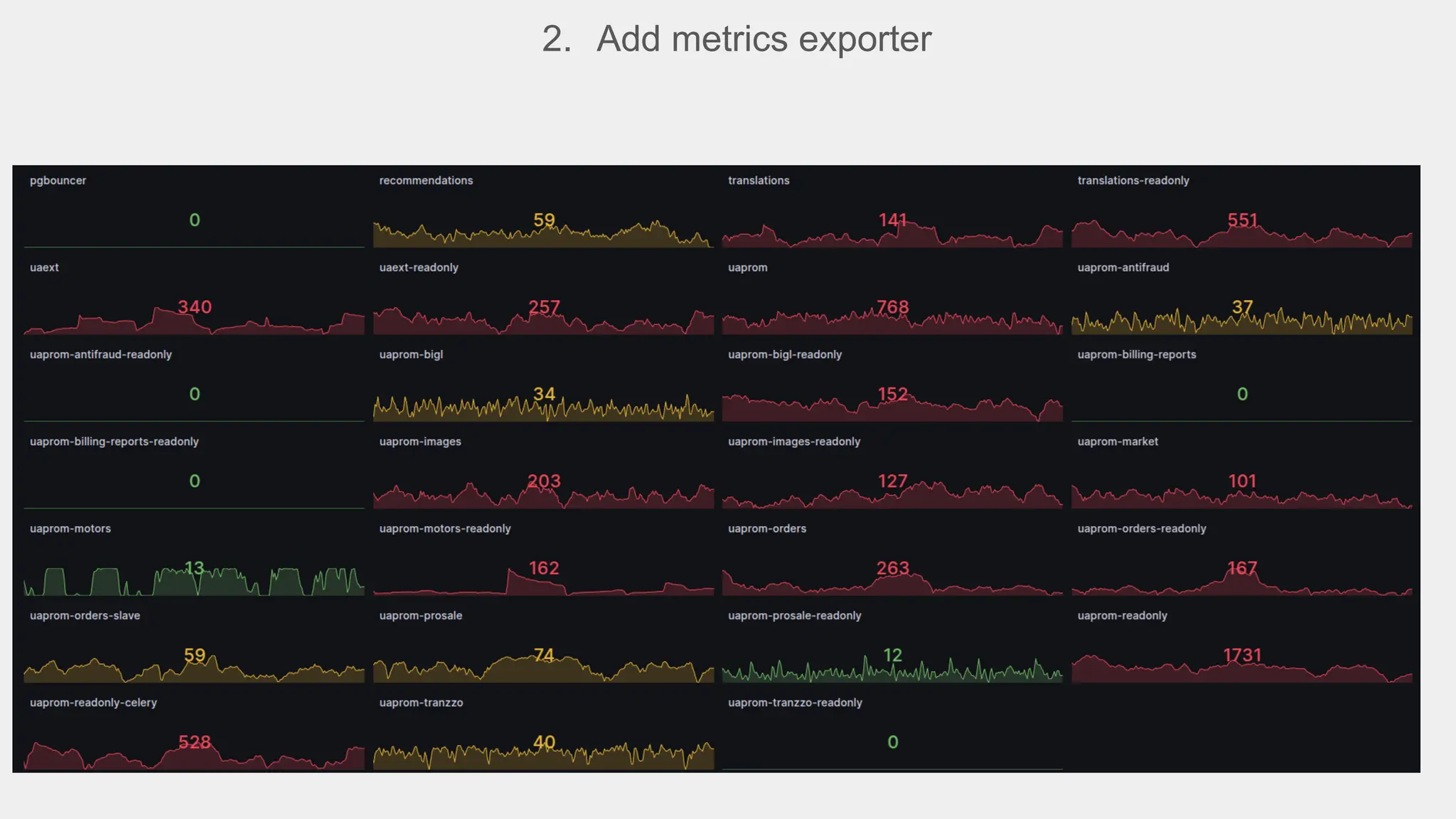
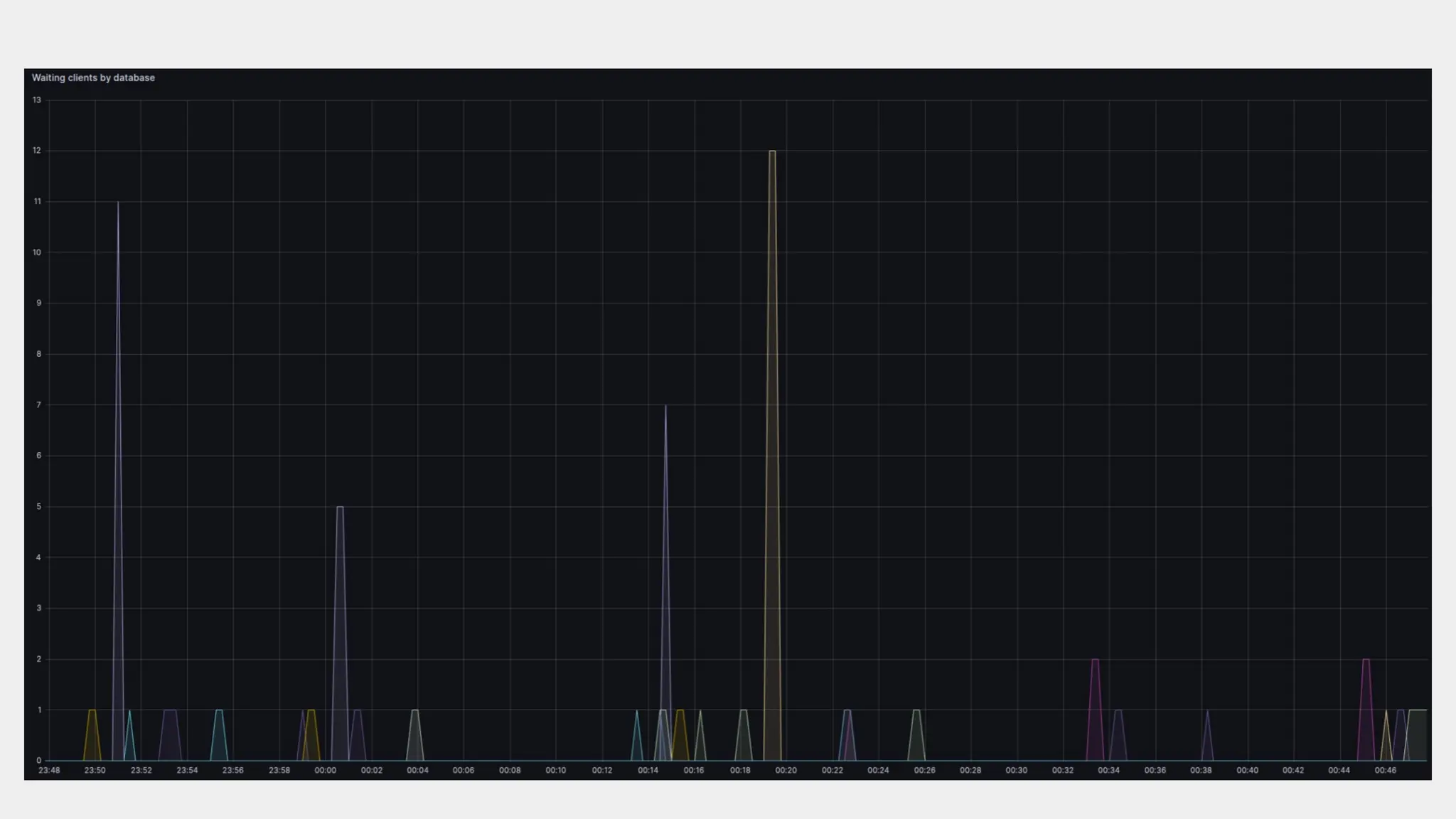
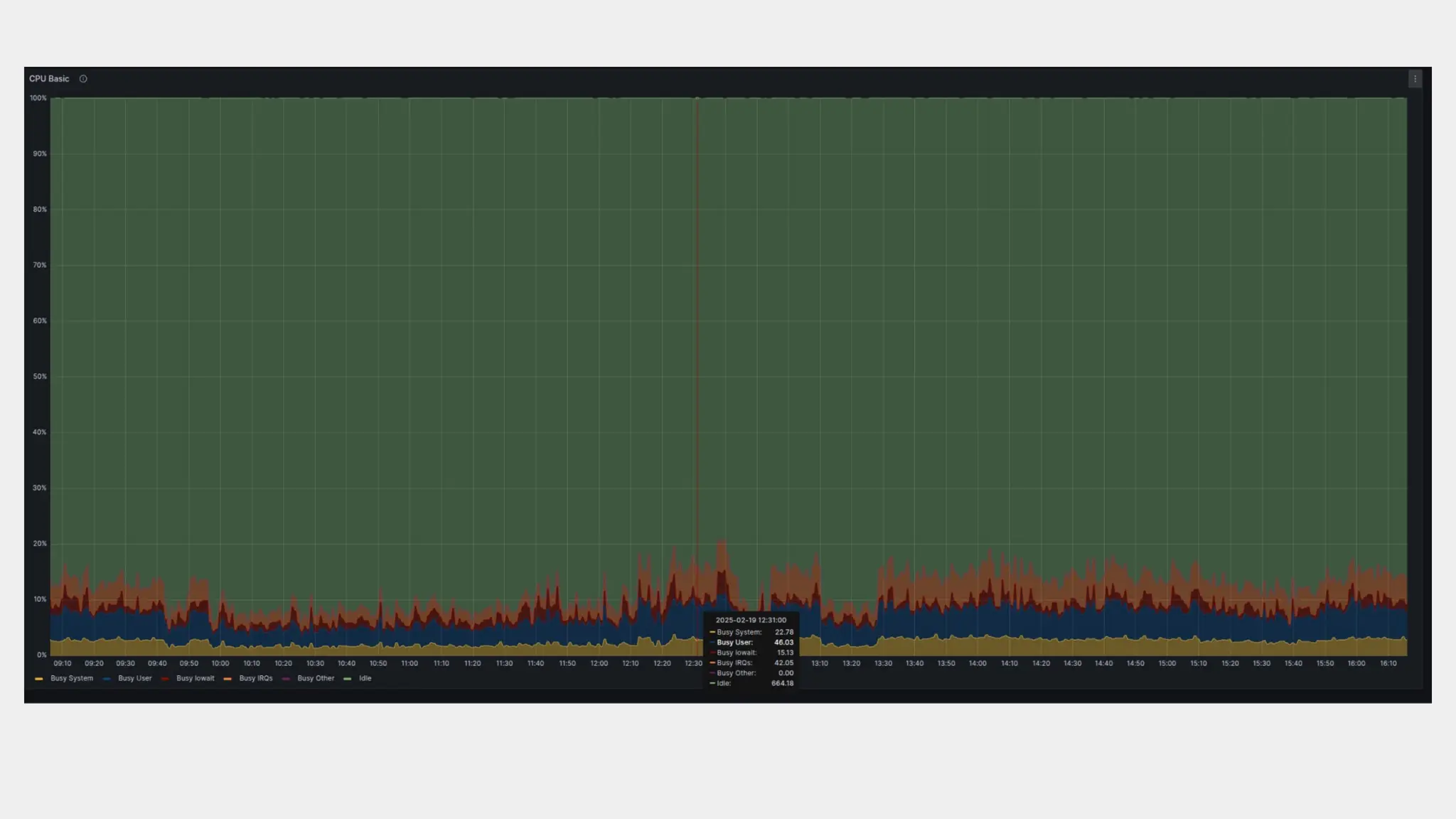
In this presentation I will try to analyze the experience of using pgbouncer and other database proxies at prom.ua. What profit does it bring in organizational sense, what new flexibility it gives to the infrastructure and everyday maintenance and scaling, which additional enchancements we managed to implement and test, what worked and what did not.


















![logit "Starting config watcher"
sleep 10s
config_file=/etc/pgbouncer/pgbouncer.ini
while true; do
if [ -f ${config_file} ]; then
