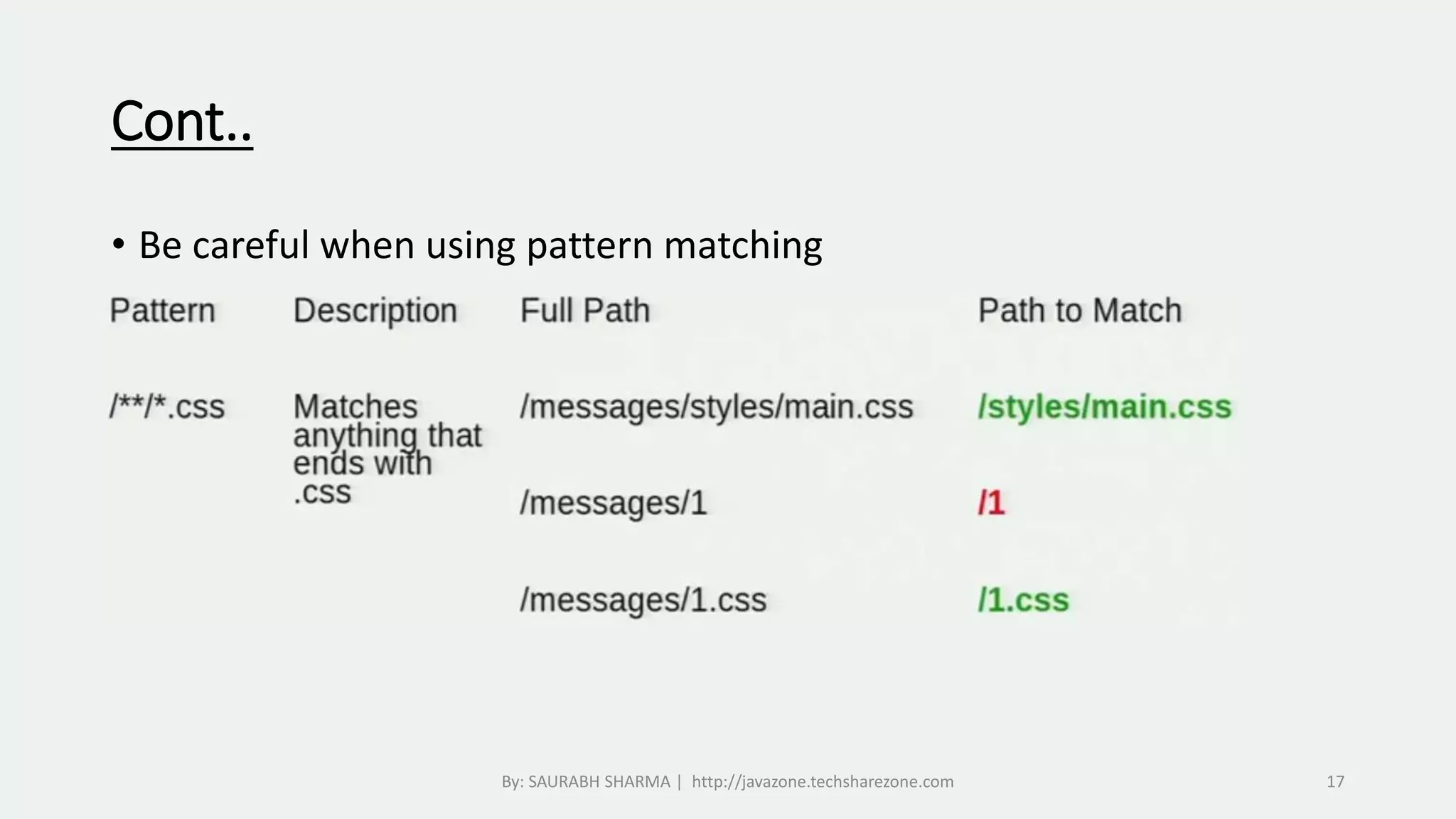
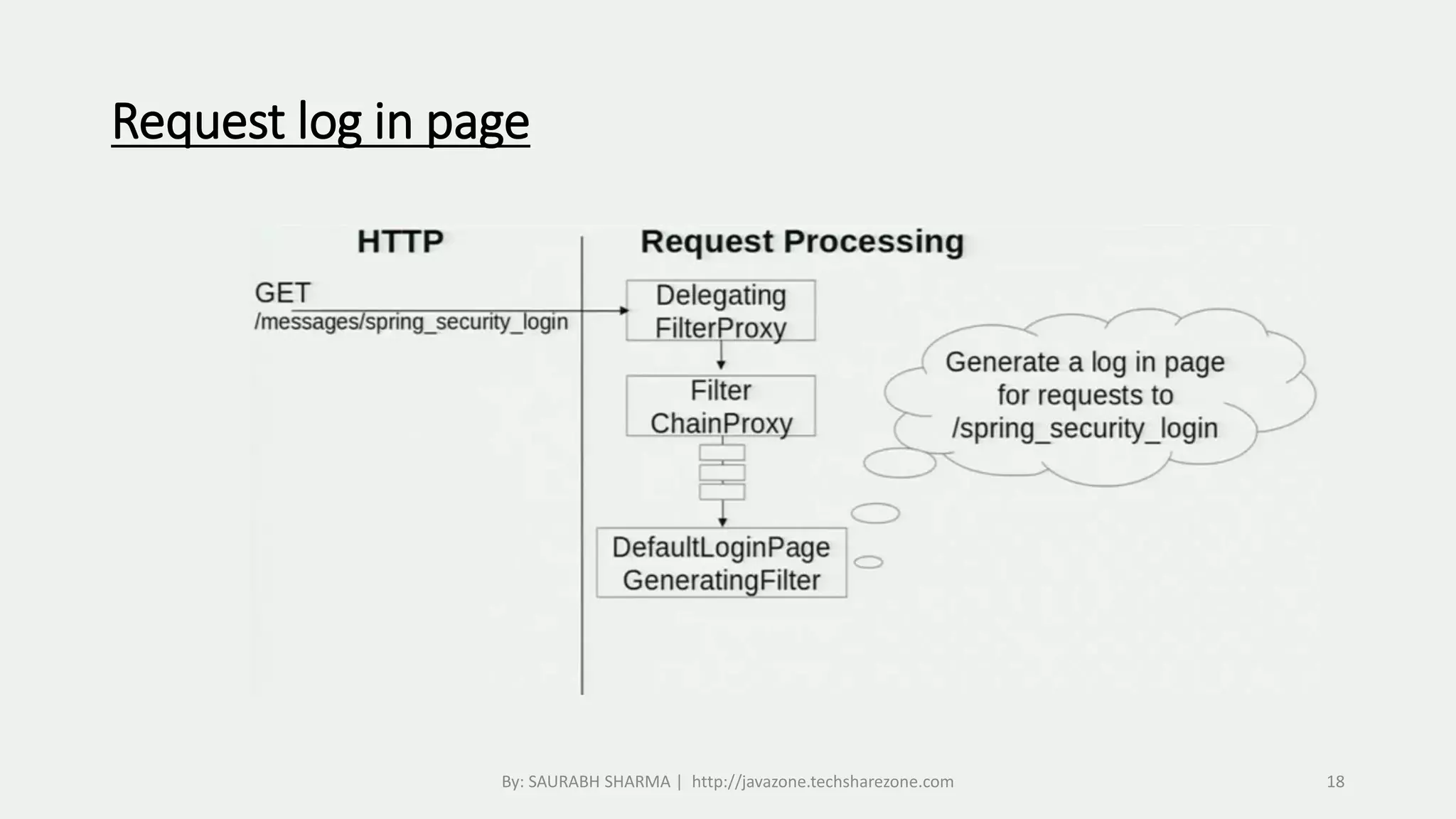
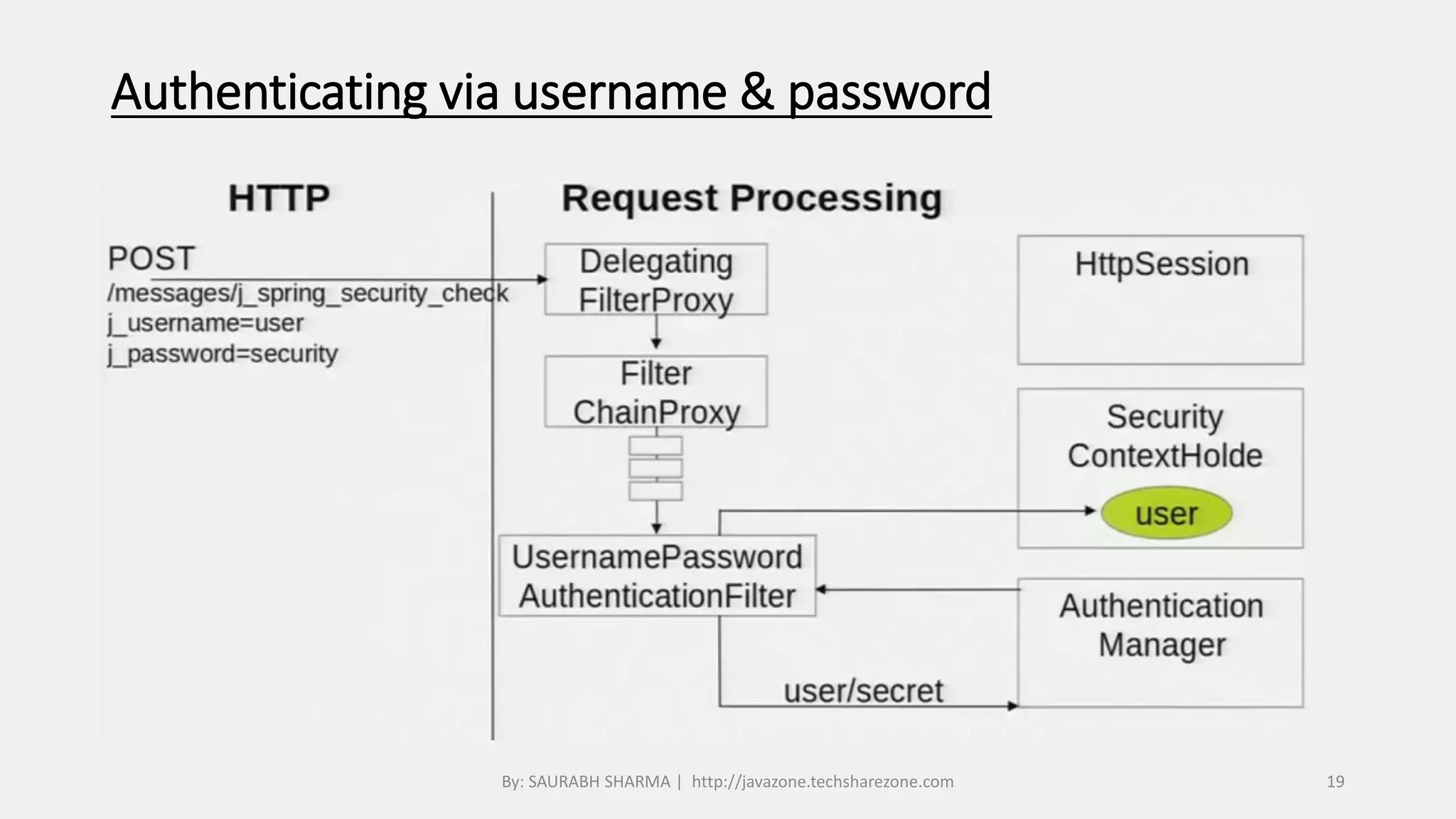
This document provides an overview of Spring Security, including what it is, how it handles authentication and authorization, and how to configure it. Spring Security provides comprehensive security services for Java enterprise applications, including authentication support for databases, LDAP, CAS, and custom authentication. It handles authentication through establishing a user's identity and authorization through controlling user access to resources. The document discusses configuring Spring Security through Java configuration and XML files, and covers topics like security filters, access control patterns, and the basic authentication process.
![Spring Security
[ Security Reloaded ]](https://image.slidesharecdn.com/springsecurity-170116065006/75/Spring-security-1-2048.jpg)