logit "Start monitoring config file ${config_file}"
inotifywait -e DELETE_SELF ${config_file} &
wait $!
sleep 1s
if [ -f ${config_file} ]; then
logit "Settings changed! Applying new settings"
cat ${config_file}
logit "Reloading pgbouncer"
psql --host=127.0.0.1 --port 6543 -U pgbadmin pgbouncer -c "reload"
psql --host=127.0.0.1 --port 6543 -U pgbadmin pgbouncer -c "show databases"
# reload the dns
curl 127.0.0.1:8081/reload | true
else
logit "Config file ${config_file} is missing. Skipping"
fi
else
logit "Config file ${config_file} is missing. Sleeping 10s"
sleep 10s
fi
done &](https://image.slidesharecdn.com/pgbouncerforfunandprofit-250224063101-41695b28/75/Spin-up-pgbouncer-for-fun-and-profit-Vitaliy-Kharytonskiy-24-2048.jpg)


![pgbouncer=# show help;
NOTICE: Console usage
DETAIL:
SHOW HELP|CONFIG|DATABASES|POOLS|CLIENTS|SERVERS|USERS|
VERSION
SHOW PEERS|PEER_POOLS
SHOW FDS|SOCKETS|ACTIVE_SOCKETS|LISTS|MEM|STATE
SHOW DNS_HOSTS|DNS_ZONES
SHOW STATS|STATS_TOTALS|STATS_AVERAGES|TOTALS
SET key = arg
RELOAD
PAUSE [<db>]
RESUME [<db>]
DISABLE <db>
ENABLE <db>
RECONNECT [<db>]
KILL <db>
SUSPEND
SHUTDOWN
WAIT_CLOSE [<db>]
SHOW](https://image.slidesharecdn.com/pgbouncerforfunandprofit-250224063101-41695b28/75/Spin-up-pgbouncer-for-fun-and-profit-Vitaliy-Kharytonskiy-27-2048.jpg)